Honey, I Lost My Credentials! Finding Plaintext Credentials on the Internet
Editorial and additional commentary by Tricia Howard
Executive summary
Akamai Hunt, the proactive threat hunting service powered by Akamai Guardicore Segmentation, discovered legitimate plaintext credentials for a financial institution on the internet.
Once detected, the situation was communicated and remediated within 24 hours.
In this blog post, we provide an analysis of the discovery and investigation of this finding, and the mitigations that we recommended to the customer.
In the interest of privacy, we have significantly redacted information in the images and copy.
Introduction
Even as a threat hunter, it’s not every day you find plaintext credentials on the internet.
Our Akamai Hunt team is composed of proactive threat hunters focused solely on detecting anomalies, threats, and risks in our customers’ networks. One of the biggest risks in the world of cybersecurity is a data breach — and that’s what we aim to prevent. Whether that means prevention, detection, or mitigation, we have methodologies to be specialized eyes and ears for our customers.
You never know where an investigation is going to lead you, but the story we are discussing in this post was something special. After detecting and decompiling a suspicious Python script, we found the inconceivable: plaintext domain user credentials for a financial institution. The sky's the limit for malicious actors with that level of access, especially in a financial institution. (Don’t worry, though, this story has a happy ending.)
The human element is considered the largest cybersecurity threat to an organization. In this blog post, we will discuss the investigation and findings, and provide some additional guidance for other security professionals.
The path to detection
Threats hide in files, and files hide in folders. Temp files and downloads are great places for malware to hide since they often remain unmaintained by the user, and you can mimic legitimate command names to fool the users who do check.
One of our proactive detection mechanisms is continuously monitoring certain folders and comparing it with the known baseline.
Through our research, we compiled a list of paths in which attackers commonly drop malicious files. We marked those paths and examined new executables and scripts that were created in a limited list of paths.
Some paths we looked for were:
C:\Users\Public
C:\Users\<username>\Downloads
C:\Windows\Temp
C:\Users\<username>\AppData\Local\Temp
When a new file is discovered, we run several checks to determine whether it’s worthy of an alert, such as:
Connections made by the executable
Existence on other network assets
Internal intelligence feeds, along with public ones such as VirusTotal
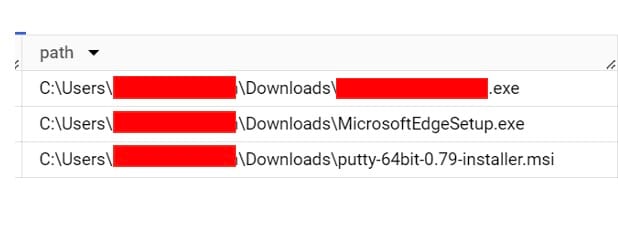
In October 2023, we detected a few files that suddenly appeared simultaneously in the downloads folder (Figure 1).
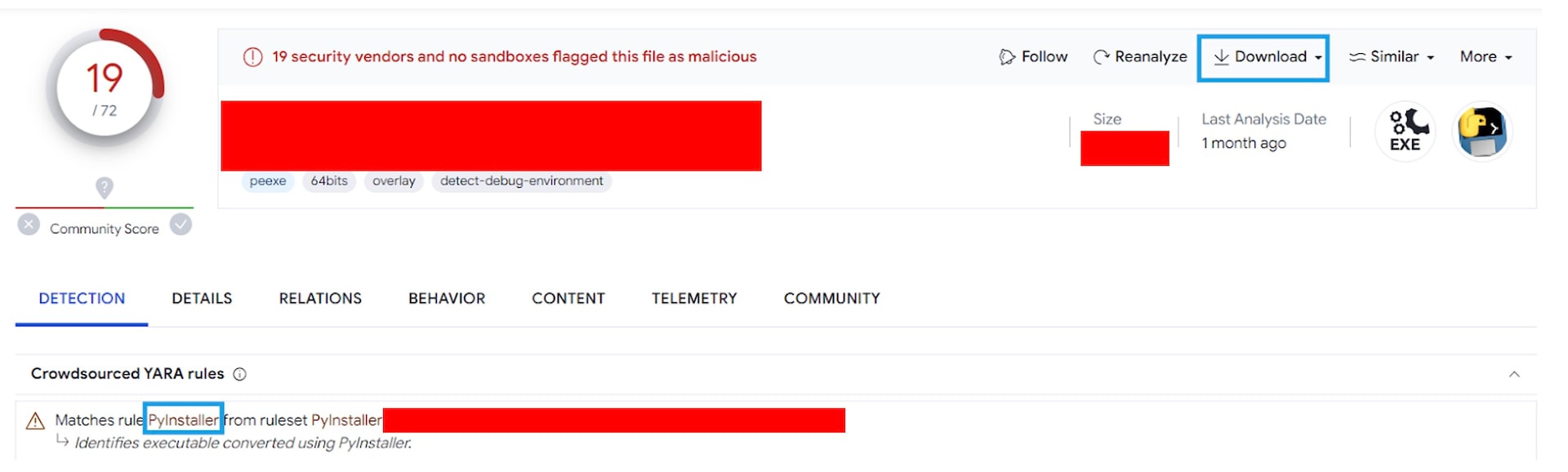
One file in particular stood out: It was recently created, and had never appeared in this customer’s network. It had been seen on VirusTotal, however (Figure 2), and it had been flagged as malicious by a number of sources. The file was available for download on the VirusTotal page, so we did that.
