You Had Me at Hi — Mirai-Based NoaBot Makes an Appearance

Executive summary
Akamai security researchers uncovered a new crypto mining campaign, which has been active since the start of 2023.
The malware is spread over SSH protocol using a custom Mirai botnet that was modified by the threat actors.
The capabilities of the new botnet, NoaBot, include a wormable self-spreader and an SSH key backdoor to download and execute additional binaries or spread itself to new victims.
As part of the attack, a modified version of the XMRig miner is dropped. The miner obfuscates its configuration and also uses a custom mining pool to avoid exposing the wallet address used by the miner.
We have seen evidence to link the botnet to the P2PInfect worm, which was discovered by Unit 42 in July 2023.
The malware obfuscation and custom code show a high level of operation security, which usually indicates mature threat actors, but the naming of the malware’s binaries and some its included strings are quite childish. This complicates attribution.
We saw more than 800 different attacking IPs in 2023, spread evenly across the world.
We have published indicators of compromise (IOCs), queries, signatures, and scripts that can be used to test for infection.
Introduction
NoaBot is yet another Mirai-based botnet. The Mirai botnet is a wormable botnet that targets Linux-based Internet of Things (IoT) devices. It is used for distributed denial-of-service (DDoS) attacks. The original Mirai botnet was identified in 2016, but its source code has been made public, and many variants can be seen nowadays.
We first detected the NoaBot campaign at the beginning of 2023. Since then, we’ve seen two evolutions of the malware, which consist of additional obfuscations or a change of command and control (C2) and mining pool domains (Figure 1). We’ve also seen several incidents that drop samples of the P2PInfect worm, which hints that the two campaigns are related.
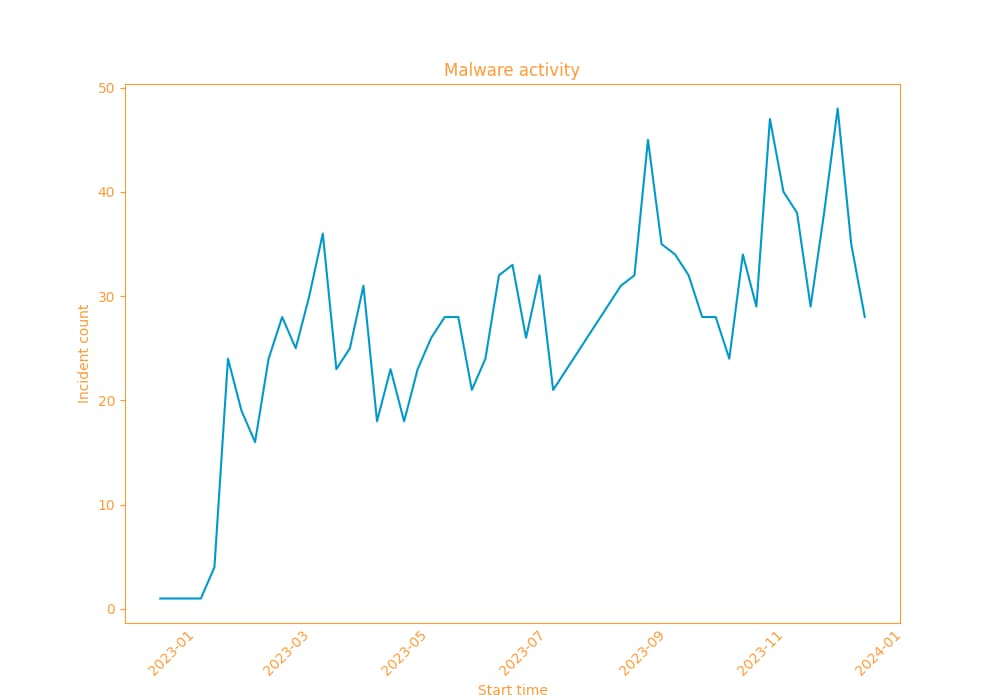 Fig. 1: Noabot malware activity over time
Fig. 1: Noabot malware activity over time
The botnet
The NoaBot botnet has most of the capabilities of the original Mirai botnet (such as a scanner module and an attacker module, hiding its process name, etc.), but we can also see many differences from Mirai’s original source code. First and foremost, the malware’s spreader is based in SSH, not based in Telnet like Mirai.
