Attack Superhighway: A Deep Dive on Malicious DNS Traffic
Executive summary
Akamai has conducted an investigation of malicious command and control (C2) traffic to gain insight on prevalent threats in corporate and home networks.
According to the data, between 10% and 16% of organizations have encountered C2 traffic in their network in any given quarter. The presence of C2 traffic indicates the possibility of an attack in progress or a breach.
26% of affected devices have reached out to known initial access broker (IAB) C2 domains, including Emotet and Qakbot-related domains. IABs present a large risk to organizations as their primary role is to perform the initial breach and sell access to ransomware groups and other cybercriminal groups.
Attackers are abusing network-attached storage devices through QSnatch, thus putting backups and sensitive data at risk of being stolen or compromised.
30% of affected organizations are in the manufacturing sector, underscoring the real-world implications of cyberattacks such as supply chain issues and disruptions to everyday living.
Attacks on home networks are seeking to abuse new attack surfaces. A significant amount of attack traffic in home networks can be correlated with mobile malware and Internet of Things (IoT) botnets.
Through our analysis, we spotted a burgeoning outbreak of FluBot malware in Europe, Latin America, and Asia. The malware spreads through mobile messages using social engineering techniques, and once installed will attempt to propagate further and steal the victim’s banking credentials.
Domain Name Servers — a highway for attack traffic
