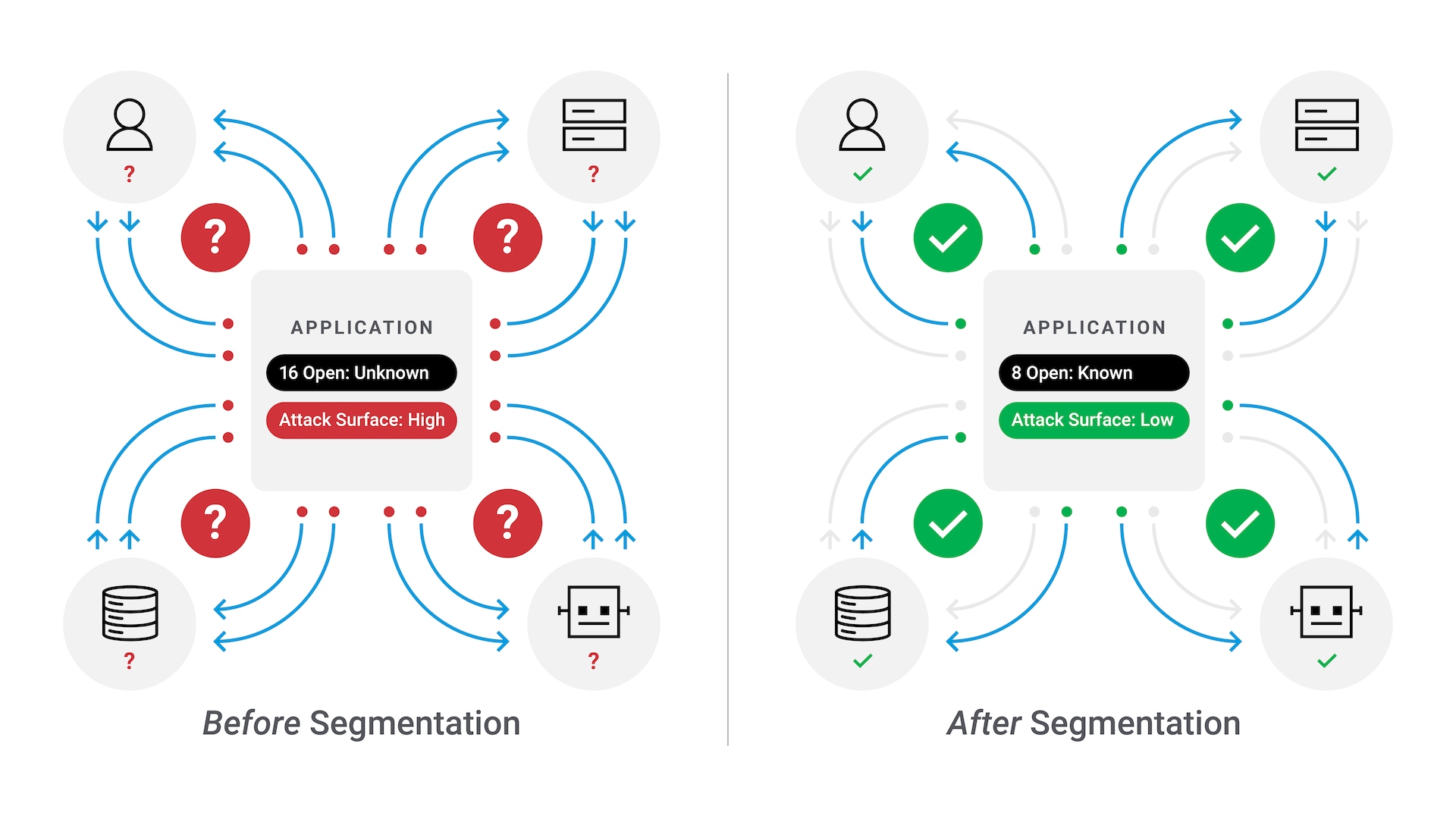
Contain attacks with segmentation for your hybrid cloud deployments
Akamai Guardicore Segmentation allows you to contain attacks on applications and workloads in hybrid cloud and K8s environments, with the same visibility and policy controls provisioned in on-prem environments. Map your assets and flows across environments, virtual machines, servers, and containers, all from a single pane of glass.
Go beyond the data center to secure Azure, AWS, GCP, and other cloud infrastructure with a single view of the cloud and a single, consistent security policy across your hybrid environment. This allows you to identify threats, anomalies, and potential vulnerabilities while quickly applying security controls that adapt to any change in your cloud environment.
Benefits
- Automate discovery, and get comprehensive visualization of cloud flows, precise segmentation policies, and network security alerts.
- Deploy a segmentation solution that works consistently across multiple cloud and K8s deployments, using native enforcement points.
- Stop breaches in the cloud by adapting automatic security policies to any change within your cloud environment, avoiding manual updates.