The SSH scanner seems to be custom made, and quite peculiar — once a connection is established, the botnet simply sends the string “hi” and terminates the connection (Figure 2). Quick termination makes sense in the context of a scanner, since it doesn’t need to keep the connection open, just to verify it exists. Why does it bother sending “hi,” though? That’s a mystery.
 Fig. 2: The SSH packet with the “hi” string. It is not a valid SSH packet so Wireshark marks it as malformed.
Fig. 2: The SSH packet with the “hi” string. It is not a valid SSH packet so Wireshark marks it as malformed.
Another quirkiness of the malware is the embedded song lyrics. Earlier samples of the botnet had lyrics from the song “Who's Ready for Tomorrow” by Rat Boy and IBDY (Figure 3). As far as we can tell, those lyrics served no purpose. Later samples did not have them.
 Fig. 3: The embedded song lyrics that seem to serve no purpose.
Fig. 3: The embedded song lyrics that seem to serve no purpose.
Other changes from Mirai is that he botnet uses a different credential dictionary for its SSH scanner, and includes a lot of postbreach capabilities, such as installing a new SSH authorized key as a backdoor to download and execute additional binaries or spread itself to new victims (Figure 4).
 Fig. 4: Botnet’s command switch case
Fig. 4: Botnet’s command switch case
Also unlike Mirai, which is usually compiled with GCC; at least according to its source code and author’s guide), NoaBot is compiled with uClibc, which seems to change how antivirus engines detect the malware. While other Mirai variants are usually detected with a Mirai signature, NoaBot’s antivirus signatures are of an SSH scanner or a generic trojan (Figure 5).
The malware also comes statically compiled and stripped of any symbols. This, alongside with being a nonstandard compilation, made reverse engineering the malware much more frustrating.
Newer samples of the botnet also had their string obfuscated instead of saved as plaintext. This made it harder to extract details from the binary or navigate parts of the disassembly but the encoding itself was unsophisticated and simple to reverse engineer.
We’ve also seen the addition of command line arguments over time. The most interesting one is the “noa” flag, which made the botnet install a persistence method in the form of a crontab entry to run after a reboot.
Coincidentally, it seems this flag was heavily used in the wild, as some of the antivirus detections for botnet samples had the prefix “Noa-”.
The postbreach operations, which we showed in Figure 4, are another evolution. Those were not present in the earlier samples that we’ve investigated.
The miner — and why we couldn't find its wallet address
The miner itself is a lot less complicated. It is the standard XMRig miner, although it was also self-compiled, and the threat actors added some code before the miner’s execution to extract the mining configuration instead of supplying it via command line or saving it inside the binary as plaintext (Figure 6).
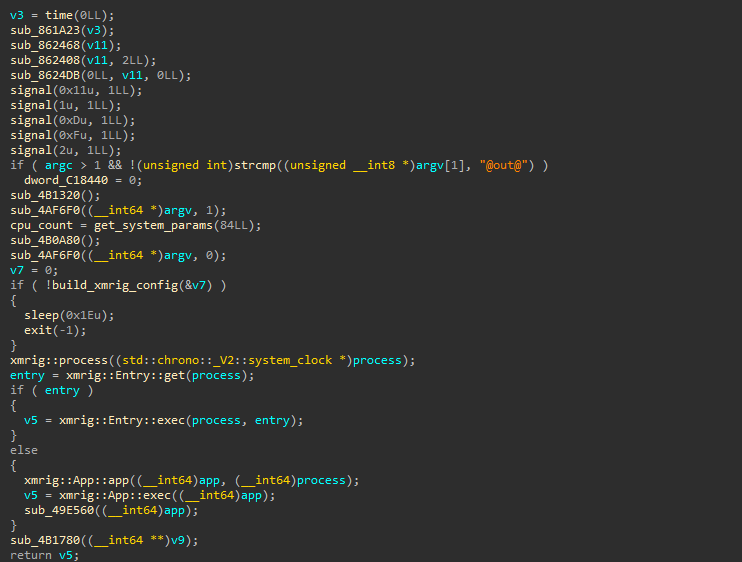 Fig. 6: The main function of the miner
Fig. 6: The main function of the miner
We can see there are some other function calls before the function call to build the XMRig configuration. If it fails, the miner terminates, but otherwise it goes to the standard XMRig miner logic. (You can compare the decompilation above to the actual XMRig source code.) Why do we as researchers care about the XMRig configuration? Usually, it contains details about the mining pool it connects to, as well as the wallet address to receive mining payments. By getting the wallet address and tracking the payments to it (which are usually tracked by public pools), we can estimate how profitable the cryptomining gig is.
