DDoS in Financial Services: What to Know and What to Do
by Mark Schimmelbusch, Dennis Birchard
Executive summary
- Akamai researchers have been monitoring the trends of distributed denial-of-service (DDoS) attacks between Q1 2021 and Q1 2022 and have found a significant uptick toward Layer 7 DDoS attacks despite them being more expensive and more difficult to execute.
- DDoS has evolved into multi-vector attacks which are increasingly more difficult to detect and mitigate.
- Starting in November 2021, our wealth management customers began experiencing Layer 7 DDoS extortion attacks.
- In July 2022, there was a major spike in this activity, with a goal of influencing investment decisions.
- The most frequent attack vector has been HTTPS flood at 35% of total attacks.
- Detection and mitigation for this level of attacks is more “hands-on-keyboard,” which is an additional stress to security teams.
Introduction
DDoS attacks aren’t going out of fashion, in fact, they’re right on the runway.
Through the years, DDoS attacks have evolved far from their experimental beginnings. With the likes of DynDNS, GitHub, and Google getting hit hard in recent years, we all know (probably personally) how much of an impact these attacks can have on organizations and the people who use their services.
Although these are all examples of attacks on large enterprise companies, which we have seen a lot of in our tenure working with DDoS, there has been an evolution occurring toward targeting small and medium-sized businesses. And this is just one example of the change in the tactics, techniques, and procedures (TTPs) used by attackers to orchestrate these blitzes.
One of the other most pronounced changes we have seen has been the shift from Layer 3 DDoS to Layer 7. DDoS extortion, application assaults, and targeted attacks against internet-facing infrastructure continue to pose a threat to organizations across all industries globally.
Akamai’s vast level of traffic on our infrastructure and years of experience protecting against DDoS attacks allows us to monitor these changes and provide some insights on what we have seen. While this is a global, cross-industry threat, for the purposes of this post we will focus on the financial services industry (FinServ) as these new developments have been observed first and most prominently there.
What has changed in DDoS and why it’s successful
To understand why these threat actors are successful, we have to examine how they are doing it. Ultimately, it comes down to motivation, persistence, and highly sophisticated TTPs such as:
Nonspoofed packets
One of the most troubling evolutions is that these attacking resources use nonspoofed packets, as opposed to what we have encountered in the past. These attacks are coming from completely valid network handshakes and request a valid protocol resource (Path, URI, URL, file). Commonly attacked protocols are HTTP, HTTPS, API services, and any other application protocol like DNS.
Multi-vector and smokescreen attacks
Multi-vector DDoS attacks are not just about how many different DDoS attack signatures are used to bring down resources. These other attack TTPs are “smokescreen” events happening at the same time. These attacks are intended to detract an organization from the real objective, such as data exfiltration or command and control malware implementation. These are highly sophisticated and often difficult to detect, much less mitigate, as the multi-vector approach is intended to seem unrelated to the other aspects of the attack. We see this a lot with short duration/burst attacks, as well as with horizontal attacks on multiple IP endpoints.
The human element
All of these evolutions are also supported largely by how humans have evolved their internet behavior. Layer 7 DDoS attacks are difficult to detect because it can be difficult to differentiate legitimate human behavior from bot activity on these web-facing applications. We see this on social media platforms all the time, particularly Twitter, where even a trained eye might not be able to determine a bot from a human, depending on subject matter and the sophistication of the bot.
The state of DDoS attacks today: Layer 7
Akamai has been observing a significant increase in Layer 7 DDoS attacks, both in number and scale, despite them being more difficult and more expensive to execute than other types of DDoS attacks. Although it might seem odd for an attacker to try something that will undoubtedly have a more difficult path to success, the potential impact of these attacks is more notable — and public — than the impact of other types of attacks. We, as an industry, are still talking and writing about the 2016 DynDNS attack because of how public it was and how many people were affected.
These evolutions also speak to the motivations of DDoS attackers and how they differ from attackers who use threat types. These attackers are looking to affect the businesses themselves, rather than focusing solely on financial gains as would a ransomware group or phishing kit . The targets of DDoS attackers are specifically chosen and executed against. This isn’t to say compensation isn’t a factor, it simply isn’t the primary motivation. These attacks are more personal; sometimes, they’re even politically motivated.
