Network segmentation is a network security technique that divides a network into smaller, distinct subnetworks. This enables network administrators to compartmentalize the entire network and deliver unique security controls and services to each part of the network.
Stop cyberthreats with a segmented network
Security teams have long turned to network segmentation to protect IT infrastructure from cyberattacks. By segmenting the network and filtering traffic between subnetworks with perimeter firewalls, VLANs, and ACLs, network security administrators were effectively able to mitigate certain types of malware and other cyberthreats.
However, traditional perimeter security measures in a segmented network can no longer keep up with the volume of network traffic that enterprise data centers see today. At the same time, cyberthreats are constantly evolving, taking advantage of the complexity of network access points, applications, and IT infrastructure to find new ways to breach network defenses. In this threat arena, traditional firewalls in a segmented network can do little to prevent attackers from using east-west traffic flows to expand their foothold after successfully breaching perimeter defenses.
As a result, more organizations are turning to microsegmentation technology from Akamai to improve cyberthreat security in their segmented networks. By using microperimeters to restrict access to individual IT assets, Akamai Guardicore Segmentation detects and prevents lateral movement to block attacks like ransomware and minimize dwell time throughout the entire cyberattack kill chain.
What Is Two-Factor Authentication (2FA)?
More businesses today are choosing two-factor authentication solutions to improve the security of workforce logins. This is the result of a startling fact: Nearly 80% of data breaches involve the use of stolen or compromised employee credentials and brute-force logins. Compromised credentials are increasingly being used to create a beachhead for cybercriminals as they deliver ransomware and other forms of malware that can have devastating consequences for business profitability and reputation.
Two-factor authentication provides an additional layer of security by requiring users to log in with more than just a password, which can be easily stolen. This extra cybersecurity measure can drastically reduce incidents of breaches — organizations that use two-factor authentication (2FA) or multi-factor authentication (MFA) solutions are 99.9% less likely to be compromised. Two-factor authentication technology built on the FIDO2 security standard is even more secure, preventing hackers from using phishing attacks and credential stuffing techniques to bypass standard MFA security.
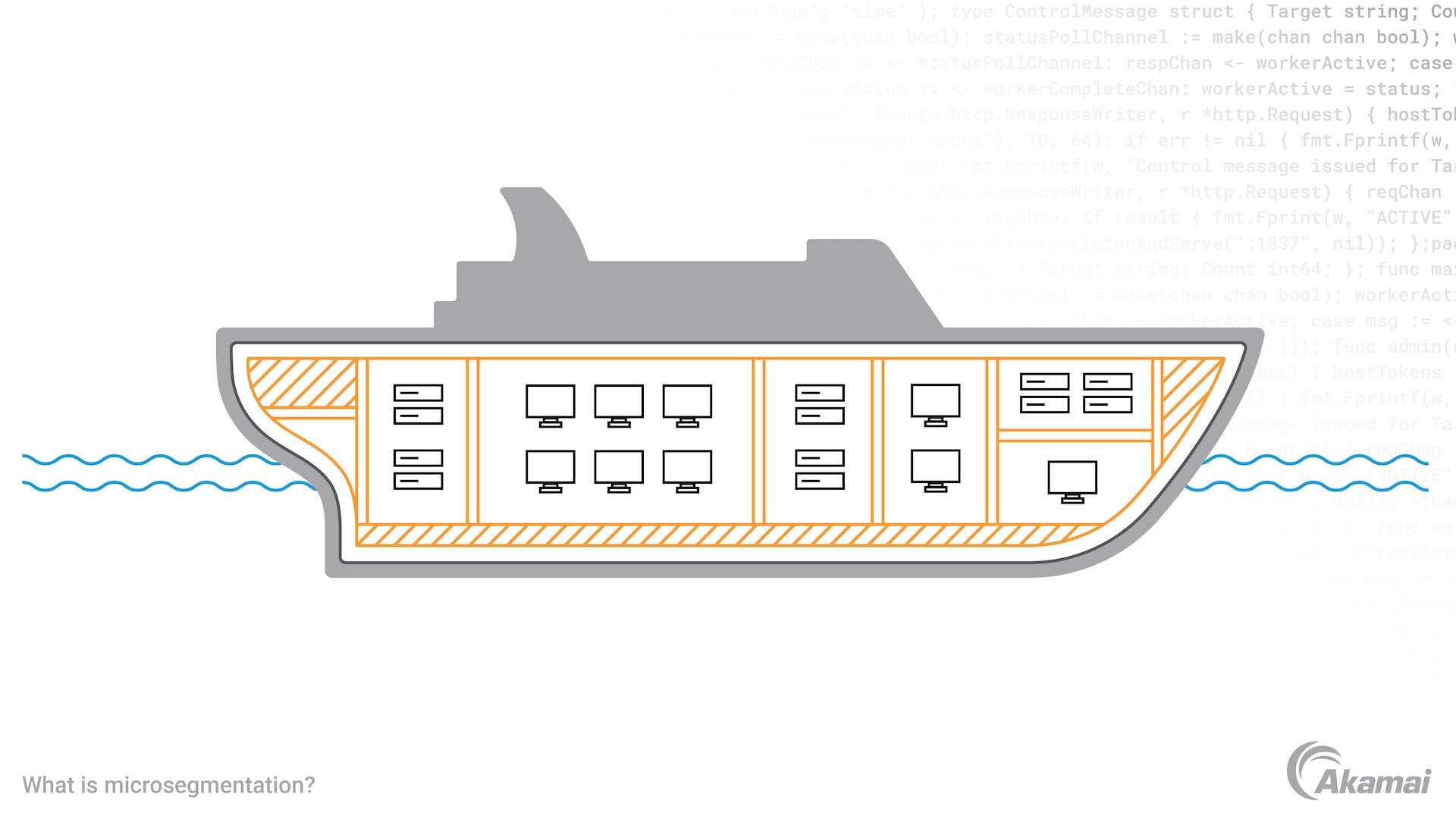 Segmentation has long been used by shipbuilders to isolate hull breaches and contain/control flooding.
