November’s Shopping Holidays: Online Shopping, Sales, and Magecart Attacks

Executive summary
Akamai researchers identified a significant increase in attempts to infect websites with Magecart attacks during Black Friday 2023 and the week leading up to it.
During Black Friday and Cyber Monday 2023, Akamai Client-Side Protection & Compliance observed more than 150 million daily user sessions (a 30% increase over regular days) and detected heightened suspicious activity among customers.
Akamai Client-Side Protection & Compliance provides its customers with real-time detection and immediate mitigation abilities, ensuring protection against Magecart attacks.
Introduction
The end of November is a festive time of anticipation, and most of us look forward to the shopping holidays of Black Friday and Cyber Monday! Shoppers all around the world navigate the vast online marketplace in search of exclusive deals and discounts, but theirs are not the only online activities that are increasing.
The November shopping holidays are also an occasion for online attackers, with increasing activity of phishing campaigns, malware infections, and, of course, Magecart attacks.
How Magecart attacks steal online shoppers’ data
Magecart attacks are a type of attack that targets the end user's browser to skim and exfiltrate sensitive user information, such as credit card numbers and personally identifiable information, from targeted websites. As part of the attack, the threat actor injects a piece of malicious JavaScript code into the targeted website's pages, looking for valuable, sensitive information related to the website's end users.
To infect a website with malicious JavaScript code, the attacker can exploit first-party code vulnerabilities or carry out a third-party supply chain attack by abusing a known third-party JavaScript vendor. These attacks have a special way of hiding in plain sight and can easily go undetected for long periods, making them a lucrative way to steal precious data from online holiday shoppers.
Businesses that fall victim to these attacks face significant financial consequences, harm to brand reputation, and loss of customer trust. Many large well-known brands have suffered from Magecart-style attacks that have resulted in devastating fines.
More user sessions, more suspicious events
