DNS Threat Report — Q3 2022
Executive summary
Akamai researchers observed that 14% of all protected devices communicated with a malicious destination at least once in Q3 2022.
ֵBreaking down these potentially compromised devices further, 59% of the devices communicated with malware or ransomware domains, 35% communicated with phishing domains, and 6% communicated with command and control (C2) domains.
By examining the brands that are being abused and mimicked by phishing scams we can see that high technology and financial brands led in both the number of campaigns and the number of victims. These leading industry categories abused by phishing are consistent with Q1 2022 results.
Attacks that target financial services customers made up 39.2% of campaigns and 61.6% of victims, indicating phishing attacks against financial services were highly effective in Q3 2022.
Categorizing potential victims as consumers or businesses showed that consumer attacks continue to be more dominant across all quarters in 2022, with 93% of the phishing attack campaigns in Q3 2022.
We tracked 299 unique phishing toolkits that were used on more than one day in the quarter. A total of 53% of these kits were used for at least 5 days, indicating that they continue to be successful.
Further analysis of one of the most reused kits in Q3 2022, which counted the number of different domains used to deliver each kit, showed that kits that abuse Adobe and M&T Bank accounts are top leading toolkits: Adobe with more than 500 domains and M&T Bank with more than 400 domains.
We saw a 40% increase from the first week of Q3 2022 to the last week of Q3 2022 in the amount of DNS over TLS (DoT) traffic. This came with an increase of 23% in the number of customers adopting the usage of DoT to encrypt DNS communication between remotely connected devices.
We believe that the increase in adoption in DoT is mainly caused by the enablement of remote working over the past couple of years and the adoption of the Zero Trust and secure access server edge (SASE) architectures that support remote work.
