Shield NS53 Protects Your Origin DNS Infrastructure from NXDOMAIN Attacks
DNS: The critical internet infrastructure that’s under constant attack
Imagine if you had to type in “142.250.80.14” to search for the latest information on Taylor Swift events, or “2600:1406:3a00:281::b63” to learn how you can protect and power the online experiences of your users. Thankfully, the global Domain Name System (DNS) translates words and names that humans can easily remember — like Google and Akamai (and Taylor Swift) — into IP addresses that computers understand. This makes DNS a critical and foundational element of our digital interactions and experiences. If a company’s DNS systems go down, their online presence goes down.
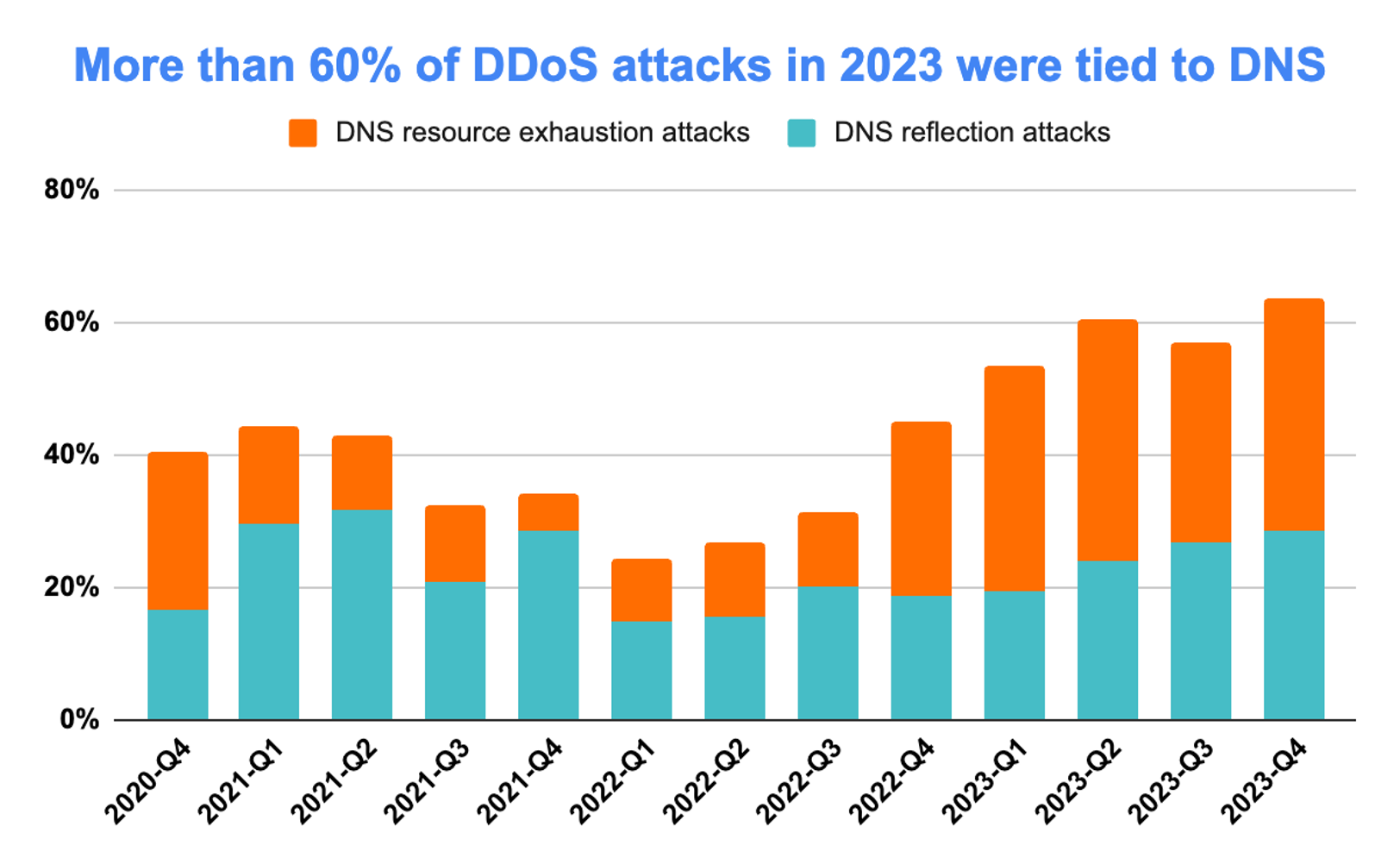
Therefore, it is probably not a surprise that cybercriminals continuously attack the DNS systems of their targets with distributed denial-of-service (DDoS) attacks. According to Akamai’s internal DDoS threat intelligence, more than 64% of the total DDoS attacks in the fourth quarter of 2023 had a DNS component (Figure 1).
