6 Common Bad Bots — What They Want and How They Get It
Bots are automated programs designed to carry out tasks online, often operating on websites or applications. There are good bots, like search engine crawlers and site development and monitoring services, which improve user experiences and enhance business performance. And then … there are bad bots. Bad bots attack organizations by disrupting services or stealing data.
If your organization has an online presence, then bot attacks are probably a growing concern for you. In this blog post, we’ll look at six of the most common types of bad bots. What are these bots trying to do, and how can you protect yourself against them? As you familiarize yourself with these threats, you’ll be better equipped to defend your digital assets.
How to distinguish between good bots and bad bots
There are many good bots that perform valuable services for companies and their users.
For example, search engine bots look at your website’s robots.txt file, then crawl your website to index content for SEO. This makes it easier for your users to find what they're looking for, and ranking highly in search engines is critical to many organizations’ marketing objectives.
Other bots might handle data collection for analytics to help inform decisions about inventory and stock based on what users are viewing on the site. Still others might be behind features like customer support chat to improve user experiences by resolving their questions more quickly.
Intent and behavior
The differences between a good bot and a bad bot are intent and behavior. Bad bots have malicious intent — like stealing data, overloading servers, or performing fraudulent activities. They’re found in every industry, from games to healthcare, targeting both corporations and individual end users.
That malicious intent shows up in the behaviors of those bots – for example, bots that attack login pages because their intent is to test stolen credentials to see if they work on the targeted website. The behavior is important because bad bots aren’t just unknown bots you’ve never seen before; bad bots often try to impersonate bots you know and allow. This means that a bot might seem like a good bot until you discover its intent and behavior, which helps you see through the impersonation attempt.
And, unfortunately, there are as many bad bots as there are good bots. We’ve outlined six of the most common bad bots to illustrate their intent and behavior.
Bad bot #1: The DDoS bot
Decades ago, the denial-of-service (DoS) attack was common. A hacker would use a single device (their computer) to flood a remote system with requests, intending to overload resources and render the system unavailable. And DoS attackers, just like legitimate businesses, have been automating their models to include bots.
With global connectivity and automation, this cyberattack evolved, and now we have the distributed denial-of-service (DDoS) attack. No longer involving a single device, DDoS uses a network of infected devices (a botnet) to flood a targeted server with internet traffic. Overwhelming the target server may result in a service slowdown or a complete outage. Entire websites or apps can be rendered inaccessible to legitimate users. DDoS bots allow the attacker to scale the attack to levels not possible with just a single computer or two.
DDoS attacks may be used to sabotage a competitor or to create a smokescreen while other malicious activities — a data breach, for example — are carried out. They may be used to extort businesses or as a form of hacktivism.
Bad bot #2: The web scraping bot
Next is the web scraping bot. These bots crawl across an entire website, automatically extracting its data. Scrapers often target valuable content such as product prices, user reviews, and proprietary information. As an example, a business may use a web scraping bot to steal content or undercut pricing strategies from a competitor. Unlike other bad bots that launch attacks over limited periods (like a day or a week), scraper bots ping websites all day every day until they’re blocked, causing site performance to degrade.
Aside from site slowdowns, are content scrapers actually harmful? All the data on your publicly available website is, after all, publicly available. Is a bot’s automated and systematic access of that data any different from a legitimate user? Yes. The automated nature of web scraping bots can lead to revenue loss and even theft of intellectual property. Your website is meant to be browsed one page at a time by humans; it’s not meant to be systematically scoured and copied by a machine.
There’s a significant difference between a human user who is browsing a site to gain information they’ll use personally and a scraper bot harvesting every bit of content to be used by competitors to undercut the prices of your product catalog or by scalpers to scoop up inventory the second it sees a hot item has come back in stock.
Bad bot #3: The credential stuffing bot
For credential stuffing bots, cybercriminals start with a list of stolen username/password pairs — perhaps by pulling it from a past data breach or by purchasing it on the dark web. Assuming that many people use the same username/password combinations for multiple user accounts, the attacker tests these credentials, which were valid on at least one site, to attempt authentication on other sites (Figure 1).