Introduction
As part of our continuing efforts to enable our customers to be more secure, we present findings on threats from our extensive DNS data. Our insights are based on this visibility into global traffic from our carrier and enterprise security services across various industries and geographies.
For the purposes of this post, we will outline traffic insights, phishing campaigns, and other malicious activity observed in Q3 2022.
Akamai traffic insights
Attacks by category
Based on Akamai’s visibility into carrier and enterprise traffic across different industries and geographies, we can see that, in Q3 2022, 10.6% of monitored devices attempted to reach out at least once to domains that were associated with malware during that quarter. On the other fronts, we can see that 6.3% of devices accessed phishing domains and 0.98% of the devices accessed C2-associated domains.
Comparing 2022 Q3 results with 2022 Q1 and Q2 results (Figure 1), we can see stability across all categories with some increase on the C2 front. Since we are not able to attribute this increase to a specific attack campaign, we are attributing it to seasonal changes in the threat landscape. It’s also possible that the increase be attributed to an increase in vulnerable devices.
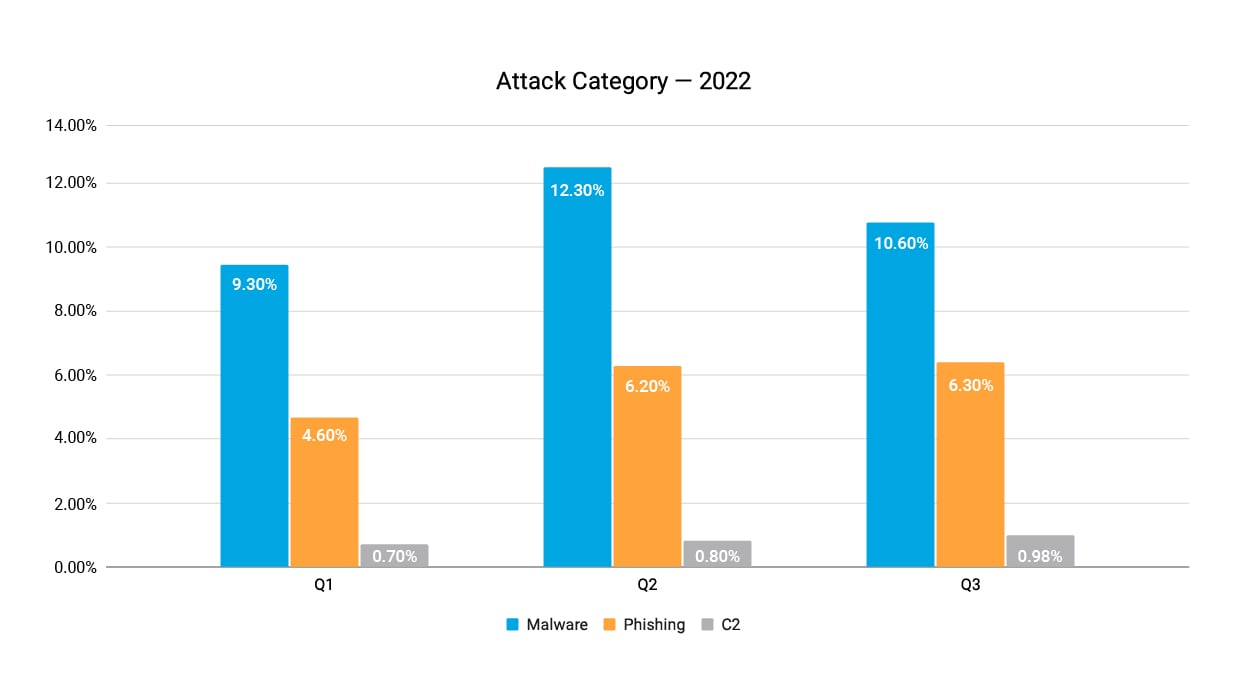
Fig. 1: Devices exposed to threats — 2022
Of the potentially compromised devices and different threat categories, we can see that in Q3 2022, 59% of devices were exposed to threats associated with malware activity, 35% with phishing, and 6% with C2 (Figure 2).
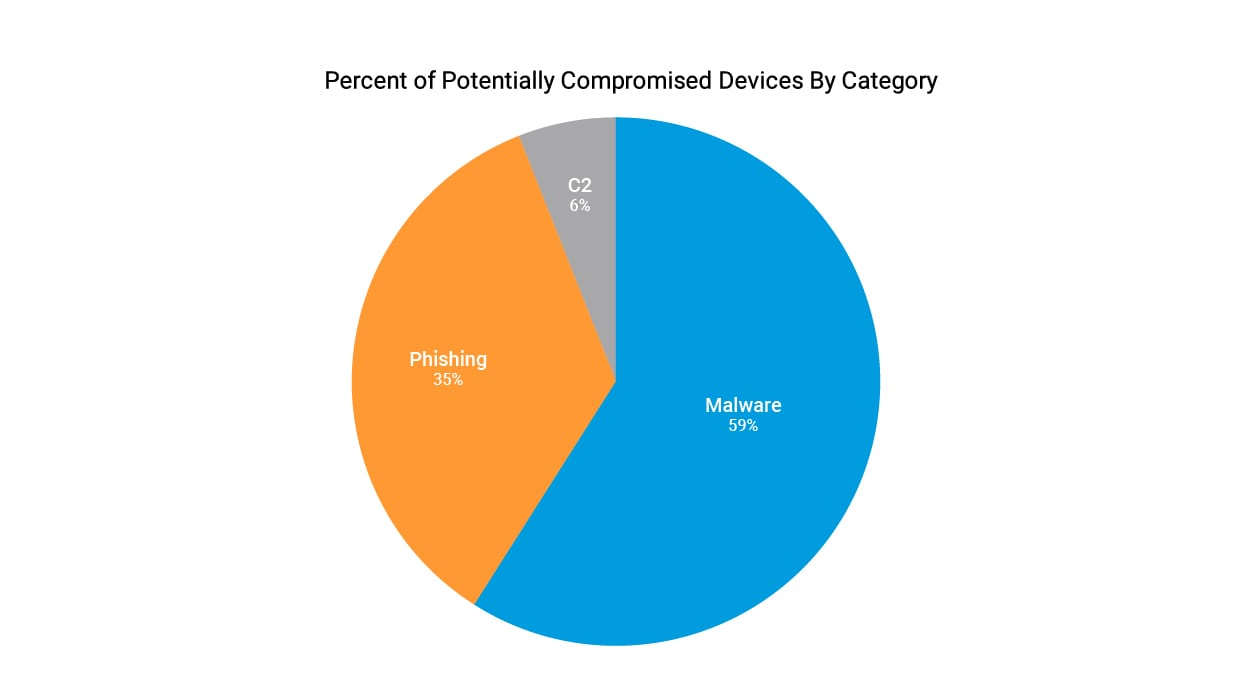
Fig. 2: Potentially compromised devices by category Q3 2022
Phishing attack campaigns
When investigating which brands are being abused and mimicked by phishing scams, there are a number of ways the data can be collected. For the purposes of this post, we collated the total number of campaigns versus the number of victims. This allows us to assess the success rate of a given campaign, as well as see what percentage of each industry is being targeted.
