Worried About Bot Attacks on B2C APIs? You May Be Missing a Bigger Risk

Many security teams now realize that APIs are one of their biggest security blind spots. Many have responded by zeroing in on their most obvious area of API risk: the business-to-consumer (B2C) APIs that external-facing mobile and web applications rely on.
Because these B2C APIs serve the outside world, they are particularly vulnerable to attack via bots and other automated methods. So, in response to those threats, many organizations have deployed specialized bot mitigation tools or use first-generation API products or web application firewalls (WAFs) to tightly manage access to B2C APIs.
These are sound practices, but B2C APIs only represent the tip of the iceberg when it comes to overall API risk. A much greater set of API risks often remains hidden below the surface — in an organization’s business-to-business (B2B) APIs.
B2B APIs are the building blocks of digital transformation
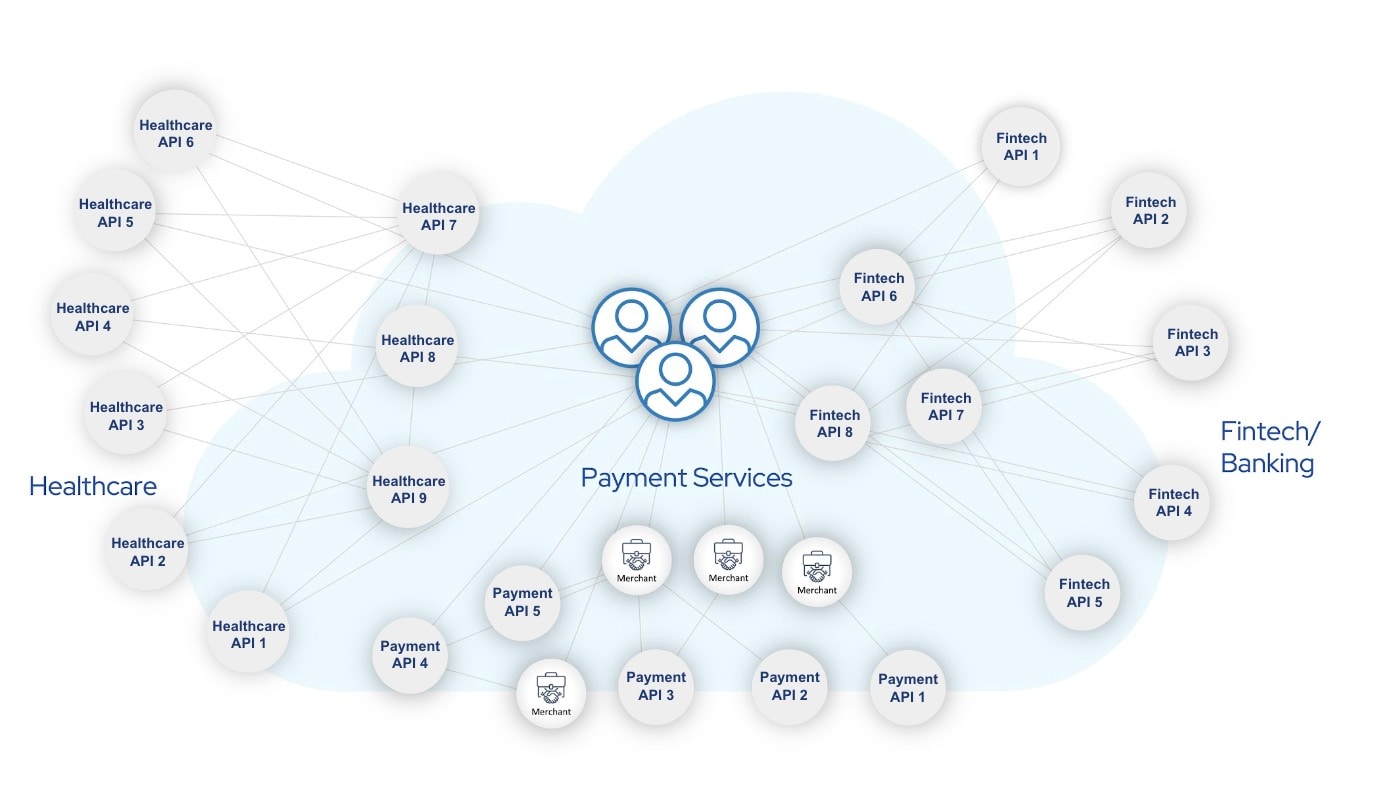
While B2C API security is now relatively well understood, many security teams overlook the central role that B2B APIs now play in their organization — and the potentially devastating risks that they expose. Digital transformation is a must for any organization that wants to stay competitive in today’s marketplace. But while business partners integrate their key operational functions through APIs, that integration creates a complex web of interconnectivity (Figure).
