Confluence Server Webwork OGNL Injection (CVE-2021-26084): So schützt Akamai Sie vor Zero‑Day-Angriffen

Kürzlich hat Atlassian eine kritische RCE-Schwachstelle (Remote Code Execution) in seinen Produkten Confluence Server und Confluence Data Center bekannt gegeben (CVE-2021-26084). Über diese Schwachstelle können nicht authentifizierte Nutzer auf anfälligen Servern beliebigen Code ausführen.
Das KernproblemThe vulnerability is an Object-Graph Navigation Language (OGNL) injection in one of Confluence’s “Velocity” (templating engine) templates that could be triggered by accessing “/pages/createpage-entervariables.action” and potentially other URLs as well. Some proof-of-concept (PoC) exploits and our data suggest additional URLs, although those are not seen in the original patch analysis.
The parameters “queryString” and “linkCreation” allow attackers to inject JAVA code. Figure 1 shows the differences between the patched and unpatched versions of Confluence Server.
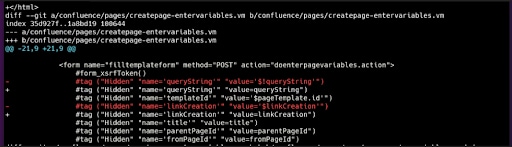 Abb. 1: Das Zeichen $ wurde bei zwei Tags entfernt (https://github.com/httpvoid/writeups/blob/main/Confluence-RCE.md).
Abb. 1: Das Zeichen $ wurde bei zwei Tags entfernt (https://github.com/httpvoid/writeups/blob/main/Confluence-RCE.md).
Unmengen schädlicher Aktivität
Die Komplexität dieses Exploits ist gering. Dementsprechend sind seit seiner Offenlegung am 25. August Dutzende PoC-Varianten entstanden. Und wie auch bei anderen Zero‑Day-RCEs wurden einige dieser PoCs in kürzester Zeit von verschiedenen Cyberkriminellen übernommen. Die erste Massenausspähung sowie die ersten Versuche, die Schwachstelle auszunutzen, wurden bereits am 28. August beobachtet.Current attack campaigns are already reported to deploy XMRig and Kinsing cryptocoin miners, and more recent ones also include Tsunami/Kaiten DDoS bots.
Although the early adopter attackers copy-pasted the existing PoCs, we now see in our data the natural evolution of variants in the wild. As well as the original two URLs that were initially published, we now have these variants:
/pages/createpage.action
/pages/createpage-entervariables.action
/pages/doenterpagevariables.action
/confluence/pages/createpage-entervariables.action
/confluence/pages/doenterpagevariables.action
/collaboration/pages/createpage.action
/jirapages/doenterpagevariables.action
/wiki/pages/doenterpagevariables.action
/-/media/pages/doenterpagevariables.action
/ae/en/pages;/createpage-entervariables.action
/link/lookup/pages;/createpage-entervariables.action
/pages;/createpage-entervariables.action
In the examples above, we can see that attackers are already utilizing a known evasion technique by adding a semicolon in the path (which represents the “path parameters“). Many servers that support path parameters will strip the semicolon before calling the URL, thus successfully reaching the vulnerable Confluence resource, while possibly evading URL-based detection.
As shown in Figures 2–4, in just the last 24 hours, we observed on our global platform:
Almost 2 million attempts to scan and/or exploit these vulnerabilities
88,378 unique hosts targeted
91% of attack activity targeted against Commerce, High Technology, Manufacturing, and Financial Services verticals
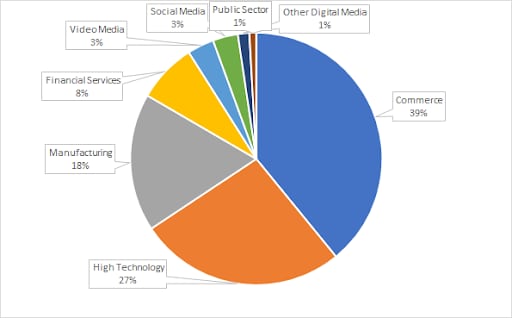 Abb. 2: Am stärksten angegriffene Branchen
Abb. 2: Am stärksten angegriffene Branchen
7.456 unique IPs involved in these attempts
- Top 3 ASNs involved in the attacks were AS4134, AS14061, and AS15169, which are known to be the origin of many malicious activities on the internet (despite being operated by legit cloud providers)
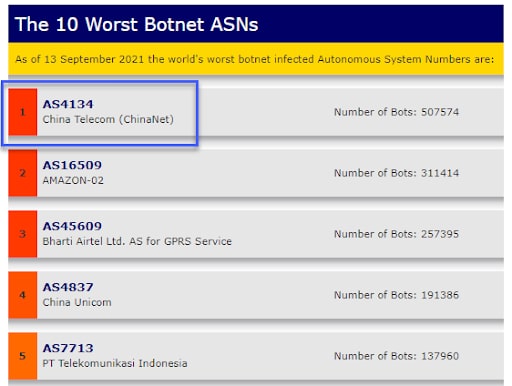 Abb. 3: Die Top 10 der schlimmsten Botnet-ASNs laut Spamhaus
Abb. 3: Die Top 10 der schlimmsten Botnet-ASNs laut Spamhaus
- Die meisten Angriffe hatten ihren Ursprung in den USA (43 %), in China (15 %) und in Indien (10 %).