Despite this, FinServ is still experiencing the most constant barrage of these attacks because of the nature of their business. The high financial stakes and abundance of sensitive data and customer personally identifiable information they hold are highly enticing to an attacker. Adding geopolitical tensions and more complex, vulnerable hybrid infrastructure into the mix, the FinServ industry has to be operating at a heightened level of readiness and incident response, as is teased in FS-ISAC’s “Navigating Cyber 2022” report.
Observations
Akamai has been researching, engineering, managing, and mitigating DDoS attacks for customers since 2003. Because of this, we have a vast and unique amount of data to analyze. Let’s begin with our overall observations in the network-layer space. Figure 1 shows the number of network-layer DDoS attacks in Q1 and Q2 2022 against FinServ.
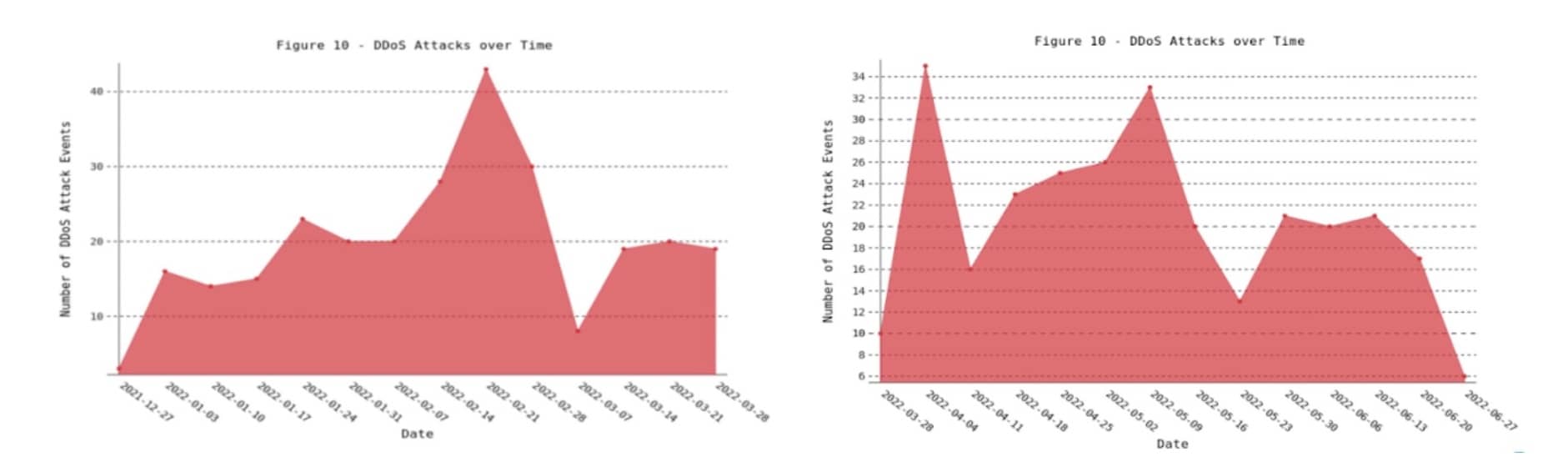 Fig. 1: Network-layer DDoS attacks against FinServ (Q1 and Q2 2022)
Fig. 1: Network-layer DDoS attacks against FinServ (Q1 and Q2 2022)
In Q1 and Q2 2022:
- 564 DDoS attack events were detected/mitigated against 149 customer data center(s).
- The most frequent attack vector was a DNS flood (35%). Other vectors observed were PSH ACK flood, UDP flood, and UDP fragment attacks.
- The largest DDoS attack in peak bandwidth was 627.49 Gbps.
- The largest DDoS attack in peak throughput was 99.79 Mpps.
