Address the Challenges of Compliance and Cybersecurity with Zero Trust
Executive summary
Compliance and cybersecurity are business-critical priorities for businesses in virtually every industry.
While most organizations have separate security and compliance teams, there’s a great deal of overlap in the objectives, practices, and technology for each area.
Regulatory requirements in financial services, for example, involve specific security practices to protect cardholder data, and healthcare regulations stipulate certain security measures to protect patient health information (PHI).
Compliance often requires organizations to defend against cyberthreats through continuous monitoring, deep visibility, and strong access control for internal and external users — which are all part of a robust cybersecurity posture as well.
This intersection of compliance and cybersecurity is an opportunity for organizations to adopt solutions that simultaneously solve challenges in both areas.
Implementing a Zero Trust security framework along with microsegmentation technology can help address compliance and cybersecurity challenges with a number of benefits.
Regulatory environments with cybersecurity requirements
Many of the largest and most common regulatory frameworks have cybersecurity compliance aspects:
NIST. The National Institute of Standards and Technology (NIST) has developed a cybersecurity framework that provides guidance for private sector organizations. Organizations seeking federal contracts or operating in regulated federal environments are often required to comply with NIST cybersecurity standards.
ISO 27001. ISO/IEC 27001 is an international standard for information security management systems that helps organizations protect the confidentiality, integrity, and availability of information. It was published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). Many organizations worldwide seek an ISO 27001 certification to demonstrate to customers, partners, and other stakeholders that they follow best practices for information security.
PCI DSS. Many financial institutions adhere to compliance requirements set out by the Payment Card Industry Data Security Standard (PCI DSS). This cybersecurity compliance program governs how businesses accept, handle, transmit, and store customer credit card data and other financial information.
HIPAA. Providers in the healthcare industry are required to meet extensive and rigorous security requirements established by the Health Insurance Portability and Accountability Act (HIPAA). Among other items, this regulation requires organizations to maintain data encryption, privacy controls, risk assessment practices, and administrative and physical security practices.
FISMA. Federal agencies and affiliated partners are incentivized to follow the practices and mandates of the Federal Information Security Modernization Act (FISMA), enacted to enhance computer and network security.
GDPR. The European Union’s General Data Protection Regulation (GDPR) governs the collection, use, privacy, portability, and retention of personal data and customer data of EU citizens.
CCPA. Similar to the GDPR, the California Consumer Privacy Act (CCPA) was enacted to enhance privacy rights and consumer protection for residents of California.
SOC 2. The System and Organization Controls (SOC 2) is a security standard created by the American Institute of CPAs. It is a private framework designed to help guide companies in implementing a robust security posture.
Enhancing compliance and cybersecurity through Zero Trust
Organizations can improve compliance and cybersecurity by implementing a Zero Trust security framework along with microsegmentation technology (Figure).
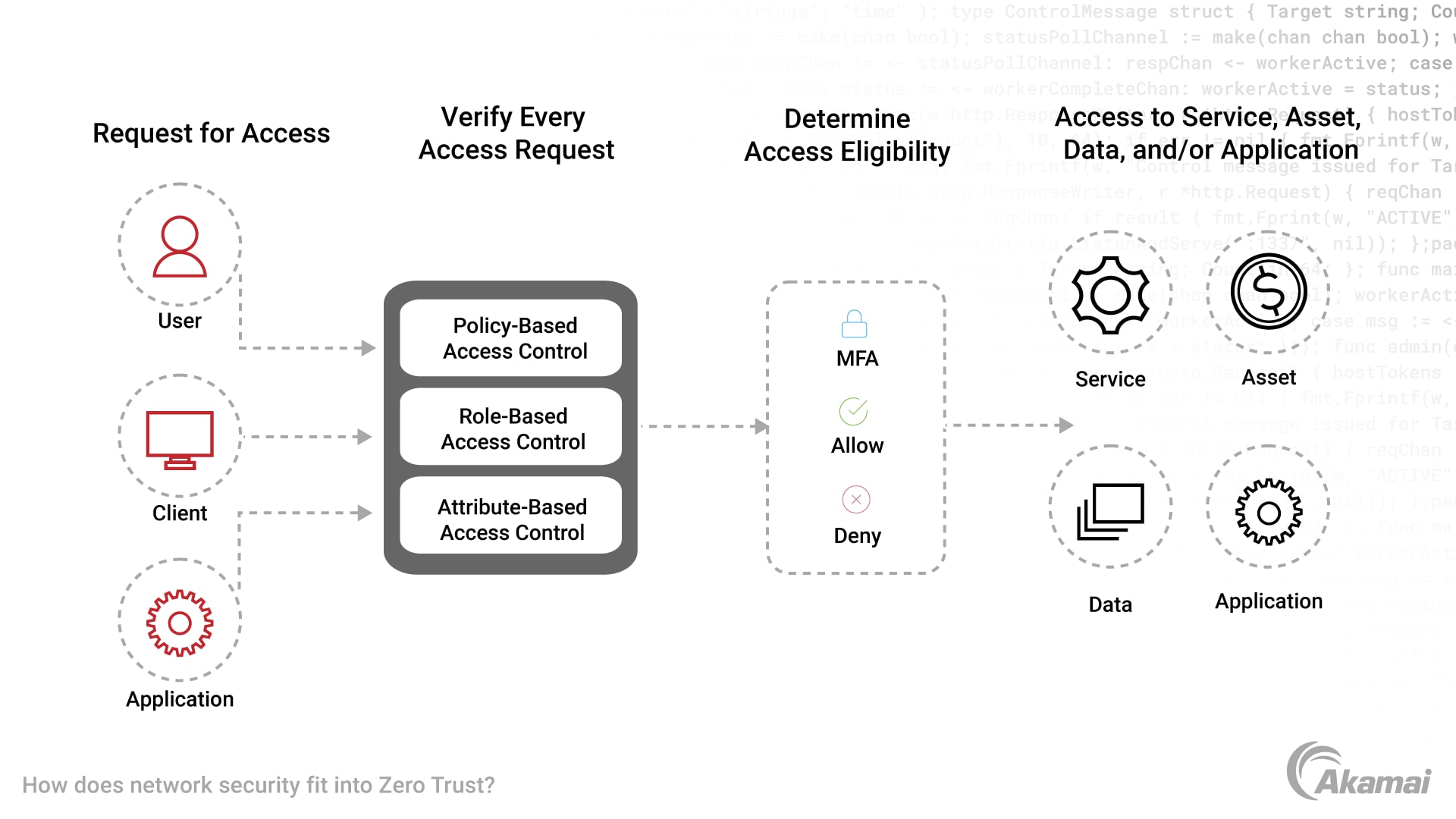
The Zero Trust model is a strategic approach to cybersecurity. It flips the traditional paradigm of cybersecurity in which users, devices, applications inside the corporate network are implicitly trusted. With a Zero Trust approach, users, devices, and applications inside and outside the organization must be authenticated and authorized for every request for access to IT resources.
