The AnyDesk Breach: Overview and Recommendations

On February 2, 2024, popular remote access solution AnyDesk disclosed that it had suffered a cyberattack that led to a compromise of its production systems. Code signing certificates and user passwords to AnyDesk’s web portal were revoked as a consequence.
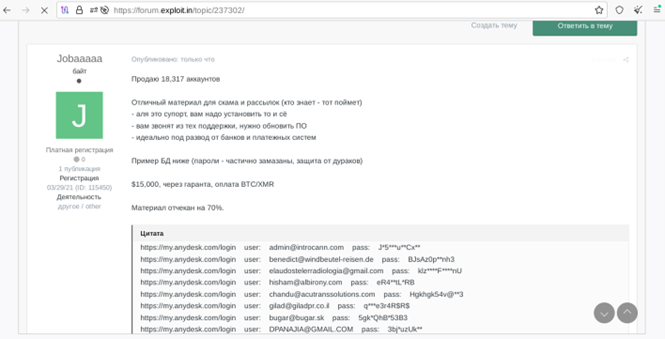
According to this blog post by Resecurity, on February 3, threat actors offered more than 18,000 AnyDesk credentials for sale on the dark web (Figure 1). The connection of the sale of credentials to the recent breach is still unclear, but this incident highlights the risk imposed by the compromise of leaked AnyDesk credentials.
In this post, we aim to provide defenders with resources to help assess the risk level for their environments and identify and mitigate potential breaches.
Potential impact on organizations
AnyDesk software is widely used by many organizations; we saw AnyDesk being used in approximately 25% of networks monitored by Akamai. From what we know so far, there are three main potential risks from the AnyDesk breach: password compromise, malicious use of stolen certificates, and a potential supply chain attack.
AnyDesk password compromise
AnyDesk claims that the attackers were not able to compromise any secrets used for user authentication, but they chose to revoke passwords to AnyDesk’s web portal anyway as a precaution.
If the attackers were in fact able to compromise these passwords, AnyDesk users are at risk of a credential stuffing attack; i.e., attackers might attempt to use the same credentials to authenticate to different services, exploiting passwords that are reused across different services. This could provide attackers with access to other sensitive services.
Stolen code signing certificate
The attackers were able to compromise the certificate used by AnyDesk to sign executables that were distributed to clients. By compromising the certificate, the attackers are able to sign any executable as AnyDesk, making it appear legitimate. This can allow them to evade security products and mislead analysts.
Potential supply chain attack
Although there isn't clear evidence for this yet, the risk of a software supply chain attack should be considered. The attackers had a significant hold on AnyDesk’s production environment, and it would have been relatively easy to insert a malicious payload into AnyDesk’s code base, potentially leading to client compromise.
Detection and mitigation
This attack was likely part of a larger operation with the eventual aim of targeting AnyDesk users. Because of that, the incident should be treated as ongoing — the attackers were able to compromise critical information from AnyDesk’s systems, but it is still unclear if, or how, they used it.
For this reason, we urge defenders to evaluate the potential risks to their environments by:
Identifying AnyDesk use
Applying mitigation steps on existing AnyDesk installations and users
Proactively hunting for suspicious activity related to AnyDesk
Identify AnyDesk use
AnyDesk can be used as part of corporate procedures, but it can also be manually installed by end users (“bring your own software”). This means that even if your organization doesn’t officially use AnyDesk, you might still be affected.
Host indicators
AnyDesk use can be identified by a variety of indicators on the host level — a comprehensive list of them was shared by @mthcht on X. We provide a matching set of osqueries based on their list, that can be used to detect these artifacts.
Processes
Anydesk processes can be identified by looking at paths that contain AnyDesk keywords.
The following query will detect these services:
SELECT
name as process_name,
path as process_path
FROM
processes
WHERE
path LIKE '%anydesk%'
Service names
AnyDesk uses the following service names:
AnyDesk Service
AnyDesk
AnyDeskMSI
The following query will detect these services:
SELECT
name as service_name,
path as service_path
FROM
services
WHERE
name = 'AnyDesk Service' or
name = 'AnyDesk' or
name = 'AnyDeskMSI'
Registry keys
AnyDesk creates registry keys to store configuration. The following query will detect these keys:
SELECT
key
FROM
registry
WHERE
key LIKE '%\SOFTWARE\Clients\Media\AnyDesk’ or
key LIKE '%\SYSTEM\%ControlSet%\Services\AnyDesk' or
key = 'HKEY_CLASSES_ROOT\.anydesk'
Named pipe
AnyDesk uses a named pipe called \adprinterpipe. The following query will detect this named pipe:
SELECT
processes.name as process_name,
processes.path as process_path,
pipes.name as pipe_name
FROM
pipes
LEFT JOIN
processes
ON
processes.pid = pipes.pid
WHERE
pipes.name = 'adprinterpipe'
Network indicators
Network logs should be inspected in an attempt to identify AnyDesk usage. Two indicators can be utilized: destination ports and destination domains.
