Secure Your Kubernetes Clusters to Stop Ransomware
While containers offer speed and flexibility that have not been possible before in the data center, they are also exposed to security threats such as ransomware, cryptomining, and botnets. According to the 2022 Red Hat State of Kubernetes Security Report surveying more than 300 DevOps, engineering, and security professionals, 93% of respondents experienced at least one security incident in their Kubernetes environments in the last 12 months. These incidents could potentially be exploited by threat actors to install ransomware and other types of malicious software, making the protection of Kubernetes clusters critical.
What is a Kubernetes cluster?
A Kubernetes cluster is a set of nodes that run containerized applications. A Kubernetes cluster provides a complete ecosystem for the nodes, including DNS services, load balancing, networking, autoscaling, and any other capability required for running applications operations. The Kubernetes cluster can host multiple applications using a built-in hierarchy structure and application segregation, with no restrictions on communications between namespaces (Figure 1).
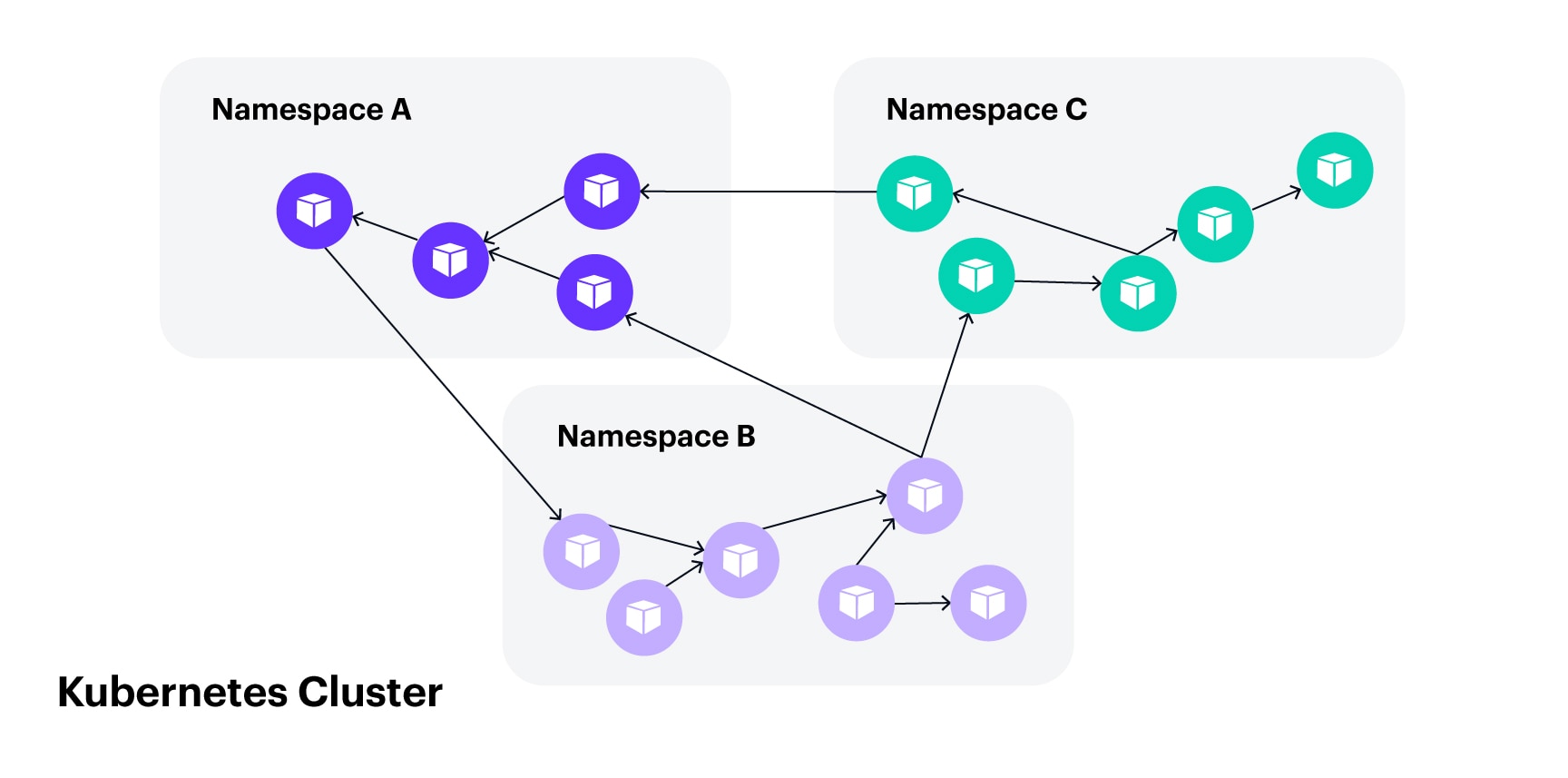 Fig. 1: A Kubernetes cluster is by default flat with no restrictions among the pods
Fig. 1: A Kubernetes cluster is by default flat with no restrictions among the pods
Why segment Kubernetes clusters?
