InfectedSlurs Botnet Spreads Mirai via Zero-Days

Editorial and additional commentary by Tricia Howard
CONTENT WARNING: The threat actors responsible for this malware use racial slurs and other offensive content as filenames that appear in our screenshots. We did not redact them in an effort to increase detection as this campaign is currently active in the wild.
Executive summary
The Akamai Security Intelligence Response Team (SIRT) has uncovered two zero-day vulnerabilities with remote code execution (RCE) functionality exploited in the wild.
The two vulnerabilities have been reported to the vendors. We are waiting on updates about impacted models and patch availability from those vendors (expected in December 2023) before we can release more details.
These vulnerabilities are being actively exploited in the wild to build a distributed denial-of-service (DDoS) botnet.
The botnet has been engaged in a long-running campaign that Akamai SIRT has been monitoring since late 2022 on our custom-built honeypots. It leverages the popular malware family Mirai.
The payload targets routers and network video recorder (NVR) devices with default admin credentials and installs Mirai variants when successful.
Introduction and discovery
The Akamai SIRT manages multiple honeypots across the globe to discover what threats are actively exploiting our customers and the internet at large. In late October 2023, we noticed a small uptick in activity to our honeypots targeting a rarely used TCP port. The activity started out with a small burst, peaking at 20 attempts per day, and then thinned out to an average of two to three per day, with some days completely devoid of attempts.
Until November 9, 2023, the vulnerable devices being targeted were unknown. The probes were of low frequency and appeared to first attempt an authentication via a POST request and then, upon success, attempt a command injection exploitation.
The investigation revealed a specific HTTP exploit path and targeted port. The SIRT conducted an internet-wide scan for the targeted port-and-path combination. Initially, these results created more questions — notably, about an odd HTTP response Server header. Since both the name and the version number have internet slang roots, it was originally assumed that the devices discovered in the wild that fit the profile we were looking for must be a honeypot or a joke.
Identifying the payloads
On the landing pages for the identified devices, a script is included that handles client-side encryption in JavaScript of the username and password values before they’re POSTed to the CGI script backend for processing. By using this code, we were able to reverse the encryption process and get plaintext username and password values from the observed exploit payloads authentication attempts. This helped us identify that the payloads we had observed were likely targeting these yet-to-be-identified devices.
When we looked at these devices through a broader lens, we were able to find some more hints about what we were seeing. Initial port and service exposures suggested real-time streaming protocol (RTSP) support and offered "Viewer" logins, suggesting a CCTV/NVR/DVR/security camera device. In some cases, devices found in the wild with enabled HTTPS had additional information leakage from the HTTPS certificate Subject line that pointed us to a specific domain, which we traced back to an NVR manufacturer.
By examining manuals and documentation for some of their NVR offerings, we were able to confirm that the plaintext credentials observed in the exploit payload are a common default, which have seen use across many products and companies, but are specifically documented by this manufacturer in multiple NVR product manuals as default administrative credentials.
The SIRT did a quick check for CVEs known to impact this vendor’s NVR devices and was surprised to find that we were looking at a new zero-day exploit being actively leveraged in the wild. Through the responsible disclosure process, the vendor communicated to us they are working on a fix that will likely be deployed in December 2023. As such, we are withholding the vendor name for now but are providing this blog so the community can check their networks.
We decided to look a bit closer at the campaign that was building the underlying botnet that was leveraging this new zero-day exploit by going back to our honeypot, malware, and botnet tracking logs. By looking at new hits that were spreading these malware samples, we identified a second zero-day exploit also being leveraged as part of this campaign.
The device identification in this second instance was made much simpler because the device's default administrative credentials included the device model number. This second device is an outlet-based wireless LAN router built for hotels and residential applications. The second vendor plans to also release details in December of 2023. For the same reasons, we are not disclosing the vendor name here either.
Who and what is affected?
We’ve not gotten a full report back from the NVR vendor of the device models and versions that are believed to be impacted. The SIRT estimates the NVR vendor produces roughly 100 NVR/DVR/IP camera products — with no version information leakage from public-facing devices in the wild, it’s difficult to know exactly which ones are and aren't impacted. Online manuals suggest several models use the default credentials pair being leveraged as part of this campaign.
The zero-day exploit against the router vendor appears to have targeted a single model, but there is a sub-variant model number that is also likely affected, which might be a unique enough application to be considered a second independent model. The router vendor produces multiple switches and routers, however, and although the exploit has been confirmed for the first device by the Japanese manufacturer via JPCERT coordination, we’ve not been told whether it is the only model that was impacted in their overall lineup. The feature being exploited is a very common one, and it’s possible there is code reuse across product line offerings.
Although this information is limited, we felt it was our responsibility to alert the community about the ongoing exploitation of these CVEs in the wild. There is a thin line between responsible disclosing information to help defenders, and oversharing information that can enable further abuse by hordes of threat actors.
