Cryptominers’ Anatomy: Cryptomining Internals
Cryptominers, or cryptojackers, are a type of malware that exploits the victim's resources for profit by mining cryptocurrency. In contrast to the usual use of cryptocurrency by attackers as a payment method, cryptominers use the fundamental base of the cryptocurrency, which is the blockchain mining operation, to generate financial gain.
Cryptocurrency was originally designed as a borderless, decentralized way to transfer money and detach from traditional banking systems. Since the first appearance of bitcoin, many other cryptocoins and crypto-based tokens have been created. Every token is based on a theme or set of features that distinguishes it from others. For example, the Monero coin aims for total privacy and prevents transaction tracking while ensuring integrity, while meme coins like Dogecoin are more sentimental than practical.
As attackers seek to profit while ensuring their anonymity, cryptocurrencies are a lucrative option — they allow threat actors to use their crypto funds with minimal risk of identification by law-enforcement. The most direct way to achieve financial gain without identification is by mining privacy-oriented cryptocurrencies, which give the attackers immediate profit without revealing themselves to the victim (and will also mask any transactions using that profit).
In this three-part blog series, we’ll take a deep dive into the world of cryptocurrencies and cryptominers. The first post (this one) deals with cryptocurrency fundamentals, including how blockchain technology and mining works in general. It also covers the attacker mindset of choosing a mineable coin that will fulfill its requirements for privacy and efficiency.
Part 2 of this series addresses cryptominers, specifically malicious ones that we found. We’ll examine some cryptominer statistics, their profits, and how they operate and infect their victims. The third and final post in the series covers defense techniques — how we can detect cryptominers, mitigate their impact, and fight back to prevent attacks from generating any profit.
Cryptominers’ impact on the world
Cryptominers have impacted the world since 2013, when a video games company allegedly exploited customers' machines to mine bitcoin. More than 10 years later, the threat has grown to an enormous scale and cryptominers are now a substantial piece of worldwide cybercrime.
Many case studies of cryptominers have been published over the years: from the WannaMine botnet in 2017 to the recent Migo campaign that targeted Redis to variants of cloud-specific and browser-mining scripts. In recent years, we at Akamai have uncovered a few cryptomining botnets ourselves, like Panchan and NoaBot.
Attack volume
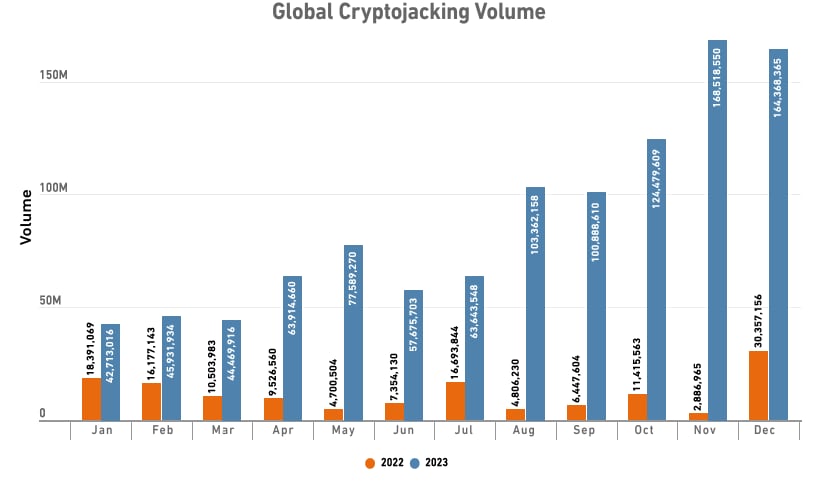
More attackers seem to shift their attention to cryptominers over time. Figure 1 shows that 2023 saw a huge spike in global malicious cryptomining activity. And this trend continued in 2024. Despite the explosive growth, analysis reports have not noted significant changes to cryptominers’ behavior. The typical cryptominer in 2024 acts very similarly to its predecessors from 10 years ago; that is, highly noisy, nontargeted attacks, infecting cloud resources and domestic computers to mine privacy-oriented coins.
Cryptominers’ industries and sectors distribution
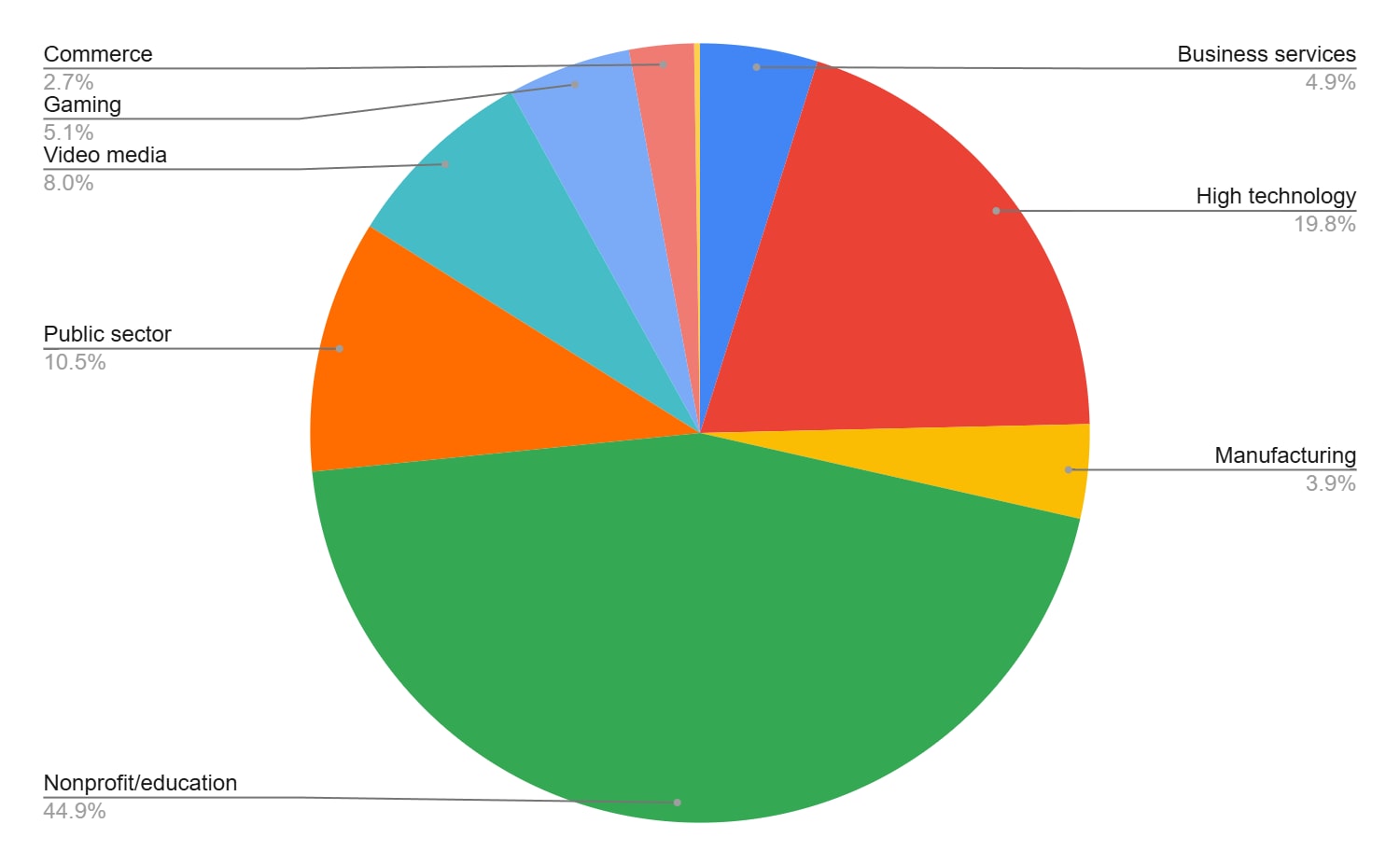
Cryptominers affect a wide variety of industries and sectors. Using Akamai’s unique view of internet traffic, we identified cryptominer communications to public cryptomining pools. Figure 2 shows the distribution of cryptomining traffic over different business sectors.
