How Account Opening Abuse Affects 6 Industries

To complete a transaction on most websites — whether in retail, travel, or especially banking — users must create an account.
Security standards for creating accounts
Websites have different security standards for account creation:
Retail, travel, and hospitality sites mostly require a first and last name and an email address
Sites that offer subscription-based services, like streaming, news articles, or cloud services, often require a credit card number and billing address
Financial services tend to be the most stringent, requiring more personal information, such as government ID, proof of residence, a valid email address, and a phone number
Verifying information before account creation
Verification levels of information provided before an account is created also vary.
In banking, all personal data is validated through know your customer (KYC) services; users are asked to verify their email address or phone number with a one-time password and may be prompted to set up multi-factor authentication (MFA). In retail, however, the focus is largely on reducing obstacles to attract more customers and, sometimes, to cater to multigenerational audiences that may not be as familiar with web technologies.
What is account opening abuse?
Popular sites are frequently plagued by fraudsters opening accounts in large numbers. This type of attack is known as “account opening abuse.” Why does this happen, and what do attackers do with these accounts? This three-part blog series will answer these questions and explain how fraud rings are organized.
What are the most common attack schemes that stem from account opening abuse?
The mass creation of accounts observed on popular websites is a symptom of a broader attack scheme. The fraud that uses fake accounts varies depending on the industry, the attacker’s interest, and the incentives that companies offer to attract new customers.
Although the fraud schemes vary, financial and personal gain are the common denominators among attacker motivations. The figure illustrates a nonexhaustive breakdown by six industries (gaming, social media, digital commerce, media and streaming, financial services, and auction sites) of the most common attack schemes that employ fake accounts.
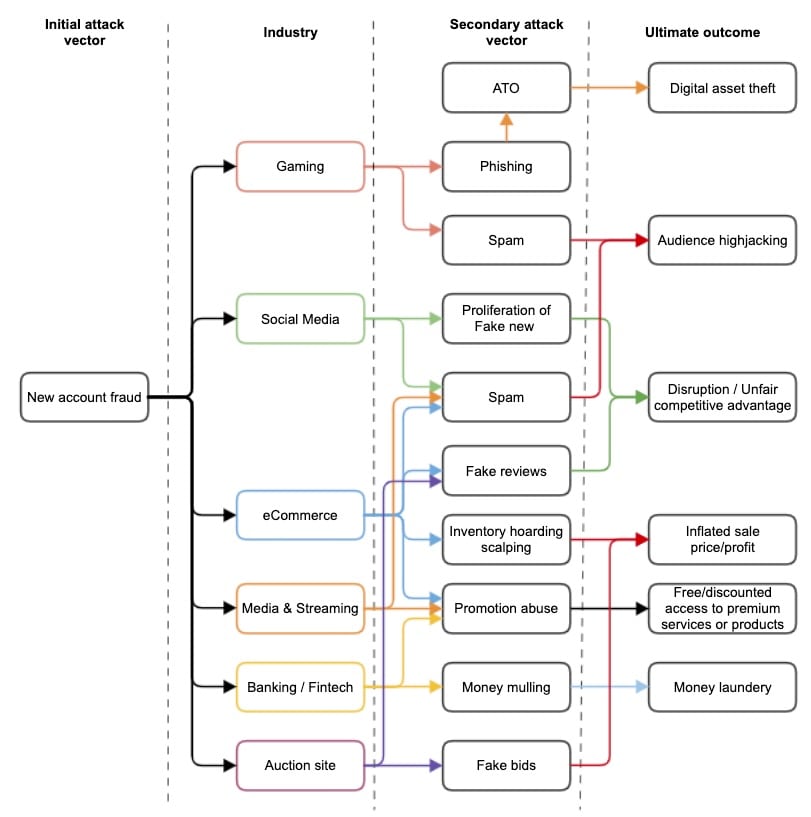 Figure: Account opening fraud schemes by industry
Figure: Account opening fraud schemes by industry
1. Gaming
A common attack scheme using fake accounts often occurs within the gaming industry. A number of games, such as esports, have a social media component. A superstar gamer is expected to have a lot of fans, and the number of followers matters for credibility.
Fraudsters may create fake accounts then use bots to control them, posting cheering comments for the “star player,” for instance, while bashing other opponents to give the star player an unfair competitive advantage.
