Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Application programming interfaces (APIs) live at the core of an organization’s digital products, services, and cloud environments. Because they allow very different systems to work together and share data, APIs are essential to innovation, business productivity, and software development.
While APIs are indispensable to our modern IT systems, they’re also a favorite target of cybercriminals. For example, APIs’ constant access to data makes them an operational risk. For this reason, API security solutions have become a critical part of the security stack. By establishing protocols, tools, and practices that safeguard interactions between APIs and other systems, API security solutions help prevent unauthorized access, data breaches, and other devastating cyberattacks.
What is API security?
An API is a set of rules and protocols that enable highly diverse software applications and systems to communicate easily and share data and functionality. APIs essentially define the methods and data formats that one application can use to request and share information with another.
This functionality has enormous benefits for software developers. As developers build new apps and web applications, APIs enable them to incorporate data and leverage functionality from existing software, rather than creating new databases and building new functionality from scratch. As a result, developers can accelerate timelines and create more powerful software.
Because they are so widely used and they frequently access sensitive data, APIs have become a primary attack vector for malicious actors. API security is the practice of putting protocols, best practices, and technology in place to guard against a wide range of API attacks.
The need for API security solutions
Because APIs are essential to the functionality of IT systems, API security is a business-critical endeavor. Successful attacks on APIs may have devastating consequences for an organization, including:
- Financial losses. API attacks may enable cybercriminals to gain access to financial accounts and steal funds. Additional financial losses include legal fees, regulatory fines, compensation for customers affected by the attack, and the long-term impact of lost business opportunities.
- Data breaches. Since APIs often handle sensitive data and personally identifiable information (PII), an API attack can result in data breaches that may lead to identity theft, financial fraud, and other malicious activities.
- Operational disruption. Because APIs are so integral to the performance of applications and systems, an API security breach can lead to downtime and loss of productivity. Additionally, threat actors often use APIs to launch denial-of-service (DoS) attacks that cause services and functionality to become unavailable to legitimate users.
- Damaged reputation. A successful API attack can severely damage an organization’s reputation. Customers may be wary of doing business with the company, and partners may lose trust in the organization’s ability to protect their data. These developments can lead to a significant loss of business opportunity.
- Loss of intellectual property. Attackers may exploit APIs to gain access to vital business information, including trade secrets, business plans, and intellectual property.
The challenges of API security
Any API security solution must help organizations overcome several major hurdles to protecting APIs from attack and abuse.
- Complexity of APIs. The complexity of modern APIs — especially those using GraphQL or REST — make security more difficult.
- Evolving threats. Threats to APIs are constantly evolving as attackers seek new vulnerabilities to exploit and new ways to abuse APIs.
- Deadline pressures. API security concerns are often in tension with the need for developers to move quickly to meet deadlines in fast-based DevOps workflows.
- Rapid proliferation. The explosive growth in the use of APIs makes it difficult for IT teams to stay on top of security, especially as new versions of APIs are released.
- Lack of visibility. As rapid and unmanaged growth contributes to “API sprawl,” IT teams are hard-pressed to accurately identify and inventory APIs — making it impossible to protect all the APIs in their ecosystem.
- Poor governance frameworks. In many organizations, multiple teams are developing APIs simultaneously without any central framework for security or governance. To make matters worse, organizations frequently adopt open-source or third-party APIs that make secure integration even more difficult.