Higher education institutions are among the most targeted sectors, presumably because of their significant computational resources, which are often unattended.
In the private sector, cryptominers preferentially target industries like cloud and hosting services. These targets provide a great opportunity to attackers, as they allow them to access extensive computational resources while eliminating byproducts in the victim environment, such as substantial noise, heat, and electricity consumption that could potentially lead to their detection.
This type of attack can be financially devastating for victims — in 2022, Sysdig suggested that for every US$1 of cryptominer profit, the victim loses approximately US$53 (Figure 3).
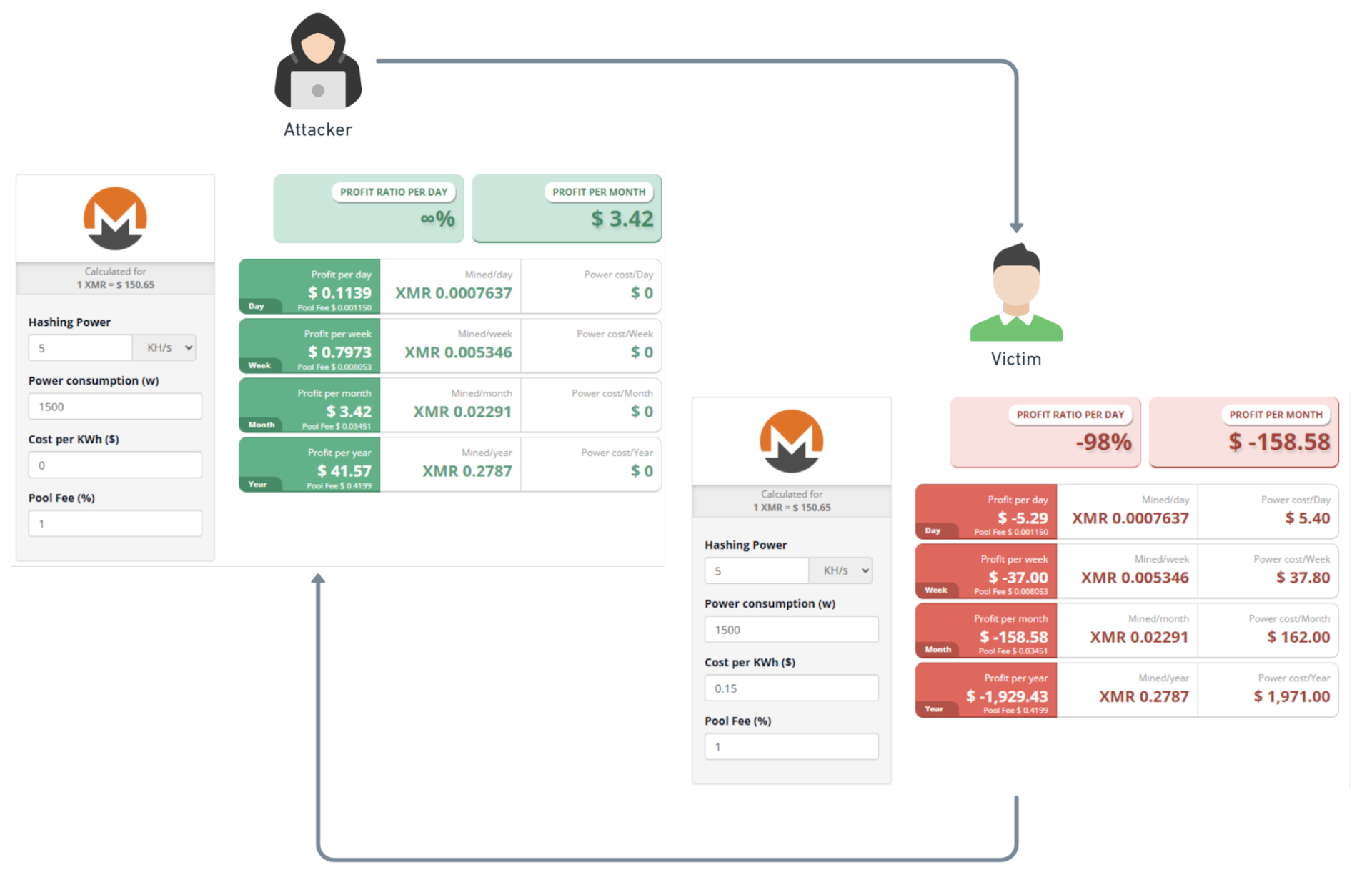 Fig. 3: Attacker profit compared with victim expenses
Fig. 3: Attacker profit compared with victim expenses
Generative AI bring new surface for cryptominers
Another trend that we predict will significantly affect the cryptominer landscape is the recent rise of generative AI. As AI computation is highly reliant on graphics processing units (GPUs), those components are becoming more common in organizational networks and servers. Because many mining algorithms are also designed for GPUs, the underlying computing infrastructure of the AI industry is very attractive for cryptominer operators.
It’s probably just a matter of time before we witness a campaign that targets AI infrastructures either directly through the model interaction or through the training process (or both).
Adversary motivation
Threat actors choose to employ cryptominers for two main reasons:
- Financial
- Privacy
Financial motivation
With the exception of state-sponsored threat actors and hacktivism, most cybercrime is financially motivated. Cryptominers are a simple and direct way to monetize an intrusion without the extra phase of translating the attacker's hold on the network into capital, like ransomware extortion or by selling sensitive data. This makes cryptomining malware an attractive money generator for threat actors.
Other considerations that attackers take into account include cryptocurrency value and mining share rate. If the attacker generates 1 US cent per year, for instance, it is not worth the risk of being arrested. Therefore, one of the attacker's goals is to find a balance between effort and profit, which lets us narrow down the list of potential coins mined by attackers.
During our research, we identified an attacker that seems to be active since at least June 2018 and was able to generate an average revenue of 300 XMR every year. If we calculate their revenue according to the current Monero value (1 XMR $150), we see that they made approximately US$45,000. This is the average revenue of a small business with no employees in the United States in 2024.
Privacy motivation
Privacy is intrinsic to most cryptocurrencies. They employ cryptographic algorithms that preserve privacy and ownership through secret keys paired with corresponding public keys, which serve as wallet addresses. By leveraging this inherent feature of cryptocurrency, along with additional privacy algorithms designed to hide transaction amounts, sender addresses, and receiver addresses, an attacker can almost completely conceal their activities.
As we mentioned, attackers consider several trade-offs when shifting their botnets to mine specific cryptocurrencies. One of these trade-offs concerns the attacker's privacy over profit, because there could be more profitable coins that offer less privacy. Coin privacy is measured through the anonymity it could provide in three aspects:
Communicating with the network; there are coins that rely on privacy network protocols such as Tor or I2P
Protecting transaction information, such as wallet addresses and amounts, to prevent tracing and hide account balances
Enlisting the cryptocurrency in exchange platforms that support privacy
For example, bitcoin lacks transaction privacy, making users vulnerable to monitoring and increasing the risk of deanonymization. This limitation restricts the range of cryptocurrencies that attackers can exploit. Consequently, adversaries remain motivated as long as profitable privacy-focused coins are available.
However, this motivation could decline if privacy coins become unprofitable or if the mining process changes, such as shifting to Proof of Stake (more info below), thereby preventing attackers from easily generating profits through resource-intensive methods.
A motivated attacker has to consider how to execute such a cryptominer campaign, and understanding the fundamentals of the mining process is crucial for that. In the next section, we will overview the mining process to understand where attackers focus their attention, which will help us create better hunting and detection techniques.
Cryptocurrency 101
What is cryptocurrency?
Cryptocurrency is a digital form of currency that leverages cryptographic techniques to secure transactions and control the creation of new units, a.k.a coins or tokens. Unlike traditional currencies (known as fiat money), cryptocurrencies operate on decentralized networks that use blockchain technology — a distributed ledger system maintained by a network of nodes.
Each transaction on the blockchain is recorded in a block and linked to the previous one, creating an immutable chain of records that is nearly impossible to alter without controlling a majority of the network’s computational power. This decentralized nature eliminates the need for intermediaries, such as banks, and offers enhanced security and transparency.
