Akamai Prevents DDoS Attack on Major U.S. Customer
Executive summary
On August 27, 2024, at approximately 17:18 UTC (or 1:18 PM ET), Akamai successfully detected and mitigated a distributed denial-of-service (DDoS) attack against a large customer headquartered in the United States.
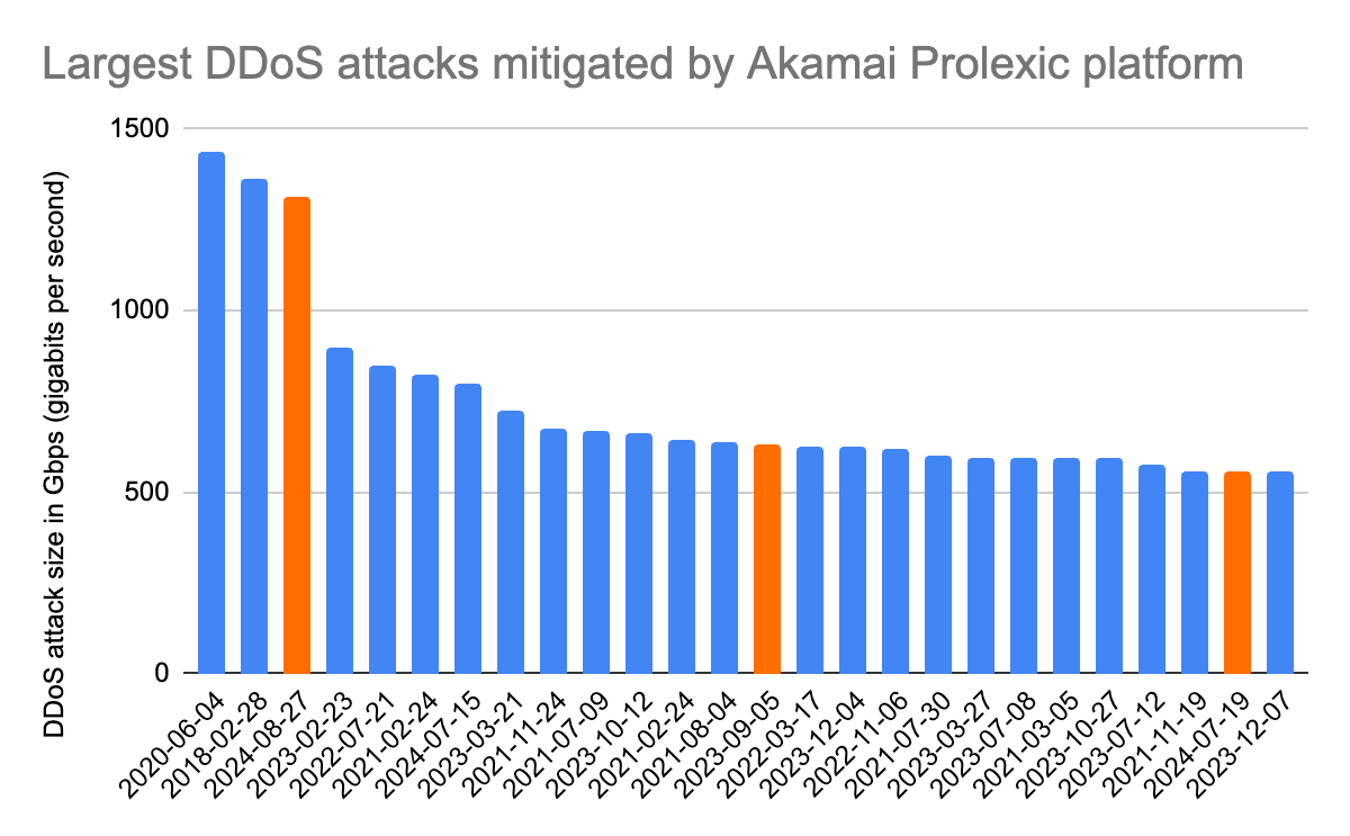
The attack peaked at 1.3 terabits per second (Tbps), making it the third-largest volumetric DDoS attack recorded on the Akamai Prolexic platform, and the most significant DDoS attack observed in the past four years.