We discovered the file was a PyInstaller-packaged binary. We decompiled the binary and got the Python source code, which we examined manually.
The investigation
Now that we know what we’re working with, we can begin the investigation of the file. We checked for connections that were made by the file, the user who executed it, other suspicious files that the attacker may have downloaded, and also more detection methods surrounding the suspicious asset.
The file communicated to many devices associated with a third party provider, which raised a flag for us because this would indicate that some amount of legitimacy was seen by the third party’s device. Since this script was found in VirusTotal with a lot of positive engines, this is deeply concerning.
We decompiled the file using pycdc and, on the first look, it appeared to be a normal IT file. Instead, the script turned out to be a backup script that executes the following three steps:
The script reads a list of IP addresses
It connects to each IP
It backs up configurations and versions
Surprise, we have your credentials!
This is where the story gets really interesting. For the script to run, an authentication had to occur. As such, the credentials of a domain user were included. We verified that the user was in fact a legitimate user, which makes the whole story even weirder. Not only that, but also the access level of this user was quite high. Why would a backup script with plaintext credentials inside it be found on the internet?
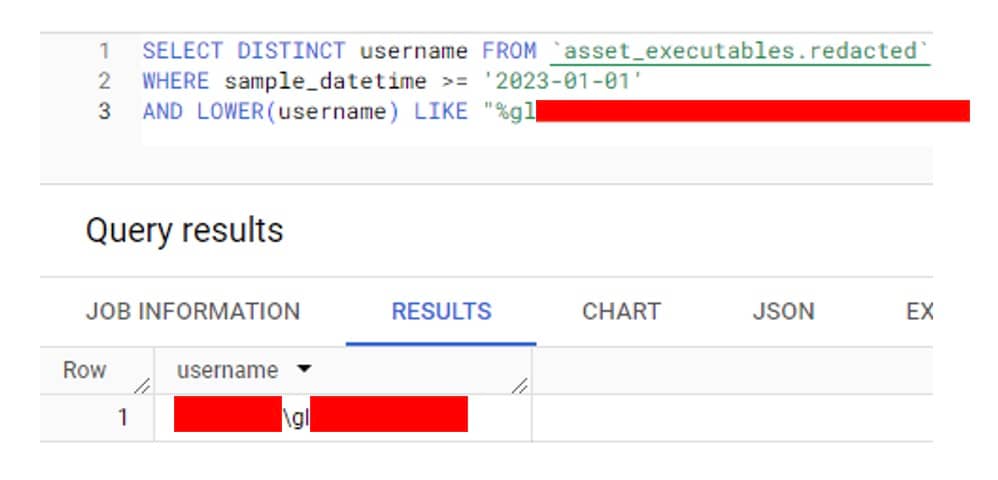
We immediately contacted the customer, who validated the script was indeed legitimate. It was an actual IT script that had been created internally and uploaded accidentally into VirusTotal (Figure 3).
Mitigations
We don’t often get to tell happy stories in security, but thankfully this one ends well. This situation was discovered, remediated, and communicated by the Hunt team all within 24 hours. When you find plaintext credentials on the internet, you better move swiftly to avoid catastrophe.
After contacting the customer we provided some recommended mitigations:
Change passwords of the exposed user and the users on the impacted devices that the file accessed
Deploy a management system for this kind of activity
Practice security awareness — don’t install untrusted softwares as private data can be stolen
The customer responded with vigor and speed to remediate.
Conclusion
Human error and developer security are two of the hottest topics in cybersecurity, and this story is a stellar example of both. It is entirely reasonable to posit that this situation could have gone undetected for quite some time — and that would have been the best-case scenario. The alternative could have been disastrous: You don’t have to be a Game of Thrones fan to imagine what damage an illegitimate entity could do (especially with elevated credentials in a financial institution).
As proactive threat hunters, the Akamai Hunt team will continue to analyze and publish the real-life scenarios we observe, such as this one, to assist the security community at large.
Follow us
To keep up with these updates and other security research, you can follow us on X (formerly Twitter).