One essential component of the cryptocurrency systems is the wallet, which is a set of cryptography secrets that allow users to transact assets over the blockchain. The wallet is represented by a string of characters in a specific format called an address. Transactions between these addresses are publicly recorded on the blockchain, but the participants' identities remain hidden unless additional information is linked to the address.
More privacy-focused cryptocurrencies, such as Monero or Zcash, take this further by implementing advanced cryptographic techniques like ring signatures, stealth addresses, and zero-knowledge proofs to obscure transaction details, including the sender, receiver, and amount. These features make it challenging for third parties to trace transactions back to specific individuals, offering more privacy and anonymity than traditional financial systems.
Consensus algorithms
To apply new blocks to the blockchain, there must be some ground of truth that everyone agrees on. Using an algorithm family called consensus algorithms and their specialized variants can make decentralized networks operate to validate blockchain transactions. These algorithms are designed to prevent double-spending, maintain the ledger's integrity, and enable trustless transactions between parties.
Different cryptocurrencies use various consensus mechanisms, each with its unique approach to achieving consensus while balancing factors such as security, scalability, and energy efficiency.
Proof-of-Work
The most well-known consensus algorithm is Proof-of-Work (PoW), used by bitcoin and several other cryptocurrencies. In PoW, miners compete to solve complex mathematical puzzles, a process that requires significant computational power. The first miner to solve the puzzle gets the right to add a new block to the blockchain and is rewarded with cryptocurrency.
This process is energy-intensive but provides robust security, as altering the blockchain would require an attacker to control more than 50% of the network's computing power, making such attacks highly impractical.
Proof-of-Stake
Another popular consensus algorithm is Proof-of-Stake (PoS), which is used by cryptocurrencies like Ethereum 2.0 and Cardano. In PoS, validators are chosen to create new blocks based on the number of coins they hold and are willing to stake.
This approach is more energy-efficient than PoW, as it doesn't require extensive computational resources. However, PoS assumes that those with more stake in the network are more incentivized to act honestly.
Cryptominers use PoW ONLY (or Proof-of-Capacity, which isn’t covered in this article) mining algorithms since the attack vector is based on resource hijacking. Hence, from now on, consider PoW in the context of mining.
ASIC-resistant algorithms
There are various types of hardware that are used to calculate the consensus algorithm. A central processing unit (CPU) is a general purpose integrated circuit (IC) that can be used to calculate any consensus algorithm easily, but sometimes not efficiently. This is why some algorithms are designed for a graphics processing unit (GPU) that can handle complex arithmetic more efficiently than the CPU.
Another type of hardware used by miners are the application-specific integrated circuit (ASIC) and the field-programmable gate array (FPGA), which are processing units optimized to perform a specific task. Both of them are excellent with deterministic tasks like calculating sha1 hashing algorithm, but both fail when there is a high memory demand or a high number of possible branches during runtime execution, which depends on previous iteration output.
Most cryptocurrencies rely on decentralization, which is necessary to keep the blockchain secure and reliable. If a network becomes centralized by controlling most of the network nodes or by being the major miner by hashrate, an attacker could perform a 51% attack. To mitigate this, many coins added specialized hashing algorithms that make the ASIC design and production less financially viable.
The algorithms are based on practices that use a general purpose processor to execute memory-hard, complex algorithms designed to work with CPU optimization features. In other words, the algorithm uses large memory address space and as many modern CPU features as possible to make the creation of a dedicated ASIC unviable. Essentially, if someone tries to create an ASIC for such an algorithm, they will end up with a full-blown CPU.
Mining process
The mining process is like a lottery at scale. Every participant gets a job to solve, consisting of block information and nonce. Miners are required to find a nonce that fulfills the network's target difficulty, which is statistically possible in a specific time frame. This time is known as target time and it is achieved by setting a difficulty (d) to the future blocks to keep the mining rate stable and within the target time frame.
Difficulty commonly suggests how many hashes need to be calculated to find a valid hash that satisfies the target (t) value. The target value indicates a supremum for all valid hashes. The way the Monero coin calculates difficulty is to take the number of possible hashes and divide it by the target.
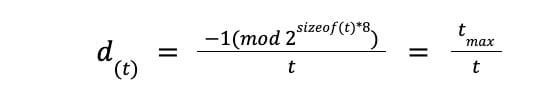
Many coins define their own difficulty calculation, but the result is similar since it should restrain the network hashrate (fhashrate[hashs]). This means if we take the difficulty and divide it by the target time we can get the hashrate of the network.
![Many coins define their own difficulty calculation, but the result is similar since it should restrain the network hashrate (fhashrate[hashs]). This means if we take the difficulty and divide it by the target time we can get the hashrate of the network.](/site/en/images/blog/2024/process-two.jpg)
For example, if t = 0x1F and the size of t is one byte, then the difficulty is 0xFF0x1F = 8. That means it’s statistically possible to find a matching value for every eight hash calculations of random nonce.
After we set a target time for the network to control the blockchain growth rate, we could average the time-per-block finding over n blocks and get the hashrate. Using the hashrate we can set the next difficulty; in some coins, this changes on every block relative to the N last blocks, while other coins change it every constant number of blocks.
Transaction privacy
Bitcoin is the first widely used cryptocurrency that uses blockchain technology to record network transactions. These transactions are stored in plaintext and are publicly accessible to anyone through blockchain explorer services (or manually, if preferred). The anonymity associated with bitcoin is somewhat misleading — although the use of digital wallets is indeed anonymous, interactions with third parties are not.
For example, if someone wants to exchange fiat money (such as the US dollar) for bitcoin, they must disclose their wallet, which leads to deanonymization by linking the identity to the wallet. Attempts to make diversionary transactions to obfuscate identity will ultimately have the same result, as these transactions can be traced until they leave the network via an exchange platform. Deanonymization most often occurs at the points where funds are deposited into or withdrawn from the network.
Privacy-oriented cryptocurrencies emerged because of the need for privacy in several legitimate contexts, such as mitigating the misuse of transaction knowledge. However, privacy can also be abused to conceal criminal activities, which makes privacy-oriented cryptocurrencies a common requirement for cryptominers and other malicious actors.
Today, privacy-oriented coins can hide the sender and recipient addresses, as well as the amounts transacted between them. This level of privacy makes transactions involving illicitly acquired funds untraceable within the network.
Cryptocurrency candidates
By analyzing the capabilities and needs of cybercriminals who operate cryptominers, we can identify a list of cryptocurrencies that meet their requirements. First, cryptominers typically operate at scale and across diverse architectures, making a cross-platform mining implementation essential. This diversity may involve x86, AMD64, ARM, and other CPU architectures.
In many cases, victims will not possess powerful GPUs or mining rigs equipped with ASICs or FPGAs. As a result, the focus shifts to ASIC-resistant algorithms, which are designed to limit mining to common and conventional platforms, such as home computers and similar devices.
Another key aspect that cryptominers rely on is the privacy of the cryptocurrency network. Since cryptominers are considered illegal in most countries, malicious actors must conceal their tracks when attempting to launder the stolen funds.
