Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Zero Trust demands adherence to its core principles: treating all entities as untrusted by default, enforcing least-privilege access, and maintaining comprehensive security monitoring.
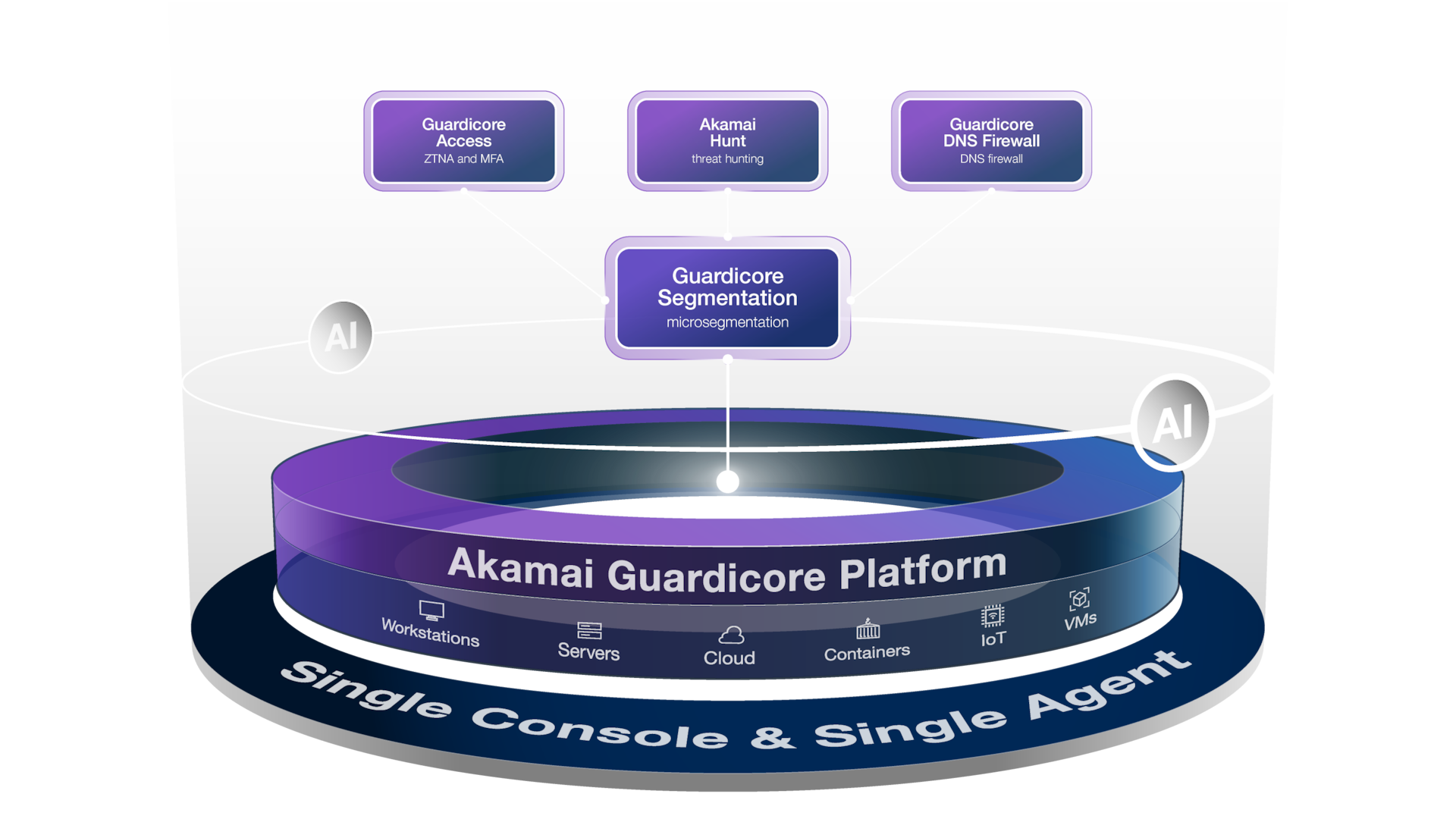
A Zero Trust platform simply and efficiently enables Zero Trust through a fully integrated combination of microsegmentation, ZTNA, multi-factor authentication, DNS firewall, and threat hunting.