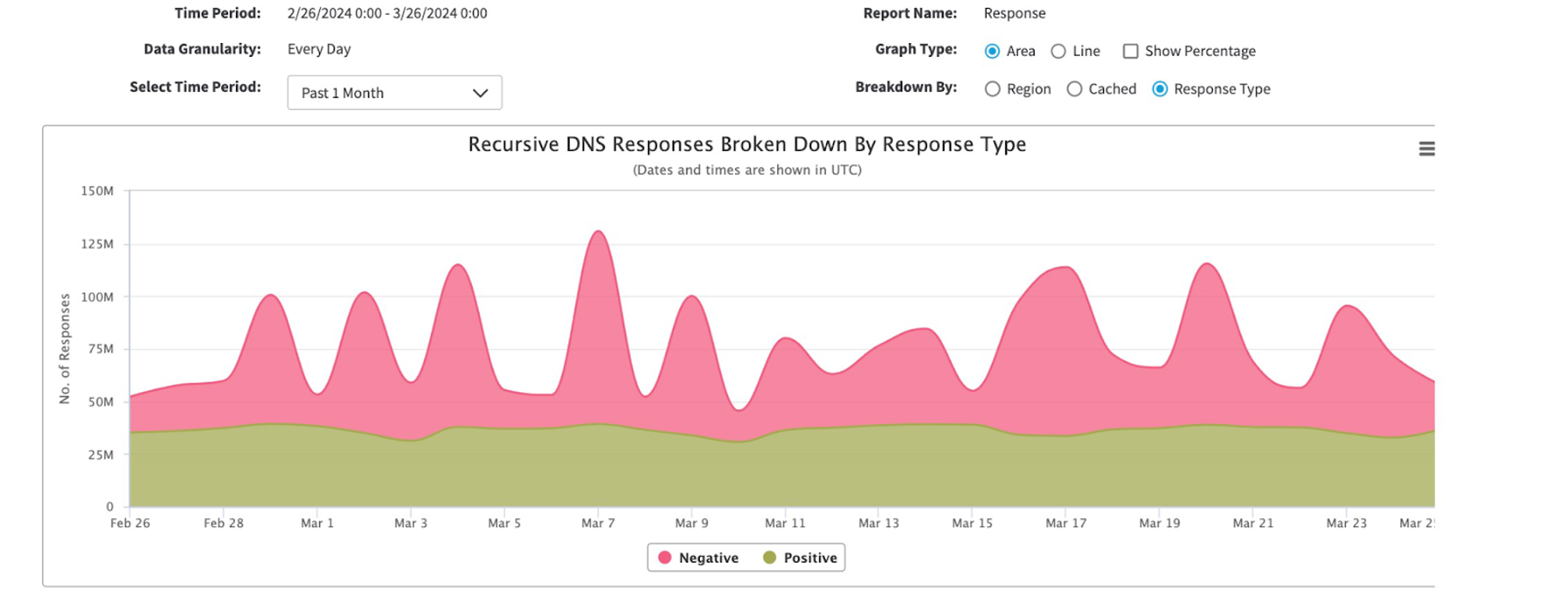
One such attack type is the NXDOMAIN, or DNS resource exhaustion attack. Figure 2 shows how a leading global financial services company’s DNS infrastructure was targeted with sustained NXDOMAIN traffic over several days in the first quarter of 2024. Akamai blocked the DNS attack in zero seconds and successfully protected the DNS customer's infrastructure from any impact.
