Common server security issues include malware infections, unauthorized access, data breaches, distributed denial-of-service (DDoS) attacks, and software vulnerabilities.
What Is Server Security?
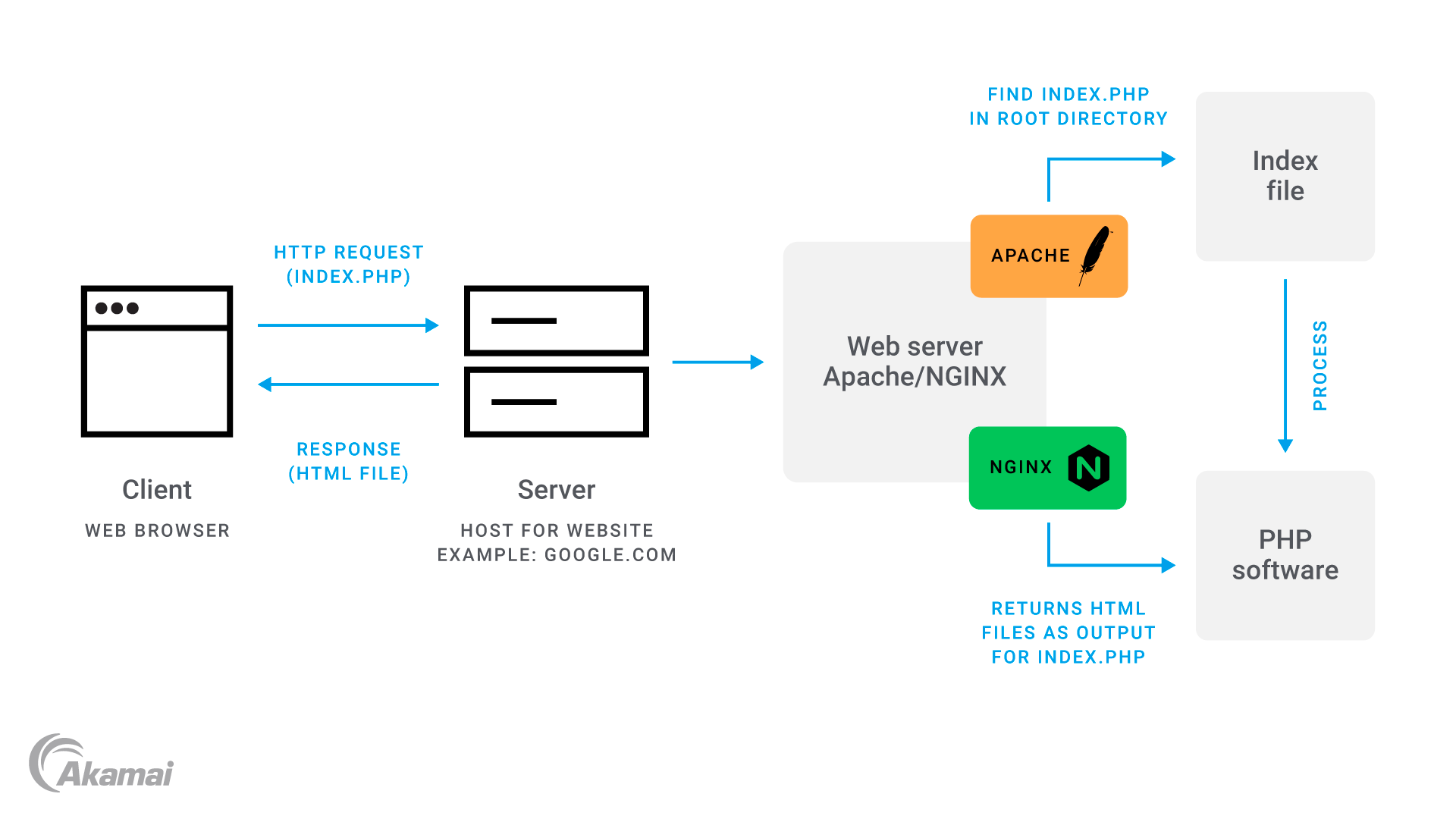
One of the most important aspects of the development lifecycle is understanding server security in the hosting environment that runs our web apps. Our servers allow incoming connections from external systems over specific ports whenever we deploy a web app. Server ports identify incoming and outgoing network traffic.