What is Akamai’s definition of a Zero Trust platform? What components should this platform have?
The Akamai Guardicore Platform brings together integrated microsegmentation, Zero Trust Network Access, DNS firewall, and managed threat hunting capabilities. These combined components provide organizations with the right solution to adhere to the core principles of Zero Trust, including treating all entities as untrusted by default, enforcing least-privilege access, and maintaining comprehensive security monitoring.
Why put microsegmentation, ZTNA, MFA, DNS firewall, and threat hunting into one Zero Trust platform?
Analysts have predicted that organizations will be looking for more integrated solutions from a single vendor rather than continuing to purchase and manage multiple point products. Putting microsegmentation, ZTNA, MFA, DNS firewall, and threat hunting into one platform provides customers with the first unified ZTNA and microsegmentation offering on the market. This offering provides both north-south and east-west leading solutions combined with end-to-end visibility and AI-empowered capabilities. We believe this combination of solutions will help organizations minimize their attack surface and reduce the risk of data breaches by verifying every access request, regardless of its origin.
What’s the main difference between the newly launched Zero Trust platform and the current product portfolio?
Unlike today where each product is siloed, the new Akamai Guardicore Platform consolidates multiple capabilities into a single agent and single console, easing your setup and maintenance efforts while providing clear end-to-end visibility, allowing you to better manage your access and microsegmentation policies.
How does the Zero Trust platform contribute to an organization’s overall security strategy?
The Akamai Guardicore Platform simply and efficiently enables Zero Trust through a fully integrated combination of microsegmentation, ZTNA, multi-factor authentication, DNS firewall, and threat hunting. Analysts predict that Zero Trust buyers in the near future will be more likely to purchase from a single vendor than continuing to purchase and manage multiple point products. The Akamai Guardicore Platform does more than that. When working on a single platform and a unified agent, you are able to deploy faster, and manage and react faster.
What differentiates the Akamai Guardicore Platform from other security solutions/Zero Trust platforms?
The Akamai Guardicore Platform is the first unified ZTNA and microsegmentation offering on the market, providing both north-south and east-west leading security solutions, end-to-end visibility and AI-empowered capabilities.
How does the Zero Trust approach benefit my organization?
The Zero Trust approach minimizes the attack surface and reduces the risk of data breaches by verifying every access request, regardless of its origin. It ensures that only authenticated and authorized users and devices can access your network and resources, providing a higher level of security.
Who are the target customers of this Zero Trust platform?
Target customers for the Akamai Guardicore Platform are any organization that has an expansive attack surface and is looking to achieve Zero Trust, reduce the risk of ransomware, and comply with mandates.
How does this platform help customers address the surging zero-day and one-day exploitation?
When a vulnerability is announced, it’s a race against the clock to identify and protect potentially compromised systems. The platform, and especially the segmentation module, has already been shown to have capabilities around “ringfencing” potentially compromised systems, preventing any communications with those systems until a patch is issued or another fix is worked out. But this still didn’t address the issue of how to find all of those compromised systems in an expedient manner. The platform now solves for this through our AI-powered chatbot, which in a single query can surface all communicating machines in your environment that may be vulnerable, allowing security teams to quickly create and enforce policy to protect those machines before the vulnerability can be exploited.
What is going to change for our current customers?
The Akamai Guardicore Platform is your new partner for the Zero Trust journey. The platform includes Akamai’s industry-leading microsegmentation solution, access control capabilities, DNS firewall, and more. All you have to do is update your agents to support these new capabilities.
Existing Akamai Guardicore Segmentation customers will need to upgrade their endpoint agents to benefit from the access capabilities. Enterprise Application Access customers will need to migrate.
Core components
What components are included in the platform?
