It’s Getting Hot in Here: EMEA SOTI
Introduction
Akamai researchers have released another State of the Internet (SOTI) report, and this time it’s zeroed in on the unique cyber challenges that affect the Europe, Middle East, and Africa (EMEA) region. The report deep dives into the volatile cyber landscape in the region, focusing on distributed denial-of-service (DDoS) attacks and their devastating effects on the victims.
It’s stellar work. But don’t take my word for it — give the whole thing a read. You'll learn some new things, and in an industry that changes as quickly as cybersecurity changes, continuous education is paramount.
Don’t have time to read it all right now? I’ll pretend not to take it personally and instead provide you with a list of what you can expect when you do read it (which you will, right? 🥺).
🗺️ Comparisons of EMEA-specific DDoS trends with the trends in other geographies
⚖️ Regulatory guidance for upcoming cyber laws
⚔️ A case study of a real European ecommerce company that was hit by a major DDoS attack
🦺 Safeguarding and mitigation tips
I bet I have your attention now. Keep reading. You’ll be thirsty to download the report by the end of this blog.
Geopolitical tensions affect security outcomes
The more digital the world gets, the more real-life things can make their way into the cyber realm, which sadly includes warfare. The Russia-Ukraine war and the Israel-Hamas war have created a frenzy of malicious online activity on all sides, including hacktivism, “hacking back,” and, of course, good old-fashioned nation-state cyber warfare.
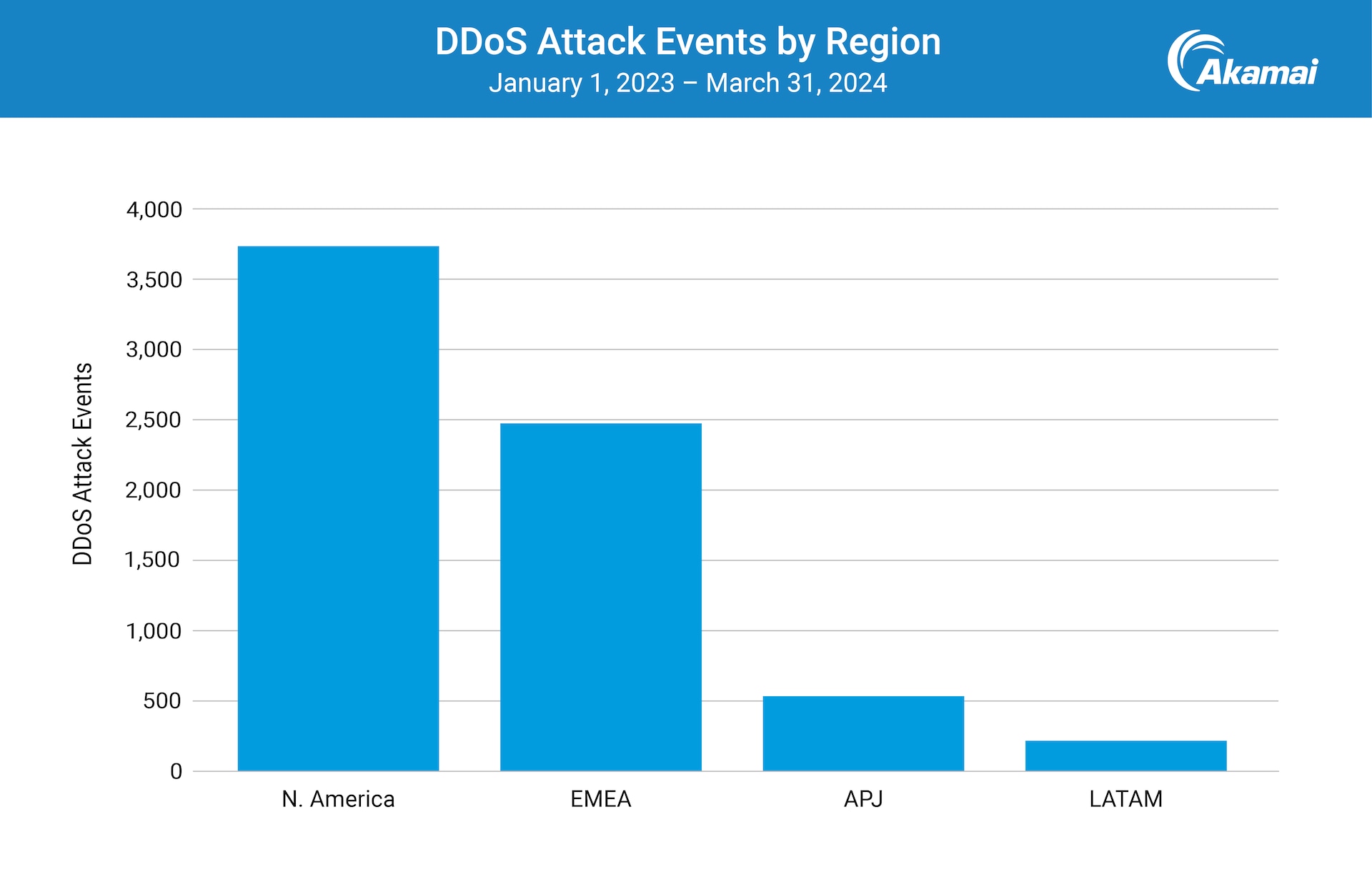
Considering that both of these wars are happening in EMEA, it makes a lot of sense that this region would see increasing amounts of DDoS attacks, which seem to be the favored tools for hacktivists and are rapidly becoming the favorite tools of nation-state threat actors, too. And EMEA is seeing these types of attacks a lot — like, a lot a lot (Figure 1).
