To get FIDO2-based MFA today, an organization needs to first deploy an MFA service and then buy, distribute, and manage hardware security keys, which significantly increases costs and operational complexities. Another challenge of physical security keys is that the end-user experience is less than ideal — people lose or forget their keys, meaning additional calls to the IT help desk.
Multi-factor authentication (MFA) is a security technology that uses multiple authentication factors for identity verification when users log in to online services. MFA requires a user to combine two or more authentication factors, which may include something they know (like a password or PIN), something they have (like a smart card or push notification), and something they are (like a fingerprint).
MFA helps create additional security layers that make it more difficult for unauthorized users and attackers to gain access to networks, systems, and services. This layered approach to verifying a user’s identity ensures that if one of the authentication factors is compromised, then there are additional barriers to prevent access.
Why is MFA needed?
As cyberattacks become increasingly frequent and more sophisticated, many enterprises are adopting multi-factor authentication (MFA) solutions to protect employee accounts. Nearly 80% of data breaches begin with stolen or compromised employee credentials or brute-force logins that use automated password hacking tools. Relying only on passwords that can be easily guessed or compromised means that stronger user authentication is now a necessity for enterprise identity and access management programs. Strong user authentication is also a key requirement for a Zero Trust security approach.
The security gaps in MFA
Adding multi-factor authentication to your employee identity and access management solution will reduce the risk of employee account takeover. However, cybercriminals are now adopting new attack techniques to bypass MFA solutions. MFA services that use push notification factors such as a text message, one-time-passwords, or email links can be exploited by hackers. These attacks typically use phishing and social engineering techniques or credential stuffing to trick an employee into accepting the push notification. This means that unless an MFA service is bolstered with additional security features, many of today’s multi-factor authentication technologies still leave your enterprise at risk.
Closing the MFA security gaps
Akamai MFA is a next-generation multi-factor authentication solution that enables phish-proof authentication by leveraging FIDO2, the strongest standards-based authentication method available. With Akamai MFA, you can increase user authentication security, and reduce the risk of employee account takeover and data breaches, while supporting Zero Trust networking. It also provides a strong foundation for moving to passwordless authentication.
Can MFA be hacked?
While MFA security is a considerable improvement over two-factor authentication that only requires a username and password for access to online accounts, multi-factor authentication is increasingly being targeted by cybercriminals to successfully gain unauthorized access.
There are numerous factors that can be used for multi-factor authentication:
- Something you know, such as a password or PIN
- Something you have, such as a smart card, key fob, one-time password (OTP), or SMS code
- Something you are, such as facial recognition, a voice or speech pattern, or a biometric fingerprint scan
However, many of these factors can be compromised or bypassed by cybercriminals. The most frequently targeted factors are push notifications such as SMS, one-time passwords (OTPs), and email links.
How are MFA push notifications abused by cybercriminals?
One frequently used technique is to employ a combination of phishing attacks and social engineering. The attack begins by sending a phishing email to an employee that looks as if it came from the company’s IT department. The email asks them to click on a link in the email to validate their username and password, but this takes the employee to a fake login page that has been created by the cybercriminal.
Once these credentials are obtained, the attacker enters them into the legitimate login page, which triggers a push notification to be sent to the employee’s mobile device. Since the employee believes the push notification is legitimate and likely accepts it, two factors of identification have now been entered, and the attacker has gained unauthorized access to the employee’s account.
In addition, the attackers might also use social engineering techniques such as calling the employee or messaging them to inject urgency into the original email request.
This means the only thing preventing an employee account takeover is your employee’s ability to tell the difference between a legitimate push notification and one that has been engineered by an attacker.
Can MFA security be improved?
The security solution to enhancing MFA to ensure that it cannot be bypassed is FIDO2, an industry standard managed by the FIDO Alliance. In basic terms, it works by making a cryptographic connection between the authentication attempt and the MFA challenge. That means attackers can’t use stolen or compromised credentials or dupe users into entering their credentials into a fake login page. This method makes it virtually impossible to compromise MFA.
Phish-proof MFA with Akamai
Akamai MFA is a workforce multi-factor authentication service that adds an extra layer of security by providing strong secondary authentication for cloud, web-based, on-premises, SaaS, and IaaS applications.
