PCI DSS v4: Uncovering Web Skimming Threats with Payment Integrations
Additional editorial and commentary by Gal Meiri and Emily Lyons

Executive summary
In the world of digital commerce, the payment process is essential during the checkout phase. Handling sensitive customer credit card information online comes with stringent security obligations set by the Payment Card Industry Security Standards Council.
The latest version of the Payment Card Industry Data Security Standard, (PCI DSS v4.0) contains additional requirements to safeguard against client-side threats, including web skimming attacks.
To alleviate some security duties and risks associated with meeting the new PCI DSS v4 requirements, many businesses choose to integrate third-party payment providers into their operations.
In this blog post, we delve into the various models of payment provider integration, explore the unique client-side risks that each model presents, and assess how organizations are still vulnerable to web skimming threats despite offloading their PCI DSS obligations onto these third-party providers.
Understanding payment integrations
Payment integrations are essential for businesses that accept payment cards online. As a critical connection point in the digital commerce checkout process, they provide businesses with a mechanism to authorize payment card details or process the transaction by directly integrating payment methods into a website.
This could involve integrating a first-party processor — or utilizing third-party merchant service gateways, which may introduce iframes or redirect the end user to their site for payment completion.
Web skimming attacks — A major threat to client-side credit card data processing
Web skimming attacks refer to a particular form of cyberattack in which hackers insert malicious JavaScript code into digital commerce websites (directly or through their third-party providers). The ultimate goal of these attacks is to exfiltrate and steal sensitive user data, such as credit card numbers and personal billing details.
The cyber community was first widely alerted to these attacks in 2016 via a report suggesting that approximately 6,000 digital commerce platforms might have fallen victim to web skimming. We’ve since seen a steady stream of reports about digital commerce platforms that have been compromised through web skimming techniques.
The most recent of these reports indicates an ongoing Magecart-style web skimming campaign, potentially placing the personal and financial details of tens of thousands of online shoppers at risk of being stolen and abused or sold on the dark web.
Client-side payment provider integration models
Direct credit card processing
In this model, the website owner manages the complete checkout experience. The payment form embedded on the checkout page collects user-entered credit card and billing information. After the order is placed, the data goes straight to the website's servers for processing, usually via the payment provider's API.
Iframe-based integration
Here, responsibility for the checkout process is shared between the website owner and the third-party payment provider. An iframe, embedded on the website's payment page, hosts the payment form, which is loaded from a domain owned by the payment provider. When the user completes their purchase, credit card and billing details are sent directly from the iframe to the payment provider's servers for transaction completion.
Redirect model
In this scenario, the website owner and the payment provider also share roles. The website owner oversees all aspects of the checkout that don't involve credit card data collection. Upon order placement, the user is redirected to a separate page that’s owned by the payment provider.
This is where the user inputs their credit card and billing information. The payment is processed on the payment provider’s end, and the user is subsequently redirected back to the original website.
Client-side risks associated with payment provider models
Basic web skimming threats
In the direct credit card processing model, web skimming attacks, such as Magecart, are relatively straightforward to implement. These attacks deploy a malicious script on the payment page of the website.
When a user inputs their credit card information into the payment fields, this rogue script captures the data. It then sends this sensitive information to a domain controlled by the attacker, setting the stage for fraudulent activities.
Sophisticated fake form attacks
A more complex variant of web skimming is the "fake form" attack. Here, a malicious script runs on the payment page, much like in the basic web skimming model. However, this script hides the genuine payment form — whether embedded in an iframe or linking to the payment provider's site — and substitutes it with a counterfeit form (Figure).
The user, unaware of the trickery, fills in their credit card information. The rogue script then harvests this data and sends it to an attacker-controlled domain for subsequent fraudulent use. After this, the script typically shows an error message and reveals the actual payment form, nudging the user to input their details again.
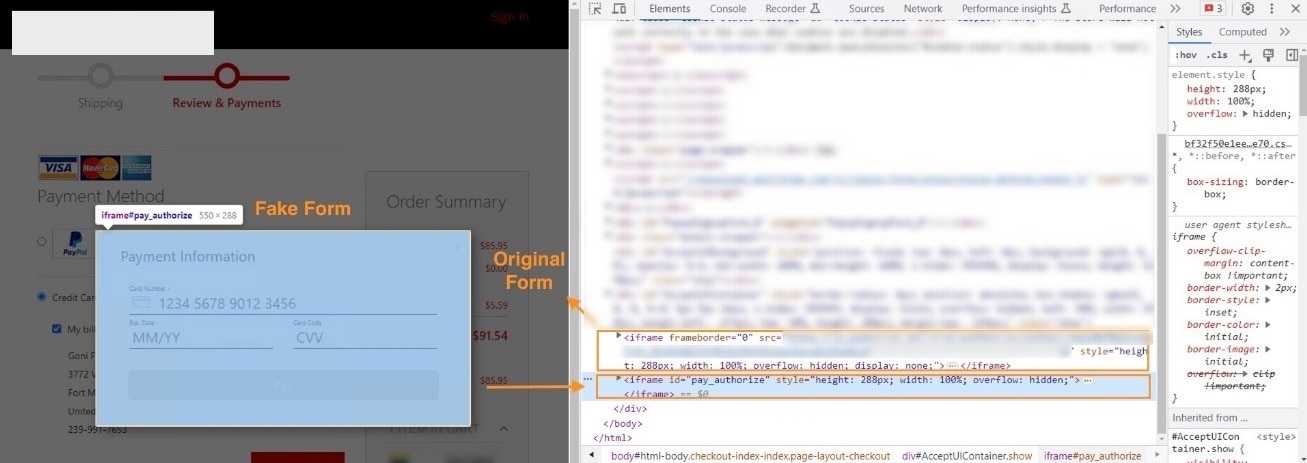 Figure: In a fake form attack, the skimmer hides the original form element and shows a fake one instead
Figure: In a fake form attack, the skimmer hides the original form element and shows a fake one instead
We’ve seen this technique trending across recent web skimming attacks. Attackers are leveraging more sophisticated techniques to hide malicious code in plain sight and bypass preventative security measures, like Content Security Policies, to target new victims and maximize the exfiltration of sensitive data.
Conclusion
Web skimming threat actors are becoming more sophisticated over time, finding new ways to exploit both first-party and third-party payment processes to steal end-user information, including payment card data, on the client side.
Regardless of the payment integration chosen, businesses with a digital checkout process are at risk of becoming a victim to these attacks. Assuming full delegation of PCI compliance to a payment provider may not always translate to bearing no responsibility for a data breach. It’s essential that organizations that process payment card information think beyond compliance and implement strong security measures to effectively protect against these threats and keep online transactions safe.
How Akamai can help
Akamai Client-Side Protection & Compliance helps protect against end-user data exfiltration and shields websites from JavaScript threats. It is designed to detect malicious script behavior and provides actionable alerts to help security teams mitigate harmful activity in real time.
With purpose-built PCI DSS v4.0 compliance capabilities, Client-side Protection & Compliance can also help organizations meet new script security requirements to protect payment card data against web skimming attacks.
June 2024 update
Released in June 2024, PCI DSS v4.0.1 introduces critical updates aimed at enhancing client-side security and ensuring comprehensive protection for payment pages. These updates clarify existing requirements and offer explicit guidance by addressing feedback from stakeholders.
Akamai Client-Side Protection & Compliance is fully aligned with these new standards and provides tools that simplify compliance and bolster security. For a detailed overview, please read the blog post.