In recent years, attacks on containers have become increasingly sophisticated. To avoid detection, attacks on Kubernetes clusters have increased their use of evasion and obfuscation techniques, including packing the payloads, using rootkits, and running malware straight from memory.
These environments allow communication between clusters and pods by default, even though it is not required for normal operations. Adversaries abuse this for lateral movement within their ransomware campaigns, so we need the ability to put policies in place that restrict these flows without disruption.
The key capabilities for segmenting Kubernetes clusters
A good network segmentation solution requires four key elements: visibility, enforcement, monitoring, and operations (Figure 2).
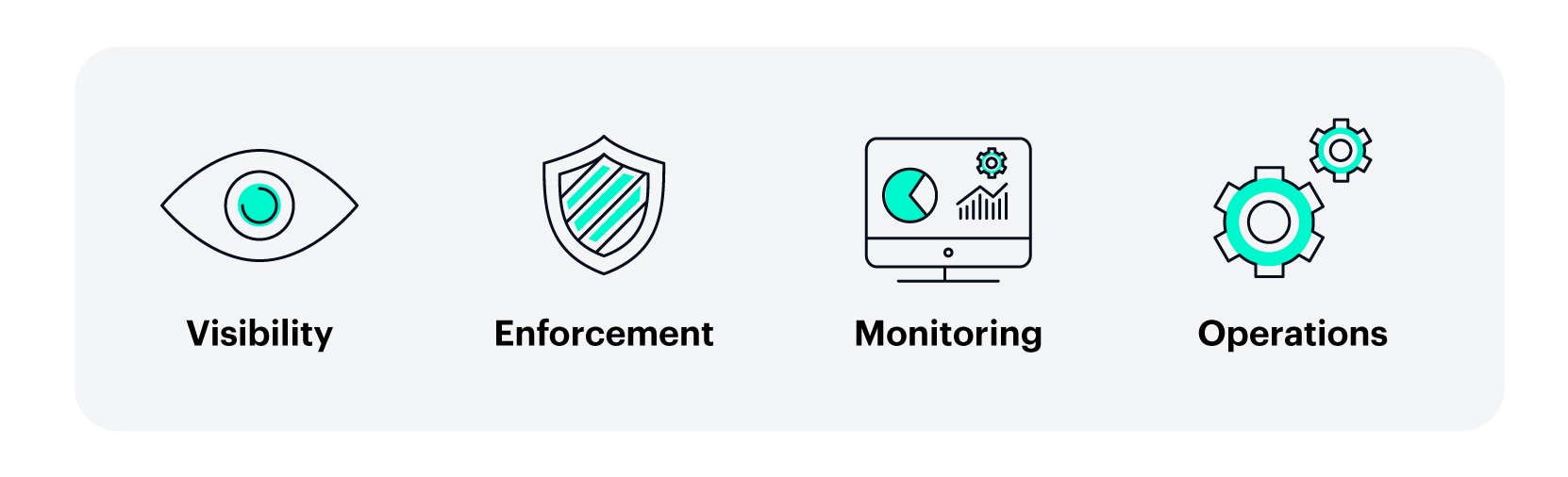 Fig. 2: Four key pillars to successful network segmentation solution
Fig. 2: Four key pillars to successful network segmentation solution
Complete visibility into Kubernetes clusters
Visibility is key in Kubernetes environments. The ability to know what’s running in your Kubernetes environment and to confirm that your traffic is going only where you want it to go is critical to successful policy creation. Guardicore, now part of Akamai, accurately visualizes Kubernetes clusters with insights into all layers of the infrastructure.
Interdependency maps
The solution provides a map for visualizing communications internally and across data centers for all types of technologies such as VMs, Kubernetes, docker containers, and more (Figure 3). Based on these maps, you can view and detect any suspicious connection among pods, services, and hosts, or namespaces.