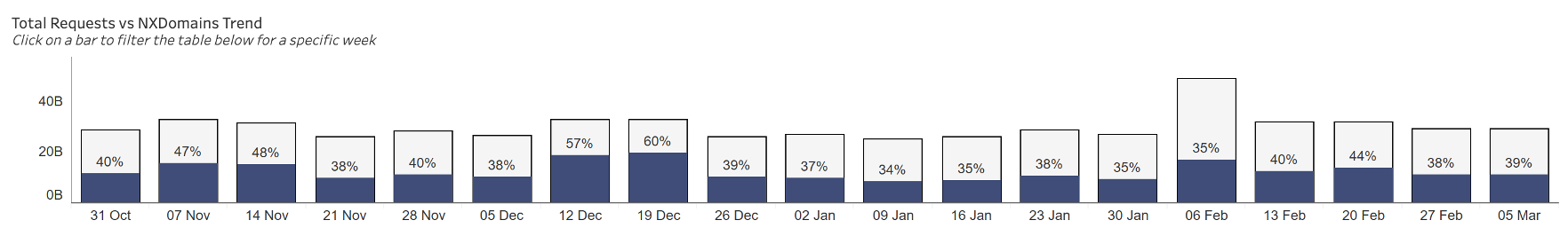
Analyzing the trend of DNS queries for the top 50 financial services customers from October 2023 through March 2024 shows that, on average, roughly 40% of the DNS queries processed and blocked by Akamai were illegitimate NXDOMAIN queries (Figure 3). The volume of NXDOMAIN queries reached as high as 60% in December 2023, indicating an attempt by cybercriminals to bring down the DNS infrastructure of these companies during the holiday season. Akamai successfully thwarted these attempts with its robust DNS security solutions.
Protecting against sustained and increasing DNS attacks has become an urgent challenge for businesses and government institutions that aim to provide a seamless digital experience for their customers, end users, and employees.
The anatomy of a typical DNS resource exhaustion attack
DNS resource exhaustion attacks are popularly known by several other names, including NXDOMAIN attacks, pseudo-random subdomain (PRSD) attacks, DNS water torture attacks, and DNS flood attacks, among others. Before we take a high-level view of how cybercriminals architect this type of attack to make sense of the various names in technical and popular discourse, let’s remind ourselves how DNS usually works.
A day in the life of DNS
When an individual types a web address (a domain name), like www.akamai.com, or a subdomain name, like www.ir.akamai.com (for the investor relations page), into their browser’s uniform resource locator (URL) bar, the steps in Figure 4 take place behind the scenes.
Client query |
→ ← |
DNS recursive resolver (often provided by ISPs) |
→ ← |
DNS top-level domain (TLD) nameserver |
→ ← |
A company’s authoritative domain nameserver |
Fig. 4: The behind-the-scenes steps when a web address is typed into a URL bar.
DNS recursive resolvers often respond to user queries from their cache of previous responses. If no cache response is available, the request gets forwarded to the origin authoritative domain nameserver. If the nameserver cannot answer an IP address for a particular DNS request, it returns an “NXDOMAIN” or “nonexistent domain” response to the resolver.