We plan to publish a follow-up blog post with additional details and deeper coverage of the devices and exploit payloads once the vendors and CERTs feel confident that responsible disclosure, patching, and remediation have run their course.
The InfectedSlurs botnet
This activity derives from a Mirai botnet activity cluster that appears to primarily use the older JenX Mirai malware variant, made famous by the utilization of Grand Theft Auto to recruit Internet of Things (IoT) devices to do the malicious bidding. There were many command and control (C2) domains identified that have overlaps in IP address resolution, as well as the exact same dates for infrastructure changes, that support this connection.
Interestingly, many of those IP addresses have a limited number of C2 domain resolutions. It is common for domains to point to an IP that’s hosting thousands of other domains but, in this case, many of the IPs were only pointing to a few different domains, typically all belonging to their infrastructure, with the first and last seen dates often changing at the same time for several domains.
The C2 domains in this cluster can tell us a few things about the individual(s) behind this: The naming conventions often contained racial epithets, offensive language, or generally inappropriate terms. The JenX Mirai variant, like many Mirai variants, prints a unique hard-coded string to the console when compromising a machine. In this case, it typically prints, “gosh that Chinese family at the other table sure ate a lot,” a sentiment that may be linked to the unsavory naming conventions described earlier. One of the associated JenX Mirai malware samples available on VirusTotal with that console string came from the C2 IP address 45.142.182[.]96, and called out to the domain iaxtpa[.]parody (Figure 1).
![One of the associated JenX Mirai malware samples available on VirusTotal with that console string came from the C2 IP address 45.142.182[.]96, and called out to the domain iaxtpa[.]parody (Figure 1).](/site/en/images/blog/2023/new-rce-botnet-spreads-mirai-via-zero-days-one.jpg) Fig. 1: Unique JenX Mirai-related console string from a malware sample with the SHA256 hash of ac43c52b42b123e2530538273dfb12e3b70178aa1dee6d4fd5198c08bfeb4dc1
Fig. 1: Unique JenX Mirai-related console string from a malware sample with the SHA256 hash of ac43c52b42b123e2530538273dfb12e3b70178aa1dee6d4fd5198c08bfeb4dc1
C2 domains
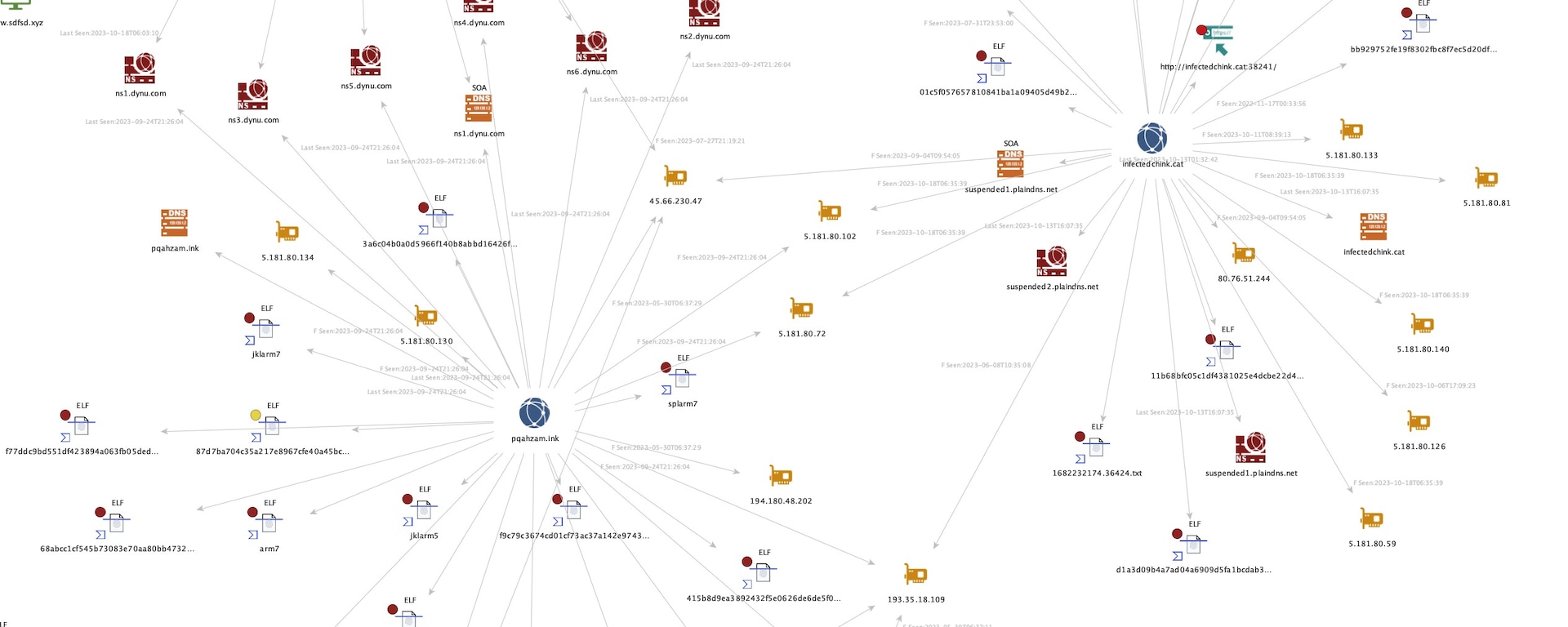
Many of the C2 addresses and the C2 domain resolutions align with IPs that fall under the Classless Inter-Domain Routing (CIDR) block 5.181.80.0/24 (Figure 2).