Destination ports
AnyDesk uses a distinct set of ports: 6568, 7070, 50001, 50002, and 50003.
Akamai Guardicore Segmentation users can use the Reveal module to map traffic over these ports and analyze communication on the process level to immediately identify AnyDesk activity (Figure 2).
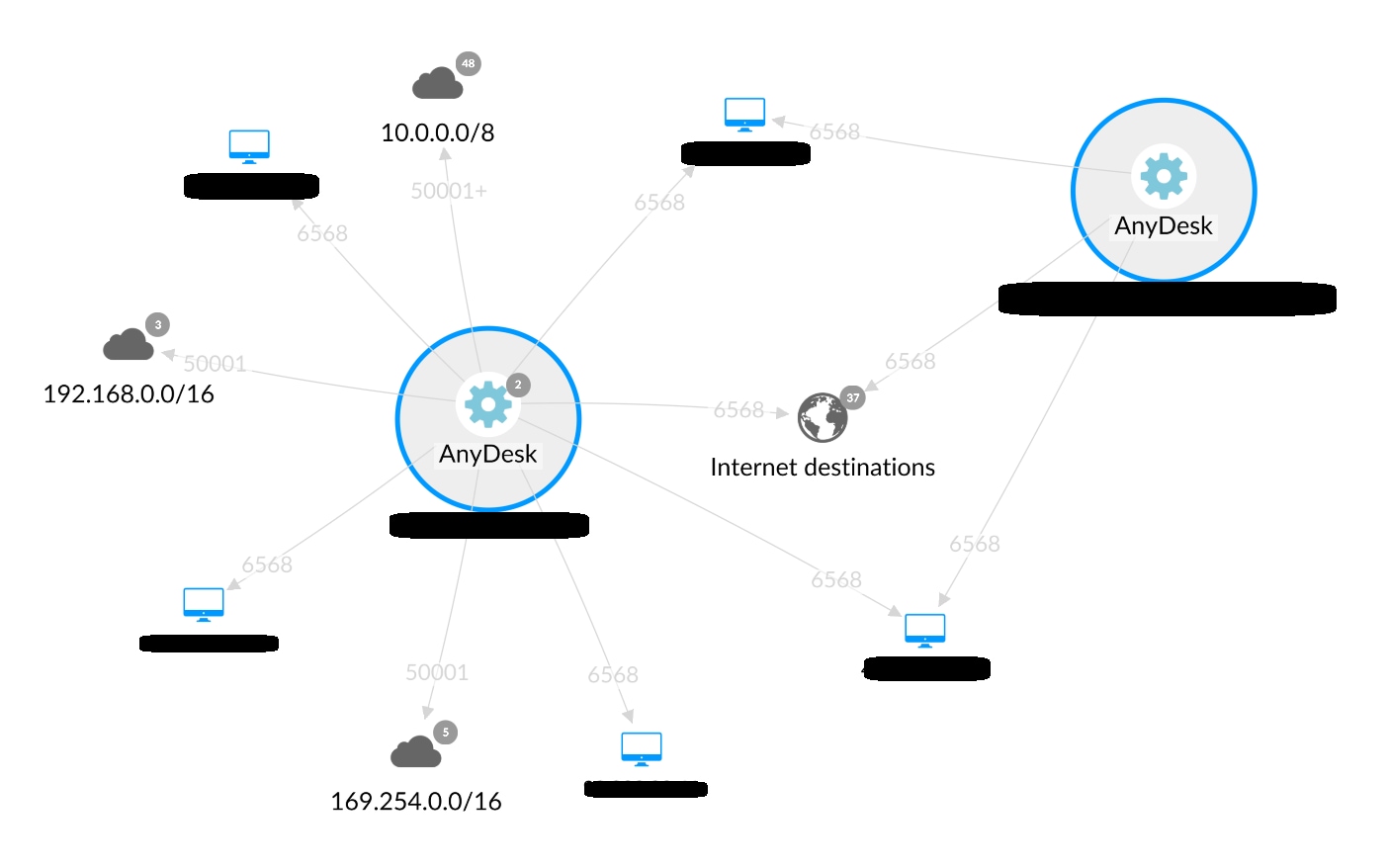 Fig. 2: Network map generated by Akamai Guardicore Segmentation Reveal, which highlights AnyDesk communication in the network
Fig. 2: Network map generated by Akamai Guardicore Segmentation Reveal, which highlights AnyDesk communication in the network
Destination domains
AnyDesk client processes will typically reach out to the AnyDesk domain at *.net.anydesk.com.