We need secure connections to maintain integrity of the system. To understand server vulnerabilities, we need to think about where communications take place.
In the example above:
- A client (left), typically a web browser, sends an HTTP request to the server.
- The server receives the HTTP request and processes it.
- The domain name is queried against one or more domain nameservers, usually managed by the domain name registrar.
- The server retrieves or generates the requested content and sends an HTTP response back to the client.
- The client receives the response and renders the content.
During this process, in certain cases, connections to our servers can be from malicious computers looking to exploit vulnerabilities in our server configurations. There are plenty of reasons why a server might be exploited.
Let’s take a look at some common server attacks that take advantage of inadequate server security.
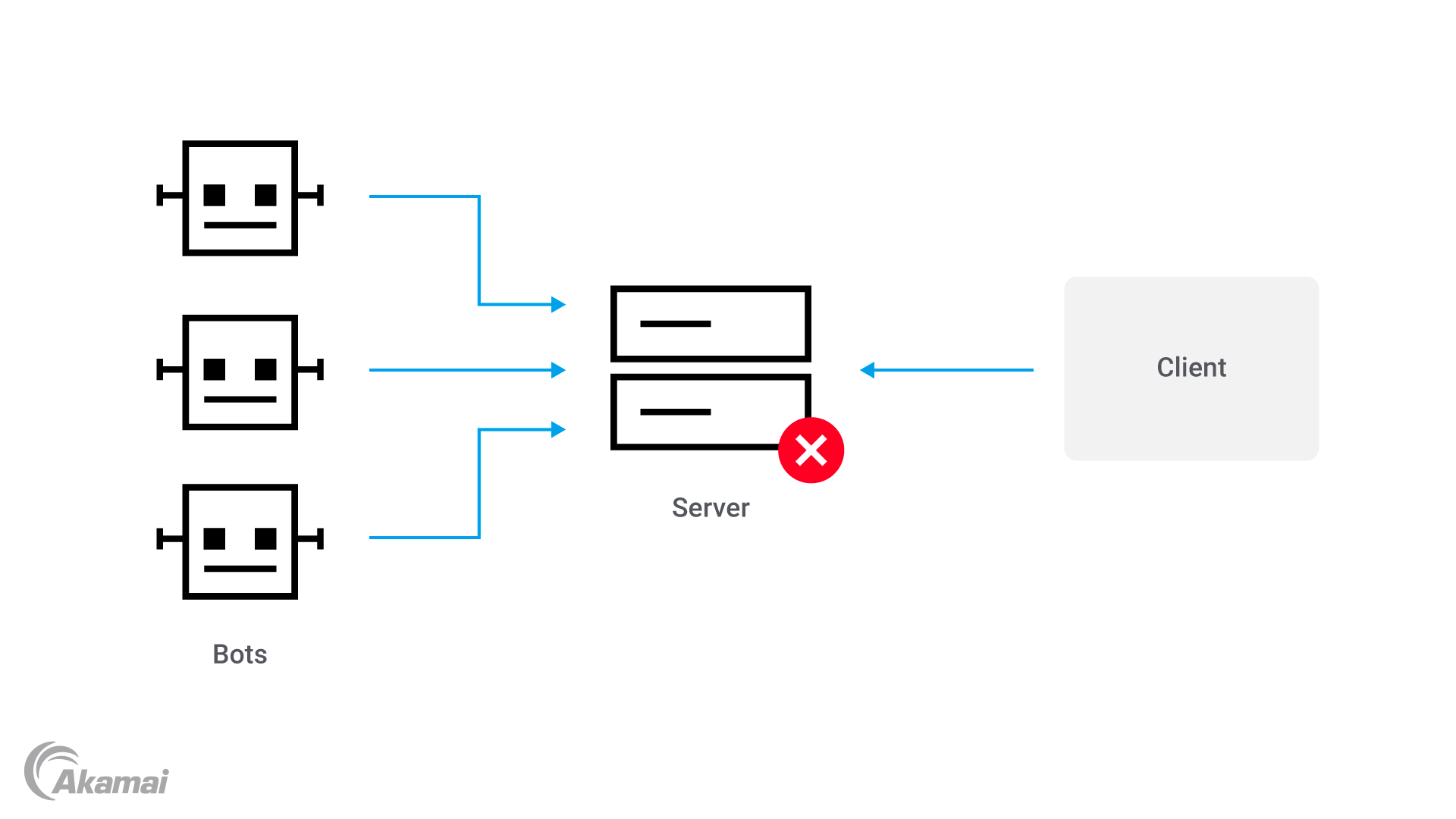
Distributed denial-of-service (DDoS) attacks
In a distributed denial-of-service (DDoS) attack, an attacker attempts to overload a targeted server with a flood of HTTP requests. This is also called an HTTP flood attack. Remember, each time we make an HTTP request, our servers are tasked with responding to the request. If our servers don’t have the resource capacity to meet the number of incoming simultaneous requests, the web server will stall or crash. Moving forward, each subsequent HTTP request will fail, rendering the web server unreachable.