These considerations allow us to highlight the requisites for choosing a cryptominer’s coin:
- Cross-platform architecture
- ASIC-resistant mining algorithm
- High and sustainable profit
- Privacy-oriented coin that supports untraceable transaction
- Lightweight mining algorithm implementation
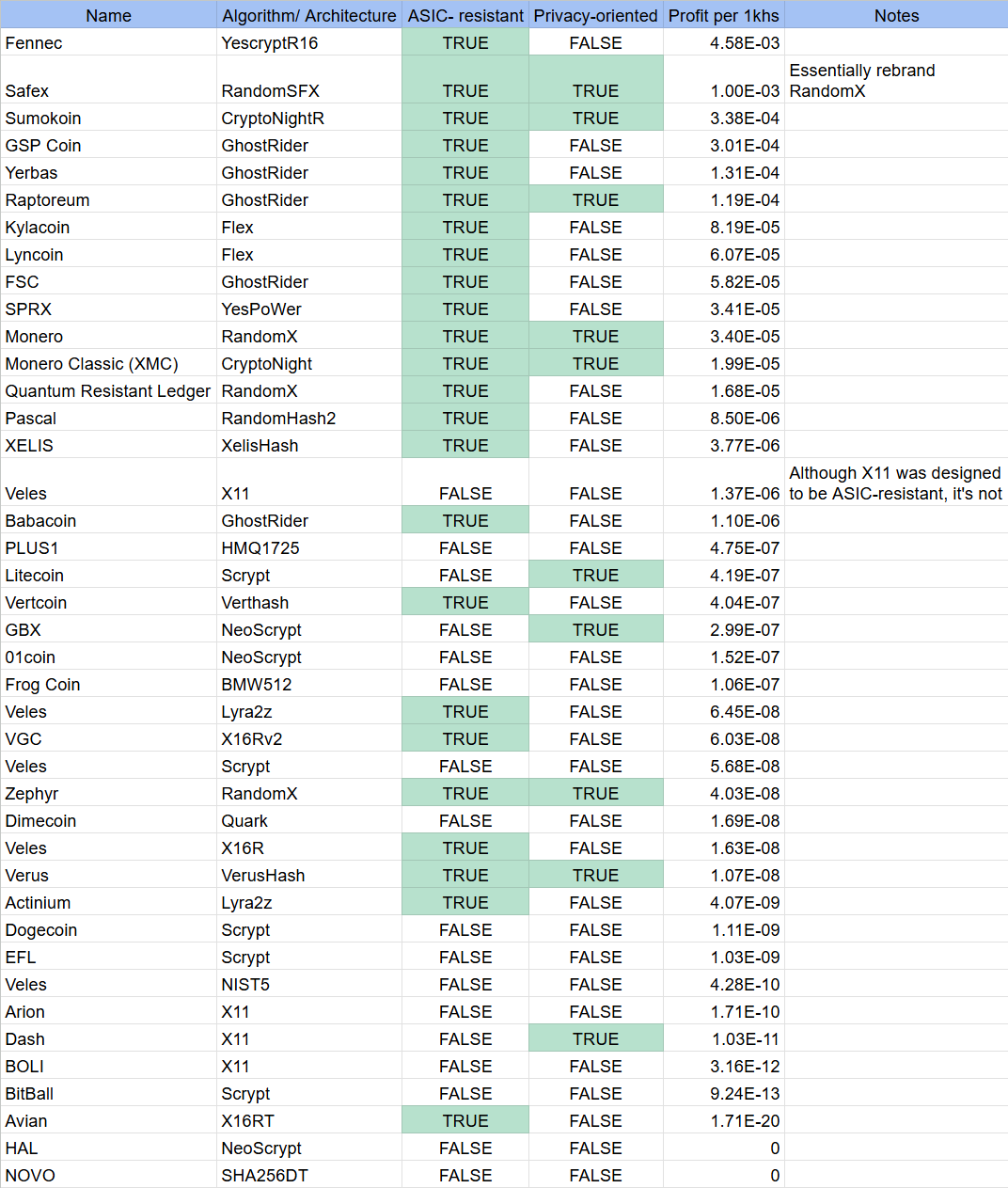
Table 1 contains a short list of the most relevant coins according to the above assumptions. This list focuses on ASIC-resistant and privacy-oriented coins, as well as the number of crypto exchanges that are currently listing them. (See Appendix A for the full list of potential cryptominers’ coins.)
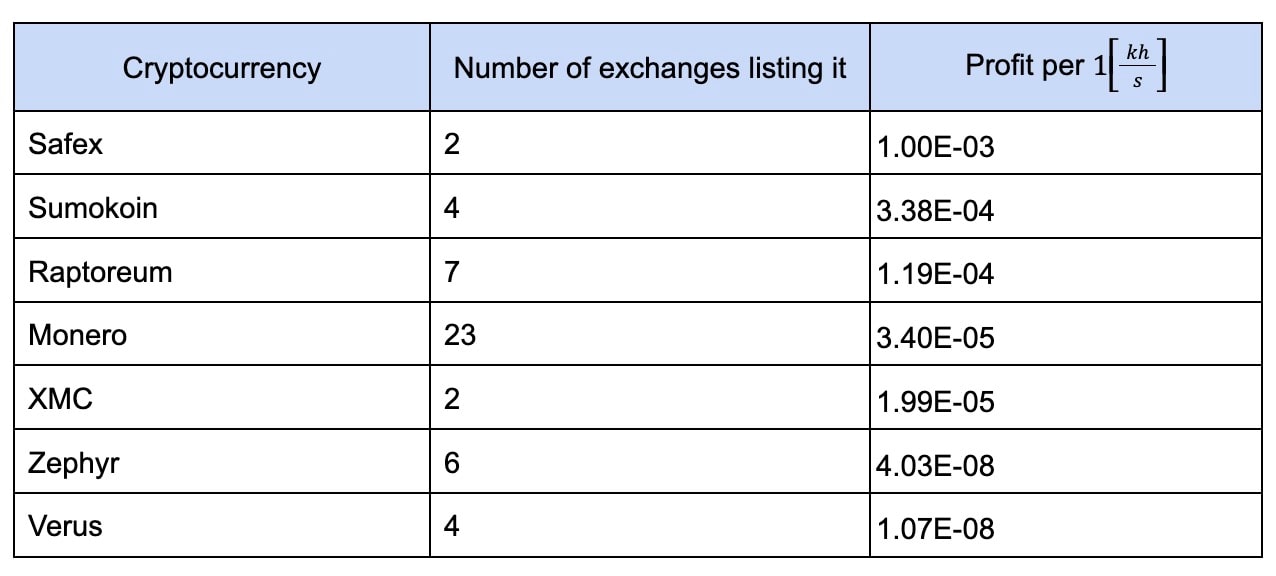 Table 1: Comparison of relevant cryptocoins for cryptominer use
Table 1: Comparison of relevant cryptocoins for cryptominer use
Table 1 sorted according to the coin's profitability at the time of writing this article. In this research, we will focus on the more common coins used by cryptominers and analyze in-the-wild (ITW) samples. To regenerate the coin candidate table according to the current market values and the reward rate, we published our code in the Akamai GitHub repository.
We were able to construct this candidate table after examining the attackers’ motivations and the fundamental principles of a cryptocurrency blockchain and its mining process. Now, we’ll more closely examine three coins and the mining topologies that both legitimate miners and malicious cryptominers can use to obtain them.
- Monero, which is well-known for its use by attackers
- Zephyr, which appears promising
- Safex, which we believe may be overlooked by attackers
Monero
Monero is the most notorious coin used by cryptominers. It is a privacy-oriented coin based on the ASIC-resistant RandomX algorithm, which makes it a perfect match for cryptominers. Monero uses advanced cryptography algorithms to achieve cutting-edge privacy technology, such as ring signatures, multiple asymmetric keys, bulletproofs, RingCT and more. More information about these privacy techniques and algorithms can be found in the Moneropedia.
Monero implements RingCT, an algorithm that combines a number of invalid input transactions alongside the real one to conceal the input used for the transaction and, therefore, the amount transmitted. It also uses multiple techniques to sign values so that only the transaction participants can read them. The sender’s and the receiver’s identities are cryptographically protected, which means it accomplishes privacy via the three main factors: sender, receiver, and amount.
To make RandomX (and therefore Monero) ASIC-resistant, it defines its own instruction set and a virtual machine (VM) that runs it. Unlike traditional VMs, this does not refer to a separate operating system, but rather a sort of interpreter that translates the custom instruction set to the underlying hardware.
Most of our research is focused on Monero, and the same practices we use to analyze the Monero network, programs, and blockchain can be applied to any other cryptocurrency.
Zephyr
Zephyr positions itself as a privacy-focused protocol that aims to revolutionize the stablecoin industry. Building upon Monero's robust privacy features and using the RandomX PoW mining algorithm, Zephyr introduces a unique ecosystem by splitting its coin into four tokens: ZEPH, ZSD, ZRS, and ZYS (Figure 4).