Despite the attack's intensity and duration, which lasted approximately 12 minutes, there was no impact on the customer or its legitimate users.
The same customer was targeted with a significant DDoS attack nearly a year ago, which was also successfully mitigated by Akamai Prolexic, our DDoS protection platform, with no impact.
Breaking down the attack
It is an understatement to say that DDoS attacks have been consistently getting larger and more sophisticated over the past few years. With powerful and well-funded nation-state actors and highly resourced professional cybercrime organizations like Killnet or Anonymous Sudan that offer DDoS as a service, today’s DDoS attacks are a level up.
In this instance, the attackers used a highly distributed botnet that cycled through a series of attack vectors within a very short period, which clearly indicates that the attack was orchestrated with a highly programmatic approach. While the vectors — UDP flood, UDP fragment, TCP ACK flood, etc. — were not novel, the scale and the constantly and rapidly evolving pattern of the attack showcased the sophistication of the attack.
While DDoS attacks are never happenstance events and DDoS is almost always the result of a targeted attack, the targeted destination IP addresses, the scale, and the sophistication of this attack make it reasonable to conclude that this particular attack was from a very well-resourced entity that intended to deprive more than 20% of the American population and businesses from accessing the customer’s internet-connected services.
At the peak of this DDoS attack, close to 30 Prolexic scrubbing centers globally were automatically activated to mitigate the attack and ensure that there was no impact on the customer’s digital infrastructure and web-facing assets. Figure 1 shows how Prolexic’s automation and machine intelligence, along with 20+ Tbps of dedicated cloud scrubbing capacity, scaled in realtime to mitigate the DDoS attack in zero seconds.
Detect and mitigate attacks
The Prolexic platform employs a wide arsenal of technologies to intelligently detect and mitigate DDoS attacks. Among many others, these technologies include:
Real-time detections observed via proprietary line rate telemetry collection systems
A wide array of mitigation capabilities that are proactively deployed with attack signatures before an attack starts
Tooling that allows for reactive countermeasures to be deployed in subsecond to minute intervals
The automated collection of training data from dynamically learned traffic allows the Prolexic DDoS protection platform to proactively mitigate the most sophisticated and multivector cyberattacks.
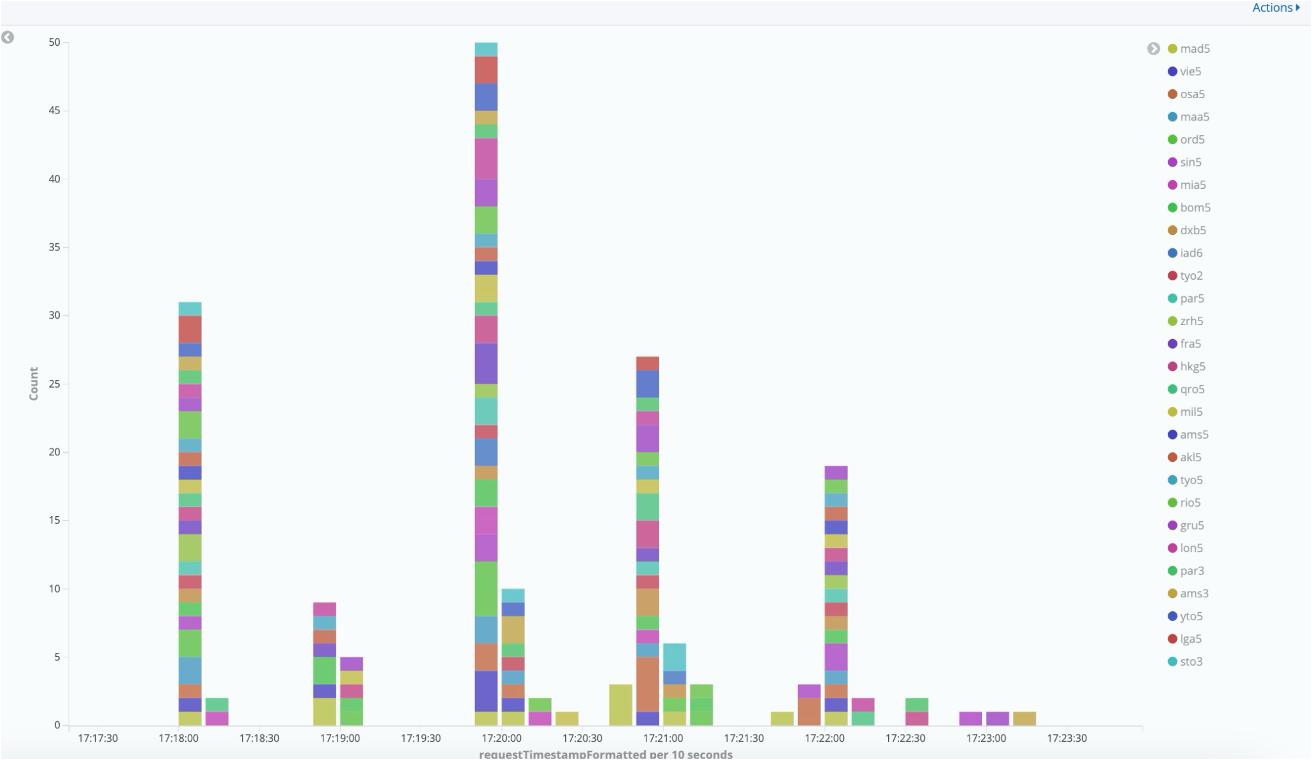
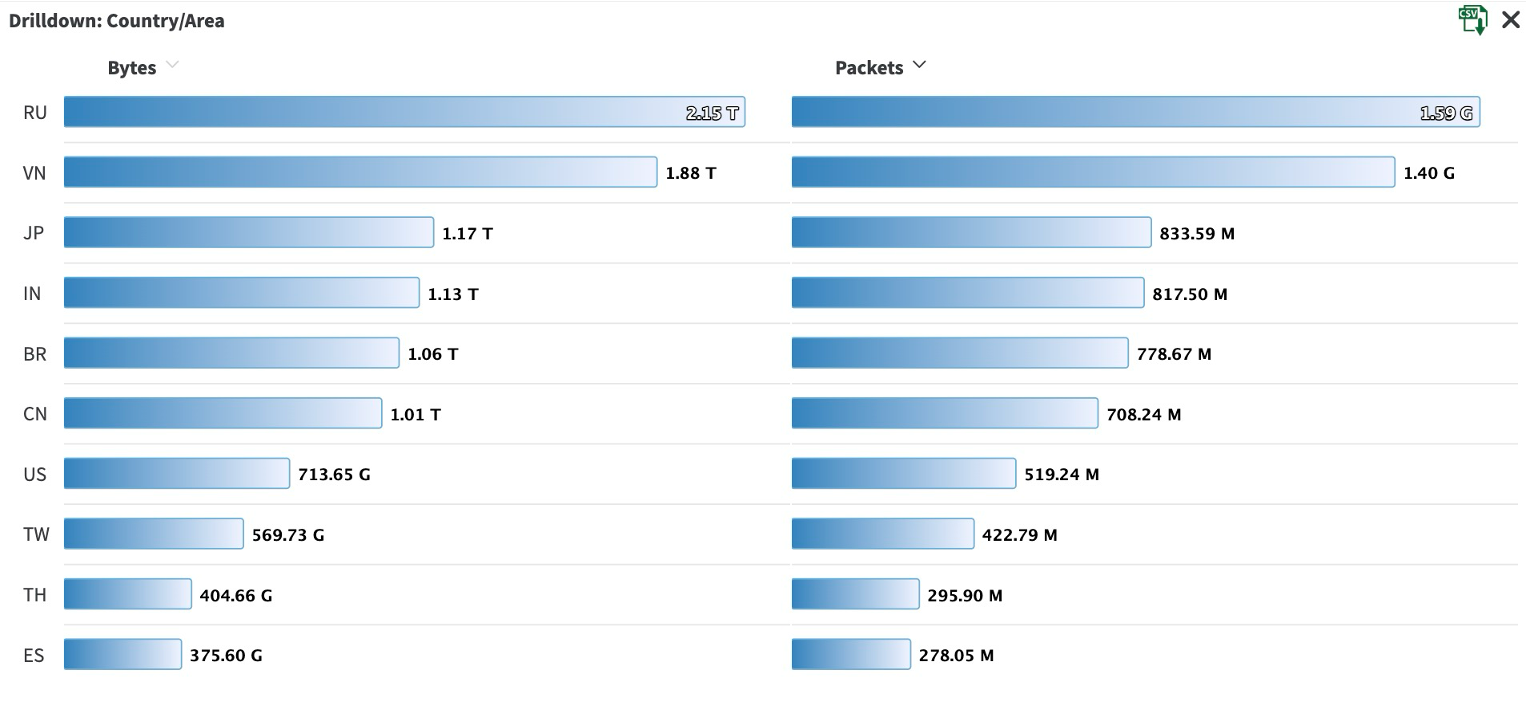
Figure 2 showcases the global distribution of the botnet as evidenced by the IP addresses that sent the attack traffic.
During peacetime, the customer gets legitimate traffic mostly from U.S.-based IP addresses. However, during the attack, we observed malicious internet traffic sourced from IP addresses in Russia, Vietnam, Japan, India, Brazil, and China, among others.
It is common for hackers and malicious actors to infect seemingly benign Internet of Things (IoT) devices with malware or hack into their often insufficient authentication systems and then use such devices as part of a global distributed botnet to command and control DDoS attacks. It is possible that some of these IP addresses were spoofed to mask the original IP addresses of the botnet devices or command and control communication systems.