Akamai Guardicore Segmentation users can identify communication to this domain by filtering the network log (Figure 3).
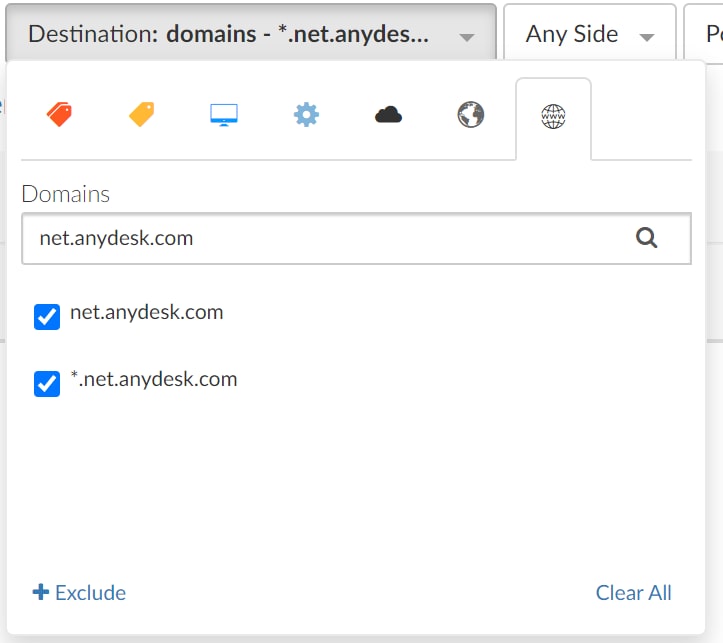 Fig. 3: Filtering the network log to identify communication to AnyDesk domains
Fig. 3: Filtering the network log to identify communication to AnyDesk domains
Apply mitigation steps
Once AnyDesk use is identified, there are two important mitigation steps that should be taken:
Update old AnyDesk clients
Assess password-related risks
Update old AnyDesk clients
AnyDesk versions prior to 7.0.15 and 8.0.8 were signed by the stolen certificate that was now revoked. Because of this, we recommend that you update clients to the latest version, which is signed with trusted certificates.
Assess password-related risks
Since AnyDesk users may be at risk of credential stuffing attacks, we recommend that you identify all AnyDesk user accounts in the environment and verify if their credentials were reused for other critical services.
Hunt for suspicious activity
In addition to the password-related risks, there are two other main risks that emerge as a result from this breach:
Misuse of the stolen code signing certificate
A potential supply chain attack through AnyDesk software
Defenders should attempt to identify both of these scenarios.
Identify revoked certificate use
Osquery could be used to identify executables in your environment that are signed with the revoked certificate. The following query accomplishes this:
SELECT
processes.name as process_name,
processes.path as process_path,
authenticode.subject_name as signer,
authenticode.serial_number as serial_number
FROM
processes
INNER JOIN
authenticode
ON
processes.path = authenticode.path
WHERE
authenticode.serial_number = '0dbf152deaf0b981a8a938d53f769db8'
In addition, this YARA rule by Florain Roth could be used to detect suspicious executables signed with the revoked certificate.
Identify anomalous AnyDesk behavior
To attempt to detect a potential backdoor distributed in AnyDesk software, you should direct special attention to machines that use AnyDesk. A software backdoor will alter the normal behavior of the application, providing a detection opportunity for defenders.
There are many possible anomalies that could indicate such a backdoor: anomalous destination ports, spawned processes, new registry keys, etc.
Akamai Hunt, Akamai’s managed threat hunting service, offers its customers protection in the form of a large set of anomaly detection techniques that constantly monitor the environment in an attempt to detect the unknown.
Specifically with the AnyDesk case, Akamai Hunt provided its customers with details and recommendations about existing AnyDesk deployments, including the potential use of the revoked certificate, which may indicate malicious activity. Additionally, Hunt constantly monitors its customer environments for any anomalous activity undertaken by a possibly modified AnyDesk process.
Summary
This is likely not the last we will hear of this breach. We are continuously monitoring the situation and will provide additional details and guidance in future blog posts as the breach unfolds.
This blog post provides an overview of our current understanding and our recommendations given the information available. Our review is ongoing and any information herein is subject to change. You can also visit our X account for real-time updates.