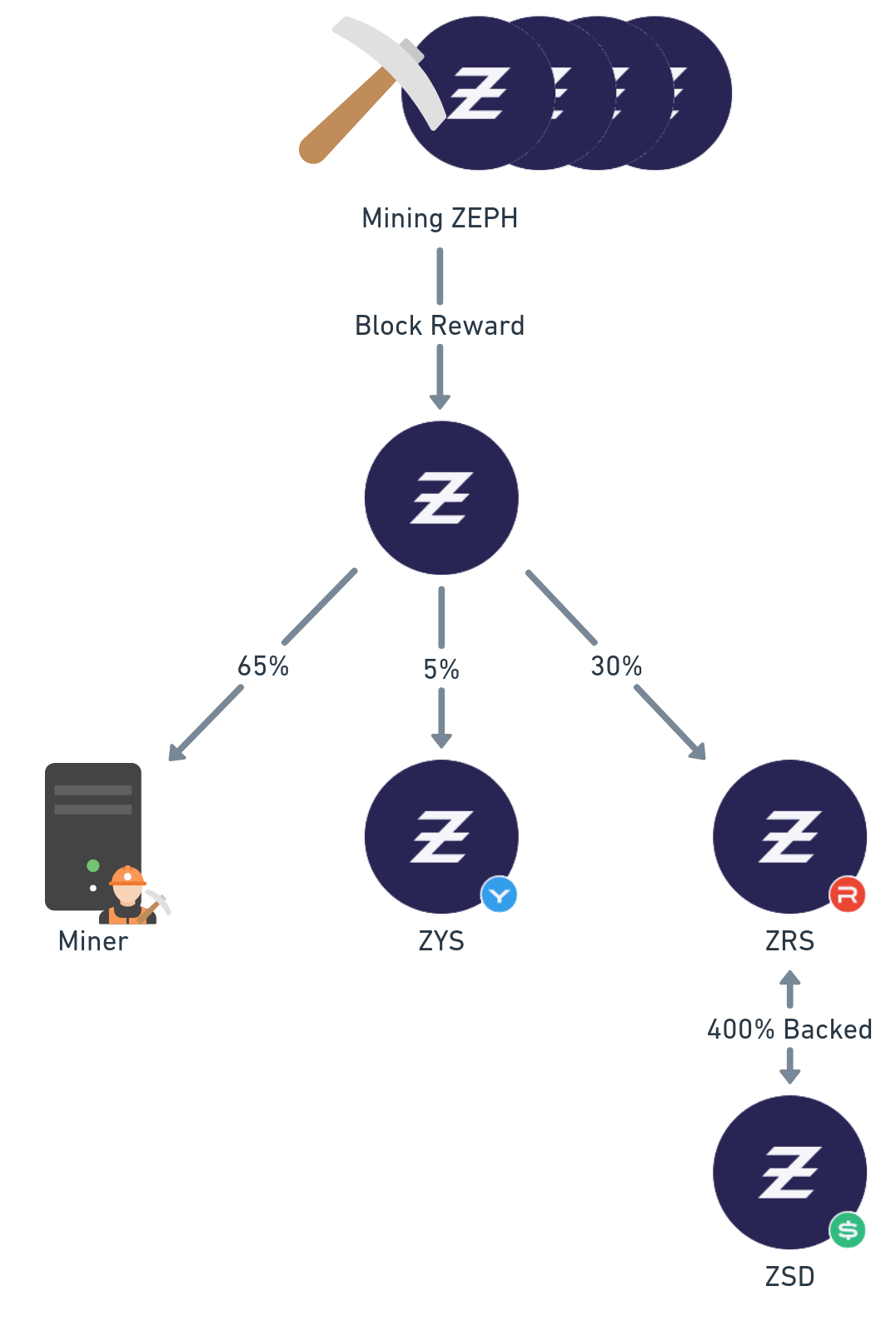 Fig. 4: The Zephyr token relations. Mining ZEPH yields 65% of the rewards to the miner and the rest is kept by the blockchain.
Fig. 4: The Zephyr token relations. Mining ZEPH yields 65% of the rewards to the miner and the rest is kept by the blockchain.
In this framework, ZEPH is the mineable coin that serves as a reference currency. ZRS functions as a reserve backing for ZSD, the stablecoin counterpart. In 2024, Zephyr launched ZYS, a yield mechanism designed to generate profit from the growth of circulated ZYS tokens.
This means that the value of ZYS consistently increases in relation to ZSD, offering users a potentially profitable investment linked to the stablecoin's performance. Attackers will use the minable ZEPH token while also considering the trends of the other tokens as incentives for targeting it.
Currently this is almost the least profitable coin for mining, and therefore the least attractive for cryptominers to use. Nevertheless, we could find malware samples that mine Zephyr. We can speculate about why attackers will use it as part of their campaign: It may be the bigger reward (7.896 ZEPH) for finding a block or evading a Monero-specific detection engine.
SafeX
Safex is a blockchain platform designed for a private, decentralized marketplace in which users can buy and sell products without intermediaries. It uses two main cryptocurrencies: Safex Token (SFT) and Safex Cash (SFX). Prioritizing privacy, Safex uses ring signatures and stealth addresses to keep transactions untraceable and protect user identities, which is essentially based on Monero.
SafeX coin appears to be the most profitable for mining at the moment. This makes it attractive for attackers, but we haven't found active cryptomining besides a few wallets in configuration files.
By mapping the Safex network using the dedicated tool we created, we can see that the network is tiny compared with the Monero network. We could find 298 nodes but only 6 publicly available nodes.
Although this coin appears to be profitable for mining, attackers are currently overlooking it. Our speculation is the attackers are not aware of SafeX profitability, and we believe it will not be long until we see malicious activity abusing this coin.
Mining topologies
Miners can set a mining network in several topologies. Every setup has its own pros and cons, but the bottom line is that they are all designed to optimize the profitability vs. security trade-off. Some of the topologies use a decentralized architecture to support the network and ensure its sustainability. Others focus on optimizing the hashrate and increasing the chances of collecting the block rewards.
The components of the various topologies are essentially the same. All of them interact using network protocols like IP, I2P, Tor and application protocols like Levin for peer-to-peer communication and STRATUM protocol over JSON-RPC. Stratum protocol is the cryptomining standard for operating a fleet of miners using simple JSON structured jobs that contains all the data needed for calculating the consensus hashing algorithm.
Case study
As a case study for different mining topologies, we will focus on Monero. A typical Monero mining topology consists of one of the components shown in Table 2.
