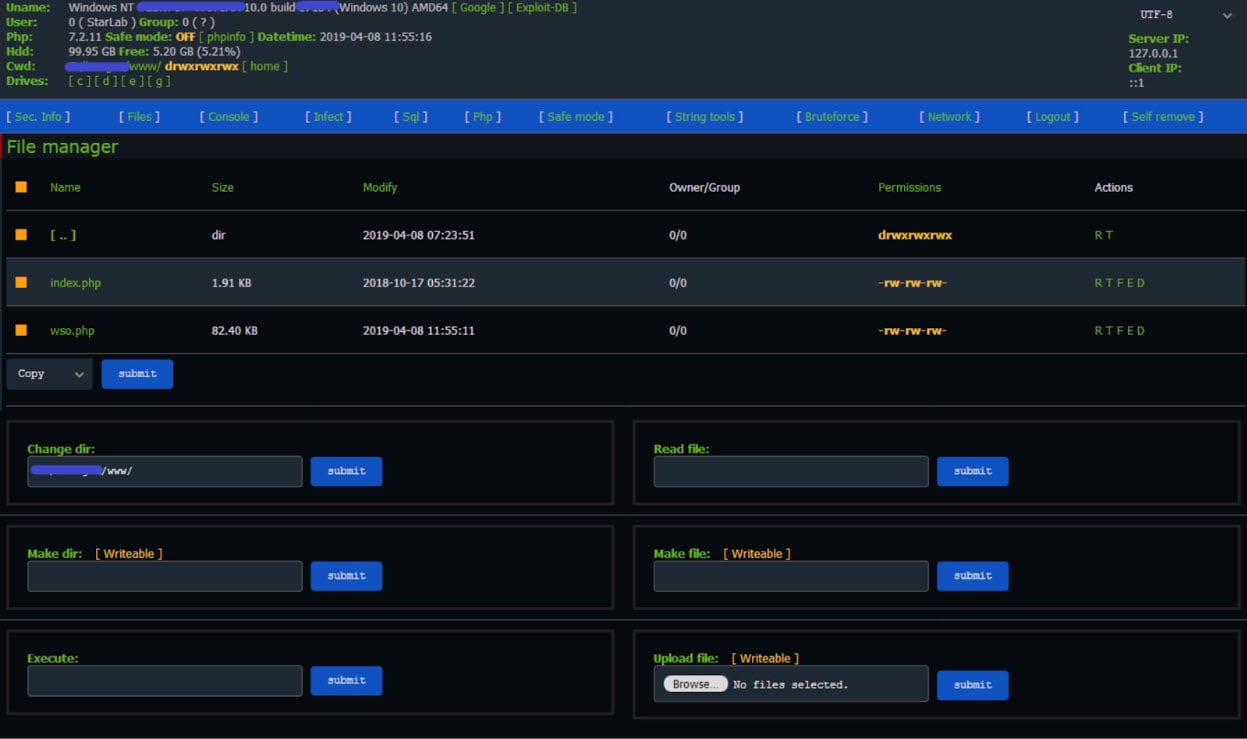
Defeat Web Shell WSO-NG

Web administrators and security professionals are becoming increasingly wary of web shells, as these malicious scripts provide attackers the ability to remotely control compromised web servers.
In this blog post, we will discuss the web shell called WSO-NG. This post is the first in a series that will shed more light on the world of web shells.
What is a web shell?
Before we get into the details of WSO-NG, let's take a quick look at what web shells entail. A web shell is a script, commonly written in a web-supported language like PHP, ASP, or JSP, that provides remote control over a compromised server. Once uploaded, attackers gain the ability to carry out a range of malicious activities, including data theft, server monitoring, and lateral advancement within the network.
According to MITRE ATT&CK, deploying a web shell is a tactic used by attackers to establish a lasting foothold on the victim's system.
A Short History of WSO
WSO, short for "web shell by oRb," is a well-established web shell that has been present for a minimum of 14 years. Its inception can be traced back to its introduction by a user named "oRb" on a Russian hacking forum (Figure 1).
WSO provides an extensive range of web shell functionalities, streamlining the process for hackers to collect information from a target server, efficiently handle files, gaining unauthorized access to databases, and executing shell commands.
Over time, the initial developer of WSO, along with collaborators, consistently delivered improvements to features and addressed bugs (Figure 2).
In 2021, a GitHub user with the name "0xbadad" revealed an updated iteration of the WSO shell. Initially called "step.php," its name was subsequently changed to "wso-ng.php," which, according to the creator, represented the fact that it is the "New generation of famous WSO web shell."
WSO-NG: The new generation
A potential foe who selects a web shell for overseeing a server has a variety of powerful options, including China Chopper, B374K, R57, and others. One of the noteworthy choices is WSO and its advanced iteration, WSO-NG (Figure 3). WSO-NG provides cyberattackers with the contemporary tools that are essential for navigating today's security-aware digital environment.
 Fig. 3: WSO-NG, the new generation of WSO (Source: https://github.com/aels/wso-ng)
Fig. 3: WSO-NG, the new generation of WSO (Source: https://github.com/aels/wso-ng)
Concealing the login page
To boost the stealth capabilities of WSO-NG and limit access, the web shell displays a 404 error page when users try to access its login interface.
