Akamai’s Perspective on April’s Patch Tuesday 2023
Don’t let anyone fool you, the real meaning of PT is Patch Tuesday. As we do every month, Akamai Security Intelligence Group set out to look at the more intriguing vulnerabilities that were patched.
There are approximately 100 patched CVEs this month, 7 of them critical, and 2 with a high CVSS score of 9.8. One of the patched CVEs is also said to have been used in the wild, designating it as a patched zero-day vulnerability.
In this report, we’ll assess how critical the vulnerabilities really are and how commonplace the affected applications and services are, and we’ll provide a realistic perspective on the bugs that were fixed. Be on the lookout for these insights in the days after every Patch Tuesday. You can also see a quick real-time overview on the day of the patch on our Twitter account.
This is an updating report and we’ll add more information to it as our research progresses — stay tuned!
In this report, we’re focusing on the following areas in which bugs were patched:
Vulnerabilities exploited in the wild
Common Log File System — CVE-2023-28252
A local elevation of privileges vulnerability in the Windows Common Log File System (CLFS) driver, that according to Kaspersky, was used as a zero-day in Nokoyawa ransomware attacks. They also explain the root cause and effect of the vulnerability, which is an out-of-bounds write that eventually leads to a free kernel memory read/write primitive. CLFS has been available in Windows since Windows Server 2003 R2, so this vulnerability has a large impact. We recommend that you patch your systems as soon as possible.
Microsoft Message Queuing
There were three vulnerabilities in the Microsoft Message Queuing (MSMQ) service — a critical 9.8 remote code execution (RCE) vulnerability, and two denial-of-service vulnerabilities. All three vulnerabilities were found by Haifei Li from Check Point Research (CPR), who published a good write-up about the vulnerabilities.
The MSMQ service is an optional feature in Windows that is used to deliver messages between different applications. Despite being optional, it is used behind the scenes by many enterprise applications for Windows, such as Microsoft Exchange server. In our observations, we found the service installed in nearly 50% of environments, usually on more than one machine.
Since the RCE vulnerability is easily triggered (requires only a single packet according to CPR), we strongly recommend patching as soon as possible. If patching is not possible, due to operational continuity or some other reason, then we recommend restricting access to the service at the very least, using network segmentation policies. Since the MSMQ service is accessible over port 1801, but shouldn’t be accessed by that many clients (since it’s mostly used by the enterprise application itself), we recommend restricting arbitrary network access to that port and service. Try to segment it using allowlist policies, allowing access only to the machines that actually need it.
CVE number |
Effect |
Required access |
|---|---|---|
Denial of service |
Network |
|
Remote code execution |
Network |
Windows Pragmatic General Multicast
Pragmatic General Multicast (PGM) is a protocol designed to deliver packets between multiple network members in a reliable manner. On Windows, the implementation of this protocol is referred to as reliable multicast. This Patch Tuesday fixed a critical RCE vulnerability, CVE-2023-28250, with a 9.8 CVSS score.
In our observations, we noticed 40% of environments had reliable multicast activated. Although in most data centers only few machines had this capability enabled, we noticed environments where multiple servers were running PGM.
Since Windows Server 2003, PGM relies on Windows sockets. In user space, it is implemented in a library called wshrm.dll (Windows Sockets Helper DLL for PGM, where rm stands for remote multicast). In kernel space, PGM is implemented through the driver rmcast.sys.
The patch added size verification in a call to memset, in the function DecodeParityPackets. Before the fix, a remote attacker could send a specially crafted packet to cause an integer overflow, which would later lead to code execution. Although not explicitly mentioned, the vulnerability may have been given a high CVSS score due to the fact that code execution is achieved in kernel mode, namely with the highest privileges possible.
According to Microsoft (in an older security bulletin about a different CVE), “Message Queuing (MSMQ) must be installed and the Windows Pragmatic General Multicast (PGM) protocol specifically enabled for a system to be vulnerable” (Figure 1). Namely, PGM depends on Message Queuing for its operation and, therefore, the recommendations from the previous section apply here as well. This is further aligned with the mitigations and FAQ Microsoft has published for this month’s CVE.