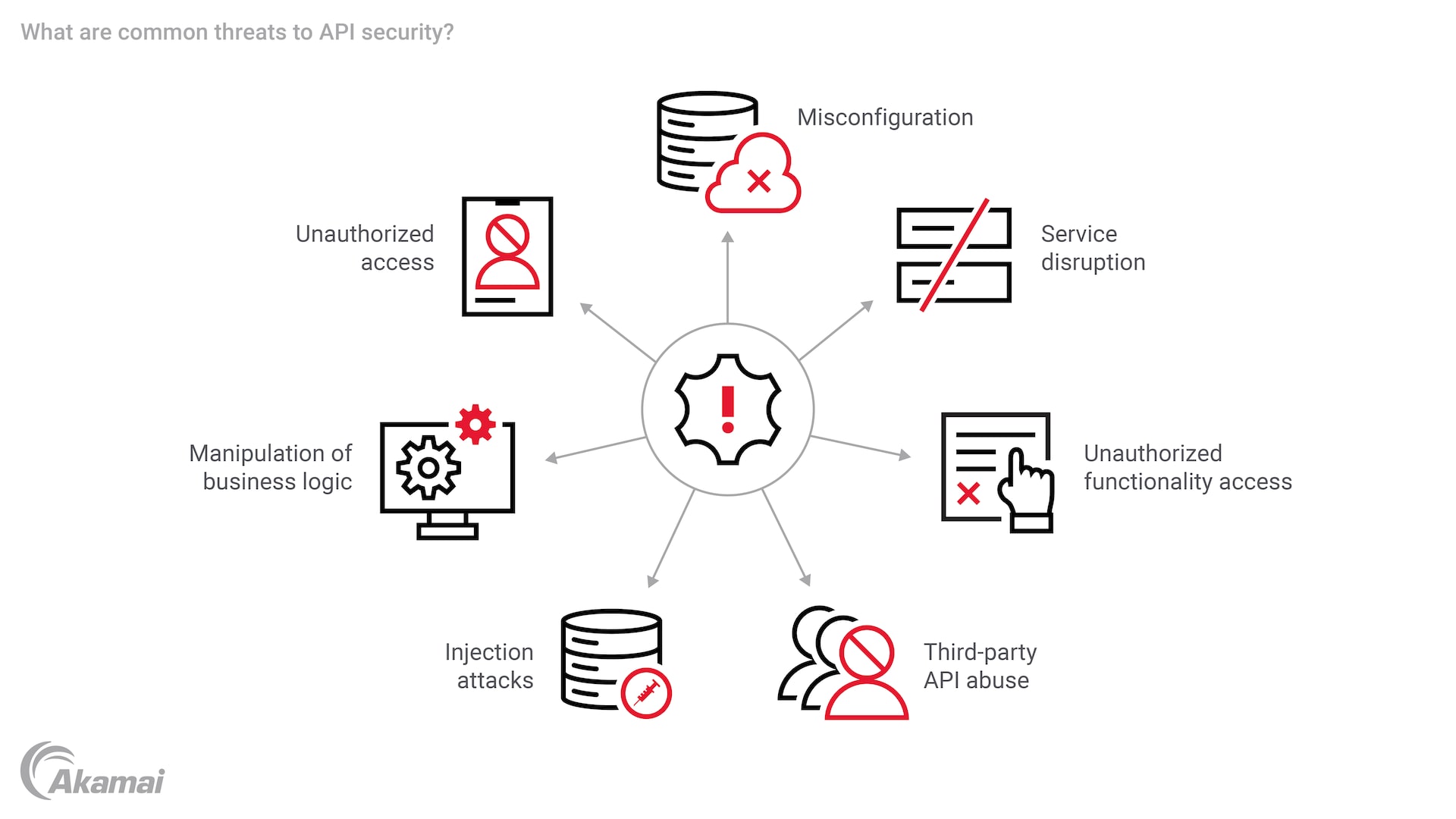
Common threats to API security
Malicious actors can use or abuse APIs in a variety of ways to exploit vulnerabilities, compromise data, and disrupt services.
- Unauthorized access. Attackers may manipulate API endpoints or use credential stuffing and brute-force attacks to gain unauthorized access to data.
- Service disruption. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks overwhelm APIs with a large number of requests, causing applications and services to become unavailable to legitimate users. Alternatively, attackers may abuse API calls to trigger excessive consumption of resources like bandwidth and compute power, increasing operational costs and potentially disrupting services.
- Injection attacks. Attacks like SQL injection and cross-site scripting (XSS) can cause APIs to perform unintended and dangerous actions that result in data loss, data breaches, or account takeover.
- Unauthorized functionality access. These attacks exploit weaknesses in access controls to perform unauthorized actions or to bypass security controls.
- Manipulation of business logic. Attackers frequently exploit APIs that fail to protect business logic, enabling them to automatically fake accounts. Mass assignment attacks exploit APIs that automatically bind input data to internal properties without properly filtering it, allowing hackers to change user roles by including extra parameters in the API request.
- Misconfiguration. Exploiting misconfigured APIs may provide attackers with access to sensitive data or functionality. Attackers may also target unmonitored or undocumented APIs with weak security.
- Third-party API abuse. When organizations trust data from third-party APIs without properly validating it, attackers can manipulate the primary service’s data or functionality to access other systems in the supply chain.
For a detailed explanation, consult the OWASP API Security Top 10 list of threats.
Types of API security solutions
Organizations can adopt API cybersecurity tools that deliver multiple layers of protection and help organizations improve security posture around APIs.