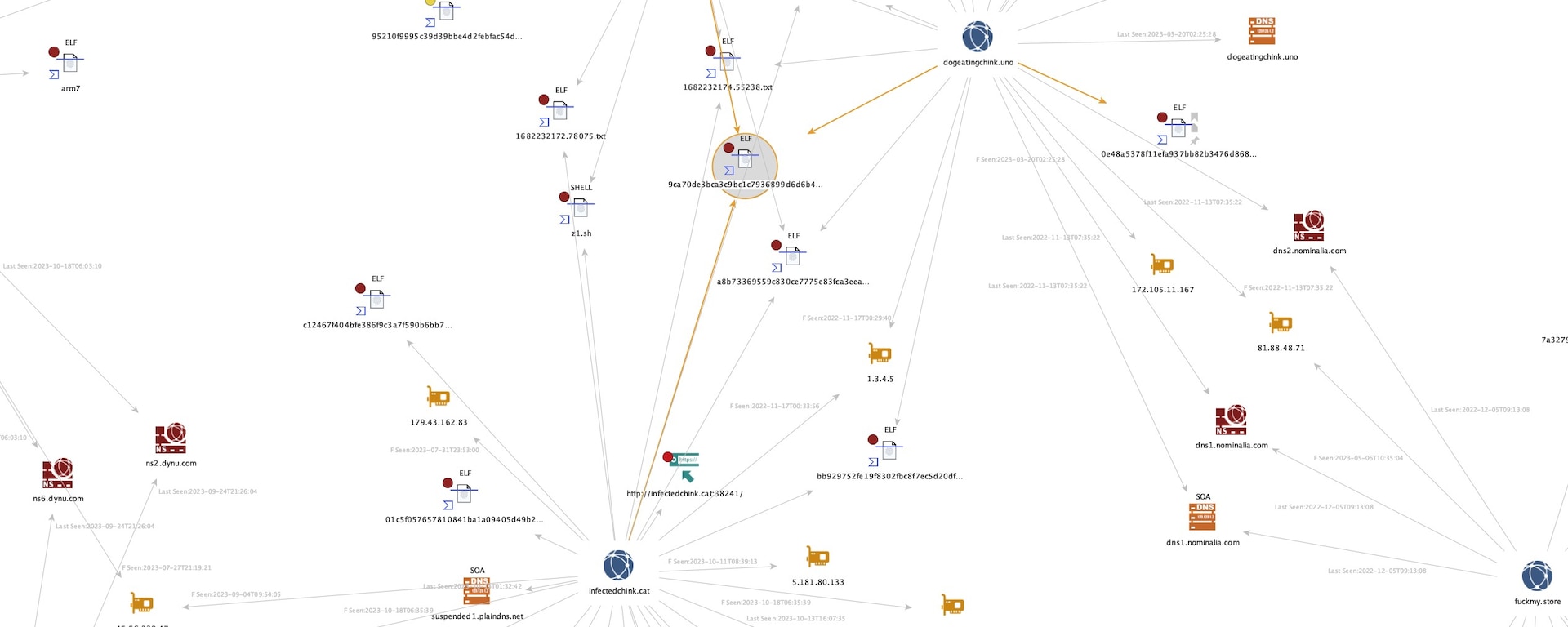
There was additional evidence of links among some of the domains with IP resolution overlap, changing to different IPs at the exact times and dates (Figures 3 and 4).
Additional malware variants associated
Although this cluster mostly uses the JenX Mirai variant, there were additional malware samples that appeared to be linked to the hailBot Mirai variant. While JenX primarily contained the filename of “jkxl”, the assumed hailBot file names contained “skid”. Additionally, one of the unique identifiers for hailBot is the console string “hail china mainland” that gets printed upon compromising a system (Figure 5). One of the malware samples we captured, named “skid.mpsl”, was seen echoing this same string to the console upon execution, and can be seen on VirusTotal. This sample came from the C2 server 5.181.80[.]120, and called out to the domain name husd8uasd9[.]online.