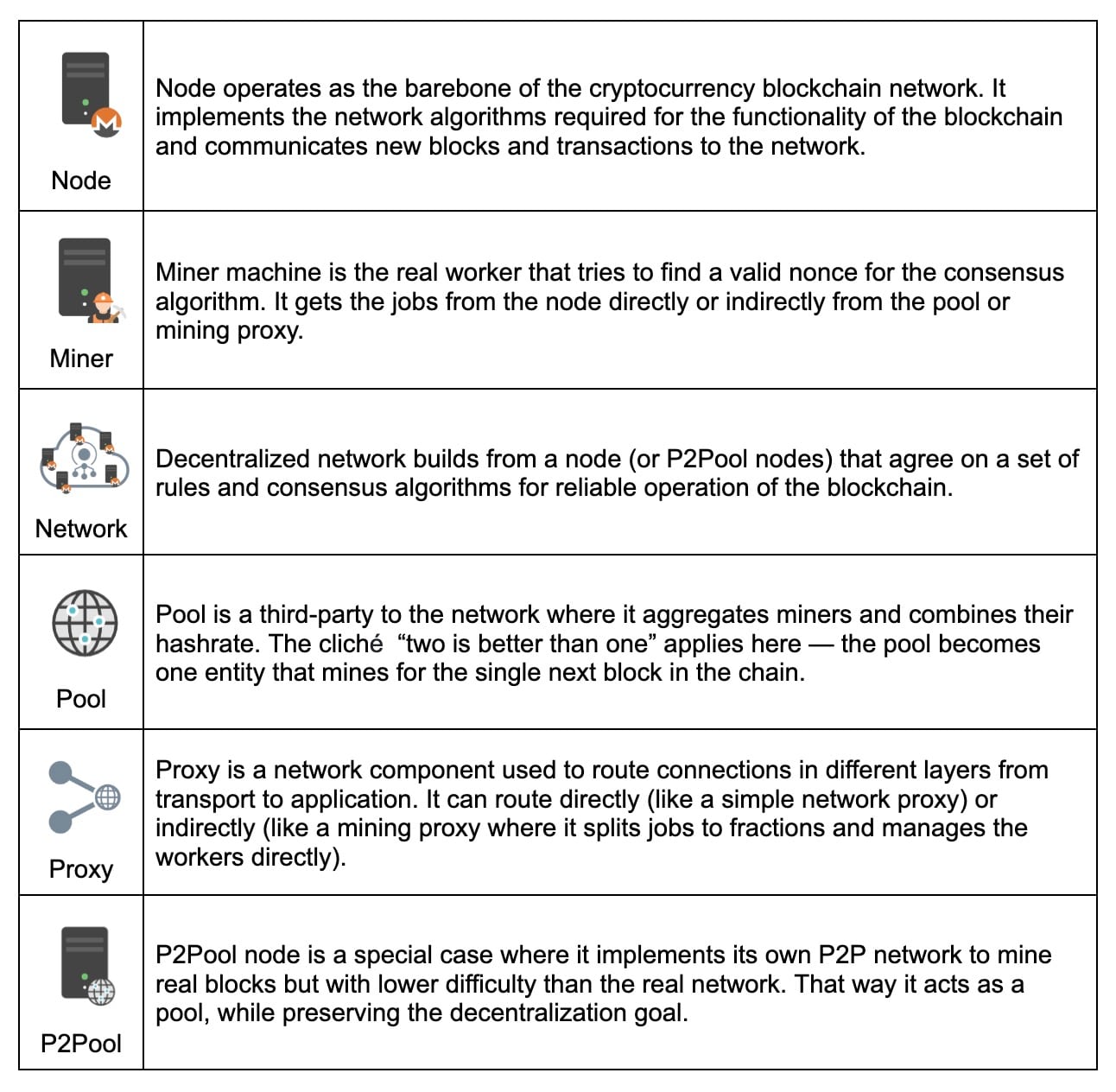 Table 2: Typical Monero mining topologies
Table 2: Typical Monero mining topologies
Topologies used for mining operations
The upcoming sections detail the different types of topologies that can be used for mining operations, including:
- Solo
- Pool
- P2Pool
- Nicehash
- Proxy
Whether for legitimate or malicious purposes, these topologies play a crucial role in the hunting and detection of cryptominers.
Solo
With solo mining, the miner works directly with their own node or a trusted one (Figure 5). While solo mining increases the attacker's potential earnings when a block is found, it also significantly reduces their chances of being rewarded. If the attacker's botnet is large enough, solo mining could be worthwhile.
However, if a single individual controls a substantial amount of hashrate, it poses a serious risk to the network.
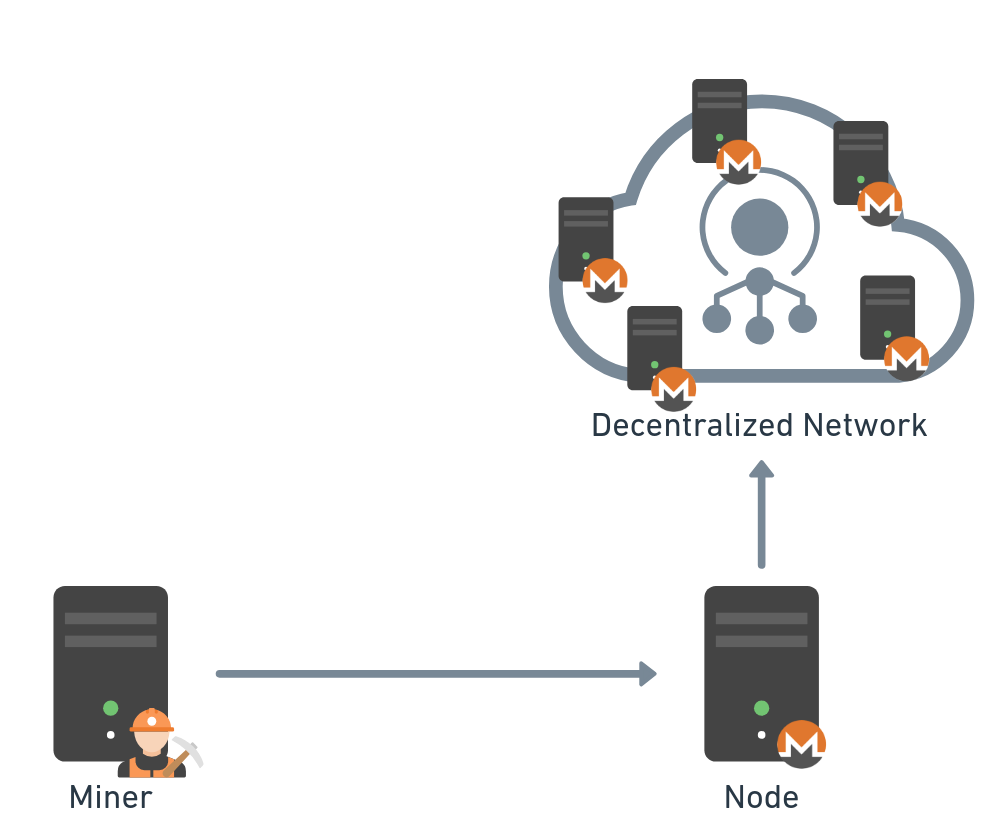 Fig. 5: Solo mining topology
Fig. 5: Solo mining topology
We haven't encountered cryptomining malware configured for solo mining yet. This could be because solo mining doesn't always reward the attacker, so other mining strategies could provide more value in the long run. Or it could also be due to the high operational costs of maintaining a node and the fact that owning one could compromise the attacker's anonymity.
Pool
Unlike solo mining, there is a way to increase the chances of finding a new block by joining forces with other miners — after all, this is a game of statistics. When multiple miners join together to solve the next block in the chain, their hashrates can be combined, allowing them to be represented as a single miner to the network Figure 6).
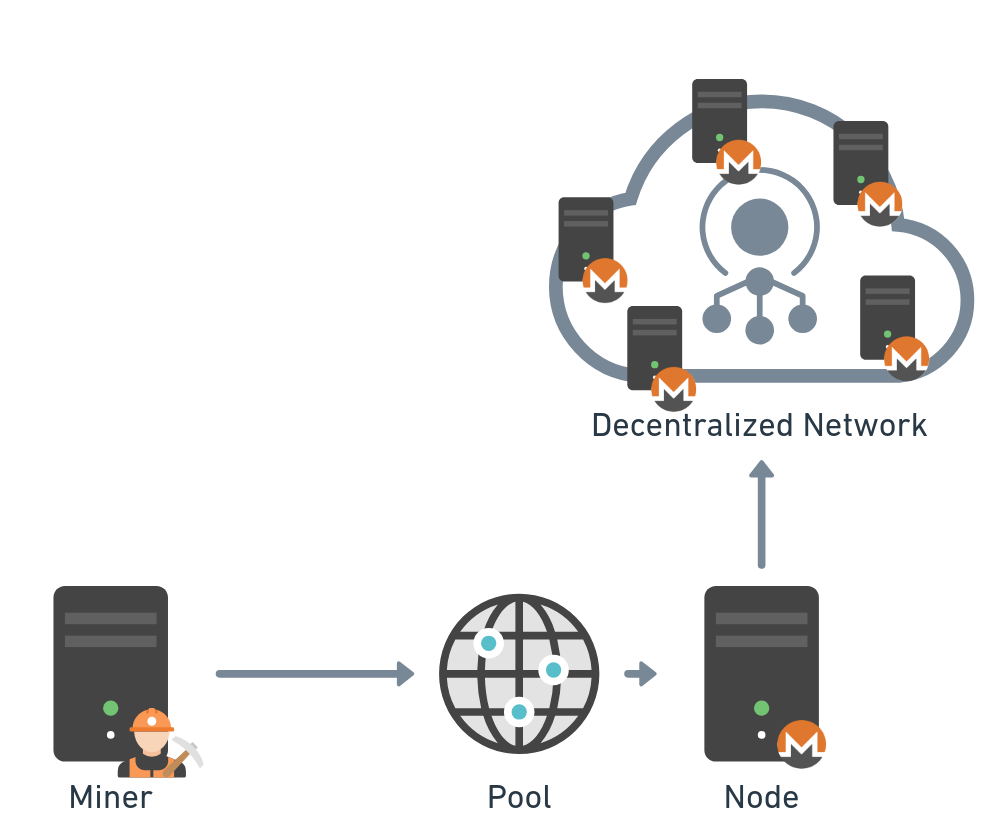 Fig. 6: Pool mining topology
Fig. 6: Pool mining topology
This miner is now called a pool and the pool is usually managed by a single entity. Whenever a new block is found, the reward is split between the participant miners according to their effort, which counts as shares. Therefore, a pool is the orchestrator of multiple miners who increase the statistical chance of mining a block and collecting the reward.