We found that high technology and financial brands led in both the number of campaigns and victims. These leading phishing industry categories are consistent with Q1 2022 results, where high technology and financial brands were also the leading categories.
We also saw 39.2% of campaigns on financial services customers were activated, resulting in 61.6% of victims, indicating that attacks against financial services were highly effective in Q3 (Figure 3).
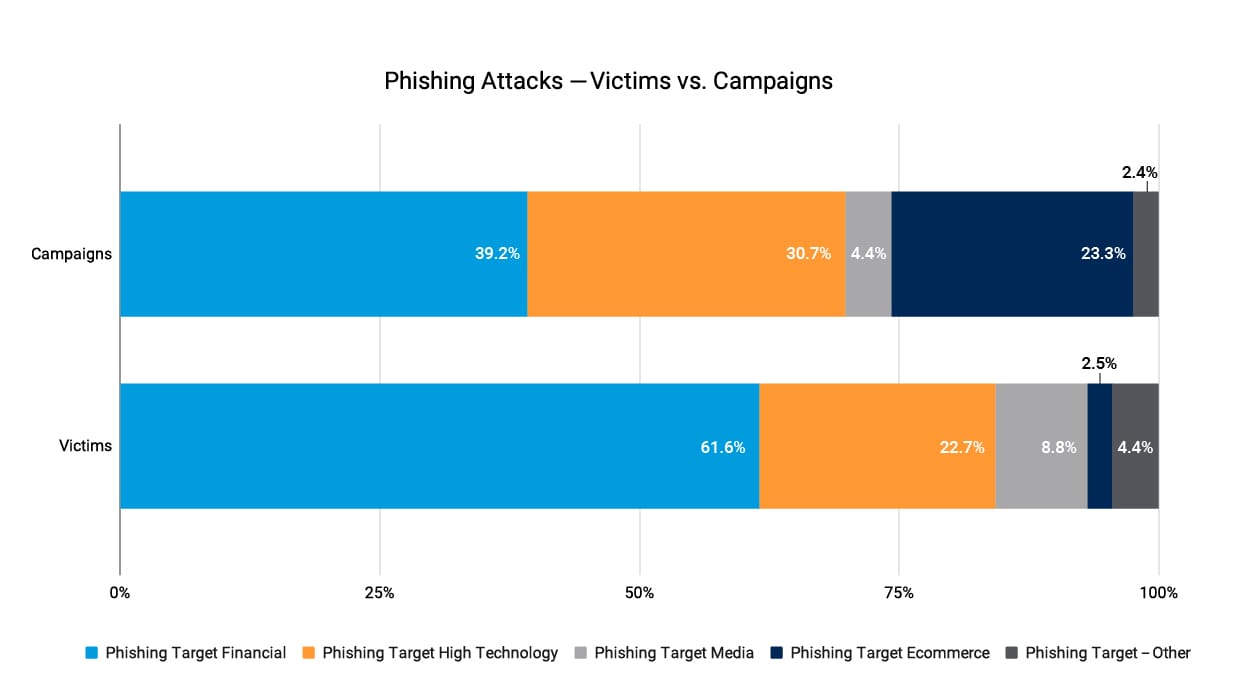
Fig. 3: Phishing victims and phishing campaigns by abused brands
Attackers are targeting more digital commerce brands
Taking a look at phishing attack rates categorized by attack campaigns — consumer- versus business-targeted accounts — we can see an increase in rate between campaigns targeting business accounts and consumer accounts in Q3 2022. We attribute the increase in consumer attacks to more attacks abusing digital commerce brands. Consumer attacks continue to be the most dominant across all 2022 quarters, with 93% of the attack campaigns in Q3 2022 (Figure 4), with an average of 88% across 2022 quarters.
