5 Steps to Make Zero Trust Achievable
The Zero Trust architecture has long been the Holy Grail of cybersecurity, promising unparalleled protection against evolving threats. However, the complexity of modern IT environments often makes this goal seem out of reach. This is why the Akamai Guardicore Platform was designed to make Zero Trust achievable even for businesses with the most diverse and complex infrastructures.
Implementing Zero Trust may seem daunting, but there are five key steps that can make it achievable:
Start with best-in-class microsegmentation and Zero Trust Network Access (ZTNA)
Leverage a single console for visibility and control
Consolidate your infrastructure for streamlined deployment and maintenance
Leverage artificial intelligence (AI) for enhanced efficiency
Help ensure a system that meets your principles
Start with best-in-class microsegmentation and ZTNA
In a 2023 report, Gartner suggested “implementing microsegmentation and/or ZTNA to move toward a Zero Trust Networking (ZTN) posture.” 1 Let’s explore why these technologies are the foundation of Zero Trust, and why they must be best in class.
By default, IT systems trust far more traffic and allow more access than required to do their jobs. Fundamentally, Zero Trust is about understanding what access and traffic is required and blocking everything else.
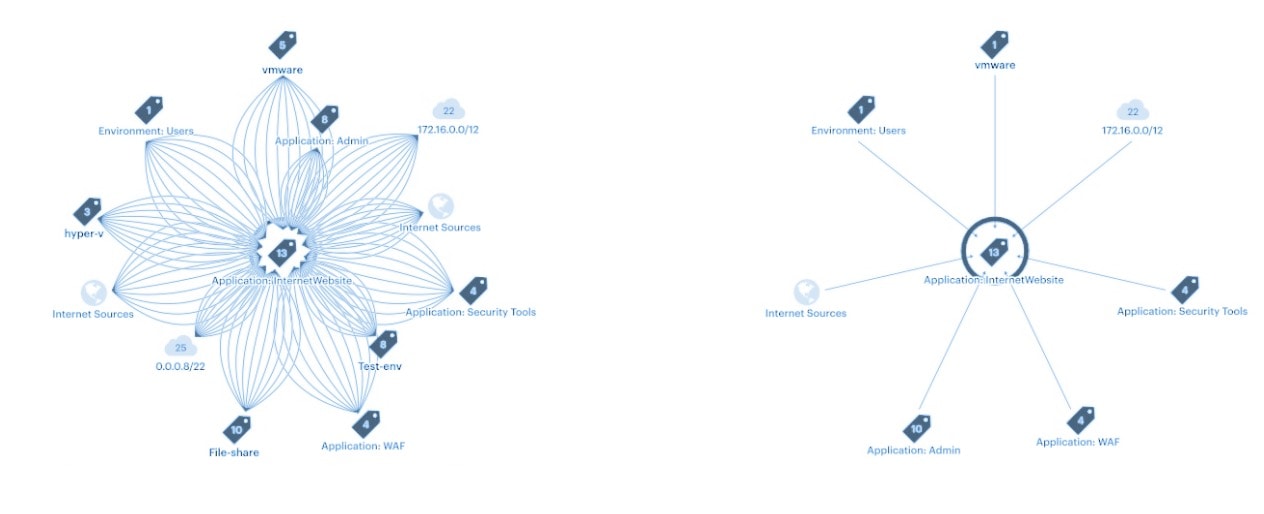
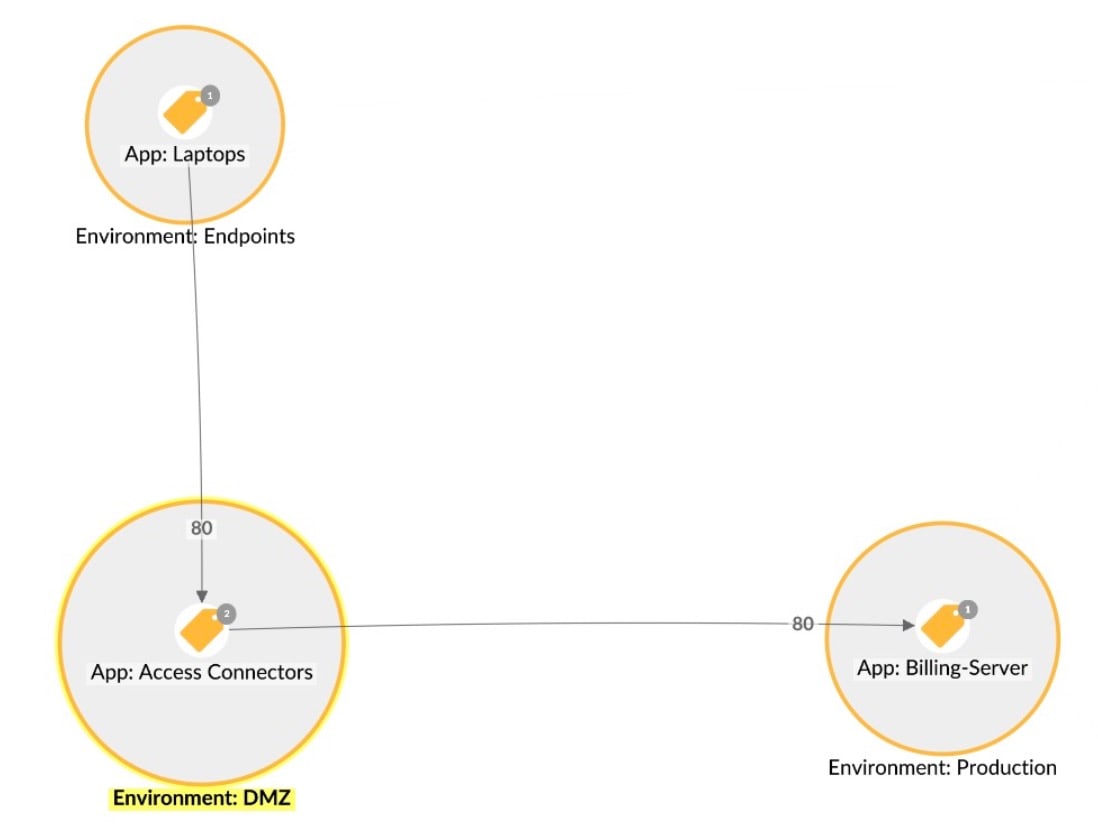
For internal (east-west) traffic, microsegmentation is the only tool that can offer that understanding and control with enough granularity for Zero Trust to be achievable (Figure 1). Guardicore Segmentation is a highly granular microsegmentation solution, allowing businesses to block not just at the port and process levels, but even down to the service level. The result is up to a 99.93% reduction in attack surface.
But achieving Zero Trust doesn’t end with solving the east-west traffic problem. You need to also make sure that your workforce can only access the applications they need to do their jobs. This is a challenging task when employees work remotely and in offices scattered around the world.
This is where ZTNA comes into play, granting precise access for users around the globe, no matter where they are, and no matter where the application resides. Akamai Guardicore Access is especially well-suited for this challenge because it has built-in FIDO2, phish-proof multi-factor authentication (MFA) that makes granting this access secure and seamless for employees.