This time, however, the attackers were ahead of us. So, let’s do a deeper dive into building the configuration. In the XMRig open source code, miners can accept configurations in one of two ways — either via the command line or via environment variables. In our case, the threat actors chose not to modify the XMRig original code and instead added parts before the main function. To circumvent the need for command line arguments (which can be an indicator of compromise IOC and alert defenders), the threat actors had the miner replace its own command line (in technical terms, replacing argv) with more “meaningful” arguments before passing control to the XMRig code. The botnet runs the miner with (at most) one argument that tells it to print its logs.
Before replacing its command line, however, the miner has to build its configuration. First, it copies basic arguments that are stored plaintext — the rig-id flag, which identifies the miner with three random letters, the threads flags, and a placeholder for the pool’s IP address (Figure 7).
Curiously, because the configurations are loaded via the xmm registers, IDA actually misses the first two loaded arguments, which are the binary name and the pool IP placeholder.
 Fig. 7: Copying basic miner configuration
Fig. 7: Copying basic miner configuration
Next, the miner decrypts the pool’s domain name. The domain name is stored, encrypted, in a few data blocks that are decrypted via XOR operations. Although XMRig can work with a domain name, the attackers decided to go the extra step, and implemented their own DNS resolution function. They communicate directly with Google’s DNS server (8.8.8.8) and parse its response to resolve the domain name to an IP address.
The last part of the configuration is also encrypted in a similar way, and it is the passkey for the miner to connect to the pool. All in all, the total configuration of the miner looks something like this:
<miner_binary_name> -o <pool_ip> --rig-id <random_id> --threads <cpus> –pass espana*tea |
Notice anything missing? Yep, no wallet address.
We believe that the threat actors chose to run their own private pool instead of a public one, thereby eliminating the need to specify a wallet (their pool, their rules!). However, in our samples, we observed that miner’s domains were not resolving with Google’s DNS, so we can’t really prove our theory or gather more data from the pool, since the domains we have are no longer resolvable. We haven’t seen any recent incident that drops the miner, so it could also be that the threat actors decided to depart for greener pastures.
Mirai is too old and developed some Rust
The most recent incidents we’ve seen also had samples of P2PInfect — a peer-to-peer self-replicating worm written in Rust. While P2PInfect was first seen in July 2023, we’ve seen NoaBot activity since January 2023, which means it predates P2PInfect by a bit. Why switch from Mirai to something else? Something that might even be custom? We have no clear answer, but a few guesses.
First, custom code is more difficult to reverse engineer than repurposed code because it is modified. Second, the threat actors seem quite tech-savvy, so it could be that they’re trying their hand at malware development out of curiosity or boredom (or both). Finally, given that P2PInfect targets Redis servers, it could simply be a case of different tools for different purposes.
How do we know that it’s the same threat actors, not just some sort of collaboration? We aren’t 100% certain, but we’re close. It all boils down to the technical professionalism in the malware, coupled with a teenager’s maturity level in terms of inside jokes, including inserting profanities in the miner’s name, embedding gaming pop song lyrics in malware binaries, and sending “hi” while scanning for open ports.
P2PInfect carries on that tradition. It seems like a sophisticated tool, but it uses a Unix socket and names it “NunzombiE” (Figure 8). And while NunzombiE is obfuscated and decoded during run time, the worm also has embedded strings for “fast_vuln_file” and “slow_vuln_file” — perfectly legit strings to contain in an executable, no red flags here.
 Fig. 8: Strace of the P2PInfect worm creating a Unix socket called NunzombiE
Fig. 8: Strace of the P2PInfect worm creating a Unix socket called NunzombiE
Victimology
There are 849 different source IPs that attacked our honeypots across 2023. Looking at their geolocation, we can see a fairly even distribution of activity across the world. This makes sense, since the malware is wormable, so every new victim becomes an attacker themselves. There is, however, one single hotspot of activity that stands out, and it is in China. It amounts to nearly 10% of all attacks we’ve seen across 2023 — it’s the brightest hot spot on Figure 9.