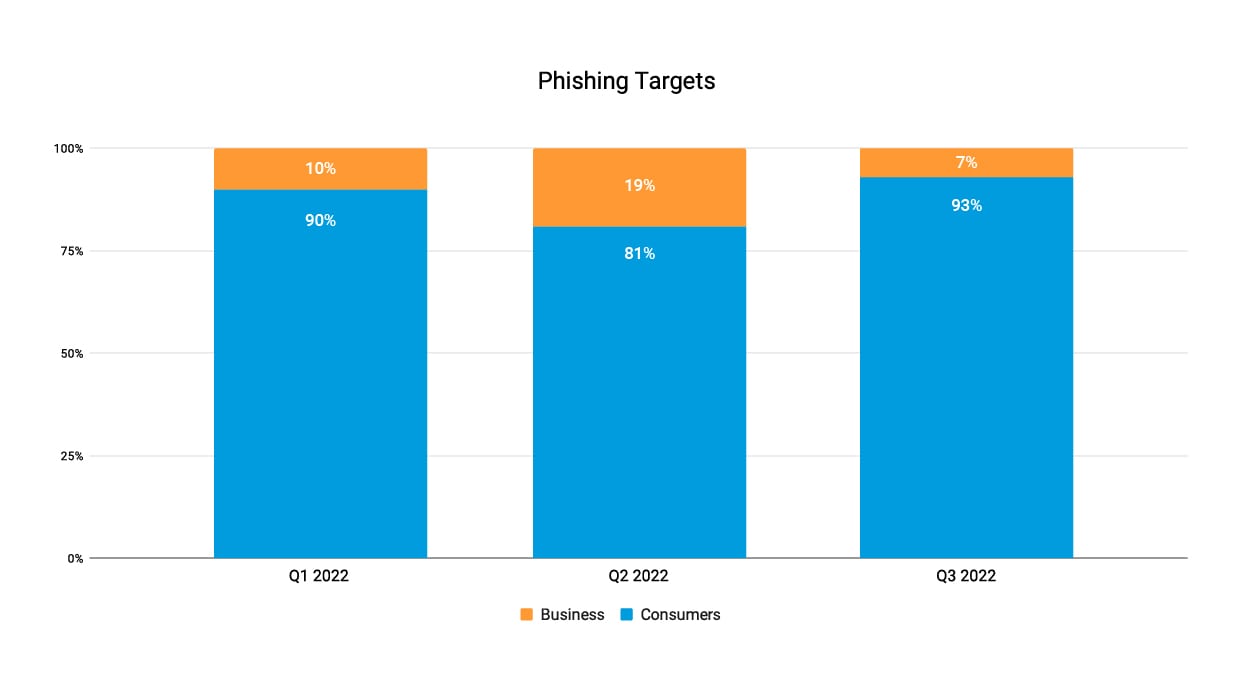
Fig. 4: Phishing targeted accounts 2022 — consumers vs. business
Although the rate of business attacks decreased, it is important to remember the potential damage of attack campaigns against business accounts is big and might lead to the targeted business network being compromised with malware or ransomware, which brings the risk of confidential information being leaked.
