Exploitation Observed: Ivanti Connect Secure — CVE-2023-46805 and CVE-2024-21887
Introduction
On January 10, 2024, multiple parties (Ivanti, Volexity, and Mandiant) disclosed the existence of a zero-day vulnerability that affects the Ivanti Connect Secure and Ivanti Policy Secure gateways. This exploit chain leads to remote code execution. Intense scanning for the vulnerability commenced on January 16, 2024.
Ivanti Connect Secure, serving as an SSL-VPN solution, has emerged as a highly coveted asset for potential attackers who are seeking an entry point into the internal enterprise network. Its functionality as a virtual private network adds a layer of encryption and authentication, which if compromised, could grant malicious actors a foothold into sensitive organizational systems and data repositories.
Thus, understanding and fortifying the security measures surrounding Ivanti Connect Secure becomes imperative to safeguard against potential cyberthreats and intrusions that are targeting enterprise networks.
About the CVE
On January 10, Ivanti released a security advisory disclosing these vulnerabilities. Successful exploitation requires chaining two vulnerabilities together. The first, CVE-2023-46805, is an authentication bypass vulnerability. This is achieved by using path traversals to get around access control checks. The second, CVE-2024-21887, allows an authenticated user with admin privileges to execute arbitrary commands. When combined, an unauthenticated attacker can achieve remote code execution.
Observed exploitation attempts
Our data reveals noteworthy signs of scans that are targeting CVE activity across our platform. After the complete disclosure of exploit details on January 16, a substantial surge in widespread exploitation was observed, reaching its peak within the initial 24 hours. The majority of these attack attempts were probes that attempted to deliver a payload that sends a beacon request to an attacker-controlled domain, serving as a proof of concept (PoC) for successful remote command execution.
Exploit 1:
/api/v1/totp/user-backup-code/../../system/maintenance/archiving/cloud-server-test-connection (Figure 1, Figure 2)
 Fig. 1: CVE-2023-46805 exploit attempt denied by an Adaptive Security Engine rule
Fig. 1: CVE-2023-46805 exploit attempt denied by an Adaptive Security Engine rule
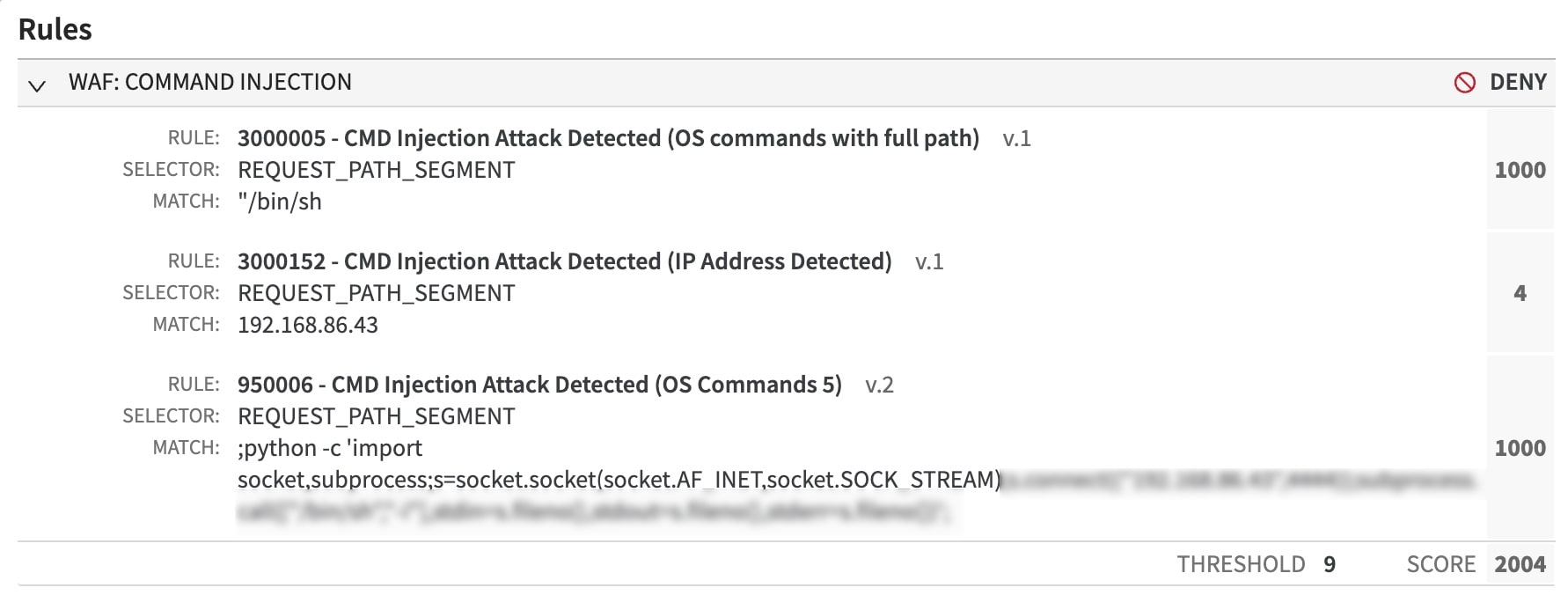 Fig. 2: CVE-2024-21887 exploit attempt denied by several Adaptive Security Engine rules
Fig. 2: CVE-2024-21887 exploit attempt denied by several Adaptive Security Engine rules
Exploit 2: /api/v1/totp/user-backup-code/../../license/keys-status/ (Figure 3)
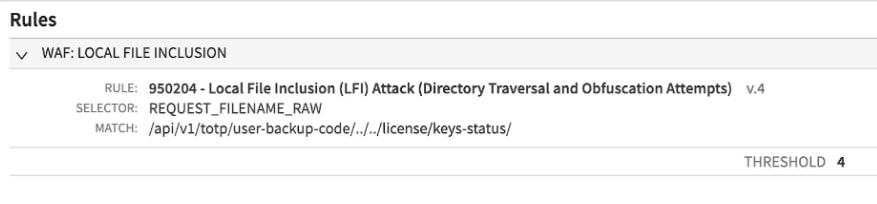 Fig. 3: CVE-2023-46805 exploit attempt denied by an Adaptive Security Engine rule
Fig. 3: CVE-2023-46805 exploit attempt denied by an Adaptive Security Engine rule
Mitigating with App & API Protector
Customers who are using Akamai Adaptive Security Engine in automatic mode and have the local file inclusion (LFI) and the command injection groups in Deny mode are automatically protected against these attacks. Customers who are using Adaptive Security Engine in manual mode should validate that they have LFI and the command injection groups or the following individual rules in Deny mode:
950204 v4 — LFI attack on PATH
Summary
Akamai App & API Protector has been successfully mitigating these attack attempts against our security customers.
While promptly applying patches provided by vendors remains the most effective defense, we acknowledge the arduous task faced by security teams. Identifying and safely patching vulnerable software can demand a substantial investment of time and effort. Moreover, with the expanding number of applications and dynamic environments, this undertaking becomes even more formidable.
A defense-in-depth strategy remains essential for safeguarding an organization's assets against an increasingly large number of threats. Attackers are adept at integrating public PoCs into their arsenal, thus intensifying the challenge for defenders.
Implementing a web application firewall (WAF), like Akamai App & API Protector, can serve as an additional layer of defense, which can protect against newly discovered CVEs and provide an extra buffer of security.
This blog post provides an overview of our current understanding and our recommendations given the information available. Our review is ongoing and any information herein is subject to change. You can also visit our X account for real-time updates.





