Introducing Akamai Hunt to Stop the Most Evasive Threats and Risks

Today, we’re officially launching Akamai Hunt, a unique service for detecting and mitigating hidden and advanced threats that typically evade traditional security defenses.
Capitalizing on the industry-leading Akamai Guardicore Segmentation capabilities and Akamai’s global attack intelligence, our team of expert researchers investigates and remediates anomalous attack behaviors and advanced threats. Hunt is an always-on service that can mitigate while actively alerting customers to attacks and helping them remediate threats.
Hunting the most evasive threats in your network
Acknowledging that breaches can happen in any environment at any time, the Hunt team relentlessly hunts for anomalous attack behavior and advanced threats immediately after the customer has deployed the Akamai Guardicore Segmentation agents.
The team detects tactics such as lateral movement, malware execution, and communication to command and control early in the kill chain so organizations can avoid disaster, even when security controls fail. With Hunt, you are notified of any critical incident detected in your network, and our experts work closely with your team to remediate any compromised asset for a fast response.
Benefits provided by Akamai Hunt
Akamai Hunt provides three main benefits: security, accelerated time to value, and seamlessness.
Security: uncover the most advanced threats everywhere
The team hunts relentlessly across your critical environments, from on-premises data centers to Kubernetes clusters in the cloud.
Accelerated time to value: instantly augment your organization’s security
You can realize the value of Akamai Hunt right after installing the first agent while our team does all the heavy lifting.
Seamlessness: gain expert, always-on threat hunting without any overhead
Akamai Hunt operates as a seamless extension of your security team and alerts you about the events that matter most to your organization. The result is reduced alert fatigue, zero false positives, and minimum disruption to your business. No additional agents or new architecture is required.
Akamai Hunt is the executive arm of Zero Trust
Forrester breaks down Zero Trust into three principles: (1) all entities are untrusted by default, (2) least-privileged access is enforced, and (3) comprehensive security monitoring is implemented. The third pillar — comprehensive security monitoring — is where Hunt plays a major role.
Microsegmentation enforces the first two pillars while Akamai Hunt comprehensively monitors your network to ensure the third pillar is solid.
What makes Hunt unique?
Akamai Hunt is uniquely positioned to provide an unmatched, dataset, immediate impact, tailored threat hunting; and guided mitigation.
Unmatched, unique dataset: Akamai Hunt combines the infrastructure, telemetry, and control of Akamai Guardicore Segmentation with the data that Akamai gathers by delivering much of the world’s internet traffic. Add to this a team of top talent in the areas of threat hunting, security research, algorithms, and analysis, and the result is an outstanding ability to find the most evasive threats across customer networks.
Immediate impact: Hunt is like a switch — once you deploy the agents in your environment, you can turn on the “Hunt switch” and start getting value immediately.
Tailored threat hunting: By continually monitoring your environment for attacks, the Hunt team develops a baseline of your security configurations and can tailor its hunting methods to your specific topology.
- Guided mitigation: Akamai Hunt will not only alert you about detected suspicious activity, but will also assist in the remediation of threats, virtually patching vulnerabilities and hardening IT infrastructure.
The Hunt process
Collect
Hunt collects unique signals from various sources, which generally fall into two buckets: (1) local data coming from hundreds of segmentation deployments including policies, processes, labels, and third-party integrations; and (2) global data sourced from Akamai’s DNS sensors into malicious DNS, IPs, and URLs.
Analyze
The platform applies AI/ML analysis to these multiple sources of telemetry and the collected signals to rapidly detect threats.
Investigate
Our experts investigate each suspicious event to ensure that only high-priority security risks trigger alerts, completely eliminating false positives.
Alert
The team generates a detailed alert on the threat or the risk, including steps for taking action. You get tailored recommendations so you can act fast.
Mitigate
The Hunt team assists in the process of mitigating the threat. Our work is done only when the threat is eliminated.
Customer story: anomaly detection
Detecting anomalies in a customer’s network traffic is no easy task. There are tens of thousands of assets per environment that the team monitors daily, so detecting specific changes within communications patterns of a specific asset requires a lot of expertise.
We’re talking about myriad different protocols, communications, and types of connections — it’s literally like searching for a needle in a haystack. Most important, in this customer’s environment we had no indications of compromise, hashes, or any known malware hunting engines typically rely on.
Collect and analyze
As you can see in the left panel of the figure, we have the baseline traffic of a single asset in one customer’s hectic environment. An anomalous dramatic change in the amount of neighboring communications of this asset triggered an alert from the Hunt detection engine.
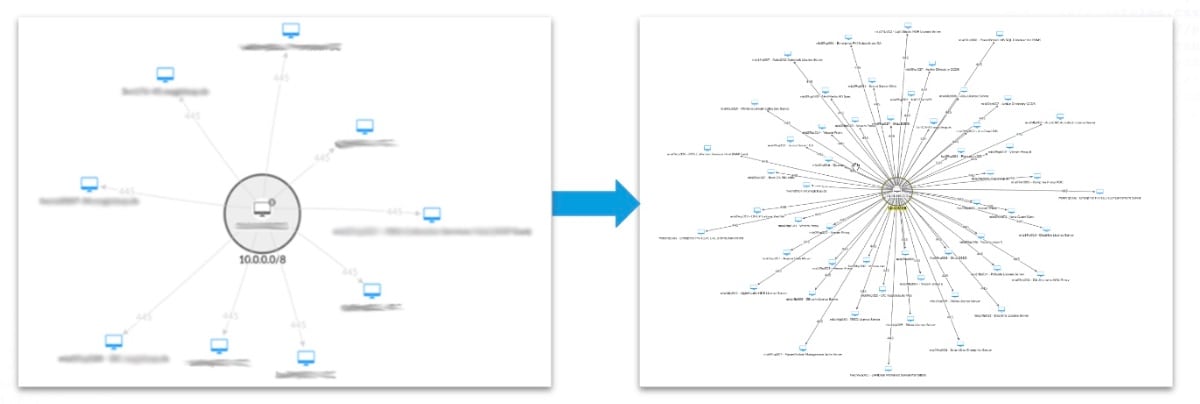 Fig 2: Anomaly detection revealed suspicious change in flows
Fig 2: Anomaly detection revealed suspicious change in flows
Investigate and alert
The team’s investigation found a compromised asset. An attacker was able to exploit a vulnerability in one of the assets’ services, install malware, and was already trying to move laterally across the network. The Hunt team immediately sent a detailed alert to the customer with all the relevant information pertaining to the attack, the traffic changes detected, and a list of mitigation recommendations.
Mitigate
One of the team’s suggestions was to implement a policy in the Akamai Guardicore Segmentation platform that would block any abnormal activity without quarantining or otherwise disrupting the business. The team continued working with the customer until normal communication was restored and the malware removed.
To learn more about Akamai Hunt, visit the Hunt product page.