Yes, blackhole routing is adaptable and can be customized to suit the specific security needs of both small-scale networks and large enterprises.
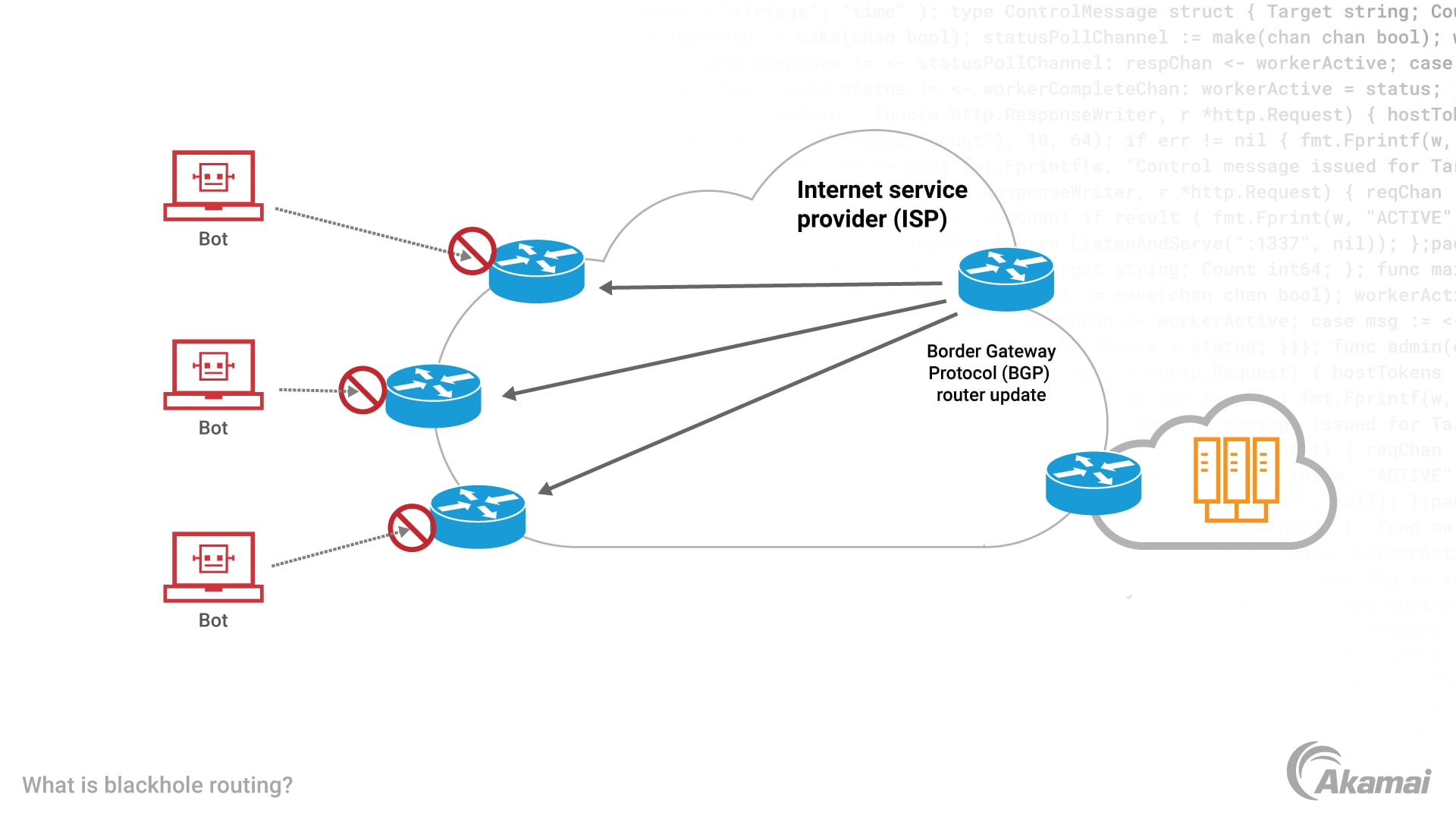
Remote triggered blackhole (RTBH) routing, also known as blackholing, is one of the defensive measures deployed by an internet service provider (ISP) or network administrators to mitigate a distributed denial-of-service (DDoS) attack. Blackhole routing redirects malicious or unwanted traffic into a “black hole” — a null interface such as null0 — via interior gateway protocol domain, where it is permanently discarded. When a DDoS attack occurs, network administrators can quickly redirect to a blackhole all traffic being sent from a specific source IP address or to a specific destination IP address. RTBH was designed mainly to move the attack traffic away from the internet border of an organization’s wide area network (WAN), which prevents the DDoS from saturating internet ports or connections. The RTBH feature is destination IP based, and if you require source IP-based filtering via RTBH, then you need to enable Unicast Reverse Path Forwarding (uRPF). It must be applied on both sides of the internet transit connection or “link,” and uRPF would need to be enabled in loose or strict mode to achieve source IP-based RTBH.
