Beyond the Login — Keeping Accounts Secure with Lifecycle Protection
In today’s digital landscape, securing online accounts is essential; studies indicate that account takeover fraud caused nearly US$13 billion in losses in 2023. Fraudsters are becoming increasingly sophisticated, targeting multiple points of the account lifecycle — from account creation to post-login activities like password resets and payments — to commit malicious activities. Full lifecycle protection is essential to stay ahead of these evolving threats and defend against a wide range of online account abuse.
The growing threat of account abuse
Online account abuse comes in many forms and targets weaknesses at many different stages of the user account journey. Organizations are vulnerable to threats like fake account creation to post-login abuse if they only focus on securing one aspect of the account.
Common types of account abuse include account opening abuse, account takeover, and post-login abuse.
Account opening abuse
Fraudsters create fake accounts using stolen or synthetic identities to exploit promotions, engage in money laundering, or commit financial fraud.
Account takeover
Attackers use stolen credentials from data breaches to attempt login on various sites and exploit users who reuse passwords. Once attackers gain access to an account through stolen credentials or phishing, they commit account takeover abuse and fraud.
Post-login abuse
Even after successfully logging in, attackers may exploit security gaps in account updates, password resets and changes, or payment transactions. They can perform malicious activities like making fraudulent transactions, hoarding inventory, committing carding attacks, or stealing personal data.
Without a comprehensive security strategy that addresses all of these common account abuse stages, businesses and users are left exposed.
Full lifecycle protection
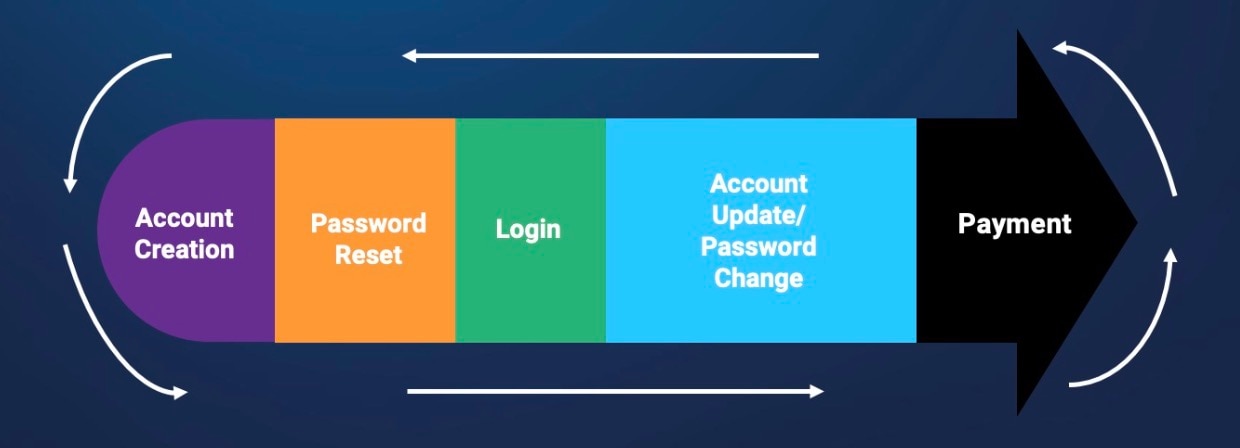
Securing online accounts requires a multi-layered approach. These are the key stages for which protection is crucial.
Account creation: Fraudsters often open fake accounts by using stolen identities or fake information to exploit promotional offers, launder money, or engage in other criminal activities. Early detection of suspicious patterns during account creation prevents abuse from escalating further.
Password reset and account verification: Fraudsters often manipulate password reset processes to take control of user accounts. By monitoring password reset requests and cross-referencing them against users’ typical behavior — such as typical device, IP address, or location — businesses can detect and block abnormal reset attempts in real time.
Account login: Account login is a major target for attacks like credential stuffing and brute-force attacks in which attackers use automated tools and sophisticated bots to try numerous username and password combinations. Implementing strong authentication methods helps to block unauthorized access.
Account update and password change: Once an account is compromised, attackers may attempt to update account details or make changes to lock out the legitimate user. Monitoring suspicious activity like unexpected account updates, password changes, or new payment methods can help identify imposter activity and prevent damage before it occurs.
Payments: After taking over an account, fraudsters often make unauthorized transactions or perform fraudulent money transfers. By monitoring anomalies in payment behavior, businesses can secure their checkouts against abuse.
Gain holistic defense with Akamai Account Protector
Account abuse leads to significant financial loss, erosion in customer trust, and reputational damage for businesses. Akamai Account Protector offers comprehensive account lifecycle protection by analyzing user risk at every stage, from account creation to post-login activities, enabling the detection of suspicious behaviors before they escalate.
Its advanced capabilities include real-time user session risk scoring, email intelligence, and sophisticated bot detection, all of which ensure businesses can differentiate legitimate users from imposters. By providing actionable insights and automated response options at the edge, Akamai helps organizations effectively protect user accounts, secure revenue, and maintain a seamless customer experience.