What Does XDR Have to Do with API Security?

A growing number of organizations understand the critical role that some form of API security plays in their overall security and compliance posture. For many of these organizations, however, it can be challenging to understand where API security technology investments fit in with their broader security stack.
Two key questions
Many security silos have evolved over time to include more unified extended detection and response (XDR) approaches. Akamai sees an opportunity to bring the power of XDR to API security. But this opportunity raises two key questions that both vendors and security teams must consider:
Can XDR as we know it today be extended to include API security?
Should API security be addressed by a separate set of security tools and practices that apply the best innovations of XDR to the unique security challenges posed by APIs?
Detection and response silos
Technologies for detecting and responding to security threats have existed for decades. Most silos started with narrow goals in mind, including:
Endpoint detection and response to protect endpoints and, in some cases, servers
On-premises network detection and response (NDR) to detect and mitigate threats on enterprise and data center networks
Cloud NDR to extend similar concepts to cloud or hybrid cloud infrastructure
Secure email gateways to detect and mitigate email-based attacks
External threat intelligence feeds to provide early warning signals about possible threats
Each of these played an important role in reducing risk, but their effectiveness was limited by the fact that they operated in individual silos. Each lacked information from the others that could provide a more complete and accurate picture of threats and risks. Instead, they put the burden on security teams to connect the dots.
Collapsing silos to create XDR
XDR innovations advanced security in three important ways. These innovations:
Converged detection and response signals across all the silos noted above into a unified model
Harnessed cloud scale and techniques like machine learning and behavioral analytics to monitor large amounts of data over longer time horizons to deliver more complete and more meaningful security insights and (perhaps more important) to establish baseline behavior to identify deviations
Presented security teams with human-understandable, timeline-based views of security incidents that avoid alert fatigue and make it faster and easier to respond decisively
When implemented and adopted correctly, XDR has a transformational effect on security team productivity and effectiveness.
Can the principles of XDR better protect APIs?
NOTE: There are APIs that involve users, which are referred to as business-to-consumer (B2C) APIs. In this post, we’ll focus on the rapidly growing space of externally facing APIs exposed to partner applications, plus the vast space of machine-to-machine (M2M) API-based communications.
Even with XDR providing significant security value, APIs are largely missing from the XDR picture. Today, we see many organizations using XDR to focus on enterprise security infrastructure where the risks center on users connecting to applications and cloud services running on hosts.
In contrast, the traffic of APIs that service M2M communications is different from users and hosts. Consequently, the characteristics of API security threats can also be quite different from enterprise security threats. For example, subtle attacks like business logic abuse do not exist in the traditional enterprise security space and require specialized detection and mitigation approaches.
As a result, API security might not gain very much from organizational use of XDR that’s focused on enterprise security activity and threat information.
But that does not disqualify the use of XDR principles for API security. In fact, the very nature of B2B or M2M API traffic suggests that XDR principles must be used because, with a vast quantity of traffic, only “extended detection” can detect unnoticed API abuses.
The same concepts applied in innovative ways
Can existing XDR approaches be extended to include APIs? Probably not. Trying to shove API security, with unique attributes like a DevSecOps focus and M2M communications into a standard XDR model may not be possible, let alone valued by current consumers of existing XDR solutions.
However, many of the core concepts of XDR are exactly the same concepts that need to be used to protect APIs at scale (Figure). They just need to be applied in unique and focused ways.