On the application-layer side, Figure 2 shows the overall attack trends since November 2021, with a significant uptick in early July 2022. As you can see, the spikes are drastically different in July than in the rest of the year, which relates to the point earlier about these being highly targeted attacks.
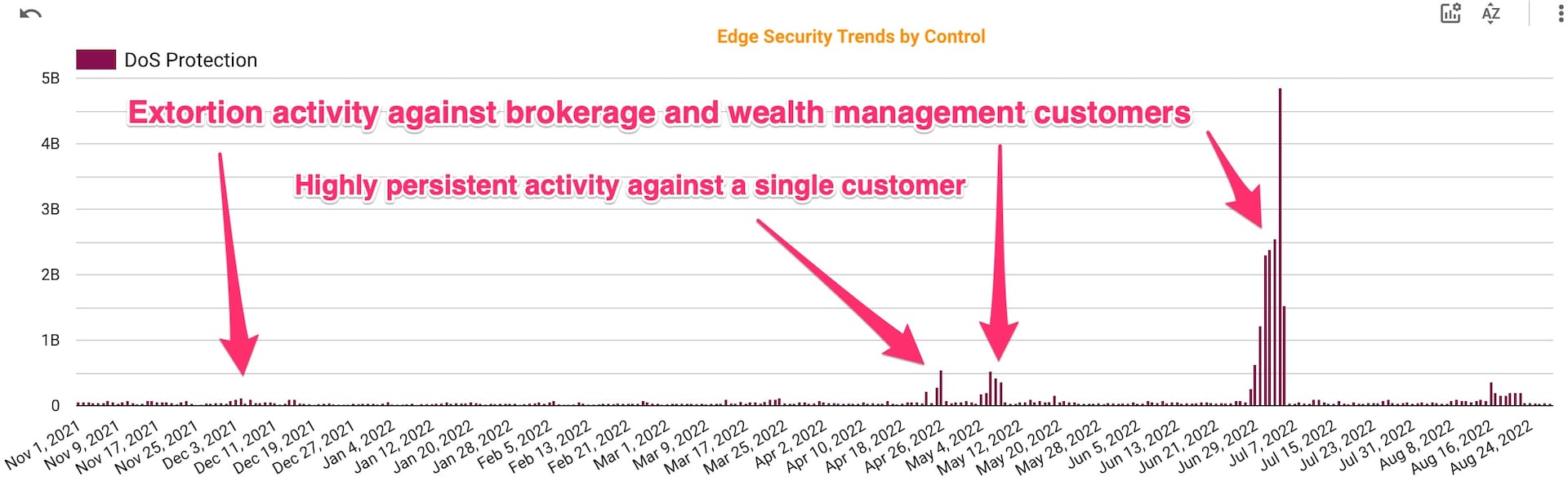 Fig. 2: Overall attack trends on the application-layer side
Fig. 2: Overall attack trends on the application-layer side
DDoS and extortion
Starting in November 2021, a segment of our brokerage and wealth management customers experienced extortion-style DDoS attacks against their applications (Figure 3).