Witness the power of peacetime cybersecurity preparation
The 4th-century Roman historian Publius Flavius Vegetius Renatus wrote (translated from the Latin), “If you want peace, prepare for war.” It is uncanny that this idea is still one of today’s most effective defense strategies — it’s certainly true for DDoS attacks in 2024.
The Prolexic customer who was attacked on August 27, 2024, has an exceptionally robust defense model based on positive security, which has been collaboratively built and refined by the customer’s network security team and Akamai’s Security Operations Command Center (SOCC) over a decade of continuous engagement.
A well-defined incident runbook and a multicloud resiliency model
Together, the customer and Akamai have worked diligently to minimize the potential vulnerabilities and the attack surface for all DDoS attack vectors ever monitored. A well-defined incident runbook that saves precious seconds when there is an attack of this scale is a cornerstone of successful response and incident management.
Additionally, the customer used Akamai's multicloud resiliency model. This includes Akamai Edge DNS for Layers 3 to 7 attacks that target DNS infrastructure and availability; Akamai Connected Cloud for HTTP(s) and API attacks on Layer 7; and, above all, Akamai Prolexic for Layers 3 and 4 attacks on all ports and protocols.
This combined impact of machine intelligence and human intelligence resulted in a superior security posture that effectively mitigated the DDoS attack in real time while ensuring zero impact to the customer’s digital infrastructure and access for the end consumers.