Akamai Guardicore Platform simply and efficiently enables Zero Trust through a fully integrated combination of microsegmentation, Zero Trust Network Access, DNS firewall, and threat hunting.
- Microsegmentation: Agent-based/agentless microsegmentation
- ZTNA: Fast and secure access for your hybrid workforce (formerly Enterprise Application Access)
- Multi-factor authentication: Mitigate risk by requiring MFA as part of your microsegmentation policy
- DNS firewall: State of the art DNS firewall with unique Akamai feeds (formerly Secure Internet Access)
- Hunt: Improve application and network security posture through advanced threat and security risk detection
Can the integrated products (Enterprise Application Access, Secure Internet Access) still be sold as stand-alone products?
Yes, every capability sold as part of the Akamai Guardicore Platform can also be sold separately. The platform contains existing portfolio products, while introducing new integrated capabilities that are only available in the platform.
How does ZTNA enhance the Zero Trust platform?
In addition to microsegmentation, Akamai Guardicore also offers Zero Trust Network Access (ZTNA) capabilities. ZTNA is a security model that assumes Zero Trust, meaning that no user or device should be trusted by default, even if they are inside the corporate network. Instead, access to resources is granted based on strict verification of identity, device posture, and other contextual factors. This approach minimizes the risk of unauthorized access and helps organizations prevent data breaches and insider threats. Users located around the world have access to any type of data center, spanning from fully on-premises to hybrid multicloud.
What is the role of MFA in the Zero Trust platform?
Multi-factor authentication (MFA) adds an extra layer of protection by requiring users to strongly authenticate before gaining network access to the sensitive ports across your data center. By leveraging MFA, you can significantly reduce the compromise of any workloads. Even if attackers manage to obtain credentials or land on an internal system, they would still need to pass additional authentication challenges. Not only does MFA enhance security, but it also provides security teams with greater control and visibility over access permissions. By dynamically opening firewall ports based on authenticated requests, you can ensure that only authorized individuals can access specific resources.
What is Akamai Hunt, and how does it integrate into the platform?
Akamai Hunt is an adaptive segmentation service designed to improve the customer’s security posture over time and allow it to respond effectively to emerging threats and risks.
How does microsegmentation work within the Zero Trust platform?
One of the key components of the Akamai Guardicore Platform is microsegmentation. Traditionally, network security has relied on perimeter-based defenses that focus on securing the outer boundaries of the network. However, as cyberthreats evolve, it has become increasingly clear that perimeter defenses are no longer sufficient to protect against sophisticated attacks. Microsegmentation takes a different approach by dividing the network into smaller, more manageable segments and applying security policies to each segment based on the principle of least privilege. This granular approach to security ensures that even if one segment is compromised, the rest of the network remains protected. With Guardicore Segmentation, every asset is protected, including on-prem data centers, cloud instances, legacy OSes, IoT devices, Kubernetes clusters, and more — without ever having to change consoles.
What are some of the new segmentation capabilities introduced in the Akamai Guardicore Platform?
The Akamai Guardicore Platform introduces several new microsegmentation features that will streamline workflows and enhance cyber resilience. In order to ensure that only authenticated users can access certain resources, the new Multi-Factor Segmentation capability adds an extra level of protection to every segmentation rule. Essential Policy provides global rules that simplify network security. Finally, Worksites offers policies specific to locations or divisions to simplify multi-site segmentation.
Akamai Guardicore Access
Akamai Guardicore Access combines microsegmentation and ZTNA capabilities into a unified endpoint solution that provides a single policy for user-to-application access and segmentation. It provides comprehensive end-to-end visibility from user to workload level, offers identity-based application access control for users irrespective of where they are located, and delivers application access with true endpoint segmentation.
Why does a customer need both Access and Segmentation?
Access and microsegmentation enforce the basic principles of Zero Trust security — all entities are untrusted, least-privilege access is enforced, and security is continuously monitored. Currently, enterprises deploy and manage these disparate point solutions. This creates complexity and operational overhead that can delay an enterprise’s transition to Zero Trust.