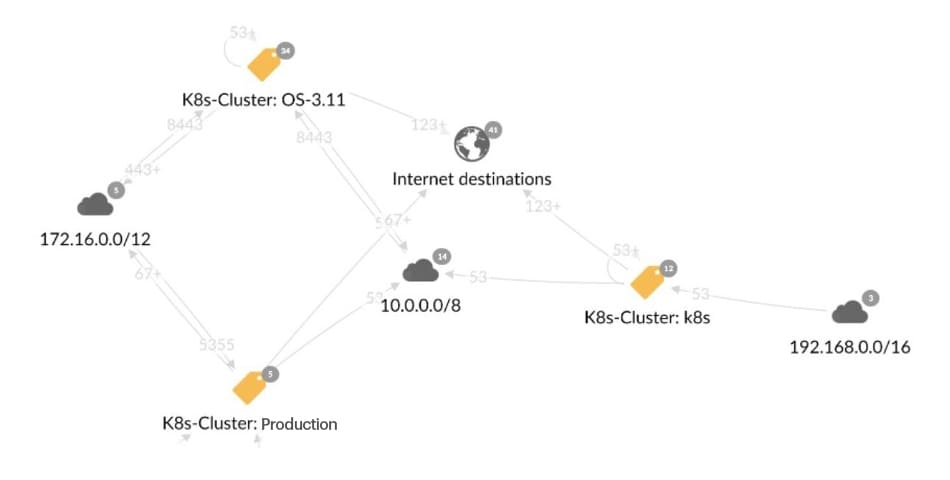 Fig. 3: Clusters represented on the Reveal map; double-clicking a cluster reveals the namespaces and their interconnections within the cluster
Fig. 3: Clusters represented on the Reveal map; double-clicking a cluster reveals the namespaces and their interconnections within the cluster
Labels
The maps accurately reflect the way the applications are deployed in the cluster by using multiple layers of labels (Figure 4). This visualization describes the Kubernetes hierarchy as it was planned by the app’s managers. This level of detail helps Akamai’s users understand exactly what is deployed in the cluster, and the networking relations between the deployed apps and the rest of the infrastructure.
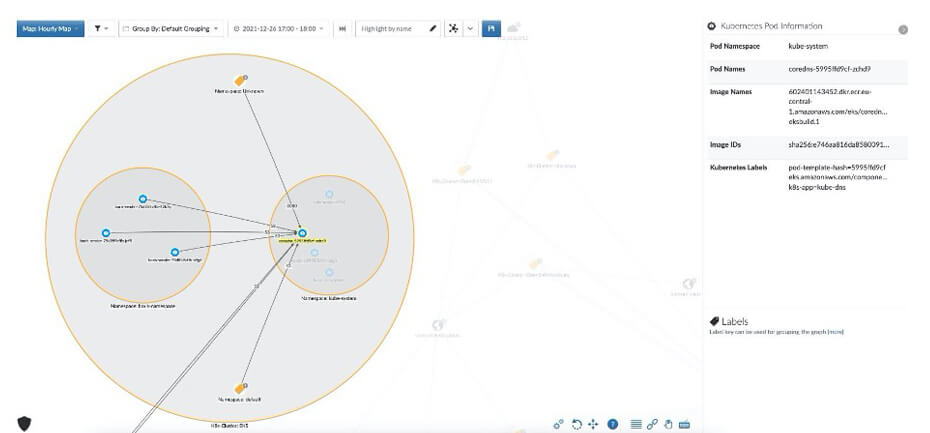 Fig. 4: Reveal map displays pod information including the pod label and image name
Fig. 4: Reveal map displays pod information including the pod label and image name
Kubernetes native policy enforcement
To help minimize the attack surface in your Kubernetes cluster, a strict segmentation policy is required. A segmentation enforcement solution should address two main criteria — be nonintrusive and without any scale and performance limitations; and provide a flexible way to ringfence all levels of Kubernetes objects including namespaces, controllers, and Kubernetes labels.
Akamai is leveraging the native Kubernetes Container Network Interface (CNI). The CNI consists of a network security policy plug-in that was originally designed for network segmentation enforcement in Kubernetes. This is a nonintrusive method with no scale limitations.
Akamai has extended its best-of-breed templates to include dedicated templates designed for ringfencing Kubernetes business-critical applications (Figure 5). Using this template, the user can easily choose which object to ringfence — whether it’s a namespace, application, or any other object.