However, beneath this illusion of an "error" page, the web shell covertly anticipates the password being input through the keyboard. The hidden login form employs a cunning CSS technique to conceal it from the user, achieved by displacing it 1,000 pixels to the left. This manipulation effectively situates the form beyond the visible screen area (Figure 4).
 Fig. 4: The blank WSO-NG login page has hidden functionality
Fig. 4: The blank WSO-NG login page has hidden functionality
Gathering threat intelligence via third parties
After gaining access through the concealed login form, the attacker's next step is likely to involve reconnaissance of the compromised environment. Using WSO-NG, the attacker can gather intelligence on the threats that are affecting the system, employing tactics and tools similar to those used by organizations that defend against cyberthreats.
WSO-NG seamlessly integrates with a threat intelligence service called VirusTotal, enabling the analysis of the compromised server's IP reputation to determine if it has been flagged for malicious activities. If the attacker plans to use this server for additional online exploits, this integration becomes crucial in evaluating the likelihood that the exploit will be blocked by potential targets, especially if the IP is already listed in their denial records (Figure 5).
Another essential aspect is that this feature can uncover whether the server has experienced previous compromises by other threat actors, which will prompt the attacker to proceed with caution.
Moreover, WSO-NG's integration with the SecurityTrails service aids attackers in identifying additional hosted domains via the compromised server, contributing to further target profiling.
 Fig. 5: Example of threat intelligence information on the server IP (Source: https://github.com/aels/wso-ng)
Fig. 5: Example of threat intelligence information on the server IP (Source: https://github.com/aels/wso-ng)
Adapting to modern environments
As cloud environments and modern technologies become more widely embraced, new methods for storing and accessing crucial technical information and operational secrets have surfaced.
A noteworthy reconnaissance feature of the web shell involves retrieving AWS metadata. This serves as a prevalent method for attempting to acquire AWS credentials associated with the active cloud instance, which could facilitate subsequent lateral movement within the cloud account.
Another reconnaissance capability offered by the web shell is the ability to search for potential Redis database connections, with the aim of obtaining more extensive access to application data. Redis, an in-memory key-value database, is widely used in contemporary applications, particularly in cloud settings.
Enhanced offensiveness
WSO-NG is a top-tier web shell; therefore, it is inherently equipped with extensive offensive capabilities right from the outset.
In the typical shared web hosting environment offered by many hosting providers, precautions are implemented to prevent website owners from accessing other sites on the same server and from escalating privileges. Hosting providers employ various mechanisms, such as restricting the use of risky PHP functions like direct shell command execution through the PHP add-filter functionality.
WSO-NG incorporates a built-in exploit specifically designed to circumvent these security measures. Additionally, it capitalizes on a pre-existing exploit for executing arbitrary code in FastCGI environments, a prevalent configuration in web hosting. This enables it to escalate privileges and establish a foothold at the "root" level.
User experience improvements
Finally, WSO-NG doesn't overlook enhancements in user experience, allowing the attacker to efficiently pursue their objectives.
The web shell introduces numerous user interface improvements, including a new breadcrumb navigation panel, keyboard shortcuts, syntax highlighting, tidy PHP code editing (Figure 6), swift copy to clipboard with a simple click, and more.
 Fig. 6: Neat PHP code editing
Fig. 6: Neat PHP code editing
Defeating WSO-NG
To deploy a web shell on a victim's server, an initial access method is necessary; that method typically involves the exploitation of a web vulnerability. To prevent this initial server access, security practitioners are advised to stay updated with the latest patches. However, as businesses struggle to keep up with patches and security measures, web shells might be also defeated by advanced web application firewalls (WAFs), such as Akamai App & API Protector.
Leveraging its Adaptive Security Engine, Akamai's WAF can pinpoint initial web vulnerability exploitation attempts that could potentially pave the way for the deployment of a web shell for sustained access. Additionally, it can detect an attacker's efforts to upload a web shell to the target server using the command injection attack group (Figure 7).
Specifically, WSO-NG might be detected by the following Adaptive Security Engine rule:
3000171 — Webshell/Backdoor File Upload Attempt
 Fig. 7: Adaptive Security Engine detection of WSO-NG upload attempt
Fig. 7: Adaptive Security Engine detection of WSO-NG upload attempt
Conclusion
In the dynamic world of digital advancements, web shells like WSO-NG emerge as powerful instruments when wielded by adversaries. Given the broad range of capabilities these malicious scripts provide to attackers, they've become a significant worry for both security experts and web administrators. Our thorough exploration of the origins and advanced features of WSO-NG highlights its potential as a threat in today's era, when cybersecurity awareness is on the rise.
The good news :As the threat grows, so do our defenses. App & API Protector, Akamai’s WAF, emerges as a powerful bulwark against such insidious scripts, safeguarding the digital realms we rely on.
We can counteract the threats posed by advanced web shells by consistently updating patches, leveraging innovative security tools like App & API Protector, and maintaining a proactive security stance — and ensure a more secure web environment for all users.