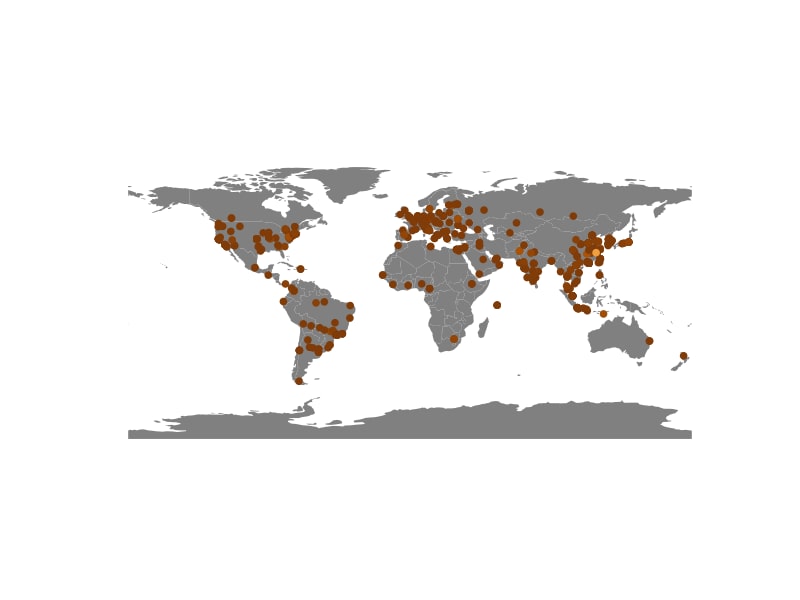 Fig. 9: Global geolocation heatmap of NoaBot attack sources
Fig. 9: Global geolocation heatmap of NoaBot attack sources
Mitigation, detection, emulation
The malware’s method of lateral movement is via plain old SSH credentials dictionary attacks.
Restricting arbitrary internet SSH access to your network greatly diminishes the risks of infection. In addition, using strong (not default or randomly generated) passwords also makes your network more secure, as the malware uses a basic list of guessable passwords. We’ve shared the credential sets used by the malware in our GitHub repository.
There is not much to say about detecting the malware, beyond looking for its binary names. It runs from a randomly generated folder under /lib, so process names are probably the way to go. It should also be possible to detect its cron job, if one was installed. An IOC CSV file is also available at our repository, as well as some YARA signatures for the mine.
In case you want to test your environment against the botnet’s SSH spreader, we’ve created a configuration file for the Infection Monkey, our open source adversary emulation platform (we’ve included a brief explanation on how to use the Infection Monkey in the Appendix). Keep in mind that since the malware uses a very large credential set, it would be impractical for us to test them all (the malware doesn’t care about computation or time costs, but we do). Instead, we opted to include only the more common credentials in the configuration. If you want to include more credentials (or different ones), feel free to build upon this configuration and include your own modifications.
This Infection Monkey configuration also adds a masquerade string that will cause our YARA signatures to trigger on the Monkey agent payload, so you could use it to test that detection as well.
Once the Infection Monkey finishes testing your environment, it’ll create a report of all the machines it managed to breach. You can also use its cryptojacking plug-in if you want to take the attack simulation to the next level and test for stronger credentials.
Summary
On the surface, NoaBot isn’t a very sophisticated campaign — it’s “just” a Mirai variant and an XMRig cryptominer, and they’re a dime a dozen nowadays. However, the obfuscations added to the malware and the additions to the original source code paint a vastly different picture of the threat actors’ capabilities. Despite the technical skills of the threat actors, they seem to have some immature naming conventions (a Unix socket called “NunzombiE,” for example) that persist even across different malware samples and binaries. We used this characteristic to associate NoaBot with P2PInfect, and perhaps this detection clue will hold true for future malware campaigns.
Appendix: Using the Infection Monkey to test your environment
Install the Infection Monkey, based on your operating system:
Follow the set up instructions.
Download the SSH exploiter plug-in from the plug-ins page in the Infection Monkey UI.
 Fig. 10: The Infection Monkey plug-in screen. Use the search bar to look for the SSH exploiter plug-in and download it.
Fig. 10: The Infection Monkey plug-in screen. Use the search bar to look for the SSH exploiter plug-in and download it.
Import the configuration file to emulate NoaBot.
 Fig. 11: The Infection Monkey configuration screen. You can import the configuration we provide by pressing the “Import config” button.
Fig. 11: The Infection Monkey configuration screen. You can import the configuration we provide by pressing the “Import config” button.