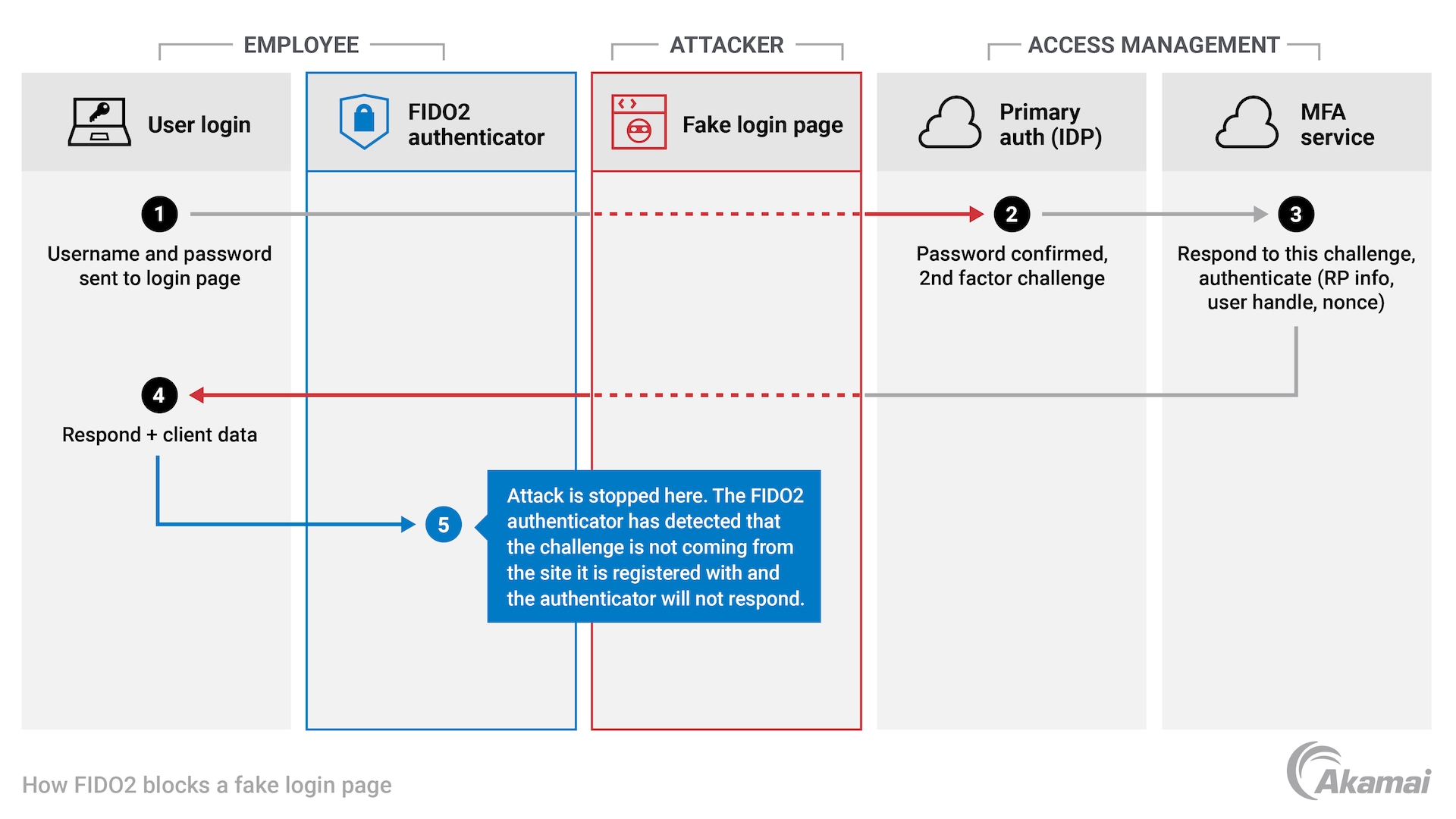
Akamai MFA relies on FIDO2 standards, which offer the highest levels of MFA security. These standards prevent phishing by always sending the request for authentication to the workstation where the request for access originated. Therefore, an attacker’s attempt to log in with stolen credentials will result in a push notification to the attacker’s workstation, rather than an employee’s phone, preventing a potential account takeover.
Additionally, with Akamai MFA, the browser sends data to the security key alongside the request for authentication. This data includes the domain name of the origin that requested authentication, enabling the security key to recognize a mismatch between the domain name of a registered site and the fake or phishing domain name requesting authentication.
While FIDO2 standards significantly increase security, they can also be difficult to implement, as the required physical security keys are costly and cumbersome to manage. Akamai MFA overcomes this challenge via a smartphone authenticator app, in place of a physical security key. End-to-end cryptography and a sealed challenge/response flow make the authentication process unphishable and confidential. This eliminates the need for costly and cumbersome hardware security keys.
The benefits of Akamai MFA
Deployed on Akamai Connected Cloud, Akamai MFA can be activated and managed centrally, and can scale for resilience and performance. With this innovative solution, you can:
Minimize risk by relying on FIDO2 authentication standards to prevent breaches that originate with phishing and social engineering attacks.
Offer employees a frictionless experience that leverages smartphones and familiar push notifications to authenticate their accounts with a second factor.
Implement MFA security quickly through a mobile app on employees’ existing mobile phones, eliminating the need to distribute physical security keys or compatible hardware.
Reduce total cost of ownership (TCO) by using FIDO2 standards with existing smartphones and web browsers, avoiding the need to purchase, replace, and maintain additional hardware.
Implement Zero Trust security by relying on the strongest available authentication and authorization protocols.
Future-proof investments in MFA technology with a cloud MFA service designed to evolve to support future use cases such as passwordless authentication and SSO.
In addition to multi-factor authentication, Akamai’s Zero Trust security portfolio includes solutions for secure remote application access to reduce the reliance on VPNs, a microsegmentation solution to limit lateral movement and reduce the risk of ransomware, and a secure web gateway that blocks access to malicious web content.
Frequently Asked Questions (FAQ)
Confusingly, these terms will often be used interchangeably. The most commonly accepted definition of two-factor authentication is authorization that relies only on user identity and a password. MFA is different from two-factor authentication in that it requires one or more additional security factors to be entered by the user. For example, after a user enters their correct username and password, the MFA solution will prompt them to provide an additional factor or factors to gain authorized access to the resource.
Compromised or stolen user identities are frequently employed by cybercriminals to gain access to employee or system accounts. Adding MFA to your identity and access management adds additional security layers that strengthens user authentication, which reduces the risk of account takeover that can often lead to data breaches or ransomware attacks. Strong authentication is an essential component of enterprise security frameworks such as Zero Trust and SASE, and it plays a vital role in remote work security.
Adaptive MFA applies additional security rules to the user authentication process. The security rules can be based on a range of parameters, for example, where the user is located, when the request is being made, and the security posture of the device. For example, if an employee is located in New York and the authentication request is being made from Sydney on an unknown device, then the MFA service could ask for an additional factor such as a fingerprint or a facial scan to ensure the request is legitimate.
Single sign-on (SSO) is a security system that enables employees to log in once and then obtain seamless access to multiple applications. This eliminates the need for employees to remember individual application login credentials and reduces the admin effort needed by cybersecurity.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.