Many of these API-based connection points provide direct visibility and access to core business functions. This may be perfectly fine when the functionality and data is limited to the intended use by trusted partners. But in the hands of a rogue partner or external threat actor, this level of API access can be exploited in ways that could have devastating business impacts.
API-to-API traffic is an overlooked attack vector
1. B2B APIs are often written and maintained — and sometimes even managed — by teams within an organization that are different from the teams that are managing the B2C APIs.
For example, the B2B APIs for resellers, suppliers, and other business partners are owned by either the business unit or the IT department. And quite often, methodologies and processes differ greatly among departments.
2. B2B APIs are generally viewed as more trustworthy because they are authenticated as known partners from established companies. This familiarity from well-known partners as API consumers often adds to the willingness to ignore API security best practices.
But in reality, companies are made up of people, and people make mistakes. They may misplace API keys or may be compromised, socially engineered, or otherwise turned into malicious insiders.
3. Third, because B2B APIs are authenticated, and typically serve a smaller number of API consumers than B2C APIs, it is easy for API and security teams to be lulled into a false sense of security. Many organizations fail to anticipate how B2B APIs can be abused in unintended ways, and they underestimate the impact on the business.
For example, an authenticated partner using your API may gain an unfair advantage — or move into competition against your business — by abusing the access they have to your data and business functions. Or worse, a trusted partner could be breached, giving a threat actor free rein to your sensitive resources and the time to probe for additional damaging API abuse vectors.
Mitigation challenges
Even when these risks are understood, they can’t be mitigated with bot mitigation tools, WAFs, or first-generation API security products. One big reason for this is that most organizations don’t have a complete inventory of the B2B APIs exposed by their organization.
Another key challenge is the fact that typically B2B APIs aren’t subjected to predictable attack patterns or traffic volume spikes that suggest bot activity. More often, they are attacked with forms of API abuse that blend in seamlessly with legitimate usage.
Even if the security team has a complete B2B API inventory that they are actively monitoring, the team is unlikely to detect these forms of API abuse using traditional attack signatures. There are no signatures that catch unique or zero-day API abuse.
Broad visibility and behavioral analytics are the keys to effective B2B API security
So how can businesses take greater control over their B2B API security? The two most important steps they can take are to:
- Implement broad and continuous API discovery and visibility capabilities
- Apply behavioral analytics technology to differentiate abuse from legitimate activity
Broad and continuous API discovery and visibility
Although most organizations strive to implement well-structured processes and governance for their APIs, rogue and shadow APIs are a fact of life nearly everywhere. Often, they aren’t generally created with malicious intent.
The reality is that most businesses have many teams and moving parts, all of which are evolving quickly. Throw in the occasional merger or acquisition and suddenly even the most proactive organization will likely find itself in the dark when it comes to seeing the APIs it is exposing.
The only answer is to continuously monitor all environments for API activity. This can be accomplished by capturing and analyzing API activity traffic and logs from all available sources, including:
Packet brokers
Traffic mirroring
API gateways
Content delivery networks
Cloud provider logs
Log management systems
Orchestration tools
Once you understand the full scope of your organization’s API activity — and have a plan to maintain your visibility as change occurs over time — you can then move on to B2B API protection.
Behavioral analytics technology
The key to closing risk mitigation gaps for B2B APIs is to augment or replace the tools and techniques you’re using to protect B2C APIs with an approach based on behavioral analytics.
Why? As many security teams discovered with extended detection and response (XDR) for enterprise security, behavioral analytics makes it possible to baseline legitimate or expected behavior and spot anomalies that would be impossible to anticipate in advance.
The same concepts can be applied to application security. It starts with profiling the users and business processes represented in your API data. Once you do that, you can more easily spot anomalies that signal your B2B APIs are being abused or, at the very least, being used in unexpected ways.
See the complete picture of your API security posture
Embracing API behavioral analytics to gain a greater understanding of API use — and abuse — doesn’t need to be complicated. You don’t need complex and costly on-premises security infrastructure. With Akamai API Security, you can gain your first insights in minutes and at scale to help you understand and protect your entire API footprint through our 100% percent software as a solution (SaaS) approach.
Take the first step
Akamai’s API security solution can help you find and protect all your APIs and offer reassurance that your data is safe. Our platform-agnostic SaaS-based solution brings XDR capabilities to application and API security.