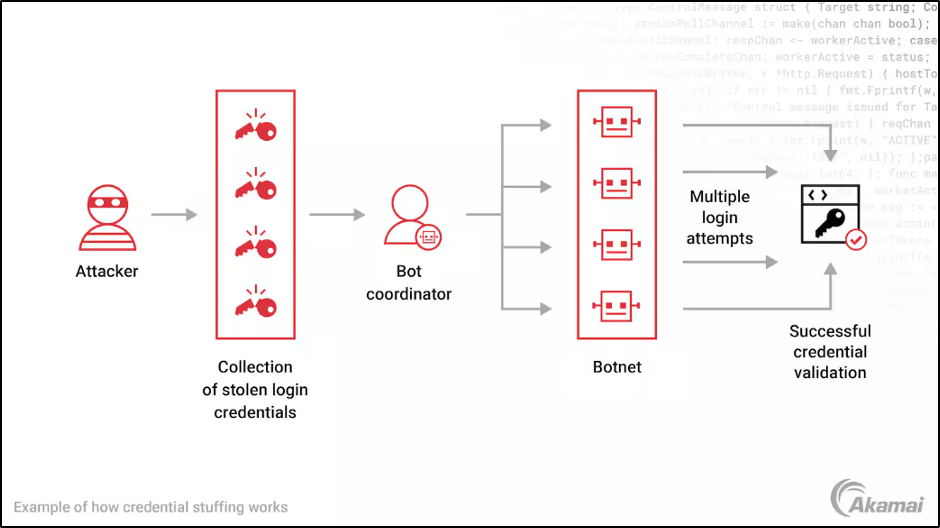
Fig. 1: How credential stuffing works
Again, bots can automate these attempts rapidly and without end. These attacks can lead to large-scale account takeover (ATO), exposing sensitive data from users and businesses. Other ramifications may include identity theft and financial losses.
At its most primitive, a credential stuffing attack is a brute-force attack thatworks like this: launch as many requests at the login as possible to overwhelm the bot management system. Typically, the goal is not to generate enough traffic to DDoS the site, but enough to make the bot management system “fail open” — basically, to not be able to evaluate every request so lets some requests through to avoid blocking potentially legitimate traffic. If not mitigated, the brute-force attack works and allows the bot operator to validate a large number of credentials in one attack.
Bad bot #4: The spam bot
You’re likely all too familiar with spam bots. They flood websites, blogs, and social media platforms with unwanted content (Figure 2). Spam might come in the form of comments on posts, instant messages, or emails. Typically, these bots are used for phishing scams with malicious links that users will follow, leading them to unwittingly download malware or disclose personal data.
In other cases, spam bots may simply be promoting unrelated (and unsolicited) products. And, of course, spam bots can also be used to post misinformation or make users on a social media site believe a particular opinion is more popular than it really is.
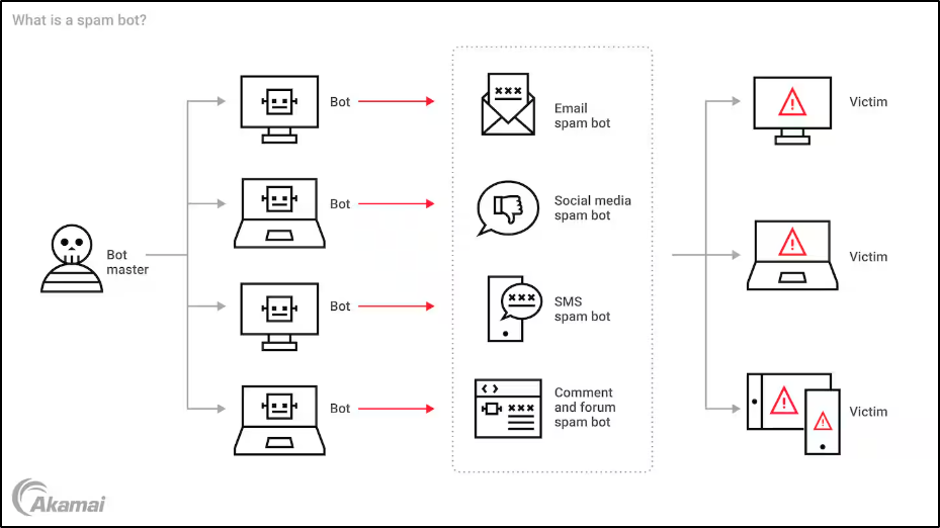
Fig. 2: How a spam bot works
Spam bots will damage the end-user experience. However, they can also hurt the website owner’s business reputation, lead to security breaches if users click on those malicious links, and even harm users if the bots spread misinformation (such as posting incorrect information about how to get help during a natural disaster).
Bad bot #5: The credit card testing bot
When attackers have information from stolen credit cards, they may use a credit card testing bot to automate the process of attempting small transactions on ecommerce sites to see if those cards are valid. Once valid credit cards are identified, attackers can make larger fraudulent purchases and then sell the credit card information to other attackers who will also attempt to make purchases.