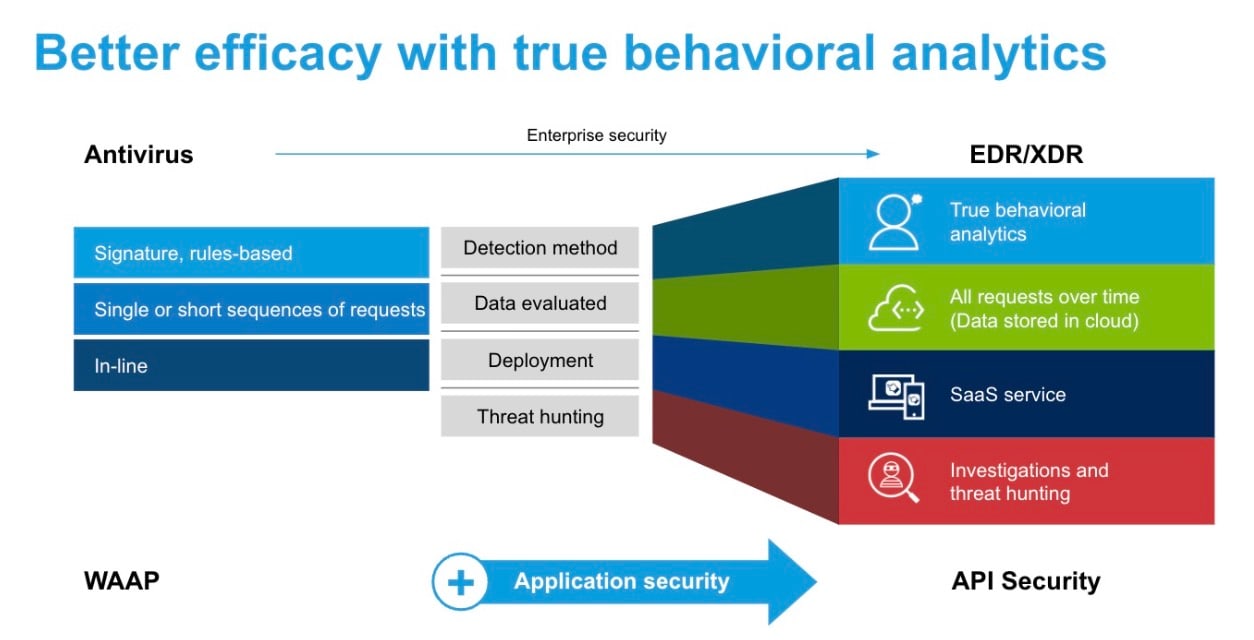 Many core innovations of XDR can be applied to APIs
Many core innovations of XDR can be applied to APIs
That is the Akamai API Security innovation: We’re applying to application security many of the same XDR concepts that transformed enterprise security.
Leading the evolving API security industry
Much in the same way that enterprise security evolved from attack signatures and point-in-time detection to behavioral analytics, Akamai is leading the API security industry through the same evolution with:
Extended detection via broad API traffic data collection to a cloud-based service with long-term data retention and enriched data
True machine learning and behavioral analytics
Contextual investigations and threat hunting
Automated, flexible response mechanisms, including software development lifecycle and API Gateway integrations
We believe that the benefits of this transformation will be even greater for APIs and application security than they were for enterprise security. Security teams will not be able to keep pace with the vast amounts of M2M communications without an assist from behavioral analytics.
Applying behavioral analytics to large datasets is also a better way to address the nuances of application security threats. For example, API abuse cannot be detected effectively through inline or point-in-time analysis. Creating baselines of normal behavior to detect anomalies is the only way to differentiate abuse from nearly identical legitimate activity.
What about threat hunting?
Several XDR solutions on the market today enable threat hunting in their user interfaces and a subset of those solutions offer managed threat hunting. Akamai’s utilization of XDR principles offers these services as well. The Akamai user interface includes a powerful API threat hunting toolset. Alerts can trigger teams to search for malicious behavior using entity timelines, logical expressions to narrow down traffic, and more.
We recognize that API security is a new solution and API threat hunting skills in your organization may still be in the growing stages, so we offer Akamai API Security ShadowHunt, the industry’s only managed API threat hunting service staffed by experts.
Apply the principles of XDR to your APIs today
Are you ready to apply XDR concepts to your growing set of API security challenges? Continue to explore how Akamai API Security can bring greater clarity to your API security and see the results fast!