- Authentication and authorization technologies: To ensure that only authorized users can access APIs and manipulate data, organizations must adopt authentication methods like multi-factor authentication, OAuth, OpenID Connect, and API keys. Authorization technologies include role-based access control and attribute-based access control.
- API gateway: An API gateway serves as the entry point for all API requests, performing tasks like authentication, rate limiting, traffic management, and caching to prevent DDoS attacks in real time.
- Encryption: Encryption solutions prevent data transmitted via APIs from being intercepted by attackers. To protect API traffic, requests, responses, and data at rest, organizations may use techniques like SSL, TLS, and AES encryption.
- Rate limiting: Rate limiting prevents DoS attacks by limiting the number of requests a user or device can make within a specified time period. This prevents attackers from overwhelming APIs with requests.
- Auditing and logging: Auditing involves tracking API requests and responses, while logging involves recording API events and activities in a secure and tamper-proof fashion. Continual review of audits and logs can help provide visibility into API activity, allowing IT teams to detect and mitigate security threats.
- API security testing: Development and security teams must regularly test to identify API vulnerabilities and potential API risks. Using manual techniques or automation, API testing ensures that APIs are secure and that they function as intended. The dynamic application security testing (DAST) approach enables organizations to test APIs in runtime under real-world conditions, while static application security testing (SAST) reviews an API’s code to detect and address security issues early in the development process.
- API monitoring and runtime protection: Continuous monitoring of API usage and behavior lets security teams establish normal baseline behavior and identify anomalous or suspicious behavior that may indicate API abuse.
- Vulnerability management: To prevent attackers from exploiting vulnerabilities within APIs, security teams may deploy API security solutions for vulnerability scanning, patching, and remediation.
- API security platform: Organizations may choose to adopt an API protection platform that consolidates a number of API security solutions in one location.
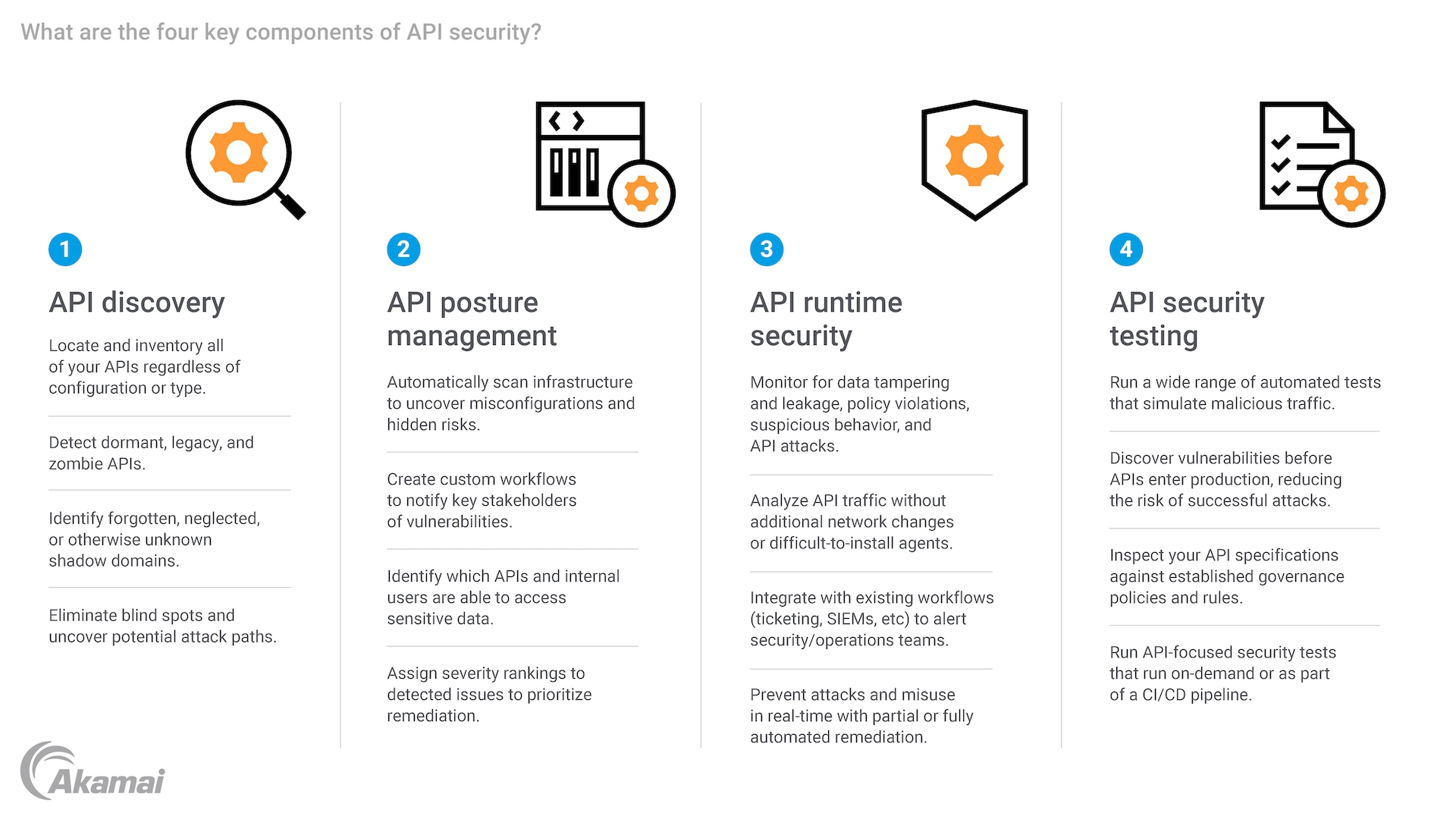
The four key components of API security
1. API discovery:
- Locate and inventory all of your APIs regardless of configuration or type.
- Detect dormant, legacy, and zombie APIs.
- Identify forgotten, neglected, or otherwise unknown shadow domains.
- Eliminate blind spots and uncover potential attack paths.
2. API posture management:
- Automatically scan infrastructure to uncover misconfigurations and hidden risks.
- Create custom workflows to notify key stakeholders of vulnerabilities.
- Identify which APIs and internal users are able to access sensitive data.
- Assign severity rankings to detected issues to prioritize remediation.
3. API runtime security:
- Monitor for data tampering and leakage, policy violations, suspicious behavior, and API attacks.
- Analyze API traffic without additional network changes or difficult-to-install agents.