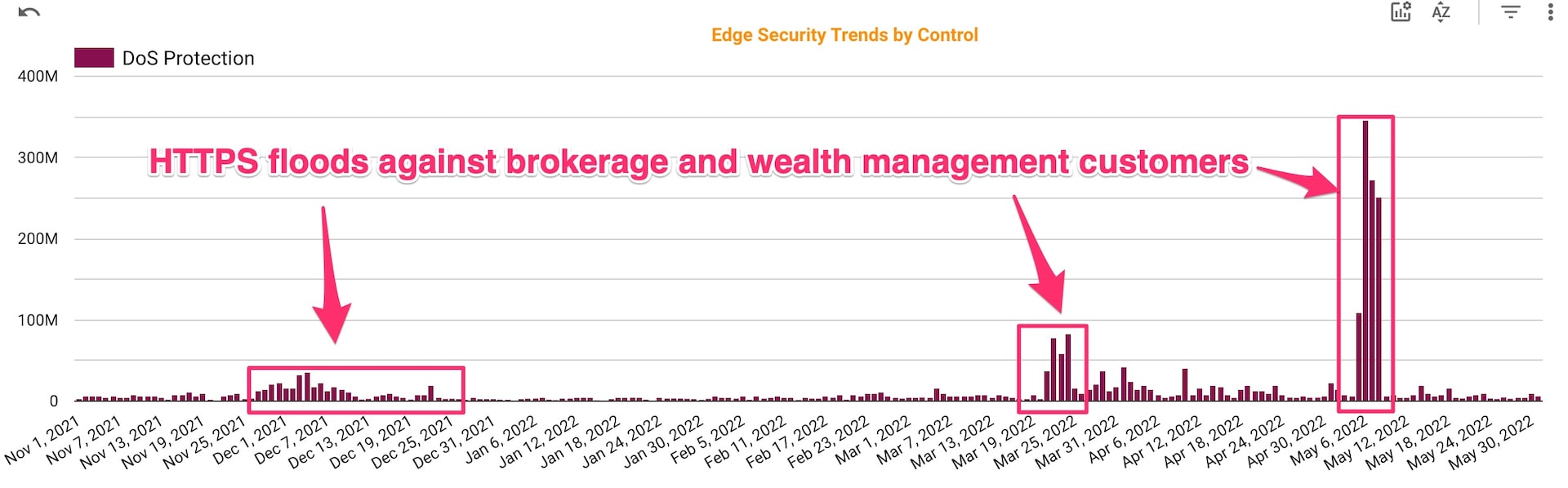 Fig. 3: Extortion-style attacks on brokerage and wealth management (November 2021 – May 2022)
Fig. 3: Extortion-style attacks on brokerage and wealth management (November 2021 – May 2022)
These attacks targeted specific customers in this subvertical with the intention of influencing their investment behavior, in a similar fashion to the bandwidth.com incident in 2021. If a company doesn’t comply with the extortion demands, the attackers go after the customers and investors of the original target to apply more pressure. However, if we move the graph right by adding activity in June and July 2022 (Figure 4), we see the activity returned, but was focused on a single customer at a much larger volume, about 10 to 20 times more than previous attacks against the entire subvertical.
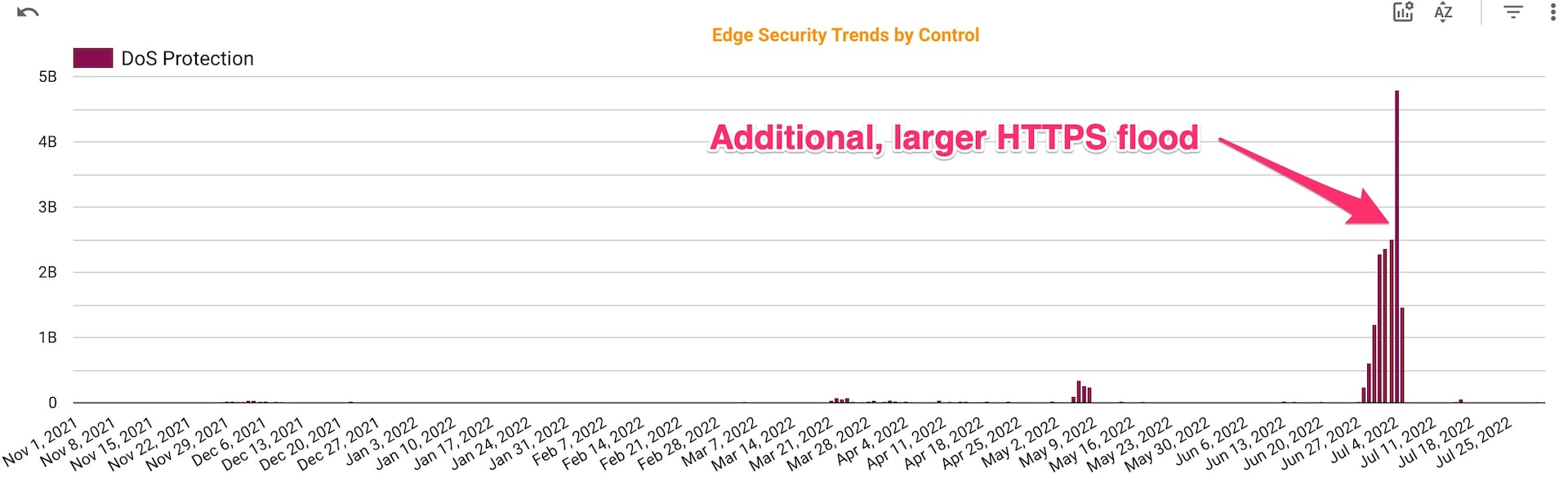 Fig. 4: Extortion-style attacks on brokerage and wealth management (November 2021 – July 2022)
Fig. 4: Extortion-style attacks on brokerage and wealth management (November 2021 – July 2022)
Also, during this late June attack, we observed a DNS query flood against one of the customer’s DNS zones in tandem with the HTTPS flood (Figure 5).