Evidence on the potential impact of phishing against a business can be seen in recent details on the Uber hack, which demonstrates how organizations are still vulnerable to phishing and social engineering attacks.
Phishing toolkits
As covered in the Q2 2022 report, the overwhelming phishing landscape scale and magnitude is being enabled by the existence of phishing toolkits. Phishing toolkits support the deployment and maintenance of phishing websites driving even nontechnical scammers to join the phishing adversary landscape and run and execute phishing scams.
According to Akamai research that tracked 299 different phishing toolkits being used in the wild to launch new attack campaigns, in Q3 2022, 2.01% of the tracked kits were reused on at least 63 distinct days (Figure 5). Further, 53.2% of the kits were reused to launch a new attack campaign on at least five days, and 100% of the tracked kits were reused on no fewer than three distinct days over Q3.
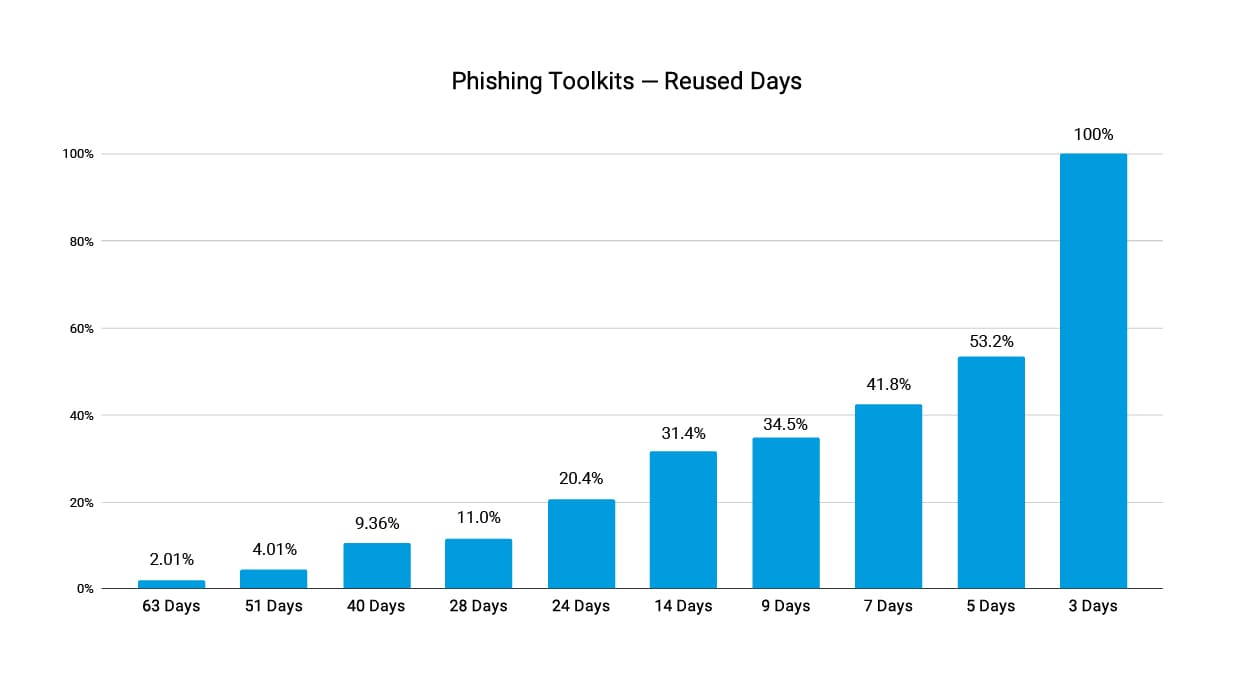
Fig. 5: Phishing toolkits by number of reused days Q3 2022
The average toolkit was reused on 9 days in Q3 2022, compared with the average toolkit being reused over 8 days of Q2 2022.
Further analysis on one of the most reused kits in Q3 2022, counting the number of different domains used to deliver each kit, shows that kits that abuse Adobe and M&T Bank are top leading toolkits: Adobe with more than 500 domains and M&T Bank with more than 400 domains (Figure 6).
