DDoS Chart Toppers—BPS, PPS and RPS Greatest Hits

There has been a great deal of buzz of late on the “largest ever” recorded DDoS attack.
New to the scene, monster-sized botnet Mēris is raising some eyebrows with giant requests per second (rps) attacks as shared by Cloudflare (17.2M rps, reported August 19), Yandex (peaking at 21.8M rps on September 5), and KrebsOnSecurity (2M rps on September 9). Some commentary came in on Slashdot, The Record, and The Hacker News.
As a quick refresher, there are several predominant ways DDoS attacks can cause outages to disrupt internet-facing infrastructure:
Clogging internet pipes — bps (bits per second)
Overwhelming hardware — pps (packets per second)
Overwhelming web infrastructure — rps (requests per second)
Overwhelming DNS infrastructure — qps (queries per second)
Historically, Layer 3 and Layer 4 DDoS attacks targeted the pipes leading to an origin, attempting to fill them with bogus traffic so legitimate traffic is unable to reach its destination. Or they are composed of large floods of small packets designed to overwhelm and choke firewalls, routers, and other networking gear.
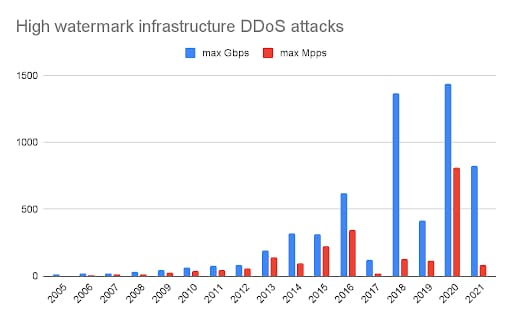
On the bits per second and packets per second front, last summer we mitigated the following chart-toppers — which targeted a hosting provider and European financial services organization, respectively:
1.44 Tbps — Akamai record-breaking
809 Mpps — internet record-breaking
Record requests per second?
Finally, there are Layer 7 (application layer) DDoS attacks or rps that target web and/or application servers, most commonly via HTTP floods. These are the very definition of business as usual — the volumes are consistently high, attack traffic is automatically dropped at the edge, and our platform has ample capacity to manage the legitimate traffic. Rps is a pretty good measure of intensity here, but it tends not to be interesting to report.
With that being said, we recently recorded this whopper of an rps event:
100 million requests per second — record Akamai event
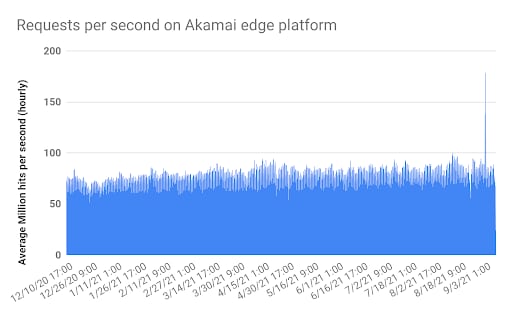
Why didn’t we show-and-tell? While 22 million rps may seem large, on any given day at Akamai we average more than 3x that volume and have seen spikes as high as 8x. Suffice it to say our edge platform has significant headroom to handle customer events, traffic growth, and large attacks, so “business as usual” didn’t strike us at the time as being blog-worthy.
Upon further review of our data, the most recent top rps attack Akamai has seen firsthand was around 5M rps and related to malicious bot activity around a customer event (highly sought-after soft goods launch). This pales in comparison to our normal traffic load and spikes due to legitimate customer activity.
What’s notable about Mēris, a botnet targeting web servers and applications, is that it has yet to be seen on the largest CDN or cloud-based DDoS provider on the planet (we’re talking about us).
Are they choosing specific targets or providers? Are we just waiting our turn?
Meet Mēris — not the botnet next door
Based on what’s been reported, Mēris has amassed an arsenal of 250,000+ compromised MikroTik routers stemming from an unpatched 2018 vulnerability. Once attackers gain access to the device, they then reconfigure the router to become part of their growing botnet. And because routers are designed to interconnect large bandwidths and move tremendous amounts of packets, Mēris can generate exceptionally large quantities of packets per second (pps), which can then be crafted to a full transaction generating huge transactions per second (tps) or requests per second (rps). With the latest attack rounds, Mēris has been engineered to attack Layer 7 applications and services via HTTP pipelining, and as one report noted, is fueled by high-bandwidth ethernet-connected devices for added capability.