Although North America continues to wear the crown for most DDoS attacks, the precipitous increase in volume in EMEA is disconcerting to say the least. The attack count climbed to nearly 2,500 from the beginning of 2023 to the first quarter of 2024 alone — more than three times as many as in the Asia-Pacific and Japan (APJ) and Latin America (LATAM) regions combined.
All rise for new legislation
A very large consideration for organizations in EMEA is the new legislation landscape. The General Data Protection Regulation (GDPR), with its focus on privacy, was just the beginning. Now, we’re also moving into infosecurity with the new Network and Information Systems (NIS2) Directive and Digital Operational Resilience Act (DORA) among others. Both of these laws give solid guidance on how to stay more secure and resilient. (Pssst! It’s Zero Trust.)
If you’re someone who enjoys reading legislation, read your little heart out! If you are not one of those people, but still need to know what’s in them, and how the new regulations will affect your industry, just read the SOTI report. Our team has read and distilled the new compliance regulations for you already. You’re welcome.
Money doesn’t just talk; it curses
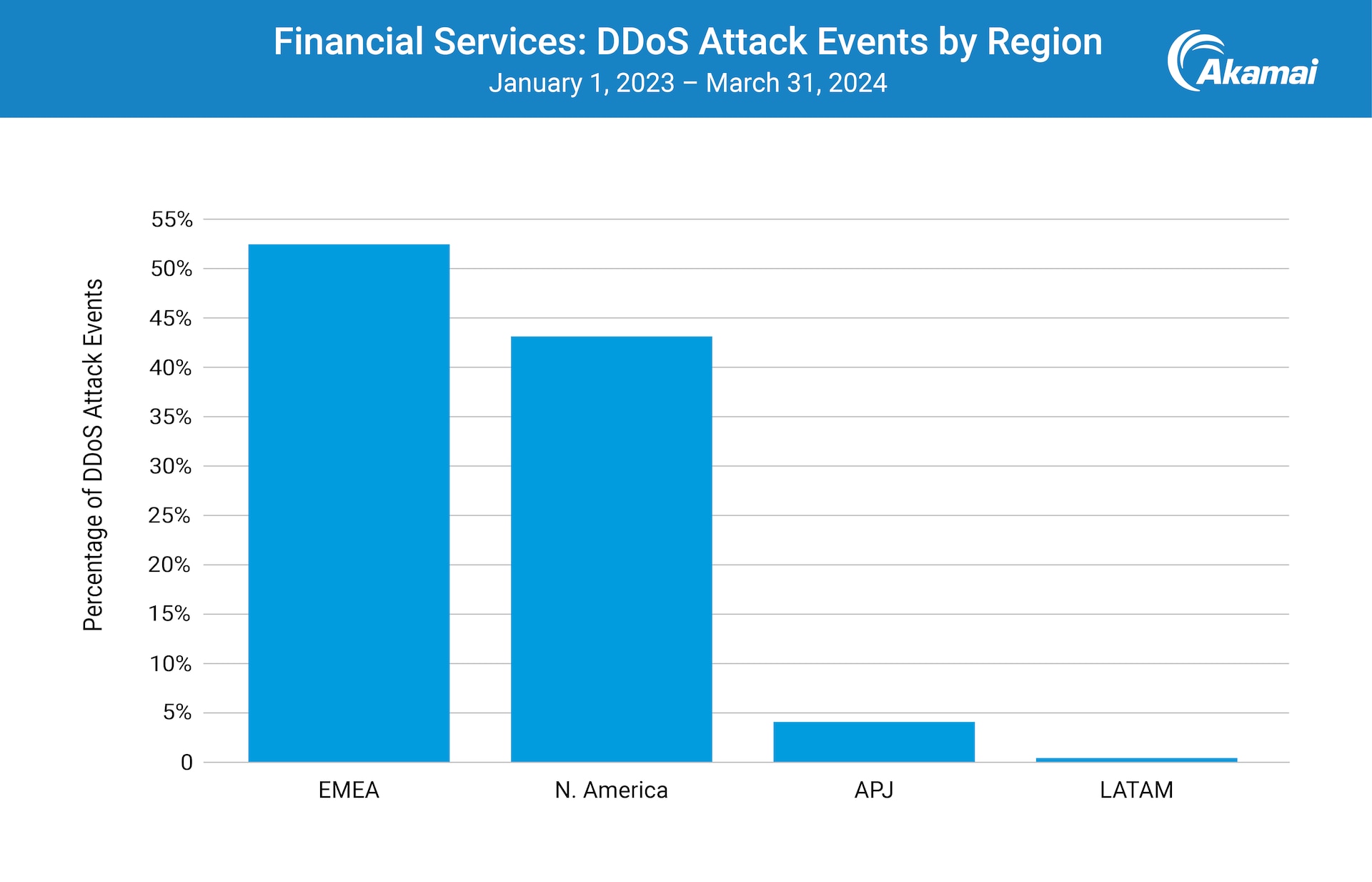
When it comes to industries, the finance sector is more affected by DDoS attacks in EMEA than in any other region. EMEA led the pack for Layer 3 and Layer 4 attack event traffic in financial services, with more than half the attacks that took place globally (Figure 2).
Despite Europe making up only 1.2% of Earth’s surface, 52.5% of Layer 3 and Layer 4 attack event traffic in the financial services vertical were in EMEA. That’s pretty wild to think about — especially when you consider that only 1 of the top 10 banks globally are in this region, and that one bank (HSBC in London) is sitting at spot #8. For reference, China is home to 4 of the top 10 global banks, and you can see in Figure 2 how low the APJ numbers are.
Layers 3 and 4 aren’t the only seismic cyber activity in the region — Layer 7 also got some fierce attention from attackers, especially when they targeted commerce. If your ecommerce store gets wrecked with traffic and becomes inaccessible, you can lose a lot of money. You may also be so distracted by mitigation efforts that you fail to notice that the attackers are stealing your customers’ data.