The modern threat landscape is posing significant challenges to security practitioners. As we’ve recently learned from our analysis of ransomware groups, modern attackers are working toward a more hands-on approach to breaching and moving laterally within networks. This makes C2 communication an important component of a modern attack. C2 can be used to facilitate an attack in progress, to download the next-stage malware and other payloads, and to establish backdoor access. These transactions and attack traffic often pass through the Domain Name System (DNS).
Attackers have been using domain-generating algorithms for more than a decade as a means to evade detection and circumvent security measures. Although traffic over DNS is often seen as the interaction between users and websites, it can, in fact, contain large amounts of malicious traffic, and act as an important part of the attack’s infrastructure. Akamai’s secure web gateway provides not only visibility into this traffic, but also the ability to block the traffic before it can reach the attacker’s domain. In adopting a Zero Trust mindset, we must consider where and how attacks can be disrupted, and where to apply these principles.
In the latest edition of the State of the Internet/Security report, we provide a thorough analysis of malicious DNS traffic from home users and enterprises worldwide, including correlation with attacker groups and their tools. This could arm organizations with important information regarding the most prevalent threats to their environment, and aid security practitioners in evaluating their defense posture and conducting gap assessments to address the techniques and methodologies leveraged against them.
Danger ahead: the pervasiveness of malicious traffic in organizations
Multistage attacks have become a staple of the modern attack landscape. Attackers are finding increased success when they are able to work together (or hire one another), or when they are able to combine various tools in a single attack. C2 is pivotal in the success of these attacks. They can be used not only for communication, but also to facilitate downloading a payload and the next-stage malware to move the attack onward.