DDoS attacks are generally performed through botnets. Botnets are a network of devices infected with malicious software, also known as malware, which is designed specifically to produce a flood of HTTP requests to a target machine that lacks sufficient firewalls.
The above illustration provides an overview of how HTTP flood attacks work. On the right side, we have the client making a request to the server, but because there are several bots also making requests to the server, thus draining the server’s resources, the client cannot connect to the server.
Directory traversal
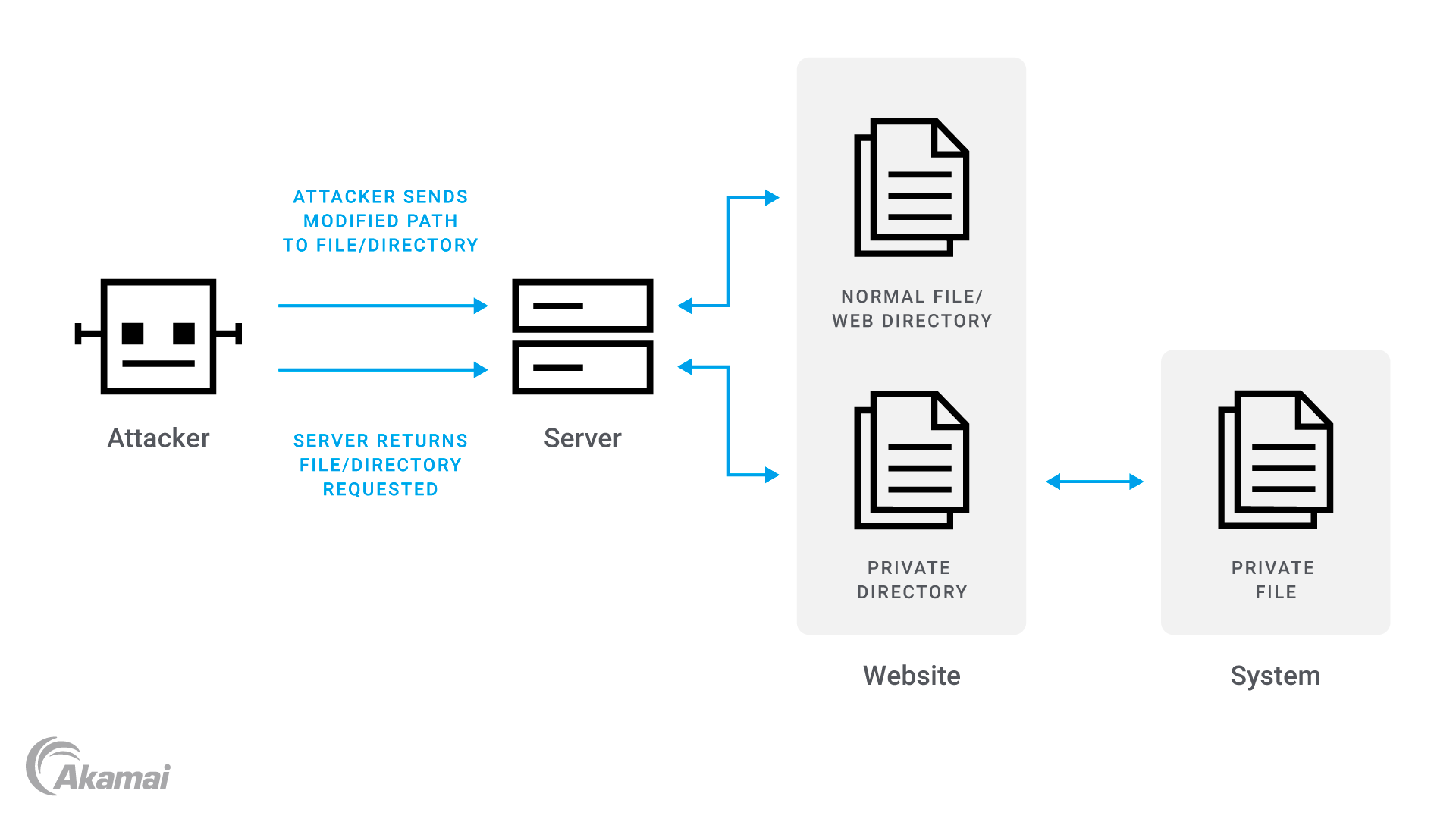
A directory traversal is another common exploit that generally targets poorly configured servers. All web files are served directly from the web root directory. Users connecting to our servers via HTTP web requests should only be able to access specific files from the web root directory without being able to navigate to or execute files from folders that are higher in the directory structure. If this were to happen, it could mean an attacker could gain access to critical system and configuration files, and wreak havoc on the server.
The above image demonstrates how this attack works. The attacker submits a malicious HTTP request using a modified URL, which includes the directory path to a system or configuration file. The server processes the request and, as a result of poor server security configuration or application design, can retrieve the system file and display its contents or source code.
