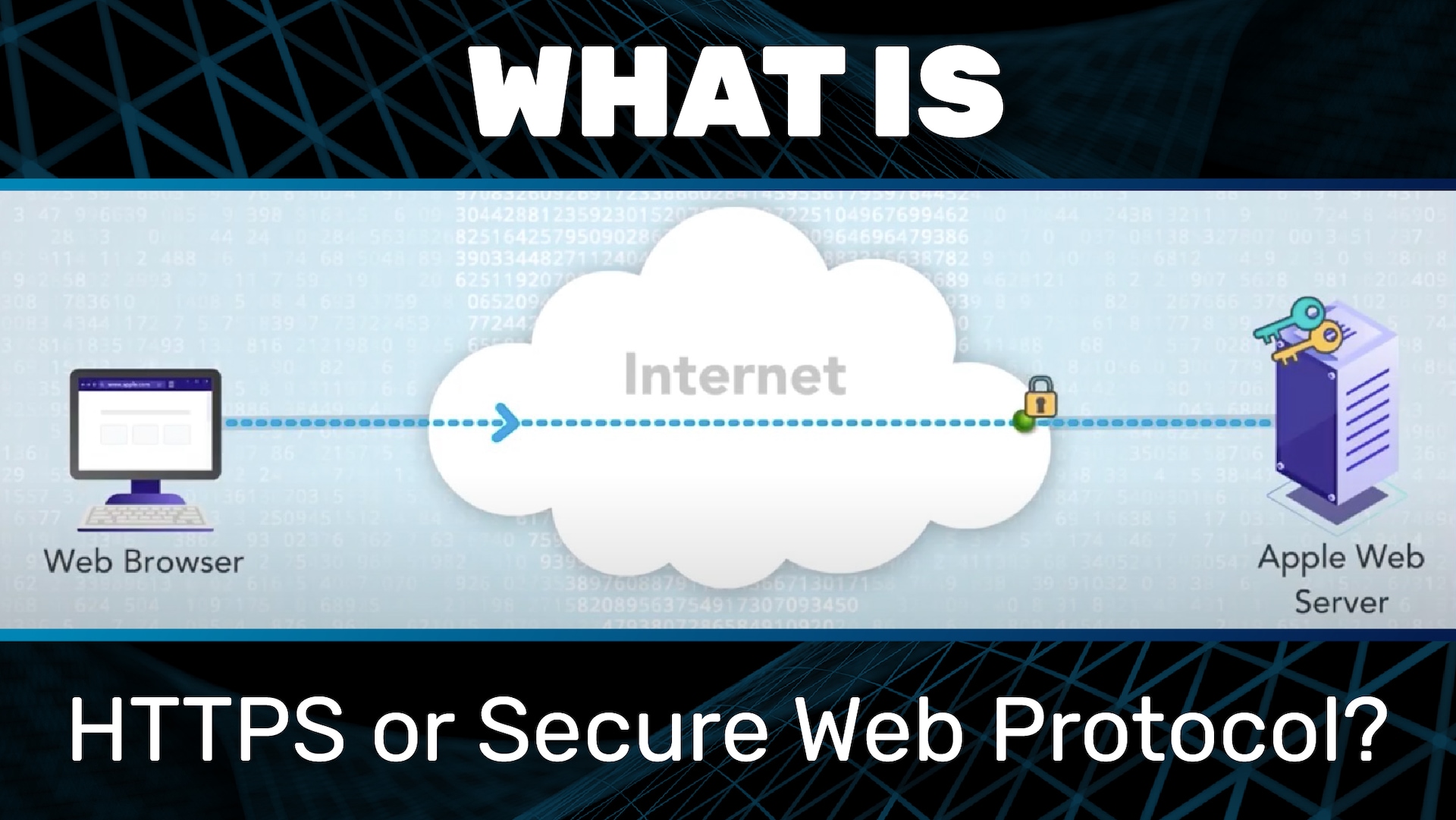
Now let’s look at the secure web protocol, HTTPS. The “S” at the end of HTTPS, of course, stands for “secure.” HTTPS provides for authentication of the website as well as encryption of the communication. Authentication of the website is how you know that you’re actually visiting www.apple.com and not some fake. Initially, HTTPS was used to protect logins and confidential online transactions like online banking and online shopping. These days, though, HTTPS is pretty much the default for everything.
HTTPS is based on a technology called public-key cryptography. To make it work, the website needs a public-private key pair that is certified by a certificate authority. I will not be getting into the workings of public-key cryptography.
Now, let’s redo our example, this time with HTTPS. Step 1 is just as before: We type the address or click on a link.
Before we can move on to step 2, we have to insert a new step that I’m numbering as 1.5. In this step, the browser and web server perform a cryptographic dance, that is, an exchange of messages and some really interesting computation, using the web server’s public-private key pair, in order to authenticate the website and create two new keys that are called session keys — one for the client and one for the server. These session keys are used to encrypt and decrypt the messages.
These cryptographic functions are performed by a protocol that is called Transport Layer Security (TLS), which is the successor to the now-deprecated Secure Sockets Layer (SSL).
Now we can move on to step 2, which works just as before, but now, after the browser writes the request message, before it can send it, it uses its session key to encrypt it. The encrypted message is then sent to the web server. The web server then, after receiving the message, uses its session key to decrypt and then read the message.
Step 3 operates similarly with the response message. After writing the response message, the web server encrypts it using its session key and then sends it back to the browser. The browser, then, after receiving the message, uses its session key to decrypt and then read the message.
Finally, step 4 operates as before — the browser renders the response, and we can see the web page.
Note that the padlock icon indicates a secure connection and authentication of the website.
You may be wondering how the request and response messages find their way to the web server and back. The answer is the Internet Protocol, IP, and that is the subject of the next presentation, What Is an IP Address?