If these types of bots are used on your site, you may experience financial losses from charge-backs. In addition, your business credibility may be harmed. So, it’s important to detect and block these kinds of bot attacks swiftly.
Bad bot #6: The click fraud bot
Based on the name, you can probably guess what click fraud bots do. They’re designed to generate false clicks on advertisements. Bots such as these may click on ads multiple times, or mimic the behavior of a legitimate user to avoid detection.
Why might an attacker program a bot to do this? Consider a business that launches a click bot campaign to click on ads from its competitor. Every ad click costs this competitor a few cents. Automate this with a click bot, and the company’s advertising budget is spent without achieving the desired audience engagement. In addition, these fraudulent clicks may skew the company’s engagement numbers, causing it to make business decisions on faulty data.
As another example, think of the social media influencer whose earnings increase as more people view their videos or click on ads during their videos. By using a click fraud bot, a malicious user can artificially inflate engagement and conversions to earn more money.
The challenges of malicious bot traffic
Across the six major categories of bad bots, we can see that these attacks aren’t random; they’re typically driven by specific motives benefitting the attacker, including:
- Financial gain
- Competitive advantage
- Disruption and sabotage
- Information gathering
Bot operators are continuously innovating and finding new ways to evade detection, making bad bots harder to stop. Some of these innovations include:
- Mimicking human behavior more effectively, which makes them difficult to distinguish from legitimate users
- Using proxies or frequently changing IP addresses
- Disguising their user agent to look as if they’re legitimate web browsers or devices
- Creating synthetic telemetry, like mouse movements and clicks, that appears human
Effectively managing bot traffic is a delicate balancing act. If you block too aggressively, you disrupt the essential functions of good bots or inconvenience real users. That’s why most modern organizations rely on advanced bot management tools to accurately filter out malicious bots without impacting legitimate web traffic.
How to protect against bot attacks
Protecting your organization from bad bots means implementing tools and techniques at different layers in your tech stack. Here are some key strategies that will help you safeguard your websites and applications.
Use bot detection and monitoring tools. Specialized tools analyze behavior patterns, which helps to distinguish between legitimate users and automated threats from bots (Figure 3).
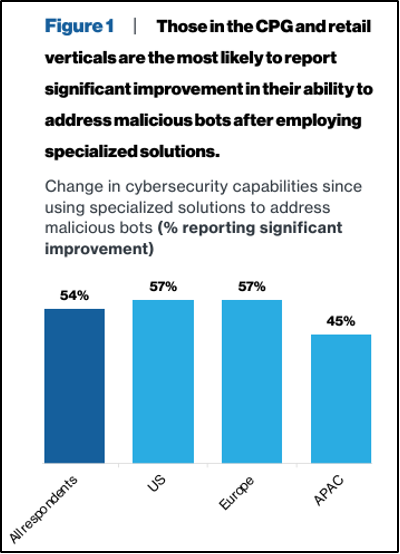
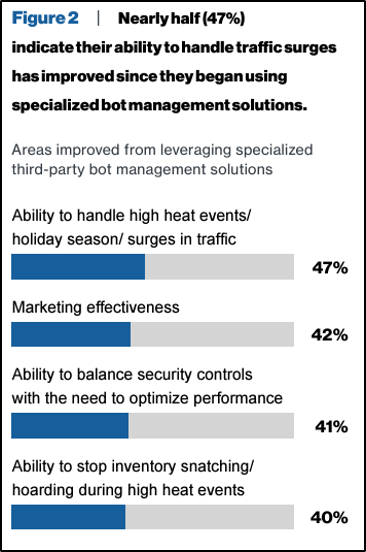
Fig. 3: Bot detection and monitoring tools analyze behavior patterns
Implement challenges. Challenges are mini puzzle-like tasks that help determine if the request is coming from a bot or a human. In some cases, like CAPTCHA, a user must complete a task to prove that they are human. In other challenges, like a cryptographic challenge, a bot must solve a mathematical puzzle in a predefined amount of time, causing the bot operator to slow down and spend more money to attack a site. Challenges are most often used when a request has some characteristics of bot behavior and some characteristics of human behavior — and the company does not want to block the request automatically.
- Enforce rate limiting. Limit how many requests can be made to your site from the same IP address within a certain timeframe. This will reduce the impact of bot activity by slowing down or blocking suspicious traffic.
- Use web application firewalls. A web application firewall (WAF) filters out malicious traffic, including bots, by analyzing incoming requests and blocking those that exhibit harmful patterns.
- Keep an IP denylist. Add known malicious IP addresses to a denylist; this can help prevent some bad bots from accessing your site.