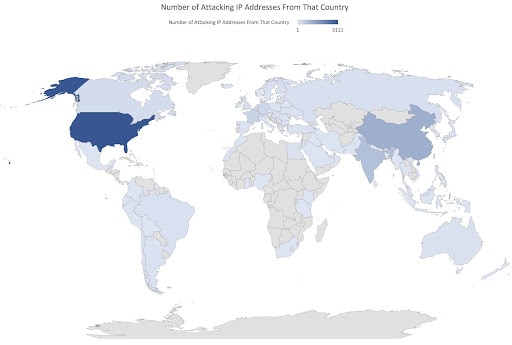 Abb. 4: Anzahl angreifender IP‑Adressen nach Land
Abb. 4: Anzahl angreifender IP‑Adressen nach Land
Unsere bisherige Erfahrung mit ähnlichen Schwachstellen lässt uns vermuten, dass diese Kampagnen sehr wahrscheinlich ihr Arsenal erweitern und serverseitige Ransomware einsetzen werden. So könnten sie die Knowledge Base von Unternehmen sperren oder mit Geschäftsgeheimnissen handeln.
Abwehr von Zero‑Day-AngriffenThe protection provided by Akamai’s platform against web exploitation attempts, including many of the zero-day attacks, benefits from Akamai’s threat detection ecosystem. Furthermore, Akamai’s vast and worldwide coverage provides its customers with unprecedented visibility into threat intelligence, which is translated into protections. “Layered defense” is not just a marketing phrase when operating at Akamai’s scale. Besides the threat intelligence–based Client Reputation, which includes deeper protection layers, such as scanning activity and client requests anomaly detection, Akamai provides HTTP request compliance checks and a collection of generic Kona Site Defender rules to identify “weaponized” adversarial payloads.
Figures 5 and 6 show examples of a real attacker, sending a weaponized HTTP request (i.e., a request with the ability to deploy malware or to take over the server) detected by existing rule sets.
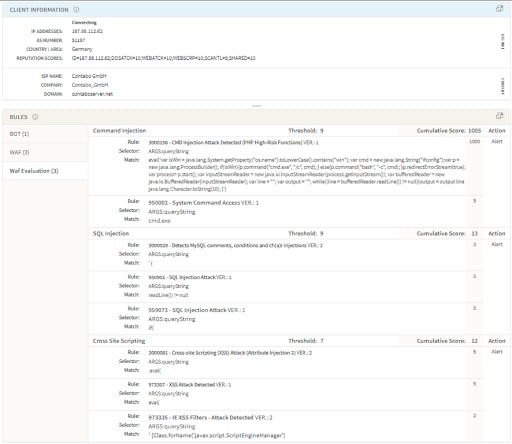 Abb. 5: Von Akamai Adaptive Security Engine erkannt
Abb. 5: Von Akamai Adaptive Security Engine erkannt
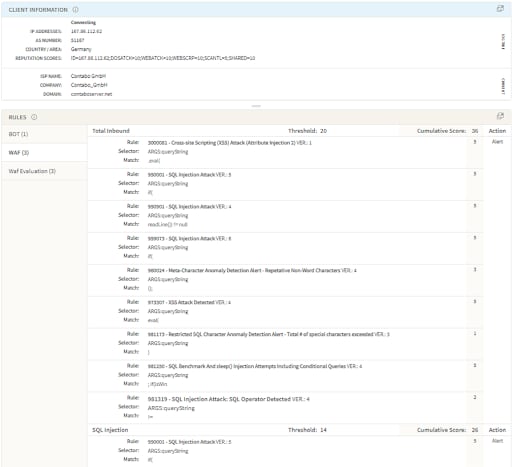 Abb. 6: Von Kona Rule Set erkannt
Abb. 6: Von Kona Rule Set erkannt
Doch der Angriff wurde nicht nur anhand der Böswilligkeit seines Ursprungs erkannt, welche Akamai Client Reputation bekannt war (Webangreifer, Webscanner usw.), sondern auch durch die vorhandenen, allgemeinen Regeln. Sie zielen darauf ab, gefährliche Befehlsmuster zu erkennen, die von Angreifern verwenden werden.
Adaptive Security Engine is detecting and blocking the current weaponized exploits based on existing rules in command injection and cross-site scripting attack groups.
· 950002 — CMD Injection Attack Detected (OS Commands 4)
· 3000156 — CMD Injection Attack Detected (PHP High-Risk Functions)
· 973307 — Cross-site Scripting (XSS) Attack (Eval/Atob Functions)
· 3000081 — Cross-site Scripting (XSS) Attack (Attribute Injection 2)
· 3000005 — CMD Injection Attack Detected (OS commands with full path)
Automated Attack Groups is detecting and blocking the current weaponized exploits based on existing rules in command injection and cross-site scripting attack groups.
· 1000002 — XSS Attack Group
· 1000005 — CMD Injection Attack Group
Kona Rule Set is detecting and blocking the current weaponized exploits based on existing
rules in PHP injection and cross-site scripting attack groups.
· 958976 — PHP Injection Attack (Common Functions)
· 950109 — Multiple URL Encoding Detected
· 973307 — XSS Attack Detected
· 3000081 — Cross-site Scripting (XSS) Attack: Attribute Injection
Final Note
It is the same pattern we have seen in the past, where threat actors show an ability to adapt PoC exploits for fresh zero-day vulnerabilities within a single day. Having a web application firewall as another protection layer might buy you some very precious time until a patch is deployed on the vulnerable target, and significantly reduce the risk on your web applications.
The Akamai Threat Research team continues to monitor any new exploit variations, and rapidly responds by providing rule updates and latest recommendations to customers.