 Fig. 5: Unique hailBot Mirai-related console string from a malware sample with the SHA256 hash of a3b78818bbef4fd55f704c96c203765b5ab37723bc87aac6aa7ebfcc76dfa06d
Fig. 5: Unique hailBot Mirai-related console string from a malware sample with the SHA256 hash of a3b78818bbef4fd55f704c96c203765b5ab37723bc87aac6aa7ebfcc76dfa06d
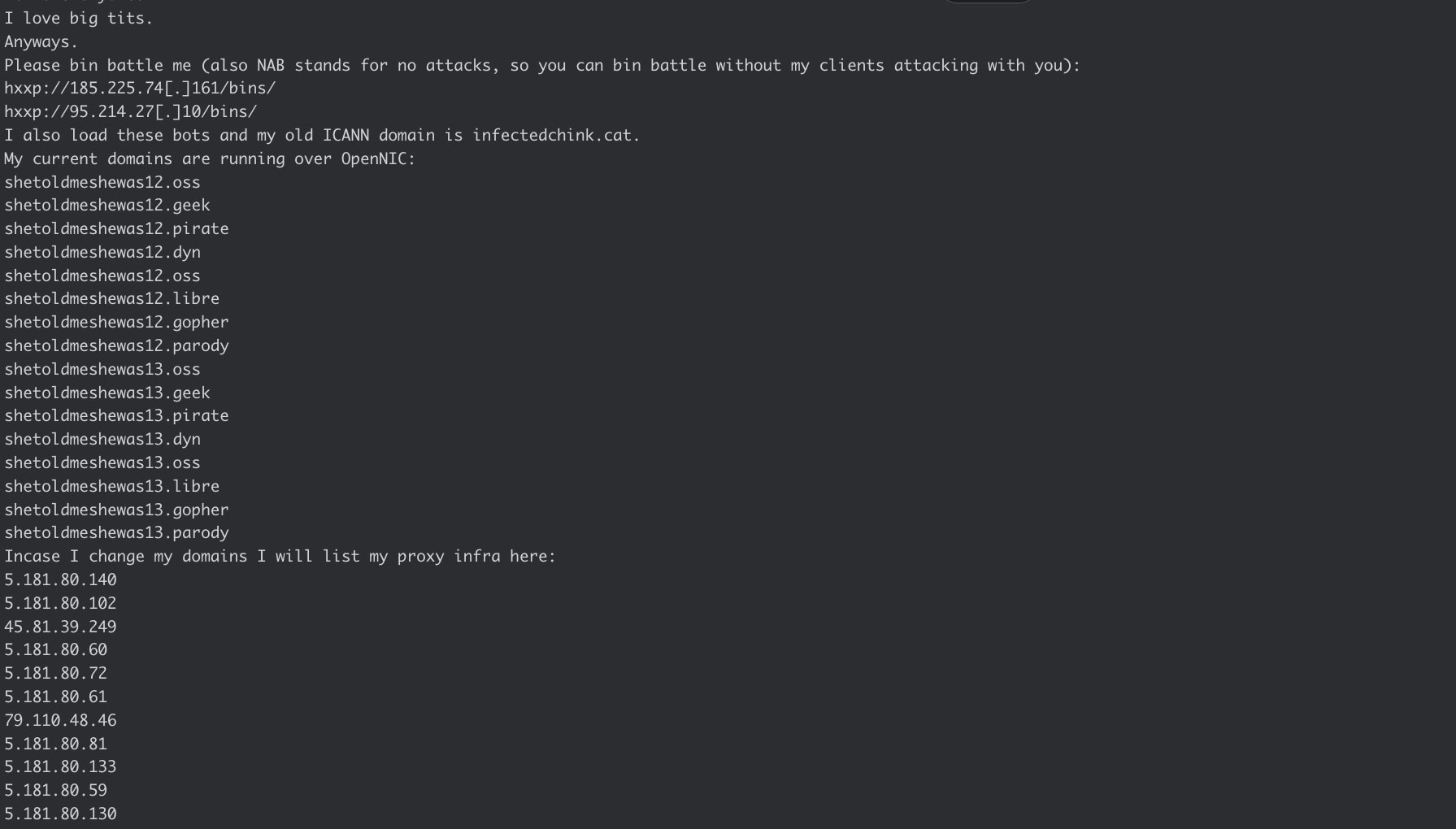
Additionally, we discovered mentions of some of the C2 infrastructure from a deleted Telegram user in the notorious DDoS marketplace channel DStatCC. On October 11, 2023, the user asked other users in the chat to “bin battle” him and referenced several C2 IP addresses and domains that match the activity cluster there. The user referred to the domain “infectedchink[.]cat” as their “old ICANN domain,” and said that their current domains are “running over OpenNIC,” which is an alternative DNS network that provides access to domains not administered by the Internet Corporation for Assigned Names and Numbers (ICANN). According to the subsequent messages in that channel, the user had immediately deleted their account after that post.