Akamai Client-Side Protection & Compliance leverages behavioral technology to monitor and analyze JavaScript behavior on protected pages across hundreds of global Akamai customers all year round. The solution is designed to detect unauthorized and malicious activity, as well as to mitigate potential JavaScript threats, such as Magecart attacks.
Our research throughout this November’s online shopping holiday events demonstrates some interesting insights businesses should be aware of. Not surprisingly, we are seeing an increase in traffic and in the number of user sessions for almost all our customers.
Indeed, Client-Side Protection & Compliance has analyzed more than 150 million daily users’ sessions on Black Friday and Cyber Monday (Figure 1). These numbers represent an average increase of 30% in user sessions on these dates compared with regular days.
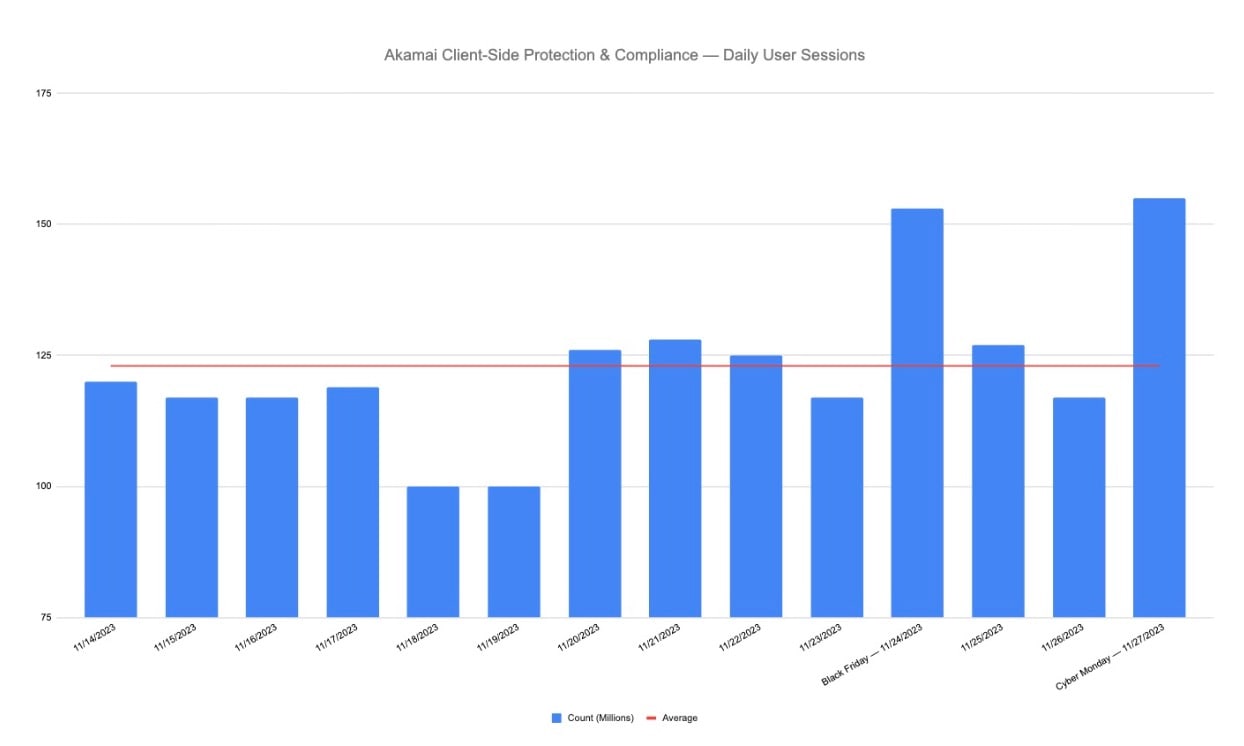 Fig. 1: Client-Side Protection & Compliance analyzed more than 150 million daily user sessions during Black Friday and Cyber Monday
Fig. 1: Client-Side Protection & Compliance analyzed more than 150 million daily user sessions during Black Friday and Cyber Monday
The increase in customer traffic brings with it an increase in suspicious activities. Akamai Client-Side Protection & Compliance inspects and analyzes every JavaScript execution across protected customer pages. In doing so, it is able to detect and alert on high-severity events that require immediate mitigation. These activities include suspicious network activity, accessing sensitive end-user information, and more.
Throughout the big shopping days, Client-Side Protection & Compliance detected 27% more suspicious activities than the average number monitored in the two weeks leading up to the Thanksgiving holiday (Figure 2).
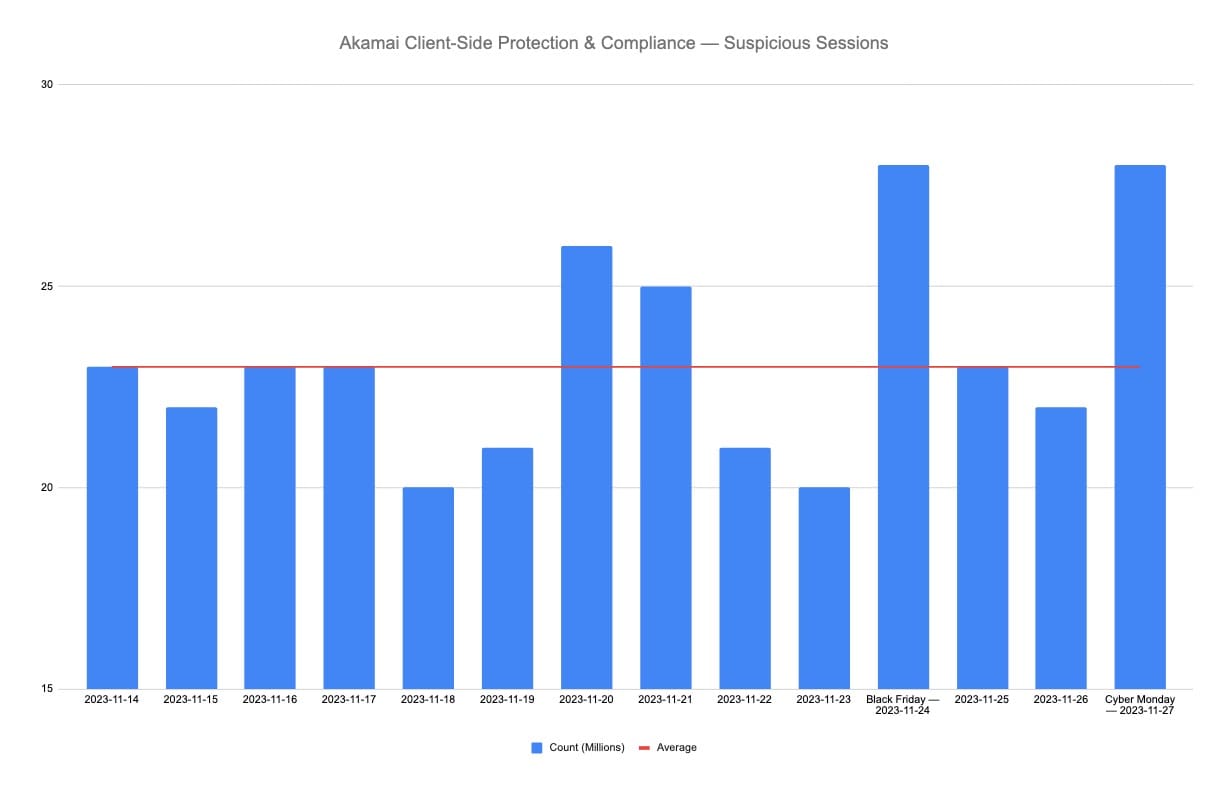 Fig. 2: Client-Side Protection & Compliance detected 27% more suspicious activities during the November shopping days than the average number monitored in the two previous weeks
Fig. 2: Client-Side Protection & Compliance detected 27% more suspicious activities during the November shopping days than the average number monitored in the two previous weeks
Infection campaigns
Attempted attacks
During the week before Black Friday and Cyber Monday, we observed an increased activity of attackers' preparations for the shopping holiday season. This activity is expressed in an increased number of attempts to infect Akamai’s customers with Magecart attacks, and an increased number of infection campaigns we monitor that are not related to our customers.
