Scanning Activity for CVE-2024-22024 (XXE) Vulnerability in Ivanti

Introduction
Over the last few weeks, Ivanti has disclosed numerous critical CVEs. The most recent — CVE-2024-22024 — is no different. Although it does not have as high a CVSS score as previous vulnerabilities, CVE-2024-22024 will still likely be a prime target for attackers.
On February 8, 2024, Ivanti published an advisory for CVE-2024-22024. Ivanti originally reported that this flaw was discovered during internal testing. However, their advisory was later updated to also give credit to watchTowr for responsibly disclosing this vulnerability.
CVE-2024-22024 is an XML external entity (XXE) injection vulnerability located within the SAML component of Ivanti Connect Secure and Ivanti Policy Secure. Successful exploitation of this vulnerability could lead to sensitive information disclosure, denial of service (DoS), server-side request forgery (SSRF), or even arbitrary code execution, depending on the underlying web application.
Observed scanning activity
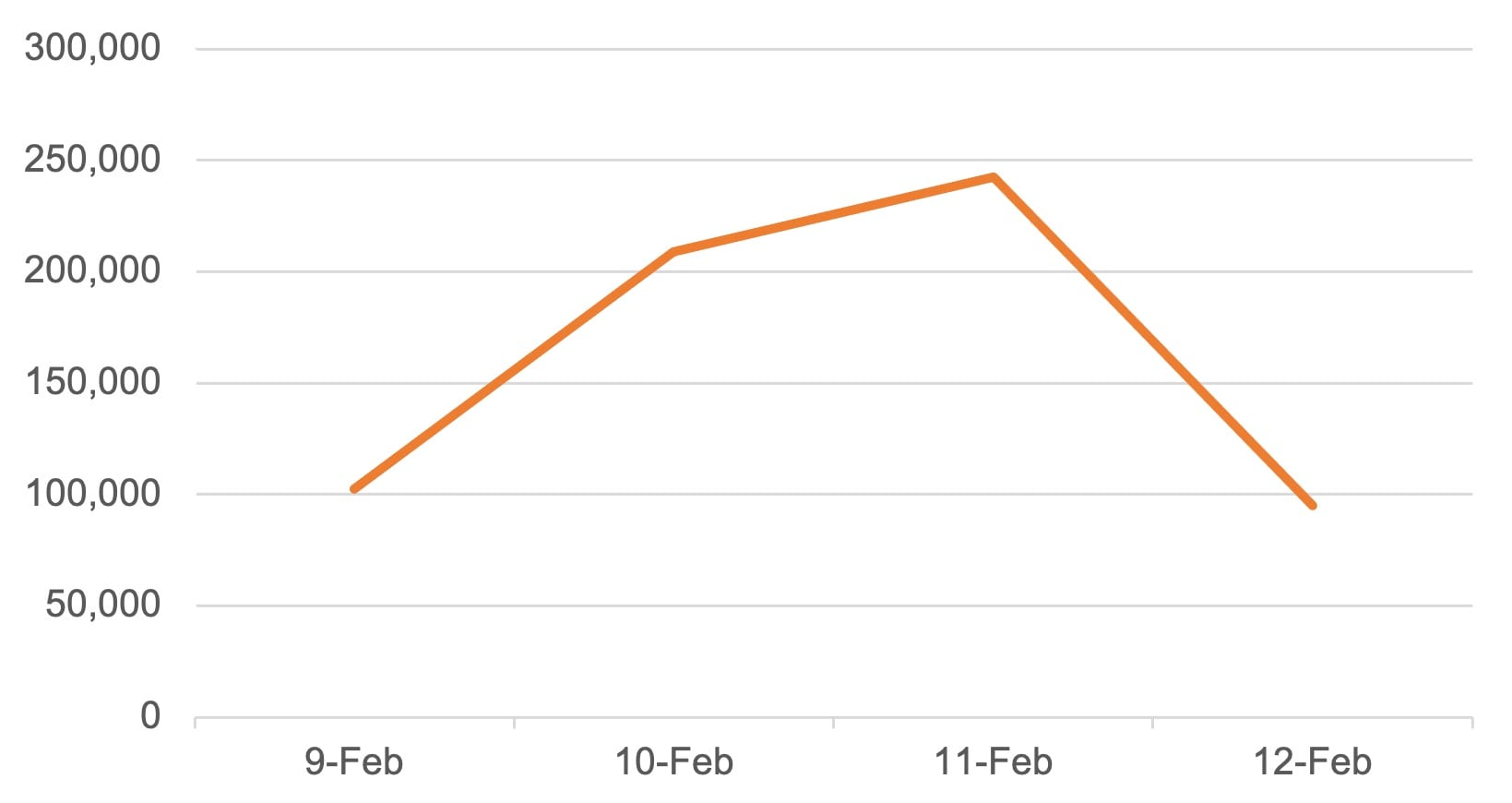
We have seen significant scanning activity across our platform that targets this CVE. After the initial proof of concept (PoC) was published on February 9, 2024, a surge of scanning was observed. The scanning traffic reached its peak on February 11 and tapered off on February 12 (Figure 1).
So far, we have only been seeing payloads similar to the original PoC published by watchTowr. There have been a few variations of the original PoC but all have been “blind” out-of-band payloads that attempt to get the targeted server to interact with one of many different listening domains.
The Akamai Security Intelligence Group will continue to analyze our web application firewall (WAF) logs for new variants or a transition to weaponized payloads, and we will update this section of the blog if we discover any new information.
Mitigating with Akamai App & API Protector
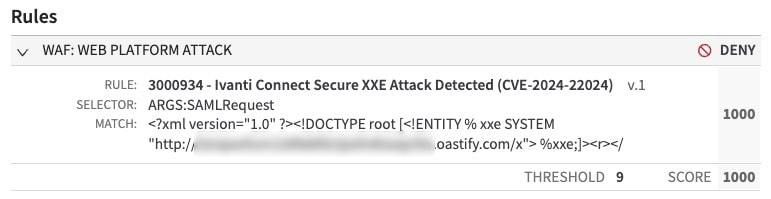
Customers who are using Akamai Adaptive Security Engine in automatic mode and have the Web Platform Attack group in Deny mode are automatically protected against these attacks. Customers who are using Adaptive Security Engine in manual mode should validate that they have the Web Platform Attack group or the following individual rule in Deny mode (Figure 2):
3000934 v1 — Improved Detection of Ivanti Connect Secure XXE Attack Detected (CVE-2024-22024)
Summary
Akamai App & API Protector has been successfully mitigating these attack attempts against our security customers.
The most effective defense will always be to promptly apply the patches provided by the vendor. However, we understand the amount of time and effort security teams need to dedicate to identify and safely patch vulnerable software — and with the growing number of applications and fluid environments, this task requires even more time and effort.
A defense-in-depth strategy remains crucial for protecting an organization's assets from an ever-increasing number of threats. Attackers are quick to incorporate public PoCs into their attack toolsets, making the challenge for defenders even greater. Implementing a WAF, like Akamai App & API Protector, can add an additional layer of defense, which can protect against newly discovered CVEs and provide an extra buffer of security.
This blog post provides an overview of our current understanding and our recommendations given the information available. Our review is ongoing and any information herein is subject to change. You can also visit our X account for real-time updates.