- Block excessive logins. Head off brute-force attacks by monitoring for failed login attempts and blocking excessive failed attempts with a temporary account lockdown.
Akamai bot management and bot protection
Bot attacks are a growing threat that businesses must take seriously. In this blog post, we’ve covered six of the most common bad bots so that you can more easily spot attacks on your site. Knowing which bot threats are coming your way and using the right bot mitigation tools can make all the difference in protecting your online assets.
Akamai’s bot and abuse protection solutions provide businesses with powerful defenses against bad bots while ensuring good bots can still operate. Akamai uses AI-powered behavior analysis and machine learning algorithms for bot detection. With features like real-time, detailed reporting and sophisticated threat intelligence (Figure 4), Akamai helps businesses gain visibility into bot traffic and mitigate threats effectively — without sacrificing website performance.
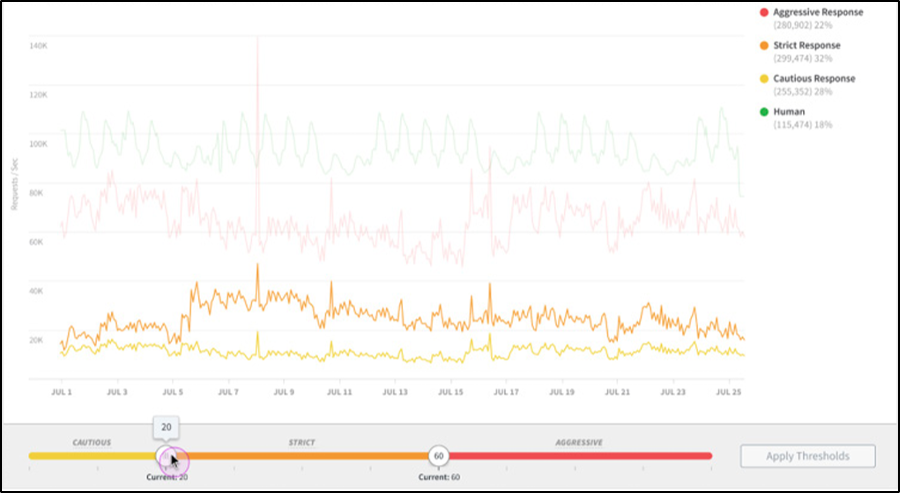
Fig. 4: Akamai’s real-time, detailed reporting and sophisticated threat intelligence provides visibility into bot traffic.
With this bot management solution, your business can balance bot security with site performance and user experience (Figure 5).
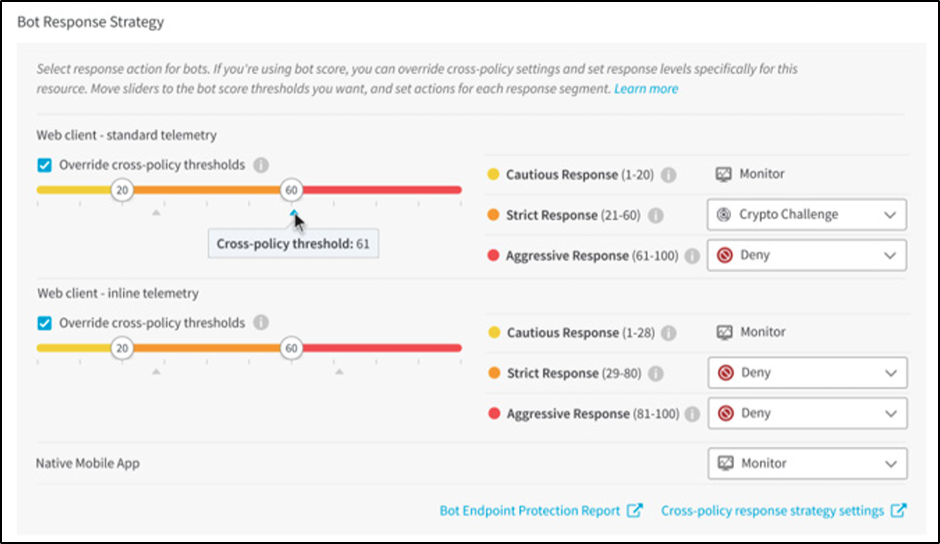
Fig. 5: Akamai’s bot management solution mitigate threats without sacrificing website performance
Learn more
To learn more, check out the following additional resources:
- From Bad Bots to Malicious Scripts: The Effectiveness of Specialized Defenses (report)
- The Evolution of Bots (on-demand webinar)