Digital asset theft
Fake accounts may also be an instrument for phishing attacks as an intermediate step for account takeover or stealing digital assets. In gaming, these assets could be in-game currency, rare items, or special player powers. The fraudster controlling the fake account may befriend other players and entice them to share their usernames and passwords.
Once they obtain these credentials, the fraudster then connects to the victim’s account and checks their digital assets. Such assets may be stolen through an auction using the fake account as a proxy. Alternatively, the attacker may decide to sell the account on the dark web, as the ones with significant assets attached to them can be sold for hundreds of dollars.
2. Social media
Social media is another industry that’s ripe for attack schemes using fake accounts. An aspiring influencer may leverage fake accounts to increase their popularity on social media. Influencers and content creators with more followers will be more visible, appear more credible, draw more actual followers, and give the company or individual account owner a competitive (and likely financial) advantage.
Proliferation of spam
In a large-scale operation, bots would comment on or “like” a post and grow their network with actual users. Some of these posts may be sophisticated, such as disinformation campaigns that alter the population's perception of certain political issues or personalities — which, in the worst-case scenario, could destabilize a country.
Beyond simply making a post more visible, fake accounts may also post spam to drive users to unrelated content to hijack the audience or even expose them to malicious content.
3. Digital commerce
Another industry that’s a target for account opening abuse is digital commerce. Premium digital commerce sites regularly orchestrate hype sales events for popular or limited-edition items to draw a large virtual crowd and build brand awareness. The events also attract scalpers who use bots to increase their chances of obtaining the coveted item.
Bots: Faster than a speeding human
In advance of the event (it could be hours, but it’s preferably days or weeks in advance to let the accounts “mature”), bot operators create multiple accounts that are then used during the sale event to try to purchase the item. Bots can access and check out the item as soon as the event starts, faster than a human could ever react. Scalpers then resell these items at a premium on a secondary market, like an auction site, thus inflating prices for legitimate consumers.
The (fake) reviews are in
Digital commerce sites also allow users to review products. Fake accounts may be used to write fake positive reviews of less popular or low-quality items, while posting bad reviews of more popular items from competitors. The reviews may also include spam to steer users to alternate content. Again, the goal is to hijack part of the audience.
Fake accounts may also be created for promotion abuse; that is, to gain access to coupons or discounts designed to be awarded only to new users on their first purchase.
4. Media and streaming
Promotion abuse is common in media and streaming, as well. Access to premium media content usually requires a monthly fee, yet most platforms offer the service for free for some time (generally one month). The new subscriber can cancel their new account at any time. Fraudsters who want to access the service without paying may keep opening and closing new accounts once the trial period expires.
These platforms often have a social media site on which users can comment on the content with a valid account. Attackers may use fake accounts to post spam on these forums.
5. Financial services
Unlike traditional banks, neo-banks operate exclusively online and face unique challenges. To attract customers from traditional banks, these banks frequently offer cash bonuses to customers who open new accounts, set up direct deposits, and maintain a certain amount of money for specific periods.
An attacker can open accounts at a neo-bank using stolen data and email addresses. After successfully opening an account, the attacker then sets up the direct deposit, and transfers the minimum amount of funds to receive the cash bonus. Once that reward is received, the attacker will then transfer the funds, including the cash reward, out of the account.
Fake accounts may also be used for money muling (transferring cash from one institution to another), which makes it more difficult for anyone to trace or retrieve stolen money in a money laundering scheme.
6. Auction sites
Sellers on auction sites may create fake accounts that can be used during an auction to bid on items. If an item is popular, fake bids generated by bots inflate the item's price and may start a bidding war.
Maintaining a reputable image as a seller is of paramount importance on auction sites. To manipulate this perception, fraudulent accounts may be used to post fabricated comments that artificially inflate the seller's reputation.
Stay tuned
In part two of this series, we’ll examine the fraud rings that create fake new accounts.
How Akamai can help
Akamai stands at the forefront of abuse and fraud protection with multiple solutions available to stop bots in real time. Solutions like Akamai Account Protector and Akamai Client-Side Protection and Compliance effectively and proactively fortify defenses against cybersecurity threats. If you’d like to speak with someone about account opening abuse, call your Akamai account representative or talk to an expert now.