The websites listed in the post contained equally troubling naming conventions of “shetoldmeshewas12” or “shetoldmeshewas13” with varying top-level domains (TLDs) such as “.oss”, “.geek”, and “.parody”. They also listed IP addresses they called their “proxy infra,” which align with the resolutions seen previously for some of the C2 domains and the CIDR block we have been tracking (Figure 6). Additionally, the user attached a screenshot of the bots they have, with the majority being Telnet (9781 bots), Vacron (6791 bots), ntel (4877 bots), and UTT-Bots (1515 bots).
In late August 2023, a threat actor dump on PasteBin showed several of the C2 domains in this cluster, including “infectedchink[.]cat” (Figure 7). This post appeared to be derived from @RedDrip7, the public Twitter profile for the RedDrip Team that is part of Qi An Xin Technology, a Chinese security vendor. They reported that this C2 infrastructure was seen targeting a Russian news website with a DDoS attack in May 2023. The C2 domains, IP addresses, hashes, and ports used are all aligned with the activity in this report.
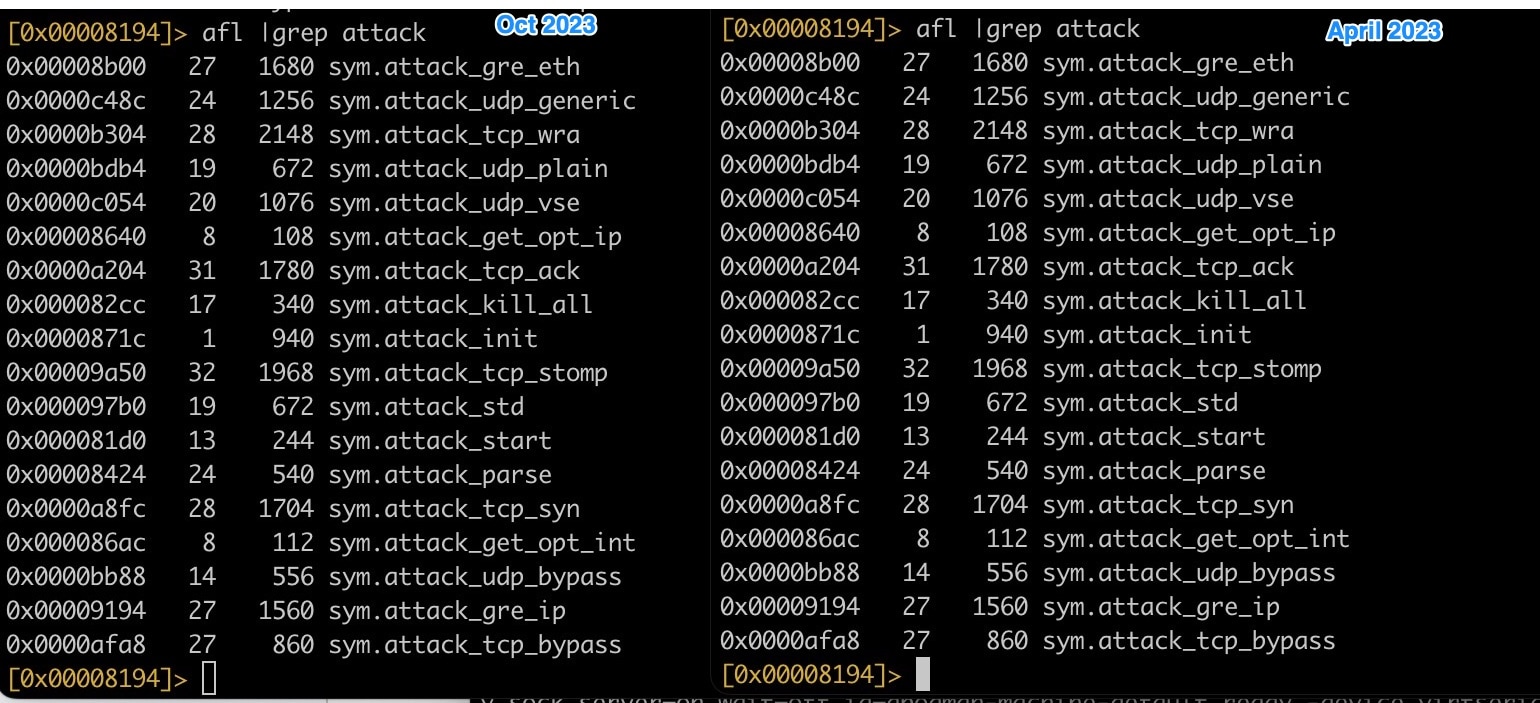
The attack functions are quite similar to the original Mirai botnet. A side-by-side comparison of older malware (April 2023) with the variant being used in this campaign (October 2023) shows the same functions in the same memory locations (Figure 8). This indicates that the Mirai code has not been modified much, if at all.
