Emotet: A Year in the Life of a Malware

Emotet malware has been around since 2014, but 2020 saw a resurgence of attacks. In September 2020, Emotet affected 14% of organizations worldwide. So, what is Emotet? And why is it so dangerous?
Emotet is a sophisticated trojan that is most commonly used as a dropper for other malware. This means that after gaining access to an Emotet-infected device, its operators can download additional malicious payloads, also known as second-stage payloads, to the compromised machine.
Those second-stage payloads can be any type of malicious code, from other Emotet extensions and modules to other malware such as ransomware.
Emotet is usually propagated and spread via phishing email attachments or embedded links that, once clicked or opened, launches the malicious payload. The malware then attempts to move laterally within a network by brute forcing user credentials and writing to shared drives.
Since early this year, numerous agencies and security vendors have reported a significant increase in cybercriminals targeting victims using Emotet phishing emails. This increase flags Emotet as one of the most prevalent and continuous threats.
Emotet infection in the wild
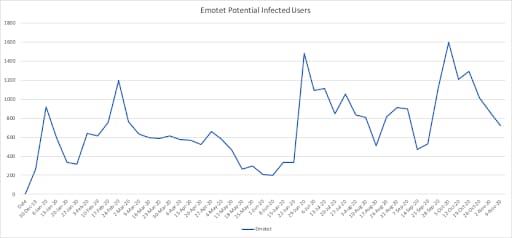
During 2020, Akamai was able to track some of the activity related to Emotet infection in the wild, monitoring access to websites associated with Emotet malware. According to sampled traffic from numerous geographies we were able to see a strong increase of Emotet infection in the months of February, July, and October in 2020. This uptick was observed by other security vendors as well.
How to minimize the risk of emotet
As with all malware, adopting a defense-in-depth approach is your best chance of blocking Emotet early in the kill chain. A cloud-based secure web gateway (SWG) that looks at all outbound Domain Name System (DNS) and URLs can block requests to Emotet delivery sites early and before any IP connection is made. In the event that a device does get compromised, that same security control point can proactively block requests to command and control (CnC) servers when the malware attempts to download secondary payloads.
Deploying an SWG that has multiple payload analysis engines combined with an endpoint antivirus (AV) or endpoint detection and response (EDR) is also recommended. That allows you to block the Emotet payload.
To block the initial infection, add an additional layer of protection over and above your email gateway. For example, a solution that can provide real-time protection when a malicious link is clicked and verify the requested resource adds additional protection and can block non-email phishing attempts, such as those delivered via social media or messaging apps.
Finally, ensure that you continue to educate users about phishing: Do not open attachments or click on URLs ... and always err on the side of caution.