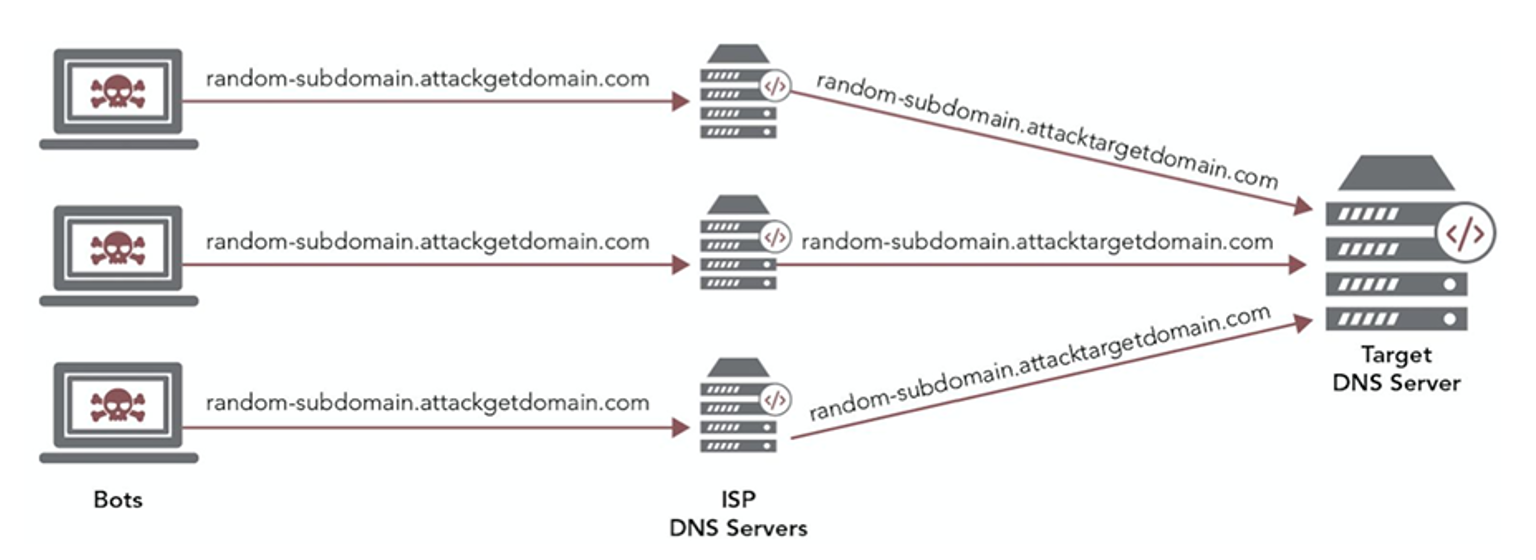
During a DNS resource exhaustion attack, cybercriminals flood an organization's DNS infrastructure with a high volume of random subdomain queries, often running into millions of queries per second (Figure 5).
The intent is to overwhelm the origin components of the DNS infrastructure stack — global server load balancers (GSLBs), firewalls, nameservers, etc. — with illegitimate queries such that the system cannot service legitimate queries from users. These application layer (Layer 7) DNS DDoS attacks can use TCP and UDP packets, often requiring no spoofing to exhaust the DNS servers.
Select key tactics used by cybercriminals to launch resource exhaustion attacks
Unique queries
The attacker crafts DNS queries for nonexistent or rarely accessed domain names. Each query is designed to appear unique, meaning that the DNS server or any upstream resolver hasn't ever seen it.
No repeats
To avoid detection and mitigation, the attacker ensures that each illegitimate DNS request differs from the previous DNS requests. This prevents upstream resolvers from caching the request and its response, as they may not have encountered the same query before.
Avoiding DNS resolver cache
By constantly changing the queries, the attacker aims to bypass caching mechanisms in upstream resolvers. DNS caching helps resolve subsequent queries faster by storing previously resolved domain names and their corresponding IP addresses. However, if the queries are unique each time, caching becomes less effective in mitigating the attack.
An example of a random subdomain DNS query
A legitimate subdomain of the Akamai website, www.ir.akamai.com directs users to the investor relations page. However, a query like www.randomsubdomain.akamai.com is an illegitimate query. Recursive resolvers wouldn’t have any cache response for such a query and would forward the request to Akamai’s DNS nameserver to answer for the IP address of this nonexistent page. As it should, Akamai’s DNS servers would respond with a NXDOMAIN response (Figure 6).
NXDOMAIN attacks constitute a significant challenge for network security leaders because they cause the DNS server(s) to use their resources to look up nonexistent subdomains. This technique increases the load on the origin DNS infrastructure and consumes network resources, potentially leading to service degradation or even downtime for legitimate users trying to access legitimate services.
Protecting your DNS infrastructure from NXDOMAIN attacks
Akamai Edge DNS offers a comprehensive, purpose-built, cloud-based authoritative DNS solution that uses the scale, security, and capacity of Akamai Connected Cloud to distribute your DNS zones across several thousand servers across the globe.