Detection
The Akamai SIRT is working with CISA/US-CERT, and JPCERT to notify vendors of the impacted devices. We’ve agreed to not publish full details to allow the vendor time to roll out patches, but given that these vulnerabilities are being actively exploited, we’re providing Snort and YARA rules to help defenders identify exploit attempts and possible infections in their environments. Once patches have been released, we’ll publish a follow-up blog post with more details on the exploits and payloads leveraged in this campaign.
Snort rules
Zero-day payload 1 (FXC AE1021 & AE1021PE - CVE-2023-49897)
Used to detect exploitation attempts by this campaign
alert tcp any any -> any any (msg:"FXC AE1021 & AE1021PE - CVE-2023-49897 (InfectedSlurs exploitation attempt)"; content:"lang="; content:"useNTPServer="; content:"synccheck="; content:"timeserver="; content:"interval="; content:"enableNTPServer="; sid:1000006;)
Zero-day payload 2
Used to detect exploitation attempts by this campaign
alert tcp any any -> any any (msg:"InfectedSlurs 0day exploit #2 attempt"; content:"page_suc="; content:"system.general.datetime="; content:"ntp.general.hostname="; pcre:"ntp.general.hostname="; content:"ntp.general.dst="; content:"ntp.general.dst.adjust="; content:"system.general.timezone="; content:"system.general.tzname="; content:"ntp.general.enable="; sid:1000005;)
Zero-day payload 3 (QNAP VioStor - CVE-2023-47565)
Used to detect exploitation attempts by this campaign
alert tcp any any -> any any (msg:"QNAP VioStor - CVE-2023-47565 (InfectedSlurs exploitation attempt)"; flow:to_server,established; content:"POST"; http_method; content:"/cgi-bin/server/server.cgi"; content:"func="; content:"counter="; content:"APPLY="; http_uri; content:"time_mode="; content:"time_YEAR="; content:"time_MONTH="; content:"time_DAY="; content:"time_HOUR="; content:"time_MINUTE="; content:"time_SECOND"; content:"enable_rtc="; content:"TIMEZONE="; content:"year="; content:"month="; content:"day="; content:"CONFIGURE_NTP="; content:"SPECIFIC_SERVER="; http_client_body; sid:1000002;)
C2 traffic
Used to detect network traffic to InfectedSlurs C2 infrastructure
alert ip any any -> 45.95.147.226 any (msg:"InfectedSlurs C2 communications"; sid:1000001;)
alert ip any any -> 45.142.182.96 any (msg:"InfectedSlurs C2 communications"; sid:1000002;)
alert ip any any -> 5.181.80.53 any (msg:"InfectedSlurs C2 communications"; sid:1000003;)
alert ip any any -> 5.181.80.54 any (msg:"InfectedSlurs C2 communications"; sid:1000004;)
alert ip any any -> 5.181.80.55 any (msg:"InfectedSlurs C2 communications"; sid:1000005;)
alert ip any any -> 5.181.80.59 any (msg:"InfectedSlurs C2 communications"; sid:1000006;)
alert ip any any -> 5.181.80.81 any (msg:"InfectedSlurs C2 communications"; sid:1000007;)
alert ip any any -> 5.181.80.72 any (msg:"InfectedSlurs C2 communications"; sid:1000008;)
alert ip any any -> 5.181.80.77 any (msg:"InfectedSlurs C2 communications"; sid:1000009;)
alert ip any any -> 5.181.80.102 any (msg:"InfectedSlurs C2 communications"; sid:1000010;)
alert ip any any -> 5.181.80.126 any (msg:"InfectedSlurs C2 communications"; sid:1000011;)
alert ip any any -> 5.181.80.127 any (msg:"InfectedSlurs C2 communications"; sid:1000012;)
alert ip any any -> 91.92.254.4 any (msg:"InfectedSlurs C2 communications"; sid:1000013;)
alert ip any any -> 185.225.74.161 any (msg:"InfectedSlurs C2 communications"; sid:1000014;)
alert ip any any -> 185.150.26.226 any (msg:"InfectedSlurs C2 communications"; sid:1000015;)
alert ip any any -> 194.180.48.202 any (msg:"InfectedSlurs C2 communications"; sid:1000016;)
alert ip any any -> 85.217.144.207 any (msg:"InfectedSlurs C2 communications"; sid:1000017;)
alert ip any any -> 45.139.105.145 any (msg:"InfectedSlurs C2 communications"; sid:1000018;)
alert ip any any -> 162.220.166.114 any (msg:"InfectedSlurs C2 communications"; sid:1000019;)
alert ip any any -> 89.190.156.145 any (msg:"InfectedSlurs C2 communications"; sid:1000020;)
alert ip any any -> 162.246.20.236 any (msg:"InfectedSlurs C2 communications"; sid:1000021;)
alert ip any any -> 194.153.216.164 any (msg:"InfectedSlurs C2 communications"; sid:1000022;)
alert ip any any -> 95.214.27.10 any (msg:"InfectedSlurs C2 communications"; sid:1000023;)
alert ip any any -> 62.113.113.168 any (msg:"InfectedSlurs C2 communications"; sid:1000024;)
alert ip any any -> 194.38.21.42 any (msg:"InfectedSlurs C2 communications"; sid:1000025;)
Mirai heartbeat
As this campaign is leveraging Mirai, we’re including a simple Snort rule that will attempt to identify Mirai C2 communications protocol heartbeats. This rule has a high probability of generating false positives and should be used sparingly and with low confidence.