Some pools request a participation fee, and all have a payout model that defines how the reward is split, such as Pay-Per-Last-N-Shares (PPLNS). Many pools don’t require authentication or identification from the miner; it is usually the wallet address that is used for both authentication and payment.
There are countless pools out there that give wide coverage for the different cryptocoins. Some of the pools gather together multiple coins under common features, like privacy, and provide an easy way to operate multiple mining rigs with the same pool in the same way. Others provide multicoin mining, in which the same rig mines multiple coins simultaneously according to their profit, similar to the nicehash operation.
Table 3 contains a list of known mining pools for the three cryptominer candidate coins we discussed earlier.
Monero |
Zephyr | SafeX |
|---|---|---|
nanopool.org supportxmr.com c3pool.com hashvault.pro p2pool.io moneroocean.stream skypool.org xmrpool.eu pool.kryptex.com herominers.com p2pool.io solopool.org monerohash.com antpool.com pool.xmr.pt rplant.xyz monerod.org dxpool.com bohemianpool.com prohashing.com mining-dutch.nl gntl.uk fairhash.org volt-mine.com zeropool.io fastpool.xyz xmr-pool.com zergpool.com xmrminers.com monerop.com pool-pay.com solopool.pro frjoga.com infinium.space minorpool.com cedric-crispin.com aikapool.com |
herominers.com nanopool.org miningocean.org 2miners.com pool.kryptex.com hashvault.pro h9.com 2miners.com ekapool.com k1pool.com raptorhash.net miningmadness.com solopool.org rplant.xyz zephyrprotocol.com gntl.uk aikapool.com fastpool.xyz pool-pay.com thunderhash.com c3pool.com moneroocean.stream minorpool.com skypool.org zergpool.com newpool.xyz coinminerhub.com
|
safex.org safex.ninja pool-pay.com fastpool.xyz skypool.org
|
Table 3: Known mining pools for Monero, Zephyr, and SafeX
Monero |
Zephyr | SafeX |
|---|---|---|
nanopool.org supportxmr.com c3pool.com hashvault.pro p2pool.io moneroocean.stream skypool.org xmrpool.eu pool.kryptex.com herominers.com p2pool.io solopool.org monerohash.com antpool.com pool.xmr.pt rplant.xyz monerod.org dxpool.com bohemianpool.com prohashing.com mining-dutch.nl gntl.uk fairhash.org volt-mine.com zeropool.io fastpool.xyz xmr-pool.com zergpool.com xmrminers.com monerop.com pool-pay.com solopool.pro frjoga.com infinium.space minorpool.com cedric-crispin.com aikapool.com |
herominers.com nanopool.org miningocean.org 2miners.com pool.kryptex.com hashvault.pro h9.com 2miners.com ekapool.com k1pool.com raptorhash.net miningmadness.com solopool.org rplant.xyz zephyrprotocol.com gntl.uk aikapool.com fastpool.xyz pool-pay.com thunderhash.com c3pool.com moneroocean.stream minorpool.com skypool.org zergpool.com newpool.xyz coinminerhub.com |
safex.org safex.ninja pool-pay.com fastpool.xyz skypool.org |
Table 3: Known mining pools for Monero, Zephyr, and SafeX
Monero |
Zephyr | SafeX |
|---|---|---|
nanopool.org supportxmr.com c3pool.com hashvault.pro p2pool.io moneroocean.stream skypool.org xmrpool.eu pool.kryptex.com herominers.com p2pool.io solopool.org monerohash.com antpool.com pool.xmr.pt rplant.xyz monerod.org dxpool.com bohemianpool.com prohashing.com mining-dutch.nl gntl.uk fairhash.org volt-mine.com zeropool.io fastpool.xyz xmr-pool.com zergpool.com xmrminers.com monerop.com pool-pay.com solopool.pro frjoga.com infinium.space minorpool.com cedric-crispin.com aikapool.com |
herominers.com nanopool.org miningocean.org 2miners.com pool.kryptex.com hashvault.pro h9.com 2miners.com ekapool.com k1pool.com raptorhash.net miningmadness.com solopool.org rplant.xyz zephyrprotocol.com gntl.uk aikapool.com fastpool.xyz pool-pay.com thunderhash.com c3pool.com moneroocean.stream minorpool.com skypool.org zergpool.com newpool.xyz coinminerhub.com |
safex.org safex.ninja pool-pay.com fastpool.xyz skypool.org |
Table 3: Known mining pools for Monero, Zephyr, and SafeX
Monero |
Zephyr | SafeX |
|---|---|---|
nanopool.org supportxmr.com c3pool.com hashvault.pro p2pool.io moneroocean.stream skypool.org xmrpool.eu pool.kryptex.com herominers.com p2pool.io solopool.org monerohash.com antpool.com pool.xmr.pt rplant.xyz monerod.org dxpool.com bohemianpool.com prohashing.com mining-dutch.nl gntl.uk fairhash.org volt-mine.com zeropool.io fastpool.xyz xmr-pool.com zergpool.com xmrminers.com monerop.com pool-pay.com solopool.pro frjoga.com infinium.space minorpool.com cedric-crispin.com aikapool.com |
herominers.com nanopool.org miningocean.org 2miners.com pool.kryptex.com hashvault.pro h9.com 2miners.com ekapool.com k1pool.com raptorhash.net miningmadness.com solopool.org rplant.xyz zephyrprotocol.com gntl.uk aikapool.com fastpool.xyz pool-pay.com thunderhash.com c3pool.com moneroocean.stream minorpool.com skypool.org zergpool.com newpool.xyz coinminerhub.com |
safex.org safex.ninja pool-pay.com fastpool.xyz skypool.org |
Table 3: Known mining pools for Monero, Zephyr, and SafeX
P2Pool
Monero's P2Pool is a decentralized mining pool that tackles the centralization issues often found in traditional mining pools. Instead of relying on a central authority to manage mining operations and distribute rewards, P2Pool creates a peer-to-peer network in which miners collaborate directly (Figure 7). This approach aligns with Monero's commitment to privacy and decentralization, enhancing both security and fairness in the mining process.