Akamai Guardicore Access combines microsegmentation and ZTNA into a unified solution that provides a single policy plan for application access and segmentation. It provides comprehensive end-to-end visibility from user to workload level, identity-based application access control for users, irrespective of where they are located and delivers application access with true endpoint segmentation.
How does Akamai Guardicore work differently from ZTNA plus next-gen firewalls?
ZTNA and microsegmentation are the two key products for any organization that wants to move to a Zero Trust architecture. Depending on its security priority, a business normally starts a transformation with one or the other. With a unified Zero Trust platform, businesses can start with either solution — but over time, they get benefits from a single agent, console, and policy. This reduces the complexity of managing disparate solutions and accelerates the time it takes to get to a Zero Trust architecture.
Specifically for ZTNA, customers can deploy ZTNA and use next-gen firewalls to segment their internal networks and workloads. However, that is a complex and inefficient approach. A unified ZTNA and microsegmentation solution offers a simpler and more secure approach, and it addresses some of the challenges that enterprises face when deploying ZTNA.
Firstly, many organizations do not have a complete picture of the business apps they are using — and the larger the organization, the bigger the challenge. Microsegmentation labeling allows a customer to quickly discover the private apps it has and who is accessing them.
Secondly, once they create an application access policy, with ZTNA on its own, they would then need to ensure that the applications are accessible which means editing firewall rules. With the unified solution, once an access policy is created, with a single click a microsegmentation policy is created instantly.
Lastly, the unified solution provides visibility of the entire path, from the user’s device right through to the application and even down to the process level of the application. That end-to-end visibility allows networking teams to quickly investigate and resolve any application access issues.
What is the added value of installing an agent on my endpoints?
Only an agent can provide your endpoints with Zero Trust segmentation, protecting them against ransomware by limiting endpoint traffic, as well as applying access policies based on the device’s security posture.
What’s the difference between Guardicore Access and the existing identity-based segmentation capabilities in Akamai Guardicore Segmentation?
With the existing identity-based segmentation, customers can create access rules based on Active Directory user groups to provide granular per-user access to applications. Active Directory needs to be registered with Akamai Guardicore to retrieve group and user information. Once that is done, security administrators can create a group based on one or more Active Directory groups.
With the unified endpoint, Guardicore Access leverages the full capabilities of Akamai’s standalone ZTNA solution that can integrate with any modern identity provider. In addition, it includes additional Zero Trust Network Access features such as device posture, context-based access, and so on.
What’s the difference between Akamai Enterprise Application Access capabilities and Guardicore Access?
Customers are now able to enjoy all of the capabilities and features of Enterprise Application Access in Guardicore Access. For the time being, some of the initial setup and configuration will be done in the existing Enterprise Application Access portal, while the day-to-day work will be supported via Guardicore Access.
Why is ZTNA considered more secure than VPN for secure remote access?
Zero Trust Network Access (ZTNA) and virtual private networks (VPNs) are both tools designed for secure remote access, but they have significant differences in their approach to security. ZTNA is generally considered more advanced and secure compared to traditional VPNs. Here’s why:
- Zero Trust approach: ZTNA is based on the “never trust, always verify” Zero Trust approach — no user or device is trusted by default, regardless of its location. Access is granted based on a combination of identity, context, and policy. In contrast, VPNs typically grant access based on network location, potentially exposing the network to threats once a user is connected.
- Granular access control: ZTNA provides granular control over which applications and resources users can access. This results in a more secure posture and mitigated scope of attack should a compromise or vulnerability occur. VPNs, on the other hand, often provide broad network access, increasing the risk if a user or device is compromised.
- Improved visibility and monitoring: ZTNA allows for better visibility into user behavior and access patterns. This facilitates proactive monitoring and rapid response to security threats. VPNs typically offer less detailed monitoring, making it harder to detect and respond to security incidents.
How can customers enable Guardicore Access?