Customers delegate their zone authority to Edge DNS by updating nameserver records at the registrar and using those provided by Akamai. Akamai Edge DNS provides an unparalleled attack surface and proactive security controls that can mitigate even the largest DNS attacks without impacting a customer's DNS performance, reliability, and availability.
In many instances, organizations maintain on-premises DNS infrastructure and cannot delegate their authoritative zones to an external cloud solution to protect themselves from various types of DNS attacks. The reasons for such preferences range from compliance concerns to dynamic configurations on origin GSLBs to a simple desire to manage their authoritative zones at the origin.
Oftentimes, this is a business decision based on the fact that a company might have already made significant capital investments in building on-prem DNS infrastructure, therefore delegating zones to the cloud would not be a financially viable option, at least in the near term.
In certain hybrid scenarios, an organization that has delegated some of its authoritative DNS zones to Edge DNS but prefers to serve the remaining zones from an on-prem origin leaves the on-prem infrastructure vulnerable to DNS resource exhaustion attacks.
So, how can an organization in one of these scenarios protect themselves from DNS resource exhaustion attacks? Enter Akamai Shield NS53!
Akamai Shield NS53: One-stop Protection for on-prem and hybrid DNS infrastructure
Get protection from NXDOMAIN attacks
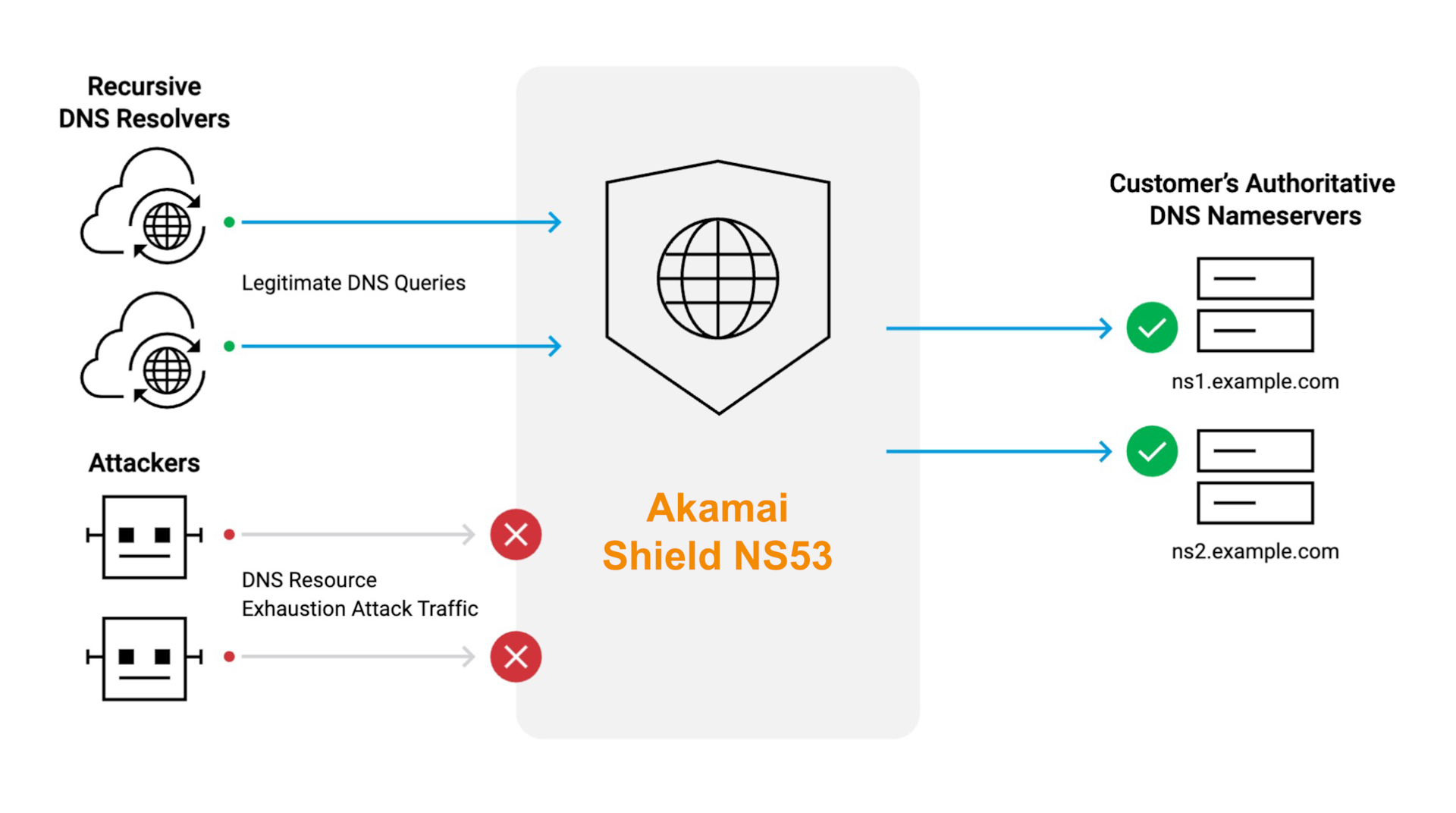
Akamai Shield NS53 is a bidirectional DNS proxy solution that protects key components of your origin DNS infrastructure from resource exhaustion attacks. Using an intuitive user interface on the Akamai Control Center, you can self-configure, administer, manage, and enforce your organization’s specific dynamic security policies in real time. Illegitimate DNS queries and DNS attack floods are dropped at the very edge of the Akamai network, keeping your DNS secure, reliable, and available (Figure 7).
Optimize your DNS performance
Shield NS53 also helps alleviate the load on your on-prem DNS infrastructure by responding to legitimate queries from the cache and forwarding queries to the origin name servers only when necessary. Additionally, the solution reduces latency and improves user experience by accessing Akamai’s global NAMES anycast network, which is built with thousands of servers, to respond to user queries from the closest point of presence.
Optimize your total cost of ownership