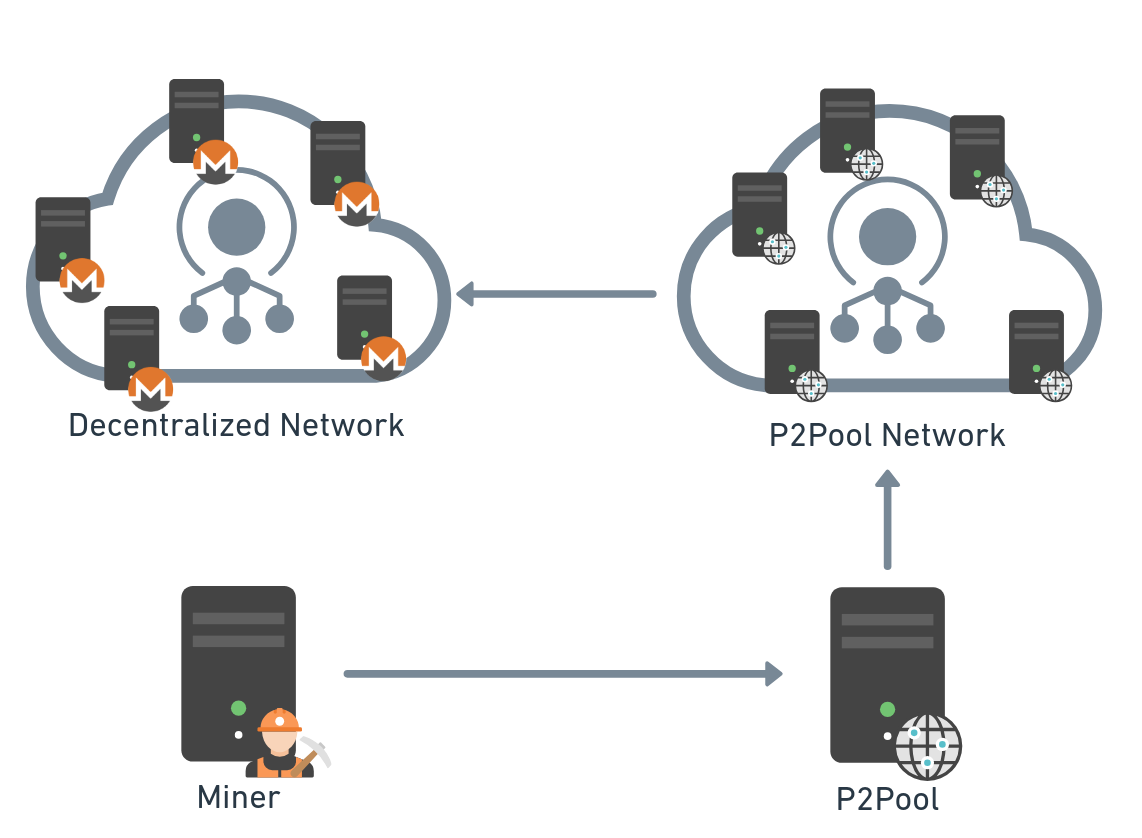 Fig. 7: P2Pool mining topology
Fig. 7: P2Pool mining topology
In the P2Pool system, each miner runs a full Monero node and contributes to the network's hash power while maintaining control over their own mining activities. Rewards are distributed proportionally based on each miner's contribution, all without compromising Monero's robust privacy features.
By eliminating centralized control, P2Pool reduces risks like single points of failure and potential censorship, and offers a more resilient and democratic environment for miners in the Monero ecosystem.
Despite the advantages of using P2Pool topology, including no fees and higher block find rate, we have not encountered a malicious sample that works in such topology. If the operation of a stable node is a disadvantage from the attacker's perspective, that can compromise the attacker's anonymity.
Nicehash
Nicehash is a service for computational resources trading. Miners can offer their rigs’ hashrate for sale without specifying a single algorithm and get a fixed price for it. It eliminates both the statistical element of mining and the luck factor, and replaces it with reduced, but constant income.
This type of mining is similar to pool mining, in which the mining jobs combine multiple algorithms at the same time, meaning that the miner will mine via different algorithms at the same time for multiple buyers.
It’s less likely to find cryptominers linked to Nicehash due to their KYC (know your customer) requirement for the identification of the sellers and buyers. They could be linked using fake or stolen identity but it probably won’t last.
Proxy
Proxy is a well-known network component that routes connections on the transport or application layers. Monero mining, and mining in general, uses Stratum protocol to deliver mining jobs — and as with any application protocol, it can be redirected using a proxy or simple routing table rule to another server, if needed.
Alternatively, a mining proxy server can serve the miners directly by splitting a job from pool or node and distributing it to the connected miners, just like the Monero software XMRig proxy that acts as middleware for job assignments (Figure 8).
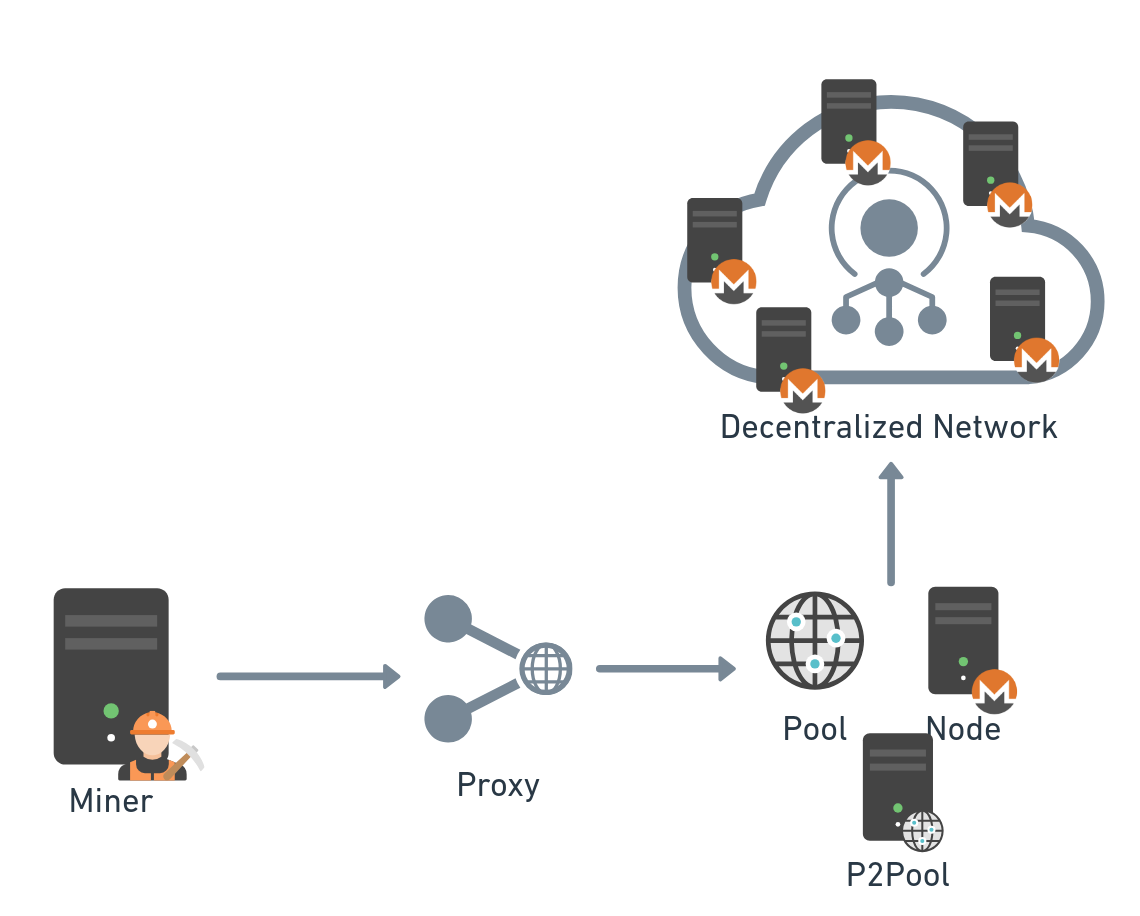 Fig. 8: Proxy mining topology
Fig. 8: Proxy mining topology
We could find both types used by attackers, where the distinguishing difference was that one attempted to hide the mining pool address, while the other hid the pool and the wallet used.
Conclusion
Using cryptocurrency in cybercrime operations is common, but it is typically employed as a payment method. In contrast, cryptominer malware exploits the fundamental aspect of cryptocurrency — its mining process — as a primary means of generating profit.
Attackers can leverage various mining topologies to enhance their privacy and increase resilience against commonly used detection methods. For example, avoiding the inclusion of wallet addresses in the malware samples reduces the effectiveness of static analysis engines designed to identify wallet address patterns. This strategy also makes it harder to link individual samples to a larger campaign, thereby protecting the operation's anonymity.
Creating a table of cryptominer candidates allows us to anticipate the attackers' coin of choice, which may be used within their cryptominer botnet. This insight can help us uncover unnoticed campaigns and focus our detection methods to a specific range of cryptominer candidates.
Appendix A: Potential cryptominers’ coins
The source code for the candidates gathering and calculating profitability is available on our GitHub repository.