So, both microsegmentation and ZTNA are required to achieve Zero Trust. But until now, if you wanted the best of both, they had to be deployed and managed separately. This is no longer the case, as the Akamai Guardicore Platform combines best-in-class microsegmentation with ZTNA, providing organizations with a robust framework to start their Zero Trust journey on the right foot.
Leverage a single console for visibility and control
Zero Trust will remain out of reach if you keep trying to manage disparate security tools and policies to achieve Zero Trust. A unified view of your entire network through a single console is paramount. This means seamless management of both north-south and east-west traffic, with policies enforced consistently across on-premises and cloud assets, as well as for both remote and in-office workforces.
You need to see your north-south access and east-west traffic patterns in one place to build and maintain Zero Trust policy quickly and effectively. Switching between consoles and having a map that only sees part of the picture is untenable. With everything in one map, policy requirements become clear.
Additionally, these products benefit from sharing signals. For example, when microsegmentation is aware that ZTNA is attempting to grant access, false positives can be reduced. The Akamai Guardicore Platform is designed so that access is allowed and not blocked by a microsegmentation rule. Visibility and control of east-west traffic and north-south access must be combined if real progress is to be made in the pursuit of Zero Trust.
Consolidate your infrastructure for streamlined deployment and maintenance
Your business can simplify deployment and management with a single agent solution to expedite and simplify Zero Trust objectives. Businesses need this to support broad and varied fleets of assets that include legacy and modern operating systems, on-prem and cloud applications, Internet of Things (IoT) devices, containers, and more.
Traditionally, supporting all Zero Trust efforts across all these systems requires several agents, which are a nightmare to deploy and maintain. Not to mention the negative impact they can make on the performance and reliability of protected devices.
The Akamai Guardicore Platform has a single agent that supports microsegmentation, ZTNA, DNS firewall, and more. This will reduce the impact on end users and workloads, reduce strain on deployment teams, and streamline maintenance for all components of Zero Trust.
The Akamai Guardicore Platform enables quick and effective deployment of Zero Trust across your infrastructure with minimal impact on system performance and downtime. When agents aren’t viable, the platform offers agentless protection.
