Leaking NTLM Credentials Through Windows Themes
Editorial and additional commentary by Tricia Howard
Executive summary
Akamai security researcher Tomer Peled recently discovered a spoofing vulnerability in Microsoft Themes. It was assigned CVE-2024-21320 with a CVSS score of 6.5.
The vulnerability can trigger an authentication coercion — an attack in which a victim is coerced into sending credentials (usually in the form of NTLM hashes over SMB) to an attacker’s machine. The attacker can later crack the credentials offline.
To exploit this vulnerability, the attacker only needs the victim to download a theme file to their computer. When the user views the file in Explorer, the browser will automatically send Server Message Block (SMB) handshake packets that contain credentials to the attacker’s server.
All Windows versions are affected, as Themes is a built-in feature in the Windows operating system.
Microsoft fixed this vulnerability in January’s Patch Tuesday 2024.
We provide a proof-of-concept (PoC) Theme file, as well as a PoC video, and present several ways to mitigate this vulnerability.
Introduction
Since the days of Windows XP, Microsoft has provided several previsual personalization options out of the box — colors, fonts, and cursors, to name a few. This personalization is easy for users to do. They can view the installed themes simply by right-clicking on the desktop, selecting “personalize,” and clicking on “Themes.” Theme files have the suffix .theme and they can be created using this overview from MSDN.
This seemingly innocuous nicety can provide a home for some sneaky vulnerabilities. In our analysis of September’s Patch Tuesday 2023, we briefly discussed the impact of CVE-2023-38146, a vulnerability within Themes. While analyzing the vulnerability, we decided to “play” with the values in a Theme file, and discovered there is a lack of validation in certain parameters.
By abusing this lack of validation, we can perform an attack with effectively zero user interaction: All the users must do is download a malicious Themes file. Once the user views the file in Explorer, the exploit begins.
We have documented what you need to know about this vulnerability, including mitigations and a PoC. Read on.
How it works
The Theme file format consists of several blocks of parameters. In this post, we will discuss two parameters: the BrandImage parameter inside the [theme] block (Figure 1) and the Wallpaper parameter (Figure 2) inside the [Control Panel\Desktop] block.
Every file in Windows has a thumbnail that is supposed to correspond to its function. The thumbnail can be anything from the product’s logo to a depiction of its use (as with Calculator, for example). Theme file thumbnails are composed of three parts: a wallpaper (the black square), an MSstyle file (the purple square), and the brand image (the Infection Monkey image; Figure 3).
These components are written inside the Theme file in three different parameters — BrandImage, Wallpaper and VisualStyle. All of them can be remote paths that point at UNC endpoints.
How it’s exploited
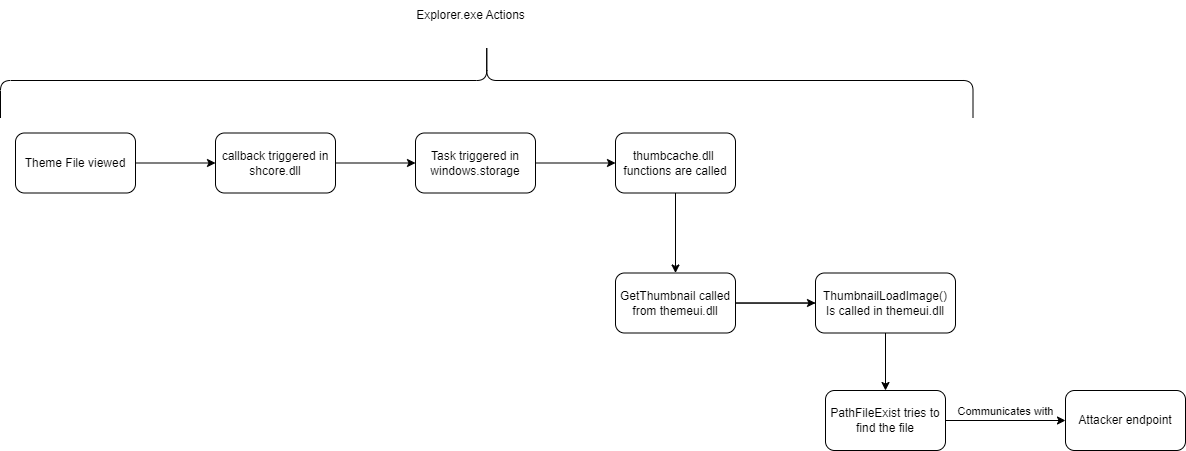
When a Theme file is created or viewed, Windows will try to create the right thumbnail for it from its three components. This thumbnail creation process will start automatically inside the Explorer process. Figure 4 outlines the code flow for thumbnail creation of a Theme file.
Since these actions start automatically, it's a great place for attackers to look for ways to manipulate the outcome. One of the ways attackers can do this is by changing the value of each of these three parameters to a UNC path pointing at an attacker-controlled server, hoping the victim's machine will try to authenticate against their machine.