Segmentation has long been used by shipbuilders to isolate hull breaches and contain/control flooding.
Microsegmentation and Zero Trust security
In a world of escalating risk, the Zero Trust security framework is quickly becoming the gold standard for organizations and CIOs that want a more rigorous security posture. A Zero Trust architecture abandons the notion of a trusted network inside a well-defined perimeter. Rather than rigorously defending the perimeter and trusting everything within it, a Zero Trust approach trusts no device, user, or IT asset unless it has been authenticated and continually verified.
Microsegmentation can play a critical role in adopting Zero Trust security. In contrast to a traditionally segmented network, microsegmentation is a software-based approach that protects individual IT assets with microperimeters of control that block all communication and traffic that is not necessary or legitimate. Microsegmentation is faster and easier to manage than internal firewalls and VLANs. And by separating security controls from the underlying infrastructure, microsegmentation technology enables organizations to extend protection and visibility anywhere within the IT ecosystem.
To protect a segmented network with microsegmentation technology, cybersecurity teams must have granular visibility into the assets within an IT ecosystem and the sanctioned and unsanctioned activity between them. That’s where Akamai Guardicore Segmentation can help.
Akamai Guardicore Segmentation
Akamai Guardicore Segmentation is the fastest way to visualize and protect assets in a segmented network within a data center, cloud, or hybrid cloud infrastructure. By making it easy to visualize activity within IT environments and implement precise microsegmentation policies, Akamai Guardicore Segmentation helps to detect and block possible breaches quickly.
Akamai’s segmentation technology protects the organization from external and internal threats by using process-level details to inspect and control all east–west and north–south traffic. Our solution delivers an accurate, real-time view of the entire IT environment, delivering stronger protection and authentication for business-critical applications than the traditional defenses in a segmented network.
Akamai Guardicore Segmentation enables you to:
- Increase coverage. Protect essential assets wherever they are deployed or accessed — on-premises, in cloud environments, virtual servers, bare metal, or containers.
- Enhance policy enforcement. Apply the same level of granular, process-level rules across different operating environments for more consistent enforcement of security policies.
- Simplify segmentation. A flexible allowlist/denylist model for segmentation policy enables fast risk reduction with a few rules.
- Achieve zero downtime. Akamai delivers faster results with no changes to computer networks or applications and no downtime.
- Detect breaches faster. Comprehensive breach detection capabilities include reputation analysis, dynamic deception, and a threat intelligence firewall.
Benefits of network segmentation
Microsegmentation with Akamai delivers significant advantages over traditional security solutions in a segmented network.
Reduce your attack surface. Akamai’s software-based segmentation simplifies risk reduction without requiring costly security hardware.
Block lateral movement. Real-time threat detection and incident response capabilities can detect and block lateral movement, minimizing dwell time throughout the entire cyberattack kill chain.
Protect critical assets. Enforce Zero Trust principles in a hybrid cloud infrastructure to protect critical assets from ransomware and other forms of cybercrime.
Simplify compliance. Akamai delivers comprehensive visibility into regulated assets, enabling IT security teams to ensure they are isolated from the broader network and in compliance with regulations regarding segmentation in technical requirements. Akamai can also reference real-time and historical data to prove that segmentation is working as intended and that no noncompliant communications are taking place.
Enhance identity-based access control. Microsegmentation with Akamai enables your security teams to manage access control based on granular options in context, including specific services, ports, and processes.
Frequently Asked Questions (FAQ)
To improve security in a segmented network, microsegmentation separates security controls from the underlying infrastructure, allowing organizations to extend protections and visibility throughout an IT ecosystem. Microsegmentation policies place granular controls around individual IT assets, rather than larger segmented networks or subnets, to provide a more effective defense posture.
East-west network traffic is traffic that originates and terminates within an organization’s own network boundaries. This type of traffic usually involves communication between applications, services, and workloads running on the organization’s internal network. Examples of east-west network traffic include requests from an application server to a database server, or from a web server to an authentication service.
Lateral movement is the process of moving from one system to another within a network, in order to gain access to resources that the attacker would not normally have access to. It is a common tactic used by attackers to gain access to sensitive systems. The attacker may use a variety of techniques, including social engineering, password cracking, and exploiting missing patches or configuration errors.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.