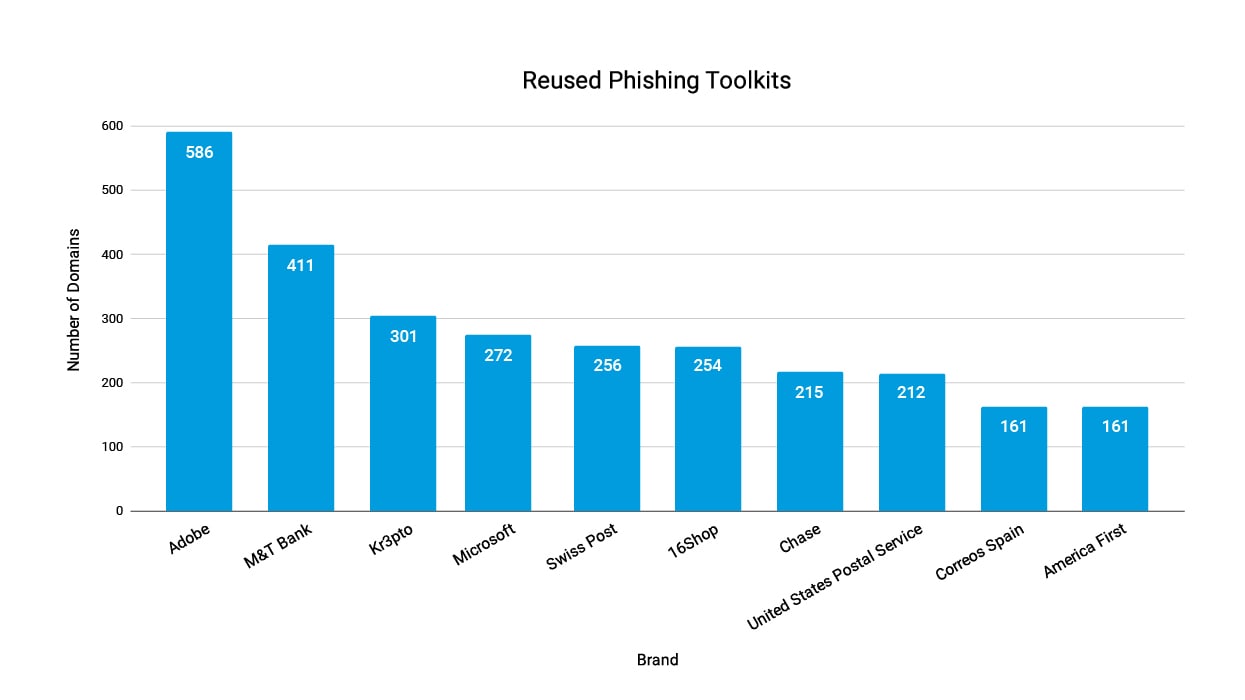
Fig. 6: Top 10 reused phishing toolkits
The reusing behavior of phishing toolkits described above is more evidence of the trend of the phishing landscape that continues to scale, moving to a phishing-as-a-service model and utilizing internet free services. Phishing attacks are still as relevant as ever, knocking on our door seeking engagement when we are most vulnerable.
DNS over TLS adoption trends
Via Akamai research into the adoption and usage of DoT, we were able to see a continuous increase in the adoption rate of DoT in our enterprise and small and medium-sized business customers. DoT value is in the usage of TLS on top of DNS protocol, bringing security and privacy to DNS communication and making sure there is no visibility of DNS transactions. We saw a 40% increase from the first week of Q3 2022 to the last week of Q3 2022 in the amount of DoT traffic (Figure 7). This comes with an increase of 23% in the number of customers adopting the usage of DoT to encrypt DNS communication between remotely connected devices.
As DNS transactions are being transferred in plain text, DoT helps to prevent attacks that sniff DNS traffic resulting in exposure of sensitive information and attacks that manipulate DNS traffic via machine-in-the-middle techniques.