While there are industry efforts to uncover and clean up infected MikroTik routers, this process won’t be speedy. Patching and firmware updates alone will not protect these devices, as passwords may already have been exploited from 2018, requiring users to not only change them, but also recheck firewall rules to ensure that remote access is not provided to unknown parties. Users should also look for scripts that they did not create. Given these circumstances, expect the Mēris botnet to be used again ... and again.
While we haven’t seen any Mēris-specific botnet attacks per se, we have mitigated DDoS attacks recently delivered by compromised MikroTik devices used as proxies by malicious actors. It’s clear the 2018 vulnerability is being used in several nefarious ways in an attempt to disrupt customer infrastructure.
IoT supercharges today’s botnets
Growing amounts of bandwidth at the attacker’s disposal means more massive attacks to defend against are around the corner. As mentioned previously, in early summer 2020, we observed record-breaking 1.44 Tbps and 809 Mpps attacks against our Prolexic platform, which served as a foreshadowing of what was in store — global DDoS extortion.
Throughout the various waves of the DDoS extortion campaigns, we witnessed attackers evolve their tactics, techniques, and procedures (TTPs) and bring out bigger and bigger DDoS cannons. For example, the initial wave of extortion attacks averaged about 200 Gbps, but by the third wave, we mitigated attacks upward of 800 Gbps. In fact, in a recent attack campaign, we observed an attacker ramp up bandwidth from 0 to 600+ Gbps in less than a minute.
It’s clear attackers have easy access to DDoS booters and stressors — many are free to download, and there are YouTube tutorials on how to use them — in addition to significant amounts of bandwidth to burn. With home internet speeds commonly at 1 Gbps and the explosive growth of edge computing endpoints to exploit, compromised Internet of Things (IoT) devices will pack a volumetric punch, especially when combined with DDoS amplification and reflection techniques.
These dynamics align with what has been reported publicly about Mēris in terms of its supercharged rps capabilities orchestrated by its botnet operators.
Capacity counters capability ... but not complexity
We’ve been able to weather the storms we’ve seen, sometimes without noticing, because we’ve invested in capacity and networks that scale to several times the size of the largest observed attacks (not just the ones we’ve observed, but those reported publicly).
This is for all measures (bps, pps, rps, and qps) in all locales.
But modern DDoS attack fighting isn’t just about scale. It requires the right human-driven intervention to meet the most complex and targeted assaults head on — for the highest quality of mitigation. Our 225+ frontline Security Operations Command Center (SOCC) responders have developed decades of expertise mitigating the most sophisticated attacks to protect high-risk, complex attack surfaces. And while automation is an important part of DDoS detection and mitigation capabilities, a one-size-fits-all approach doesn’t cut it with today’s attacker TTPs. Having highly available and skilled SOCC experts to review events, customize countermeasures, and address exceptions is a highly sought-after, not easily replicated, capability for industry-leading DDoS defense.
Parting recommendations for Akamai customers
Depending on the kind of assets that you are protecting, the following recommendations in mitigation mode can help protect against Mēris and other DDoS attack–producing botnets:
Applications and APIs
Review rate control configuration to ensure the thresholds are set to the appropriate levels
Leverage Akamai threat intelligence via Client Reputation to block known malicious clients, such as those participating in DDoS attacks, even before the threat actors hit your assets
Ensure proper configuration of WAF and Bot Manager solutions to detect automation and tooling used in attacks
Review caching rules to improve application offload and avoid any unnecessary requests in the event of an attack
Hybrid cloud origin infrastructure
Ensure internet-facing assets are routed onto Prolexic DDoS defense platform to reduce risk
Implement preconfigured mitigations to reduce attack surfaces and take advantage of a 0-second mitigation SLA
Akamai Edge DNS should be enabled to protect customers’ DNS against DDoS attacks, which is sometimes overlooked by network defenders
All Managed Security customers should ensure their runbooks and authorized contacts with the Akamai SOCC are up to date and incident response plans are current.
If you are under attack or threat of DDoS extortion, reach out to the Akamai DDoS hotline, 1-877-425-2624, for immediate assistance. Additionally, if you receive an extortion email, please contact local law enforcement. The more information they have to work with, the more likely it is the criminals will be stopped.