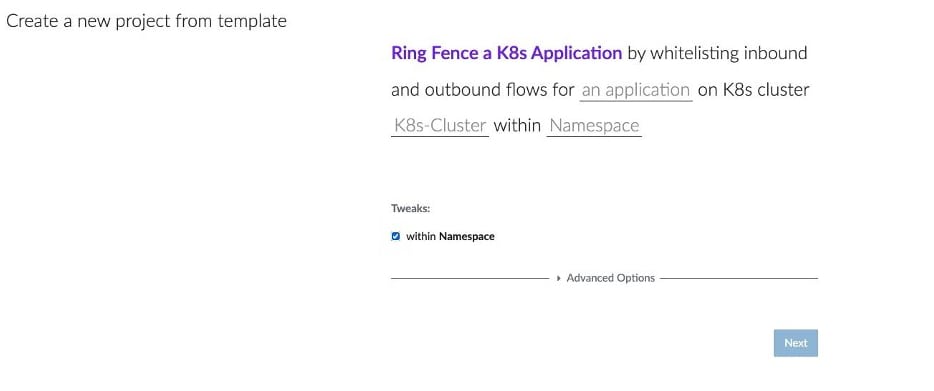 Fig. 5: Kubernetes application ringfencing template
Fig. 5: Kubernetes application ringfencing template
Advanced monitoring
Using our advanced logging and monitoring system, our dedicated network log is now adjusted to Kubernetes networking, displaying destination services, node IPs, source and destination ports, and processes for every event. This provides an easy way to investigate anomalous activity in the network and export data to a third-party application such as SIEM.
Cluster operations
Securing Kubernetes assets begins with real-time visibility and operational awareness. A dedicated Cluster Operations screen provides all necessary data on the deployed clusters, including the number of agents monitoring the cluster, warnings, and alerts flagging on the agent’s function; the state of the Kubernetes orchestration; and more (Figure 6).
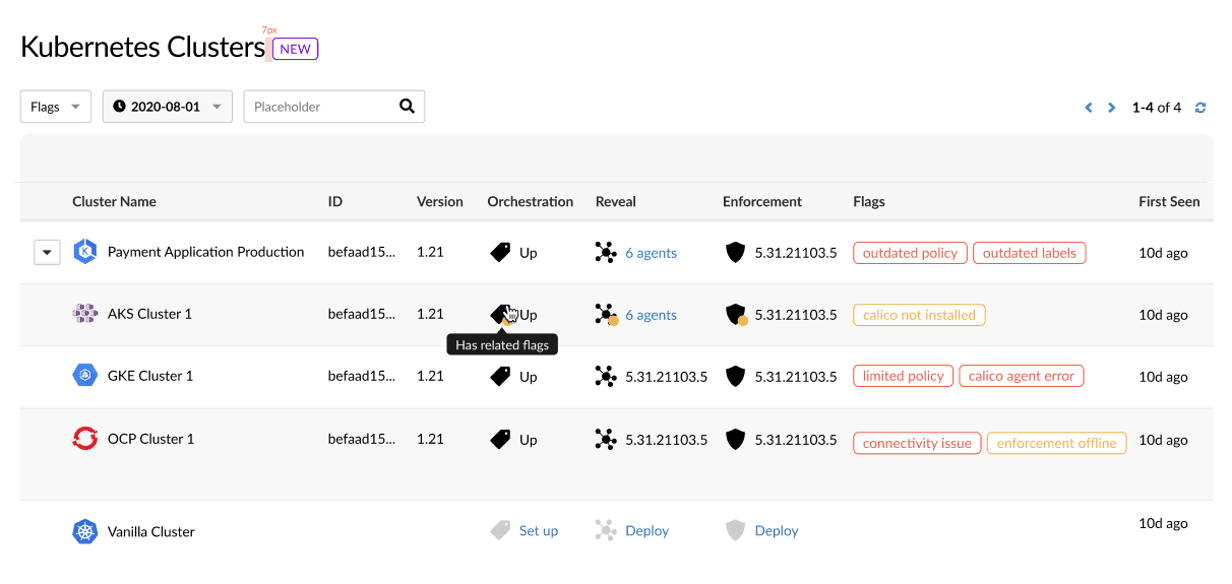 Fig. 6: The Cluster Operations screen
Fig. 6: The Cluster Operations screen
Summary
While most of us will agree that we need to “assume a breach,” there are few tools that allow us to act on this notion. Especially with new technologies like Kubernetes, tools that allow us to treat each asset as the perimeter are severely lacking. With Akamai Guardicore Segmentation, we’ve enabled businesses, even those with complex infrastructure, to act on the notion that threat actors have already breached our networks. Akamai’s solution for Kubernetes is nonintrusive, with no cluster scale limitations, providing comprehensive visibility into Kubernetes clusters and native Kubernetes enforcement that works with any operating system — all from the same console you’re using to manage the rest of your infrastructure.