Guardicore Access is an add-on module that is licensed separately. However, customers are able to trial the capabilities for 60 days at no cost. Once enabled, customers need to deploy the Access Connector, integrate Access with their identity provider and directory services, and configure the application access policies.
DNS firewall
What is Guardicore DNS firewall?
The DNS firewall analyzes all of your organization’s DNS queries against a continuously updated threat intelligence library, blocks high-risk connections, and detects other types of malicious activity. This prevents device infection, as well as efforts to use DNS maliciously for command and control and data exfiltration during attacks.
What types of threats does DNS firewall block?
DNS firewall blocks a variety of threats, including malware domains, phishing attacks, ransomware, and other malicious activities that are recognized via DNS queries. It uses continuously updated threat intelligence to maintain efficacy against new and emerging threats.
How does Guardicore DNS firewall stand out from competitors?
Leveraging our reputation as a content delivery leader, Akamai has extensive visibility into global web traffic and is also one of the world’s largest providers of DNS.
We also aggregate extensive log data from across our product lines, providing additional visibility into emerging threats on a global scale. Our elite security and machine learning researchers combine our own first-party data with research by Akamai’s Security Intelligence Group, third-party threat intelligence, and public information to create an extensive cloud-based threat intelligence feed.
Additional advantages include:
- DNS protection everywhere: Using the Akamai Guardicore Segmentation agent allows us to protect assets everywhere.
- Protection against highly sophisticated attacks: To bypass DNS Security tools, malware often uses customer DNS nameservers for their domain, thereby avoiding being detected by the DNS security DNS nameserver. The Akamai Guardicore agent that analyzes all network traffic can detect malicious domain requests addressed to any DNS nameserver.
How do DNS firewall and microsegmentation work together?
When combined, DNS firewall and microsSegmentation provide a multilayered security approach. DNS firewall blocks malicious DNS requests, stopping many threats before they manage to spread, while microsegmentation isolates critical assets, so even if a breach exists, it is contained to the single workload and doesn’t spread laterally to continue infecting other assets.
Generative AI: Product features and security
How does Akamai leverage AI for Zero Trust?
Many aspects of effectively implementing Zero Trust can be streamlined with the use of AI. Here are a few ways that the Akamai Guardicore Platform is leveraging AI:
- Easily communicating with your network: Through the use of AI, the Akamai Guardicore Platform allows its users to communicate with their network logs using natural language to help expedite compliance efforts and time-sensitive incident response activity.
- AI labeling: Creating Zero Trust policy requires the practitioner to have an accurate inventory of each asset that they’re responsible for protecting. This begins with labeling: a notoriously difficult, manual, and time-consuming task. The Akamai Guardicore Platform leverages AI to look into the way these assets are behaving and suggest labels. These suggestions come with a confidence score as well as an explanation as to why the label was chosen.
- AI queries: Osquery is a powerful tool that is built into the Akamai Zero Trust client. It allows businesses to ask questions that pull answers from every protected asset in their environment. The only downside is that asking these questions requires a specific SQL-like syntax. Most CISOs know what they need to ask, but don’t know the syntax required. The Akamai Guardicore Platform leverages AI to translate natural language into queries so even the not-so-technical security professionals can get answers quickly. This is especially useful in vulnerability assessments, like for determining if and how you might be vulnerable to an exploit like Log4j.
- AI policy: Enforcing policy is the ultimate goal when it comes to Zero Trust, but knowing exactly what to enforce is difficult. On one end of the spectrum are overly permissive rules that often allow unwanted traffic. On the other is policy that actually prevents necessary traffic and disrupts the business. AI can be leveraged to suggest just the right policy given your unique traffic patterns.
How can generative AI be used in labeling?
Labeling is the backbone of software-based segmentation. The problem is that many organizations don’t have a single data source with a complete, up-to-date set of server metadata, which is necessary to ensure correct labeling, and by extension, ensure correct enforcement of a comprehensive security policy.