As remote work, cloud computing, and BYOD make the traditional network perimeter virtually obsolete, Zero Trust security helps stop cybersecurity threats and limit the blast radius of successful cyberattacks.
Benefitting from the principles of Zero Trust
The key principles of Zero Trust can be invaluable for both compliance and cybersecurity programs.
Never trust; always verify
Least-privilege access
Multi-factor authentication
Continuous monitoring
Microsegmentation
Never trust; always verify
Zero Trust security solutions assume that every request for access may be malicious and each request requires constant authentication and authorization. So, it’s important to heed the motto: “Never trust; always verify.”
Least-privilege access
Under a Zero Trust framework, the scope and duration of access is minimized as much as possible. Least-privilege access prevents users with permission to access certain resources from accessing other parts of the network.
Multi-factor authentication
A Zero Trust approach requires strong identity and access management for users and devices. Multi-factor authentication supports Zero Trust by requiring users to provide at least two forms of identification, including passwords, one-time passwords, biometric scans, tokens, and other forms of verification.
Continuous monitoring
Rather than responding to attacks after the fact, Zero Trust frameworks continuously monitor the security posture and configuration of networks and devices to search for any signs of data breaches, enabling faster mitigation and incident response.
Microsegmentation
Microsegmentation segments a network into smaller parts — including individual workloads, virtual machines, applications, and operating systems — so that security teams can implement custom security policies for each area that limit the types of east-west traffic across servers and applications.
This granular approach provides greater visibility into potentially malicious traffic inside the network, blocks attacks based on lateral movement, and helps security teams quickly identify potentially suspicious behavior that could signal an attack.
Benefits of Zero Trust and microsegmentation for compliance and cybersecurity
Zero Trust and microsegmentation offer significant benefits for compliance and cybersecurity.
Data security and data privacy. Many regulatory frameworks require robust data-protection measures. Zero Trust and microsegmentation support compliance by enabling access to sensitive data to be tightly controlled and monitored.
Strong access control. A Zero Trust architecture enforces the strong authentication and authorization protocols required by many compliance regulations.
Continuous monitoring and reporting. Zero Trust networks continually monitor and log access and activities and help identify and respond to security incidents faster — a key requirement of regulatory compliance.
Risk management. Zero Trust and microsegmentation identify and mitigate risks by continuously validating every aspect of digital interactions and by proactively complying with regulatory requirements focused on risk assessment and management.
Addressing insider threats. For regulations that require protection against internal threats, the principle of least privilege ensures that every user has access to only the resources required for any task, reducing the risk posed by malicious insiders.
Segmentation of compliance environments. Using microsegmentation to divide network assets into smaller areas of security control, Zero Trust security complies with regulations that require certain data to be isolated from other parts of IT infrastructure.
Vendor and third-party management: Zero Trust principles extend to all users — including vendors and third parties — helping organizations ensure compliance with regulations that require strict control over supply chain security.
Learn more about Akamai solutions for cybersecurity and compliance management.
Why customers choose Akamai
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. Akamai Connected Cloud, a massively distributed edge and cloud platform, puts apps and experiences closer to users and keeps threats farther away.