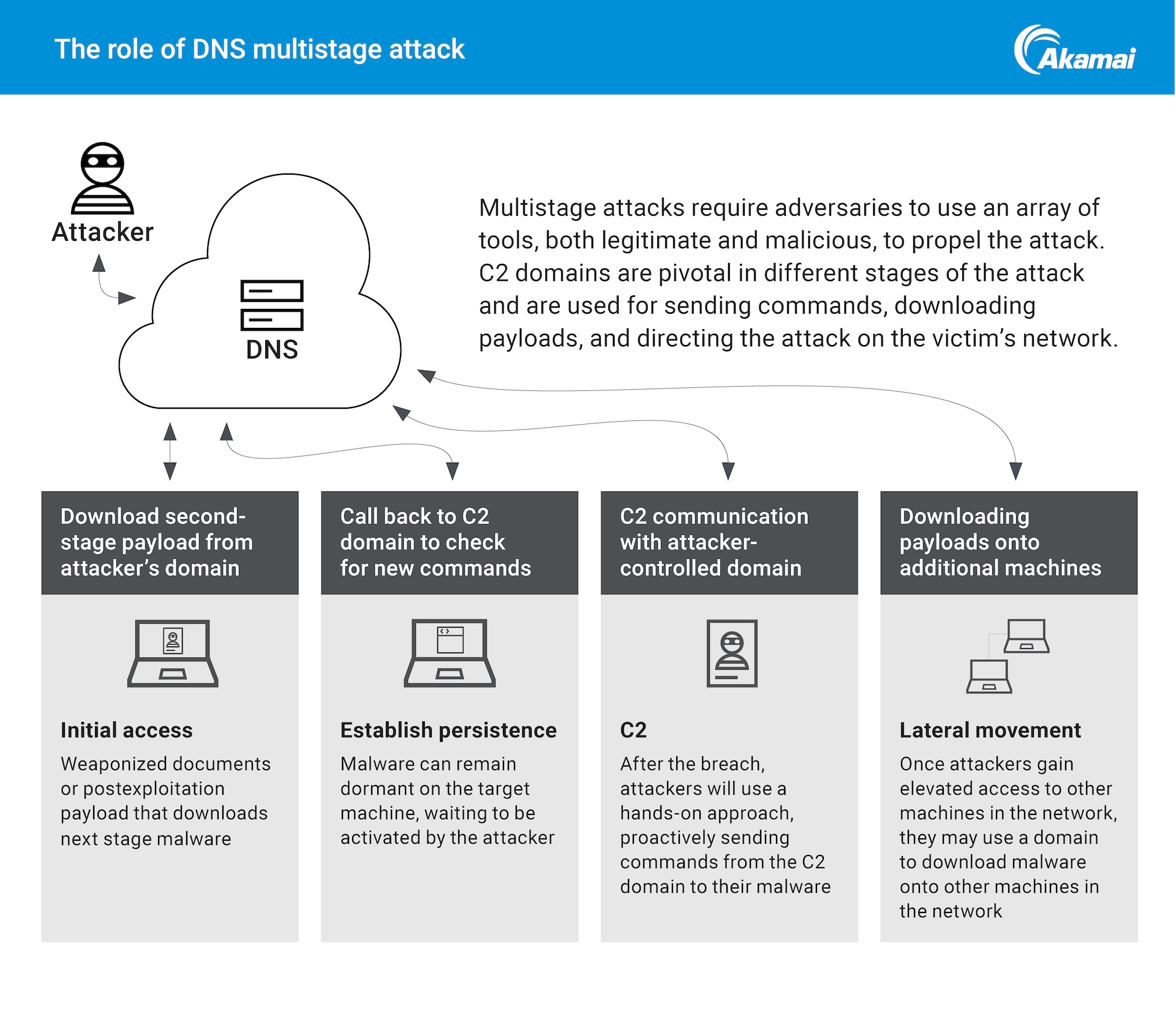 Fig. 1: DNS provides visibility on various attack activities that security practitioners can use to mitigate attacks in progress.
Fig. 1: DNS provides visibility on various attack activities that security practitioners can use to mitigate attacks in progress.
According to our DNS data, between 10% and 16% of organizations have experienced at least one instance of C2 traffic attempting to travel out of their network, in any given quarter (Figure 2). This may be indicative of malware attempting to communicate with an operator and is a potential sign of a breach. This C2 traffic was blocked by our solution from reaching its destination, but successful attacks might have resulted in data exfiltration, ransomware attacks, and more. Our research highlights the effectiveness of applying Zero Trust principles to DNS to prevent malware from progressing in a network or causing harm.
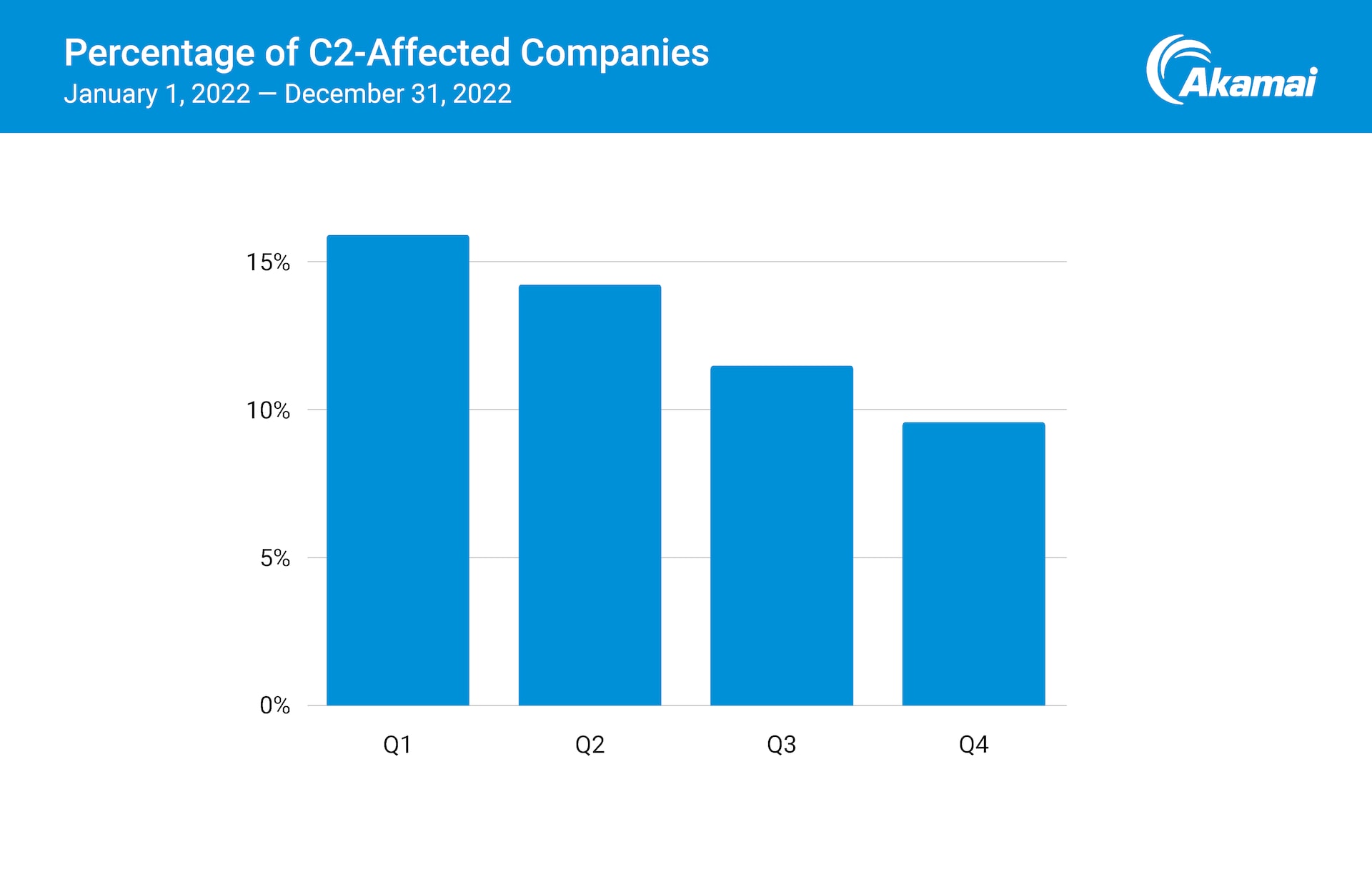 Fig. 2: An analysis of malicious C2 traffic shows the percentage of organizations that have reached out to a C2 domain throughout the year
Fig. 2: An analysis of malicious C2 traffic shows the percentage of organizations that have reached out to a C2 domain throughout the year
In Figure 3, the C2 domains we’ve observed could be categorized into domains with and without attribution to a specific threat family or attacker group. Attacker groups are then classified into IABs, botnets, and RaaS groups. Our data reveal that IABs pose one of the biggest threats to corporate networks, as do botnets aimed at data exfiltration.
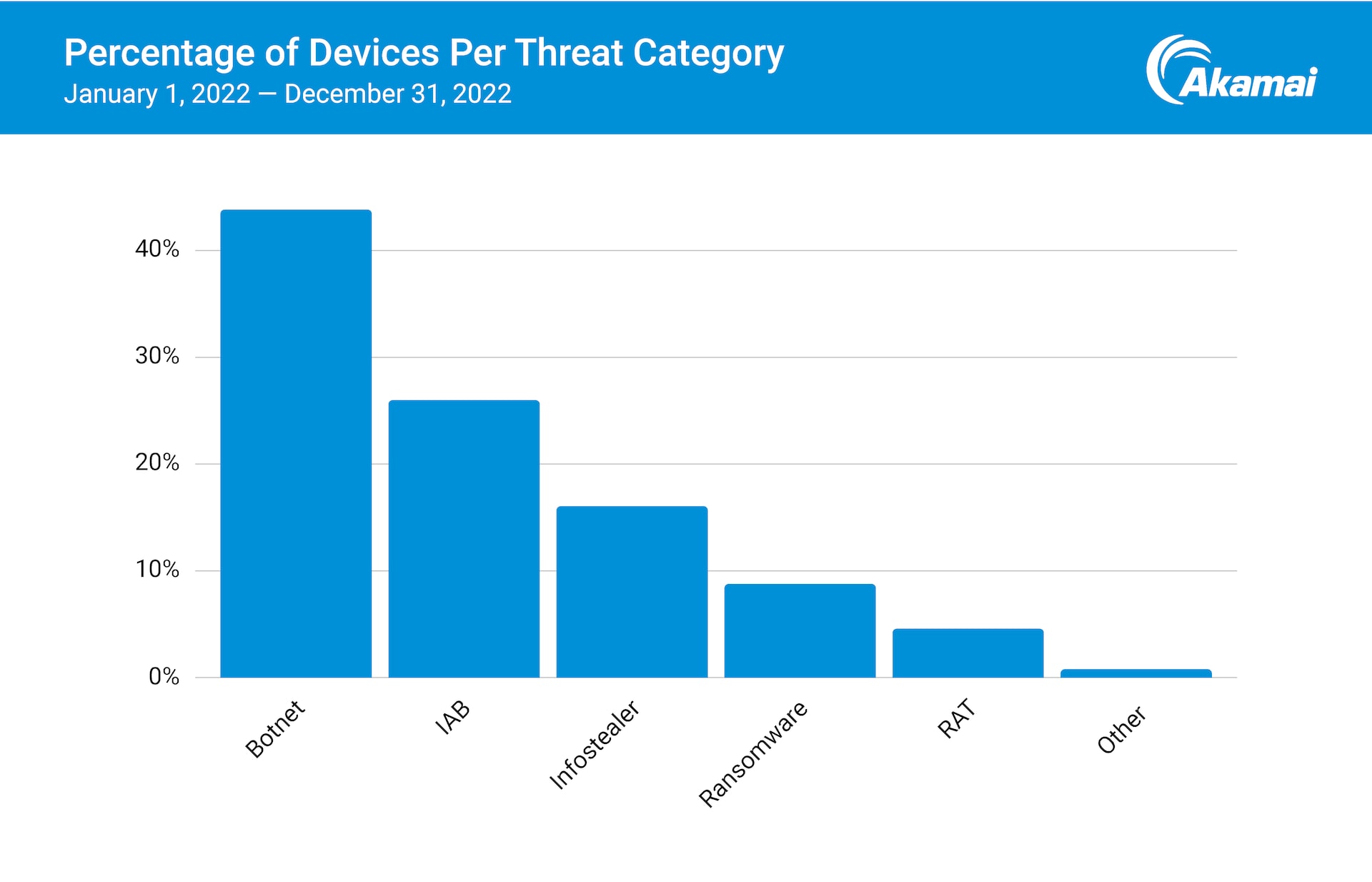 Fig. 3: Enterprises are predominantly targeted by botnets, followed by IABs and infostealers
Fig. 3: Enterprises are predominantly targeted by botnets, followed by IABs and infostealers