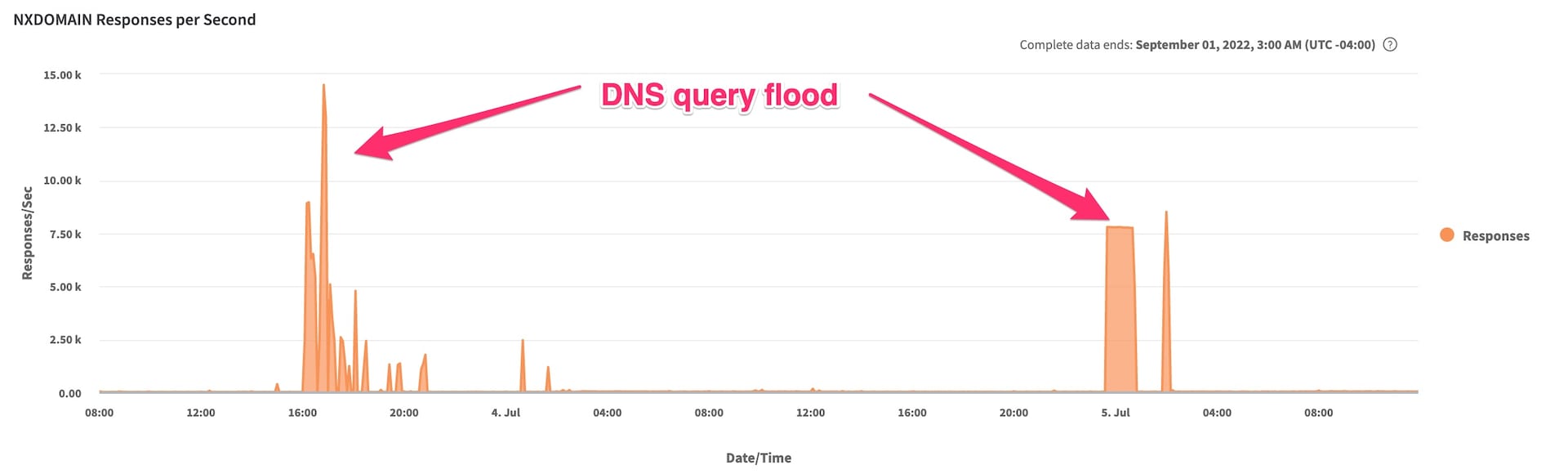 Fig. 5: DNS query flood (June 2022)
Fig. 5: DNS query flood (June 2022)
Persistence and resistance
Next, we’ll focus on an attack that targeted a different FinServ customer in April 2022. This was a multi-vector attack that started as an approximately 600 Mbps DNS flood directly against the customer’s data center. Once that activity was mitigated, the attack shifted to a HTTPS flood.
This activity used a highly distributed set of source IPs that changed tactics as defenses were applied, such as shifting and/or increasing the distribution of the source IPs. As shown in Figure 6, the attack continued over the course of several days in late April, with follow-up bursts occurring in early May.