alert tcp INTERNAL_NET any -> EXTERNAL_NET any ( msg:"mirai heartbeat to c2"; sid: 100001; rev:1; content: "|00 00 00 01|";)
YARA rules
InfectedSlurs supporting scripts
rule infected_slurs_scripts_1 {
meta:
description = "infected-slurs-scripts-1"
author = "Akamai SIRT"
date = "2023-11-20"
strings:
$s1 = "ftpget.sh ftpget.sh && sh ftpget.sh;curl http://" fullword ascii
$s2 = "chinese family" fullword ascii
$s3 = "\\x23\\x21\\x2F\\x62\\x69\\x6E\\x2F\\x73\\x68\\x0A\\x0A\\x66\\x6F\\x72\\x20\\x70\\x72\\x6F\\x63\\x5F\\x64\\x69\\x72\\x20\\x69\\x6E\\x20\\x2F\\x70\\x72\\x6F\\x63\" fullword ascii
$s4 = "/bin/busybox hostname TBOT" fullword ascii
condition:
3 of them
}
rule infected_slurs_scripts_2 {
meta:
description = "infected-slurs-scripts-2"
author = "Akamai SIRT"
date = "2023-11-20"
strings:
$s1 = ";<=>?@ABCDEFGJIMOPQRSTUVWX[\\^_`abcxyz{|}~" fullword ascii
$s2 = "#$%&'()*+,234567" fullword ascii
$s3 = "BOOOOOOONS_" fullword ascii
$s4 = "npxXoudifFeEgGaACScs" fullword ascii
condition:
3 of them
}
InfectedSlurs Mirai binaries
rule infected_slurs_bins {
meta:
description = "infected-slurs-bins"
author = "Akamai SIRT"
date = "2023-11-20"
strings:
$s1 = "attack_gre.c" fullword ascii
$s2 = "attack_ongoing" fullword ascii
$s3 = "ensure_single_instance" fullword ascii
$s4 = "/home/landley/aboriginal/aboriginal/build/temp-armv7l/gcc-core/gcc/config/arm/pr-support.c" fullword ascii
$s5 = "words_left" fullword ascii
$s6 = "kutil_strncmp" fullword ascii
$s7 = "fflush_unlocked" fullword ascii
$s8 = "methods_len" fullword ascii
condition:
6 of them
}
Indicators of compromise
SHA256SUMs
dabdd4b5a3a70c64c031126fad36a4c45feb69a45e1028d79da6b443291addb8 arm
3f3c2e779f8e3d7f2cc81536ef72d96dd1c7b7691b6e613f5f76c3d02909edd8 arm5
75ef686859010d6164bcd6a4d6cf8a590754ccc3ea45c47ace420b02649ec380 arm6
f8abf9fb17f59cbd7381aa9f5f2e1952628897cee368defd6baa6885d74f3ecc arm7
8777f9af3564b109b43cbcf1fd1a24180f5cf424965050594ce73d754a4e1099 kdvrarm7
ac43c52b42b123e2530538273dfb12e3b70178aa1dee6d4fd5198c08bfeb4dc1 mips
a4975366f0c5b5b52fb371ff2cb034006955b3e3ae064e5700cc5365f27a1d26 mpsl
cd93264637cd3bf19b706afc19944dfb88cd27969aaf0077559e56842d9a0f87 nigga.sh
8e64de3ac6818b4271d3de5d8e4a5d166d13d12804da01ce1cdb7510d8922cc6 ok.sh
35fcc2058ae3a0af68c5ed7452e57ff286abe6ded68bf59078abd9e7b11ea90a ppc
7cc62a1bb2db82e76183eb06e4ca84e07a78cfb71241f21212afd1e01cb308b2 sh4
29f11b5d4dbd6d06d4906b9035f5787e16f9e23134a2cc43dfc1165127c89bff spc
cfbcbb876064c2cf671bdae61544649fa13debbbe58b72cf8c630b5bfc0649f9 x86
a3b78818bbef4fd55f704c96c203765b5ab37723bc87aac6aa7ebfcc76dfa06d mpsl
ac43c52b42b123e2530538273dfb12e3b70178aa1dee6d4fd5198c08bfeb4dc1 mips
Malware samples
arm: ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, stripped
arm5: ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, stripped
arm6: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, stripped
arm7: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, with debug_info, not stripped
kdvrarm7: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, with debug_info, not stripped
mips: ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
mpsl: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
nigga.sh: ASCII text
ok.sh: ASCII text
ppc: ELF 32-bit MSB executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked, stripped
sh4: ELF 32-bit LSB executable, Renesas SH, version 1 (SYSV), statically linked, stripped
spc: ELF 32-bit MSB executable, SPARC, version 1 (SYSV), statically linked, stripped
x86: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped
C2 domains
opewu[.]homes
wu[.]qwewu[.]site
dfvzfvd[.]help
husd8uasd9[.]online
homehitter[.]tk
shetoldmeshewas12[.]oss
shetoldmeshewas12[.]geek
shetoldmeshewas12[.]pirate
shetoldmeshewas12[.]dyn
shetoldmeshewas12[.]libre
shetoldmeshewas12[.]gopher
shetoldmeshewas12[.]parody
shetoldmeshewas13[.]oss
shetoldmeshewas13[.]geek
shetoldmeshewas13[.]pirate
shetoldmeshewas13[.]dyn
shetoldmeshewas13[.]libre
shetoldmeshewas13[.]gopher