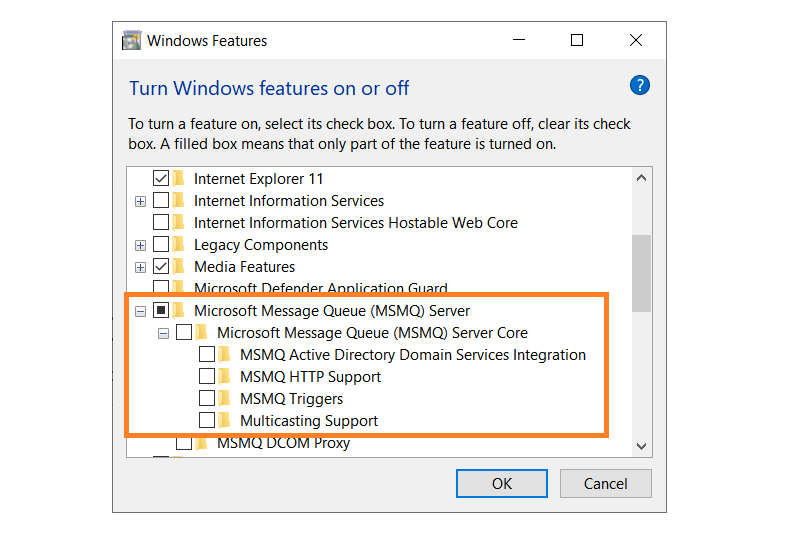 Fig. 1: Enabling MSMQ and multicasting through the Windows Features dialog box
Fig. 1: Enabling MSMQ and multicasting through the Windows Features dialog box
CVE number |
Effect |
Required access |
|---|---|---|
Remote code execution |
Network |
DHCP Server Service
The DHCP protocol is used to manage network traffic and addresses (IP address assignment, default gateway and DNS server configuration, and more). Windows has its own implementation of a DHCP server, which can be installed as an additional role on Windows Server installations. In our observations, we’ve seen the DHCP server service in approximately 40% of environments.
There is a critical vulnerability in the DHCP server this time that can be used to achieve RCE. Since DHCP is crucial to the operation of the entire LAN, it might be difficult to mitigate the risk of the vulnerability by segmentation (since, technically, the service should be open to the whole network). But it may be possible to use microsegmentation to allow network access to the DHCP service from only a small set of source processes. If you have network monitoring with source process visibility, it might be possible to map all the unique DHCP clients in your network, and limit access to only those processes. Otherwise (and regardless), you should patch your servers.
In our observations, we’ve only seen 14 unique processes access the DHCP server (and one of those was nmap, so technically it’s 13).
CVE number |
Effect |
Required access |
|---|---|---|
Remote code execution |
Local network |
Netlogon Remote Protocol
The Netlogon Remote Protocol is the protocol that is used for user and machine authentication on Windows domain environments. It is also used for synchronization between domain controllers. As such, it is inevitable in Windows domain networks, which is why CVE-2023-28268 could impact most environments.
It seems similar to a previous vulnerability we covered in November 2022’s advisory:CVE-2022-38023. Both vulnerabilities revolve around an attacker using a machine-in-the-middle (MITM) attack and using RPC signing instead of RPC sealing.
To enforce RPC sealing, Microsoft introduced the RequireSeal registry key. According to previous advisories, it should be impossible to disable the registry, and it can only be in compatibility or enforcement modes.
CVE number |
Effect |
Required access |
|---|---|---|
Elevation of privilege |
Network, MITM |
Windows Remote Procedure Call
There are three vulnerabilities this month related to remote procedure calls (RPCs; we’re including the RPCSS CVE). The RCE vulnerability is in the RPC runtime, which provides the API and implementation of the RPC protocol. It is implemented in the DLL rpcrt4.dll. The Remote Procedure Call Service (RPCSS) on the other end is an RPC server by itself, and is responsible for DCOM — namely, for making COM classes and objects accessible over the network.
Since rpcrt4.dll and rpcss.dll are both crucial to the normal operation of Windows (not to mention, rpcrt4.dll is loaded into every process that uses RPC), it might be impossible to mitigate the risk in a way that isn’t patching.
CVE number |
Effect |
Required access |
|---|---|---|
Remote code execution |
Network, authentication required |
|
Elevation of privilege |
||
Information disclosure |
Previously covered services
Many CVEs in this month’s Patch Tuesday are for systems that we’ve already covered in the past. If you’re interested in our analysis of, or general recommendations for, those services, we encourage you to look at our previous posts.
Service |
CVE number |
Effect |
Required access |
|---|---|---|---|
Remote code execution |
Network access; requires winning a race condition |
||
Remote code execution |
Network |
||
Spoofing |
Authenticated with page creation permissions |
||
Spoofing |
XSS attack; attacker must be authenticated |
||
Remote code execution |
Authentication required |
||
Information disclosure |
This summary provides an overview of our current understanding and our recommendations given the information available. Our review is ongoing and any information herein is subject to change. You can also visit our Twitter account for real-time updates.