Clean traffic delivered to the customer
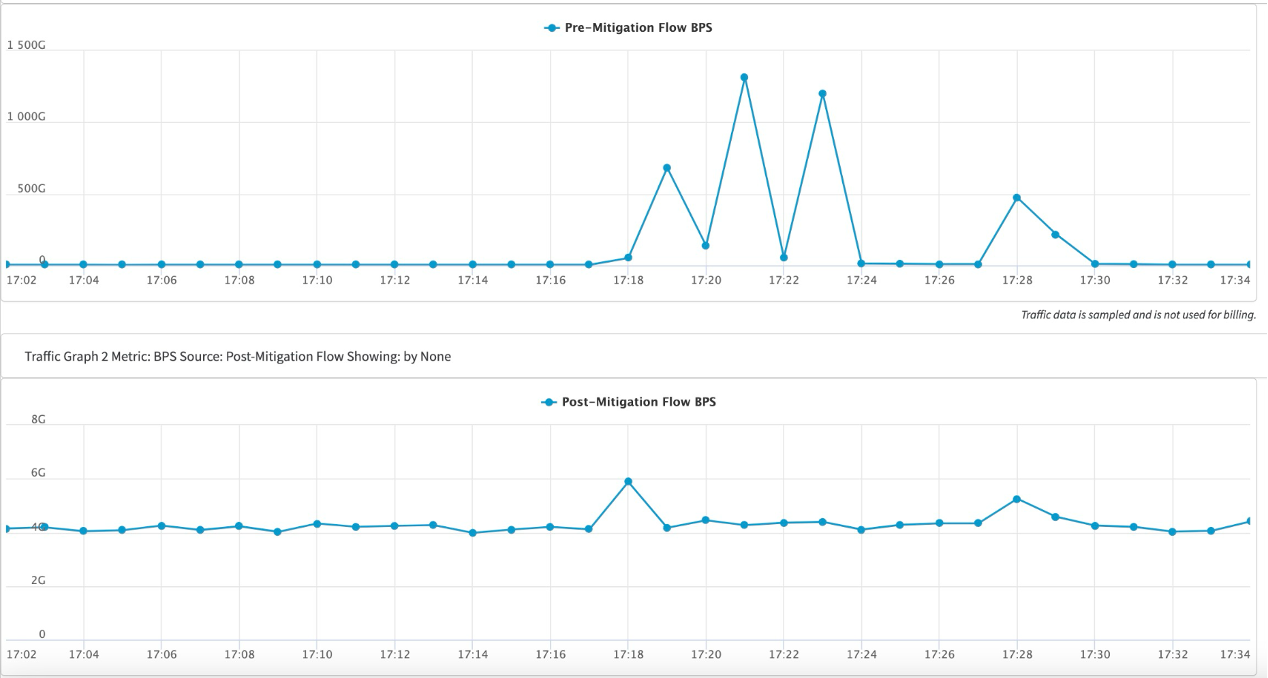
Figure 3 juxtaposes the attack traffic prior to mitigation by Akamai Prolexic and the cleaned-up traffic that flowed from Prolexic to the customer's servers. The small spike observed at the 17:18 UTC timestamp is in accordance with the specific limits and thresholds set by the customer.
Buckle up — the DDoS attack rollercoaster is here to stay
The DDoS attack shown in Figure 3 isn’t an isolated cybersecurity incident; high-traffic websites across all major industries are being attacked on a continuous basis, making it a necessity to have proper defense technology in place. According to DDoS: Here to Stay, a white paper published earlier this year by FS-ISAC and Akamai, 35% of all DDoS attacks in 2023 were aimed at the financial services industry, which has surpassed the gaming sector as the most-attacked vertical.
Driven by a dramatic surge in the power of botnets and hacktivism motivated by the ongoing geopolitical wars, the financial services industry experienced a 154% increase in DDoS attacks between 2022 to 2023.
High technology and media/entertainment are the other two industry verticals that often witness DDoS attacks that disrupt the availability of their Layer 7 web applications, DNS, and the underlying digital infrastructure (Layers 3 and 4) that powers it all.
The persistence of DDoS attacks as a cyberthreat is evidenced by the fact that the U.S.-based customer that was subjected to the attack on August 27 has consistently been protected by Akamai Prolexic from ever-increasing DDoS attacks by cybercriminals over the past two years.