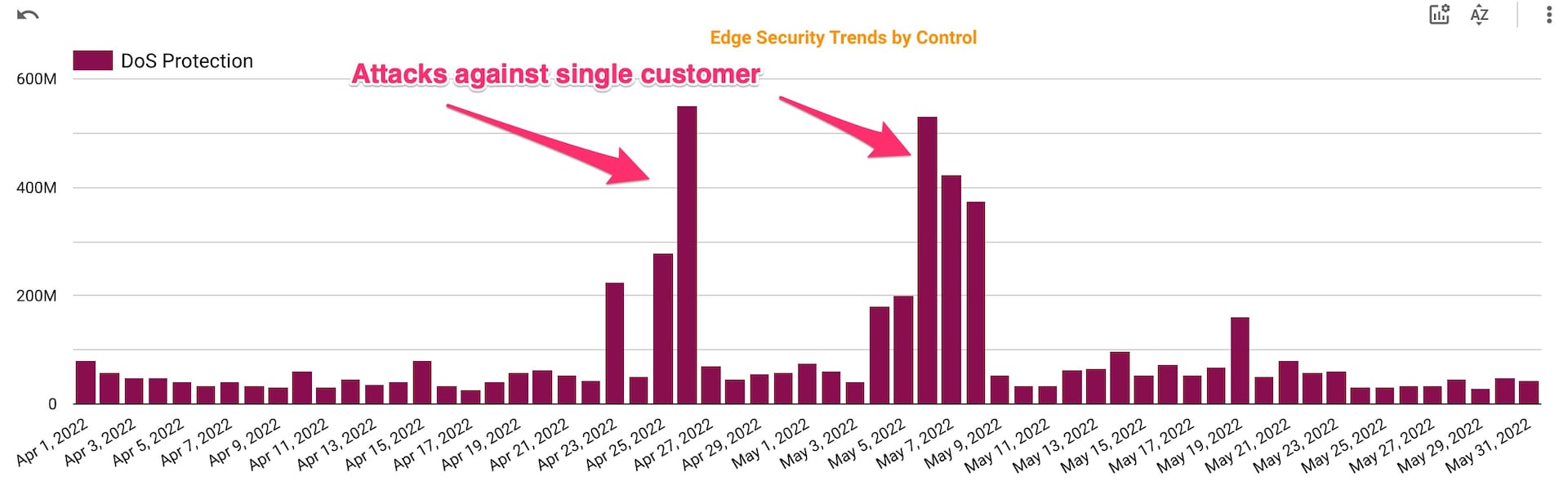 Fig. 6: A multi-vector attack on a FinServ customer
Fig. 6: A multi-vector attack on a FinServ customer
These were the first observed instances of activity coming from these source IPs, so such an attack would have incurred significant cost to the attackers since the source IPs could not be re-used in a future attack. This supports the idea that monetary gain is not the main purpose of the attack here.
Preparedness and posture
DDoS preparedness is based around an “always-on” mentality. Because of the shift to more Layer 7 DDoS attacks and the new TTPs outlined above, we have to look at mitigation a bit differently than we have in the past. Layer 7 attacks require much more of a hands-on-keyboard defense, as opposed to some of the more automated defenses that could be taken with traditional Layer 3 DDoS attacks. They require much more fine-tuning of rate controls, as well.
Based on our observations, we conclude that:
- Attacks are evolving from single-vector to multi-vector.
- Network-layer attack trends continue, but application-layer attacks are increasing.
- You should perform an evaluation of your business critical applications and their respective attack surfaces, then approach your defensive strategy with an always-on mentality that proactively mitigates risk as much as possible.
- You should ensure that controls (such as rate controls, client reputation, and network lists) are in mitigation mode.
- Due to recent DNS flood attacks, you should onboard critical DNS zones to Edge DNS.
- You should keep your runbooks up-to-date and be sure you’ve done a tabletop exercise against your incident response plan.
Under attack?
If you are currently under attack or threat of extortion, reach out to the Akamai DDoS hotline for immediate assistance: 1-877-425-2624. Additionally, if you receive an extortion email, please contact local law enforcement. To keep up with the latest research from our team, follow @Akamai_Research on Twitter.