We found that the path for the image can be any legitimate path, including a UNC path. Changing the values of “BrandImage” or “Wallpaper” yielded a connection from the victim's machine leading to an authentication coercion attack. Namely, as part of the connection to the remote server, the client performs an SMB negotiation during which their NTLM credentials are sent.
The consequences of an NTLM leak
With a victim’s NTLM credentials, an attacker can perform an NTLM relay attack — an attack on systems that accept NTLM as access credentials. By relaying the NTLM hashes, an attacker could authenticate as a legitimate user and thus gain access to systems they otherwise would not have access to.
Another option is to supply the NTLM credentials as input to a password-cracking application, such as John the Ripper, to try and crack the victim’s password using brute force.
An example of how great the impact can be is the infamous Outlook vulnerability, which was initially disclosed to Microsoft in March 2023. A similar outcome was found and it has been actively exploited in the wild, proving that this vector of attack is still relevant and lucrative for attackers.
The vulnerability from March allowed an attacker to send an email to the victim and trigger an audio file download. The path to that audio file could point anywhere, including to a remote server (using a UNC path). Akamai researcher Ben Barnea wrote extensively about this vulnerability and how he found multiple bypasses to the patch for it.
What was patched
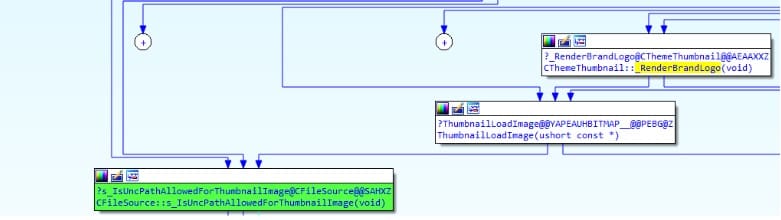
In their patch, Microsoft added a call to a function that checks whether the input is a UNC path (“PathIsUNC”), and a registry value to check whether UNC paths are allowed for Theme file use (Figure 6). If the path is a UNC path and UNC paths are not allowed, then the thumbnail will not be loaded. If they are allowed, the thumbnail will be created with the BrandImage and Wallpaper.
The value “DisableThumbnailOnNetworkFolder” can be found in the registry location: “HKCU/Software/Microsoft/Windows/CurrentVersion/Policies/Explorer/Mitigation”.The value is checked in the newly added function “IsUNCPathAllowedForThumbnailImage()” inside the library themeui.dll.
In their FAQ section for this vulnerability Microsoft wrote: “... and then convince the user to manipulate the specially crafted file, but not necessarily click or open the malicious file.” This looks to be incorrect based on our research. As we’ve explained, no modification of the file content is required; viewing it alone will trigger the credential sending.
Mitigation
On Windows 11, it is possible to block the use of NTLM authentication in SMB with remote machines via Group Policies. To do so, administrators should edit Administrative Templates > Network > Lanman Workstation > Block NTLM.
Microsoft suggested using another policy named “Restrict NTLM” that will help mitigate this vulnerability. The policy can be activated by using Microsoft’s manual.
Using microsegmentation, network administrators can block SMB traffic to remote locations outside the network. Such connections are not usually expected to take place, as SMB is mostly used for communication with Domain Controllers and file servers. See our comprehensive blog post on microsegmentation for further elaboration on segmenting SMB traffic.
Conclusion
Authentication coercion attacks are well known and used extensively by attackers for lateral movement and credential stuffing. For example, a few years ago, the group called Dragonfly used modified LNK files to obtain credentials over SMB. Triggering this kind of attack using Theme files is a surprising new vector.
This vulnerability stresses the importance of an anti-phishing protocol inside organizations, as attackers can easily send a benign-looking file that will initiate this attack.
We are happy to see Microsoft attempting to mitigate this attack vector with the addition of relevant group policies. We advise defenders to update their endpoints with the latest security patch.
Disclosure timeline
09/20/2023 — Vulnerability disclosed to the Microsoft Security Response Center (MSRC)
10/01/2023 — More Information sent to MSRC
10/18/2023 — MSRC accepted that this requires patching
01/09/2024 — Microsoft releases a patch for these vulnerabilities
03/06/2024 — Akamai blog post published



![In this post, we will discuss two parameters: the BrandImage parameter inside the [theme] block (Figure 1) and the Wallpaper parameter (Figure 2) inside the [Control Panel\Desktop] block.](/site/en/images/blog/2024/leaking-ntlm-credentials-through-windows-themes-one.jpg)
![In this post, we will discuss two parameters: the BrandImage parameter inside the [theme] block (Figure 1) and the Wallpaper parameter (Figure 2) inside the [Control Panel\Desktop] block.](/site/en/images/blog/2024/leaking-ntlm-credentials-through-windows-themes-two.jpg)