Stay buckled up even if you’ve been on this ride before
Figure 4 shows the three instances (of the 25 largest volumetric attacks) that targeted the same business that were mitigated by Prolexic. The key takeaway is that businesses across all industries must proactively establish a robust security posture against the rising tide of record-breaking DDoS attacks.
The direct and indirect costs of inadequate DDoS protection
Sometimes, organizations mistake the limited capabilities of on-prem solutions without a cloud backup or internet service provider (ISP)–driven solutions for adequate protection against DDoS cyberattacks. Similarly, businesses might mistakenly believe that just machine-level automation without expert-driven managed services would result in adequate protection against large and complex DDoS attacks.
It is crucial, however, to identify whether automation and artificial intelligence by themselves are smart enough to ensure that the mitigation process itself does not lead to further challenges; for example, by automatically blocking an entire protocol when trying to avoid certain protocol attacks, thereby preventing legitimate traffic and legitimate users from accessing your services. In other words, if done wrong, an automated DDoS response without the discernment of human discretion may successfully block an attack but cause just as much damage.
The impact of such inadequate DDoS protection measures range from direct and indirect financial losses, reputational losses, and the significant human resources hours needed to reboot and stabilize your systems.
DDoS protection requires a mature and differentiated approach
Akamai Prolexic takes a mature and differentiated approach to DDoS protection for customers. This approach has been distilled over 20-plus years of market leadership in protecting many Fortune 1,000 companies. The platform combines advanced machine intelligence along with the expertise of more than 220 global SOCC team members to build a defense-in-depth DDoS protection strategy for customers.
Prolexic offers the flexibility to be run as an on-prem, cloud, or hybrid DDoS protection platform, and the ability to keep the platform’s protection always on, or enabled on demand.
Adopt an in-depth strategy against all types of DDoS attacks
We advise businesses and organizations around the world to revisit their DDoS security posture and strengthen their defense systems to withstand attacks similar to the August 27 attack.
The 7 steps we recommend to address DDoS and related cyberattack risks
Assess risk, including the existing DDoS mitigation services. Conduct a thorough and proactive risk assessment that involves your DDoS defense provider — specifically in terms of extremely forceful sustained attacks like the one described in this post, and whether your existing defenses are sufficient.
Review critical subnets and IP spaces, and ensure that they have mitigation controls in place.
Deploy DDoS security controls in an always-on mitigation posture as a first layer of defense to avoid an emergency integration scenario and to reduce the burden on incident responders.
Extend your security posture through an edge-based network cloud firewall beyond basic DDoS protection. A firewall at the edge of your network, in front of (and in addition to) your existing firewalls, is a powerful, easy-to-deploy, and easy-to-use tool to quickly, centrally, and globally block traffic that you don’t want to hit your networks (or certain targets within your networks). Akamai Prolexic provides a network cloud firewall as part of its DDoS defense capabilities that we consider a key defense capability.
Protect your DNS infrastructure from DNS-focused DDoS attacks. Ensure that you have a robust authoritative DNS solution deployed, like Akamai Edge DNS, either in primary or secondary mode. If you have on-prem or hybrid DNS infrastructure, use a DNS proxy solution like Akamai Shield NS53, which can implement dynamic security controls to protect your network from DNS resource exhaustion (NXDOMAIN) flood attacks.
Develop an incident response plan and crisis response team. Proactively develop a comprehensive incident response plan that outlines the steps to be taken in the event of a DDoS attack. The plan should include roles and responsibilities, communication channels, and predefined mitigation strategies. Ensure that runbooks and emergency contacts are up-to-date.
Extend your security against DDoS threats beyond the network layer. Protect your applications and APIs from application-layer attacks with Akamai App & API Protector, a robust web application firewall (WAF) that prevents malicious HTTP requests over ports 443 and 80.
Contact us if you’re under attack right now or if you need Akamai’s help to future-proof your security.