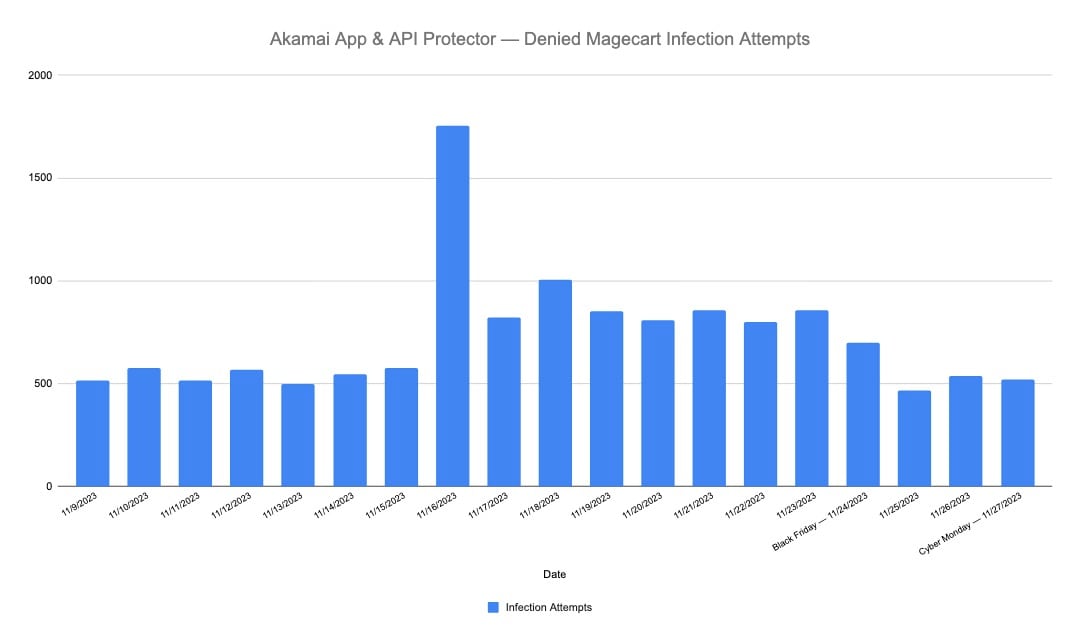
As detected by Akamai App & API Protector, there was a spike in attackers' attempts to infect our customers' websites with Magecart attacks that began on November 16, the Thursday before the holiday week (Figure 3).
These infection attempts serve as the initial phase in a Magecart attack. During this stage, attackers seek to gain access to the targeted website, either through first-party vulnerabilities or third-party exploitation. Upon successful penetration, the attacker proceeds to inject malicious JavaScript code into the sensitive pages of the website. Akamai App & API Protector provides visibility and protection for infection campaigns that target the customers’ first-party assets, but it does not provide the same for infections using third-party assets as the backdoor for targeted sites.