Theoretically, you can protect your DNS from resource exhaustion attacks by adding more capacity. If you have more resources, it will take larger and longer attacks to exhaust those resources. However, it is quite evident that such an approach is neither financially viable nor a scalable technical solution.
Shield NS53 helps organizations protect their financial investment in their existing DNS infrastructure, including nameservers, GSLBs, and firewalls, by fortifying the already deployed solutions against modern resource exhaustion attacks, thereby lowering the total cost of ownership and maximizing the return on your investment in existing DNS infrastructure.
A cheat sheet on how Akamai can protect your digital infrastructure
Akamai offers a comprehensive portfolio of solutions to protect your digital infrastructure from various DDoS attacks. You can use the following table as a cheat sheet on how to tailor your security solution(s) based on your specific needs.
Attack type |
Recommended solutions |
|---|---|
DNS NXDOMAIN attacks |
Akamai Edge DNS, Akamai Global Traffic Management, Akamai Shield NS53 |
DNS direct queries attacks |
Edge DNS, Global Traffic Management, Shield NS53 |
DNS reflection and DNS amplification attacks |
Akamai Prolexic, Akamai Network Cloud Firewall |
DNS source IP spoofing and DNS TTL attacks |
Edge DNS, Global Traffic Management |
Layer 3 and Layer 4 DDoS attacks (across all ports and protocols) |
|
Application layer (Layer 7) DDoS attacks not related to DNS (not on port 53) |
Akamai App & API Protector |
Table: How you can tailor your security solution based on your specific needs
Conclusion
It’s an understatement to say that we live in an incredibly digitally connected world. Almost all aspects of our day-to-day lives are powered by digital interactions. One of the cornerstones of these digital interactions is the underlying DNS infrastructure that makes it all possible. It is, therefore, absolutely critical for businesses and institutions to protect their DNS infrastructure to offer seamless digital experiences to their customers, end users, and employees.
Akamai Shield NS53 is a new solution that perfectly complements Akamai Edge DNS, Akamai Prolexic, and Akamai App & API Protector to create a comprehensive portfolio of DDoS protection solutions for businesses and institutions that depend on reliable digital infrastructure to power their applications and user experiences online.
Learn more
Learn more about how Akamai Shield NS53 can help your DNS security requirements.