New trends, who DNS?
Move over triple extortion, there are new DNS attacks in town. The aptly named DNS Water Torture attacks (You know, because: Flooding? Like an HTTP or UDP Flood?) drowned out other methods during the observed time frame (That’s right: drowned. You see what I did there? 😏). In the full report, there’s a really nifty graph that shows you just how many attack events we saw per vector, with DNS Flood in the first position.
You know how quickly your phone battery gets drained when it’s searching for service? That’s effectively what happens when a system is swamped with requests for nonexistent domains. Except instead of draining a battery, these NXDOMAIN attacks shut down the whole system. It’s a big bad. The impact of an attack on DNS can, to quote the SOTI report, “literally erase a company's presence on the internet.”
While the number of triple extortion attacks did decline, the triple header is still sitting on the DDoS bench, especially in healthcare. Whether it’s a smoke screen to obfuscate other efforts underway (like data theft) or a way to ensure payment by the victim, DDoS certainly gives an attacker their money’s worth.
But wait, there’s more!
The late Billy Mays would have been proud at just how much more there is in the full SOTI report. I just scratched the surface in this post — there are many more surprises waiting for you in the full report.
Here at Akamai research, we are committed to providing the community with powerful research to help fight the constant onslaught of malicious activity. Whether you are a defender, lawmaker, or even a researcher yourself, we try to provide value to all aspects of the security lifecycle. From regional analyses, such as this one, to how the science of sound can aid an attacker — and everything in between — we’ve got you. For the most recent research findings out of Akamai, check out the Akamai Security Intelligence Group on X, (formerly Twitter).
If you’re still reading this: 1. Thank you. 2. I hope you’ve smiled today. 3. Now, go download the report.