Leverage AI for enhanced efficiency
Certain Zero Trust–related tasks like scoping a compliance effort, surfacing vulnerabilities, and responding to incidents require too much time and technical understanding for a CISO to quickly complete on their own.
Consider, for example, a CISO who is asked to determine if a specific type of connection was made to a specific set of assets during a specific time frame. This is important information when responding to an incident. In these scenarios, time is of the essence as the CISO can’t choose when these attacks happen.
The CISO’s best analysts might not be available, and even if they are, those analysts have to manually search through logs and correlate information to answer the question. This is where AI needs to be harnessed. This CISO needs to get an answer by simply asking, “Was there any SSH or RDP traffic to my production environment in the last 24 hours?”
The Akamai Guardicore Platform leverages AI for tasks like natural language communication with network logs, labeling asset inventory, queries for simplified vulnerability assessments, and policy recommendations. This enables faster incident response, compliance efforts, and overall security operations.
Help ensure a system that meets your principles
Zero Trust demands adherence to its core principles: treating entities as untrusted by default, enforcing least-privilege access, and maintaining comprehensive security monitoring. The Akamai Guardicore Platform is designed so that these principles are not just ideals but actionable strategies.
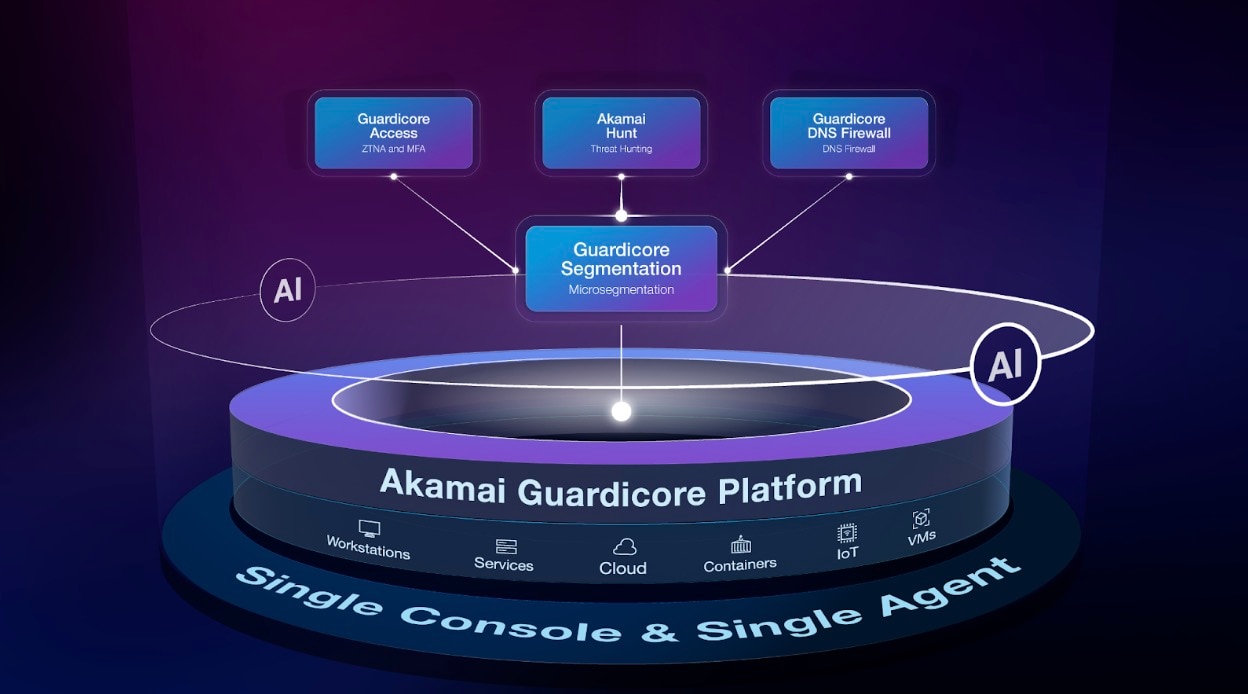
Microsegmentation and ZTNA are a good start, but they’re not the complete solution. With comprehensive security measures, including MFA, DNS firewalls, and advanced threat hunting capabilities, organizations can continue their Zero Trust journey and go beyond building a strong foundation (Figure 3).
Achieve Zero Trust implementation
The Akamai Guardicore Platform offers a practical and effective approach to Zero Trust implementation. By providing best-in-class solutions, unified visibility and control, streamlined deployment, AI-driven efficiency, and adherence to Zero Trust principles, it makes Zero Trust achievable for businesses of all sizes and complexities.
1. Gartner®, Quick Answer: What Is Zero Trust Networking? Andrew Lerner, John Watts, 13 September 2023. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.