What is a DDoS attack?
A DDoS attack is a malicious action targeting a server, service, or network. DDoS attacks overwhelm the target with traffic, exhausting its resources and bandwidth. As a result, the target may slow down or crash, preventing it from handling legitimate traffic. DDoS attacks are typically carried out by botnets (a network of computers and devices that have been infected with malware, are under the attacker’s control, and can be directed to inundate a target with traffic. Because botnets may include hundreds or thousands of devices, it can be difficult for security defenses to detect and mitigate an attack. Common DDoS attacks include ICMP floods, SYN floods, Slowloris attacks, and HTTP floods.
How does blackhole routing work?
To block a DDoS attack with a black hole, administrators configure routers to redirect traffic to a null interface, effectively discarding the traffic. This is typically due to the network not having enough internet port capacity to consume the attack without jeopardizing bandwidth for production services.
ISPs and network administrators may use several blackhole routing prevention techniques to block malicious DDoS traffic from reaching its intended target. These IP routing methods may redirect traffic based on source or destination IP addresses.
- Static blackhole routing involves manually configuring routers to drop traffic coming from or destined for a specific IP address. This static route technique effectively blocks traffic from IP addresses that are known to be malicious from targeting servers.
- BGP blackhole routing is a destination-based packet filtering technology that uses the Border Gateway Protocol (BGP) to “advertise” or communicate a blackhole route for a specific IP address to other routers within the BGP network.
- Remote triggered blackhole filtering, or RTBH filtering, typically blocks traffic based on destination IP addresses. RTBH filtering also uses BGP but provides a more controlled and targeted approach, allowing network administrators to mitigate attacks against specific hosts or subnets without affecting the entire network.
- Flowspec BGP blackhole routing provides an even more granular approach to traffic filtering. With this technique, administrators can specify additional parameters that help to target malicious traffic more narrowly while allowing legitimate network traffic to reach its destination.
- Blocklists for spam filtering can also be used for blackholing. Blocklists contain IP addresses that are known to send spam or malicious traffic. When traffic arrives at an email server from an IP address on the block list, it will be automatically discarded or quarantined for review.
- Destination-based IP filtering is commonly used to discard unwanted traffic from a network. This can be achieved by a single host router or “all” routers within the network. RTBH can also be applied to the direction a packet is traversing a network (inbound received or outbound transmit).
What are the advantages of blackhole routing?
Blackhole routing can be an alternate means to mitigate DDoS attacks and block other malicious traffic. By discarding traffic intended for certain IP addresses, blackholing may improve network performance and reduce congestion.
What are the drawbacks of blackhole routing?
Because blackhole routing may also redirect legitimate traffic, this DDoS mitigation technique may make internet-facing services or web applications unavailable to legitimate users and traffic. Blackhole routing also provides little insight into the nature of the traffic, preventing security teams from gathering information about its source or the effectiveness of mitigation techniques. With the lack of logging or visibility to the actions taken place, false positives can be an issue to remediate. Depending on the scale of the attack, blackhole routing may impact network performance for the peers of the network operator enabling the RTBH function.
Is blackhole routing an effective defense against DDoS attacks?
While DDoS blackhole routing can effectively redirect malicious traffic away from an IP address, this technique is not really an effective form of defense. Because blackholing may also redirect legitimate traffic, it can effectively take a targeted asset offline, essentially completing the attacker’s mission. Depending on the infrastructure of the ISP, other customers may experience degraded performance or be taken offline as well. For this reason, most organizations seek to adopt more effective DDoS offenses that do not interfere with legitimate traffic or cause downtime.
Frequently Asked Questions (FAQ)
Blackhole routing serves as a reactive countermeasure to divert malicious traffic away from a network, preventing potential DoS or DDoS security events from impacting production services.
Unlike traditional security measures that focus on identifying and blocking threats, blackhole routing redirects malicious traffic to a virtual “black hole,” isolating and neutralizing potential threats.
While not a total remedy, blackhole routing is one tool in a comprehensive cybersecurity strategy, providing an additional layer of defense against various cyberthreats.
One potential drawback is the risk of false positives, where legitimate traffic may be incorrectly identified and diverted. Lack of reporting and visibility also causes concern for the quality or consistency of mitigation being enabled. Careful configuration and additional monitoring are essential to mitigate this risk.
Regular updates are crucial to ensure the effectiveness of blackhole routing. Cyberthreats evolve, and staying ahead requires continuous monitoring and adjustments to configurations.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.