We also observe ransomware, remote access tools (RATs), and infostealers in the mix — all have a critical role to play in various attack stages. And with tools readily available in the underground to both novice attackers and experienced cybercriminals that allow them to gain initial entry, remain hidden in the network, and further the attack, organizations are more than ever susceptible to cybercrime. As we course through these groupings, we will also establish the intersections at which they operate and the potential implications and impacts on organizations. We provide further analysis of attacker groups within each category in our full report.
Home networks show heavy traffic from botnets
Home users represent a demographic that is often not as secure as a corporate environment, but this demographic does not present the same monetary return. Attackers know this and so look for ways to monetize their ability to more easily infect home devices. For example, they launch large-scale campaigns hoping to compromise as many devices as possible in spray and pray tactics, whereas attacks against enterprises are highly targeted. As we shift our focus to home users, we will examine the malicious DNS traffic of home networks by analyzing an anonymized sample of the millions of malicious flagged queries from the past six months to demonstrate what threats users should be concerned about.
In our analysis, we found that Pykspa, a threat that spreads through Skype by sending malicious links to the affected users’ contacts, accounted for 367 million DNS queries flagged globally (Figure 4). Pykspa queries the Skype configuration to gather personal information about the affected users. Interestingly, it checks the language interface of the affected user’s Skype and if it’s one of the many languages they are monitoring, the malware tweaks the spammed Skype message accordingly.