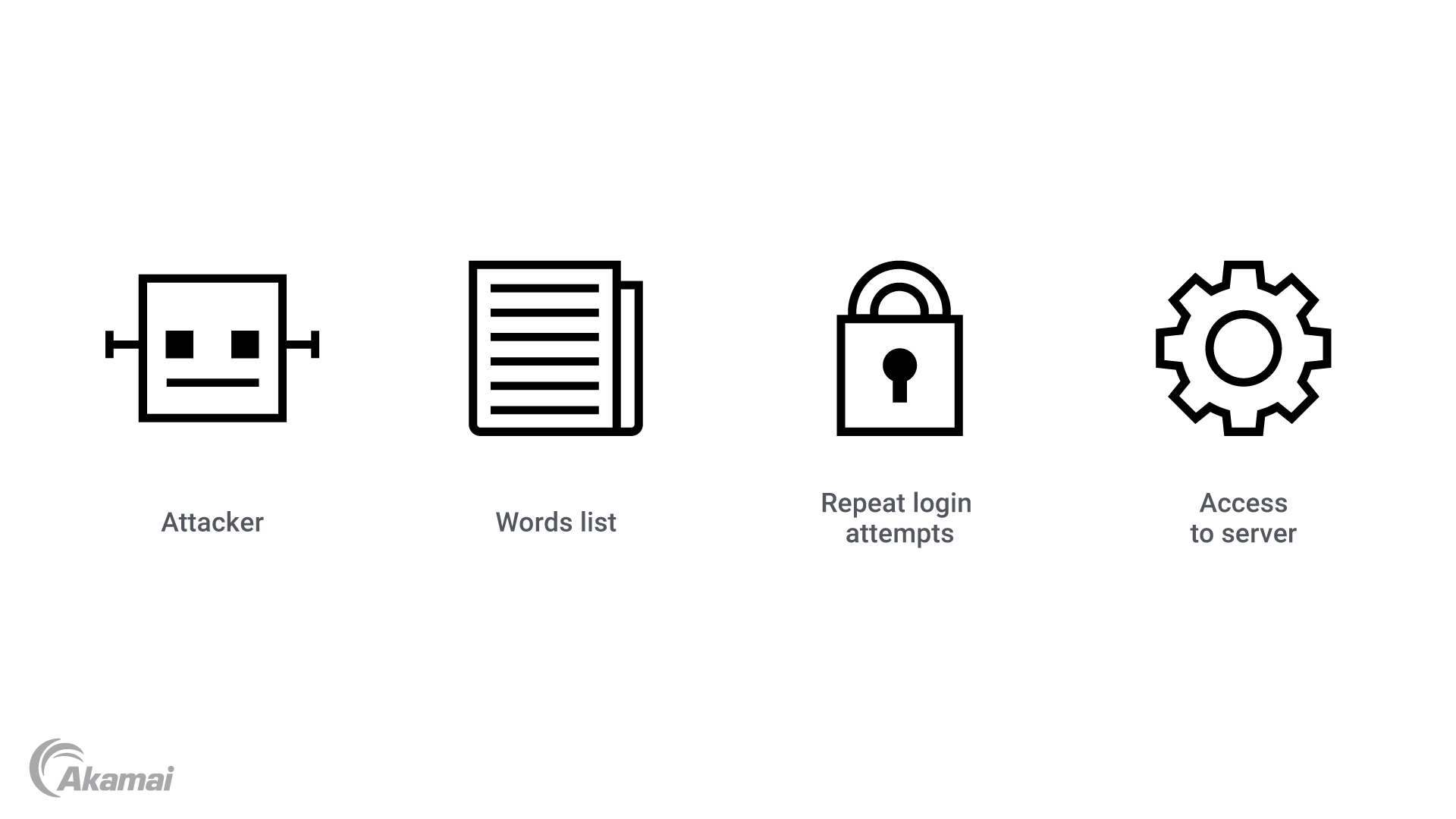
Brute-force attack
A brute-force attack, also called a dictionary attack or account takeover, is another very common attack whereby a malicious agent attempts to gain entry to a restricted access point on your server. This restricted access point is typically the server’s root account or another account with root privileges. Attackers use malware to automatically submit numerous login attempts with automatically generated password and username combinations based on dictionary words.
The illustration above demonstrates how this attack works. On the left, the attacker submits repeated login attempts generated from a word list, using malware. If the correct combinations are found, the attacker will gain access to the server. Brute-force attacks can be highly effective — even if a server uses only SSH key authentication.
Establishing and maintaining server security
Here are some server security best practices to consider when configuring secure servers:
- Keep your operating system and software up to date with the latest server security patches and updates.
- Disable or block any unnecessary services or ports to minimize the attack surface.
- Limit access to your server by only allowing authorized users to connect and interact with it.
- Secure network traffic by using encryption protocols such as SSL or TLS.
- Have a robust backup and disaster recovery plan to minimize data loss and downtime.
- Implement strong passwords and multi-factor authentication to protect against unauthorized access.
- Use firewalls to control incoming and outgoing network traffic.
- Monitor server logs and network traffic for suspicious activity.
- Use intrusion detection and prevention systems to identify and prevent attacks.
- Implement security measures such as file system permissions and access controls to protect against unauthorized access to sensitive data.
Frequently Asked Questions (FAQ)
A secure server is a server that protects data and communications with various security measures like encryption, firewalls, and secure protocols to prevent unauthorized access and ensure that data is safely transmitted and stored.
Yes, a web server can be hacked if it has vulnerabilities, such as outdated software, weak passwords, or misconfigured settings, allowing attackers to gain unauthorized access or control.
Best practices for server security include regularly updating software, using strong passwords and multi-factor authentication, encrypting data, employing firewalls and intrusion detection systems, and conducting regular security audits and vulnerability assessments.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.