shetoldmeshewas13[.]parody
hujunxa[.]cc
skid[.]uno
dogeating[.]monster
chinkona[.]buzz
dogeatingchink[.]uno
infectedchink[.]cat
infectedchink[.]online
sdfsd[.]xyz
gottalovethe[.]indy
pqahzam[.]ink
cooldockmantoo[.]men
chinks-eat-dogs[.]africa
cnc[.]kintaro[.]cc
fuckmy[.]site
fuckmy[.]store
hbakun[.]geek
ksarpo[.]parody
rwziag[.]pirate
metbez[.]gopher
rmdtqq[.]libre
pektbo[.]libre
mqcgbs[.]gopher
cbdgzy[.]pirate
czbrwa[.]geek
edrnhe[.]oss
hfoddy[.]dyn
fawzpp[.]indy
hxqytk[.]geek
iaxtpa[.]parody
mfszki[.]gopher
qhedye[.]oss
wnisyi[.]libre
asdjjasdhioasdia[.]online
jiggaboojones[.]tech
Mitigation
As with any threat, swift mitigation is of the utmost importance. Here are some tips to remain safe against InfectedSlurs and other similar botnets.
InfectedSlur infections
First and foremost, check for default credentials on IoT devices and change them if they exist.
If you find devices believed to be vulnerable in your environments, isolate them if possible and investigate for potential compromise.
DDoS attacks
Assess and implement the recommendations provided by CISA.
Conduct a thorough examination of critical subnets and IP spaces to confirm the presence of effective mitigation controls.
Establish continuous DDoS security controls as the primary layer of defense. This limits the need for urgent integration and alleviates the workload on incident responders.
Configure proactive security controls through a network cloud firewall. This external firewall serves as a potent, easily deployable, and user-friendly tool to efficiently block undesired traffic globally and centrally, safeguarding your networks and specific targets within your networks.
Test for and remove opportunities for lateral movement to limit propagation and reduce detection and remediation time in the event of an attack.
Conclusion
Using honeypots in cybersecurity is paramount — these strategically deployed decoy systems are specifically designed to lure and detect malicious actors, giving us invaluable insight into the attackers’ mindset and their tactics, techniques, and procedures. Incorporating honeypots into a cybersecurity strategy is a powerful tool for threat intelligence, early detection, and continuous improvement of defensive measures in the ever-evolving digital security landscape.
Since honeypots emulate real-life vulnerable environments, the knowledge they can provide to defenders is arguably the most valuable knowledge to obtain. Defense practices based on reality — rather than on fear, uncertainty, and doubt — provide a much more proactive strategy. Keeping up-to-date on emerging cyberthreats enables the refinement of security measures and enhances overall resilience.
If your organization’s environment does not warrant a full honeypot setup, maintaining the basics is imperative. The importance of changing a device's default password cannot be overstated. Threats such as botnets and ransomware rely on default passwords that are often widely known and easily accessible for propagation. The more difficult it is for a threat to move around, the less chance there is of unauthorized access and potential security breaches. You can test for lateral movement with our free, open-source adversary emulation platform, the Infection Monkey.
Stay tuned
The Akamai Security Intelligence Group will continue to monitor threats such as these and report on them to drive awareness in our customers and the security community in general. For more research, follow us on X, formerly known as Twitter, to keep up-to-date on what we’re seeing out there.
The Akamai SIRT would like to thank the folks at CISA, US-CERT, and JPCERT for their assistance in reporting these vulnerabilities to the vendors.





![In late August 2023, a threat actor dump on PasteBin showed several of the C2 domains in this cluster, including “infectedchink[.]cat” (Figure 7).](/site/en/images/blog/2023/new-rce-botnet-spreads-mirai-via-zero-days-infected-pqalink-eight.jpg)