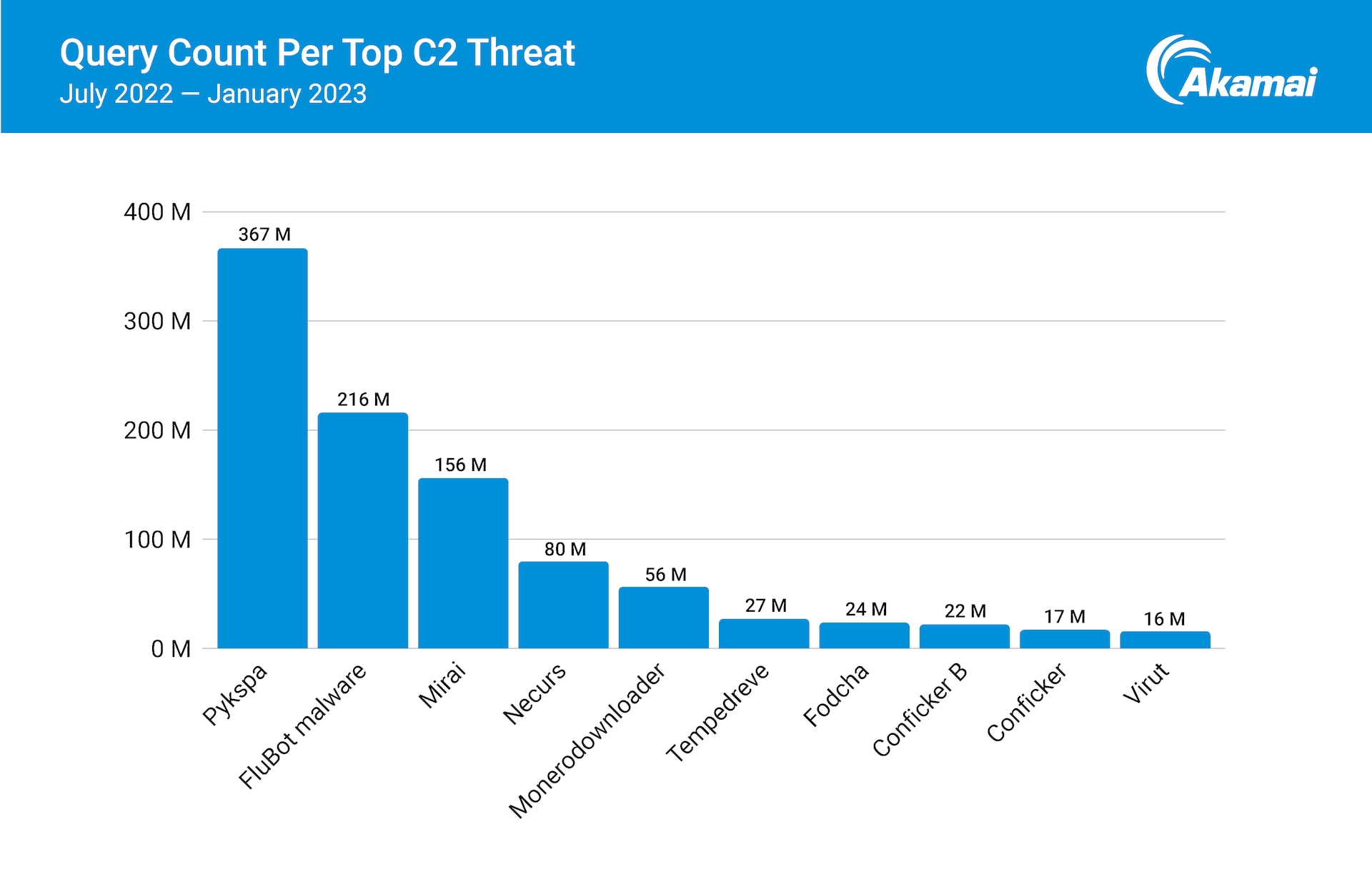 Fig. 4: Pykspa, FluBot malware, and Mirai are the top three botnets observed in the DNS traffic of home networks
Fig. 4: Pykspa, FluBot malware, and Mirai are the top three botnets observed in the DNS traffic of home networks
It is particularly interesting to note the expansion of the threat surface used against home users. Two of the most prominent botnets with C2 traffic that we were able to identify as affecting home users are FluBot and Mirai. FluBot, an android malware, spreads via SMS and infects a victim’s mobile device in order to steal banking information. Mirai is a well-known botnet targeting IoT devices. Both botnets, which are examined in further detail in the report, have been spreading like wildfire in various regions around the world, and demonstrate the attackers’ shift away from traditional devices.
Learn more
For more information on the most prevalent threats against enterprises and home users and the risks posed by them, download our State of the Internet report Attack Superhighway: A Deep Dive on Malicious DNS Traffic.