To solve for this, we’re introducing an AI labeling feature. It leverages generative AI capabilities to suggest appropriate labels based on process communications that the solution identifies. The large language model (LLM) utilized here has been trained to recognize prompts in conversational English, and it will identify the most likely identity for machines that are running commercial applications, such as Active Directory, SAP products, Splunk, and many more. It will then suggest both application and role labels for that machine.
What is the Guardicore Copilot?
Guardicore Copilot is a generative AI-powered chatbot that will serve as a built-in segmentation and Zero Trust expert, as well as an in-house cybersecurity advisor. Driven by a desire of our customers to use natural language to query their networks, to speed up manual tasks, and to have something that can advise them based on best practices, the Copilot aims to provide capabilities in two key areas: accelerating operations and providing support.
How do we keep the Copilot from hallucinating?
There are two strategies we use:
- We are feeding the LLM prompt with up-to-date information that is specific to the customer environment, to make sure it provides relevant information based on the input prompt.
- The LLM returns answers in a strict format that adheres to a well-defined schema that can be validated. Then, before sharing the answer with the user, we validate the answer format and content against the schema and the customer’s environment context (labels, assets, etc.).
Can Guardicore AI (Copilot) receive queries and instructions in languages other than English?
Not at this time.
Is the use of AI changing the types of attacks organizations face?
No, AI isn’t changing the types of attacks organizations face. Malware and ransomware continue to be the most common threats. But AI allows attackers to automate and dramatically multiply their efforts so they can pull off attacks faster, with greater accuracy, and most importantly — on a much larger scale.
How is Akamai guaranteeing the security of its generative AI features?
AI has come into the hands of both attackers and defenders at the same time. This should realistically benefit us — the defenders — as we’re not being caught off guard with this technology. It is better (and actually more secure) to embrace AI rather than ignore it.
To this end, Akamai is following established guidelines from governments and leading vendors, as well as shared best practices, but it’s important to note that at this time there is no compliance standard for AI (like SOC 2 for SaaS).
What AI models and training data did Akamai use for AI assistant and AI labeling?
We are utilizing the Azure OpenAI infrastructure, which offers managed dedicated instances of OpenAI’s LLMs. We then train these models internally. The LLM prompt is fed with up-to-date information that is specific to the customer environment to ensure it provides relevant information based on the input prompt.
When a customer asks Akamai Guardicore AI a question, where does that data end up getting stored?
Customer queries are stored exclusively in the Akamai Guardicore SaaS cloud infrastructure — just like any other customer data. The text is processed locally as well.
What types of data is Akamai Guardicore AI able to access? Just network logs and machine configurations, or actual files like documents, etc.?
The Copilot has access to Akamai Guardicore APIs — like assets, labels, etc.
Can the Copilot enforce rules automatically? Or does it just suggest rules that should be in place?
As an AI assistant, the Copilot only retrieves information and suggests changes. It does not apply changes on its own. Policy enforcement remains the primary responsibility of the user.
How long is the chat history stored? And how will that data be used?
We are storing chat history for 180 days. Chat history is stored mainly to allow users to go back to conversations they had with the Copilot in the past, but we are also using the chat history for monitoring and improving the Copilot’s performance.
The Akamai Hunt service uses AI to detect anomalies. Can the Akamai Guardicore Copilot do this as well?
Currently, AI-powered anomaly detection is a service that is only available to Akamai Hunt customers.
How is the Copilot different from all other AI bots?
The Copilot specializes in cybersecurity, and specifically in using the Akamai Guardicore Platform to secure your network.
Integration and compatibility
Can the platform easily integrate with my existing infrastructure?
The Akamai Guardicore Platform is designed to integrate seamlessly with existing IT infrastructure. It supports a wide range of environments, including cloud, on-premises, and hybrid setups, ensuring flexibility and ease of deployment.
Can the platform be used across multiple cloud environments?
The Akamai Guardicore Platform can be used across IaaS environments across all cloud environments, and at the moment it can be used in PaaS environments in Azure deployments.
What are the known limitations of the unified agent?
- The integration is relevant only for SaaS customers.
- Clientless applications are not currently supported.