Successful attacks
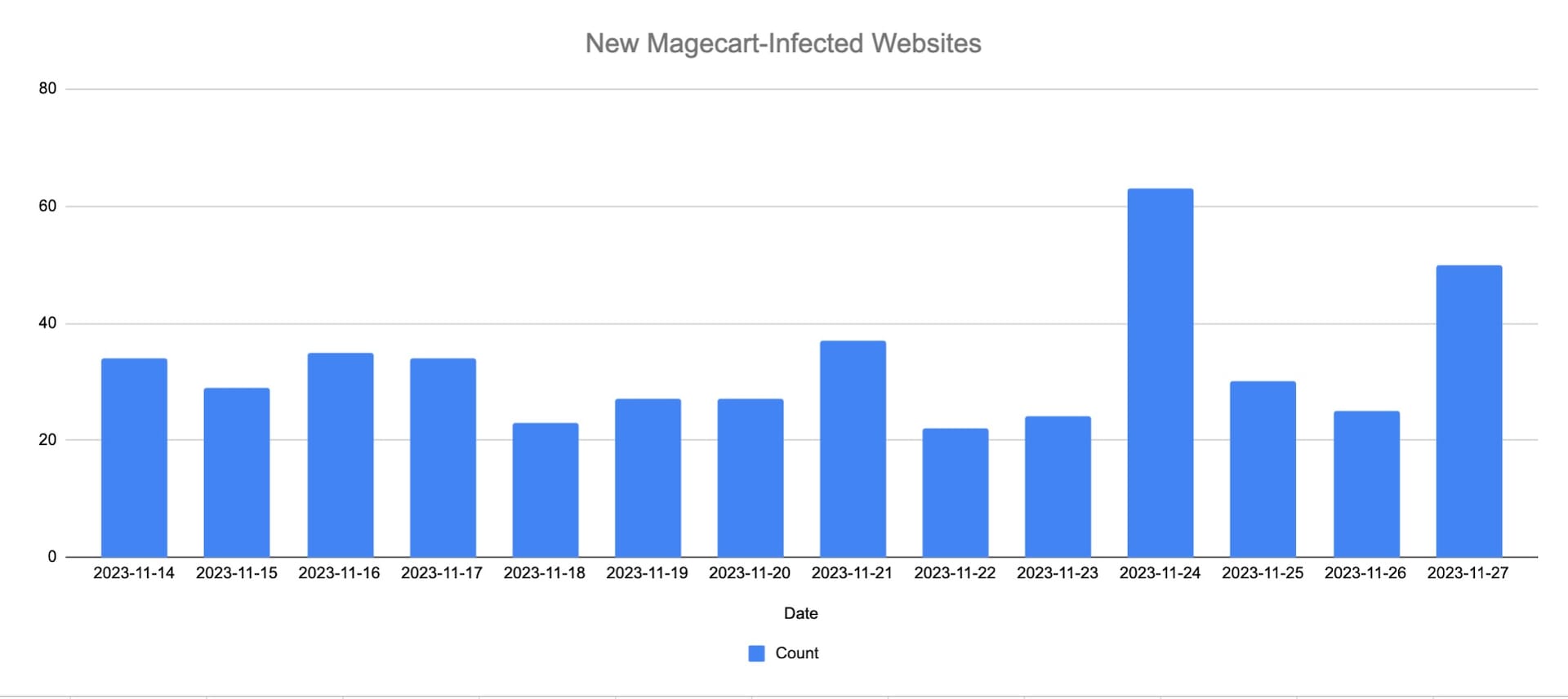
Another interesting trend we observed during the shopping holidays is the increase in successful Magecart infections, resulting in a high number of newly infected websites (Figure 4). These attacks are related to campaigns we revealed earlier this year and continue to monitor.
This trend implies that attackers’ attempt to infect as many digital commerce websites as possible during Black Friday (an increase of 90% in daily detected websites) and Cyber Monday (an increase of 50% in daily detected websites) because they know that a website without a dedicated Magecart protection solution is unlikely to notice and react to an infection during this time — and the attack is more likely to be successful.
Akamai Client-Side Protection & Compliance provides real-time detection and immediate mitigation capabilities to help our customers remain safe and protected from Magecart attacks.
Meet PCI DSS compliance requirements
It's also important to note that any organization that processes payment cards online is now required to ensure that their payment pages are protected against JavaScript threats, as outlined in the Payment Card Industry Data Security Standard (PCI DSS) version 4.0. Client-Side Protection & Compliance helps organizations meet the latest JavaScript security requirements (6.4.3 & 11.6.1) and streamlines compliance workflows to meet the upcoming PCI DSS v4.0 deadline of March 2025.
Conclusion
Ultimately, our research revealed that November’s key online shopping events resulted in increased web traffic, as well as increases in suspicious activity and Magecart attack attempts. As shoppers continue to find deals and transact online during the holiday season, it’s important for brands to ensure that they protect their customers, and their business, against the threat of Magecart. Akamai Client-Side Protection & Compliance helps organizations stay protected against JavaScript threats and keeps end-user data safe.
Learn more
To learn more about Akamai Client-Side Protection & Compliance and how to protect end-user data against JavaScript threats, contact our team of experts.