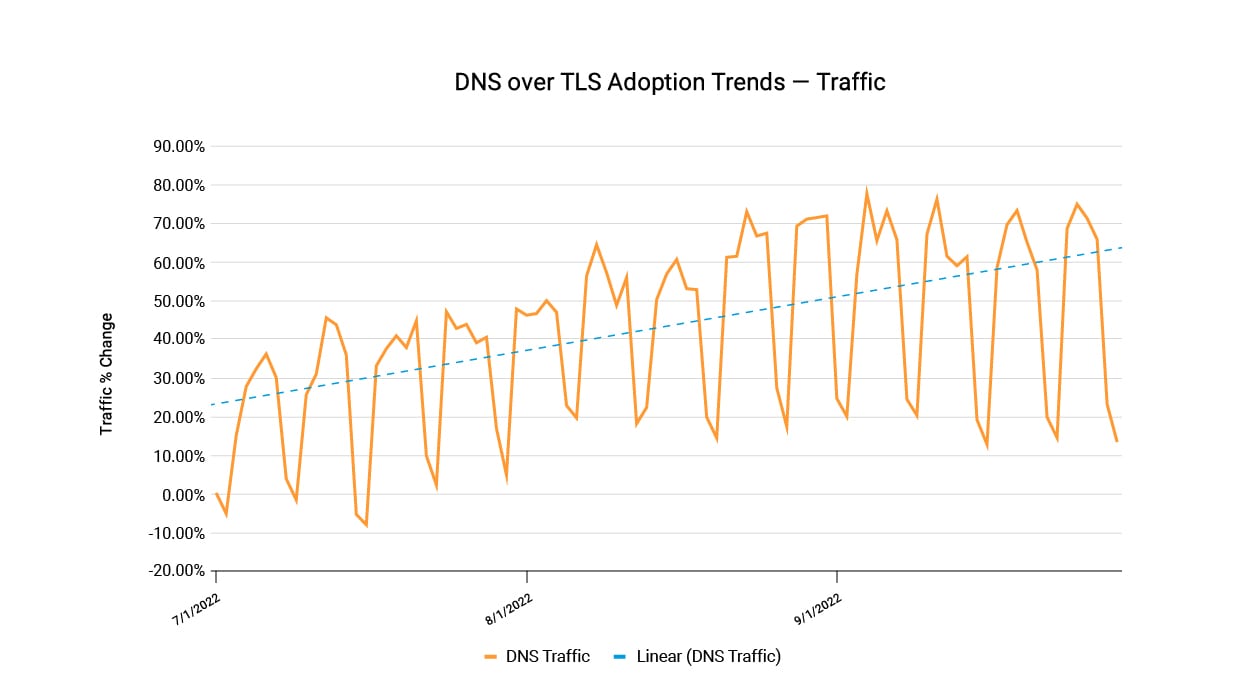
Fig. 7: Adoption trends of DoT (Q3 2022)
We believe that the increase in adoption in DoT is mainly derived from the enablement of remote working over the past couple of years and the adoption of the Zero Trust and SASE architectures that support remote work. Distributed workforce leads to higher risk as connecting devices are roaming across mobile networks on public and home routers, some of which may be vulnerable or compromised and may lead to more sniffing and machine-in-the-middle attacks.
Conclusion
As more and more of our lives and businesses become digital, cyberthreats are more impactful. Because so much traffic is seen on our sensors, it is necessary to analyze and disseminate that information responsibly. To be mindful of what is possible tomorrow, we have to look at what happened yesterday. This is precisely why we continue to do these reports.
With the holidays coming up, phishing is going to be in peak season. We are seeing these phishing kits being reused, which is troublesome — not only are they succeeding the first time, but they are also continuing to take victims. Remain vigilant throughout the holidays and beyond because these toolkits are getting more and more sophisticated.
Akamai researchers are continuously monitoring these and other threats to inform and educate the community. For more pieces like this and other cutting-edge security research, be sure to follow us on Twitter.