- Integrate with existing workflows (ticketing, SIEMs, etc.) to alert security/operations teams.
- Prevent attacks and misuse in real time with partial or fully automated remediation.
4. API security testing:
- Run a wide range of automated tests that simulate malicious traffic.
- Discover vulnerabilities before APIs enter production, reducing the risk of successful attacks.
- Inspect your API specifications against established governance policies and rules.
- Run API-focused security tests that run on demand or as part of a CI/CD pipeline.
API security best practices
Along with API security tools, IT teams may adopt a variety of API security best practices that help to protect APIs from threats and abuse.
- API security strategy: APIs play a critical role in enabling interoperability between different systems and platforms, including cloud-native and multicloud environments. Managing API security in these complex ecosystems requires a robust security strategy to ensure that APIs operate securely across various cloud environments, including AWS and SaaS providers.
- Continuous API discovery: IT teams must continually seek to visualize all APIs in their digital ecosystem — including shadow APIs and zombie APIs — and maintain an up-to-date API inventory. Discovery can also help with managing API sprawl and reduce the attack surface by ensuring that old versions of APIs are properly deprecated and retired.
- API lifecycle management: API security requires effective management of the entire API lifecycle, from design and development to deployment and deprecation. API management that focuses on API protection at every lifecycle phase can help to ensure stronger API security.
- Secure API development: Integrating security into DevOps pipelines, application security (AppSec) efforts, and DevSecOps practices helps to make API security a fundamental part of the development lifecycle.
Frequently Asked Questions (FAQ)
An API endpoint is a specific address or URL where an application can access another service to get data or perform actions. It’s the door through which requests and information pass between different software systems.
API security and application security both focus on securing software systems. API security focuses more narrowly on protecting APIs to prevent unauthorized access, to encrypt and secure data, and to remediate common vulnerabilities. Application security and web application security have a broader scope, focusing on securing the entire application, including its code, infrastructure, and user data. Application security encompasses practices like secure coding, configuration management, access control, and regular security testing. In essence, API security is a subset of application security, tailored to the specific needs of protecting the interfaces that allow applications to communicate with each other.
Akamai Security protects the applications that drive your business at every point of interaction, without compromising performance or customer experience. By leveraging the scale of our global platform and its visibility to threats, we partner with you to prevent, detect, and mitigate threats, so you can build brand trust and deliver on your vision.