Everything You Need to Know About Edge Networks
What is an edge network?
An edge network is a networked architecture containing “edge” devices — such as computers, smartphones, sensors, and routers — that share processing duties and offset some of the work done by main servers. These networks help improve the performance of cloud-connected applications and websites by freeing up central servers for more intensive computational tasks that only they can handle. A “network edge” physically connects these edge networks either to the internet or another private network.
Some important stats to consider include:
Worldwide edge computing market revenue is projected to reach US$317 billion by 2026.
Mobile edge computing market revenue is projected to increase by US$1.6 billion from 2022 to 2026.
By 2025, 75% of enterprise-generated data will be generated and processed outside of traditional centralized data centers and the cloud.
Get the edge answers you need
In this blog post, you’ll get the answers to:
- How do edge networks work?
- How do Internet of Things (IoT) edge networks improve performance?
- How do edge networks differ from edge computing?
- What makes up an edge network?
- What is a secure access service edge (SASE)?
- What are the differences among network edges, cores, and perimeters?
How do edge networks work?
Edge networks distribute processing and computational responsibilities to edge devices from a web or cloud application’s main servers (Figure 1). This ensures that main servers are more consistently available to execute the tasks that edge devices can’t handle. When deployed correctly, edge networks can help organizations improve:
- Data architecture efficiency
- Caching
- Performance
- Digital resource distribution
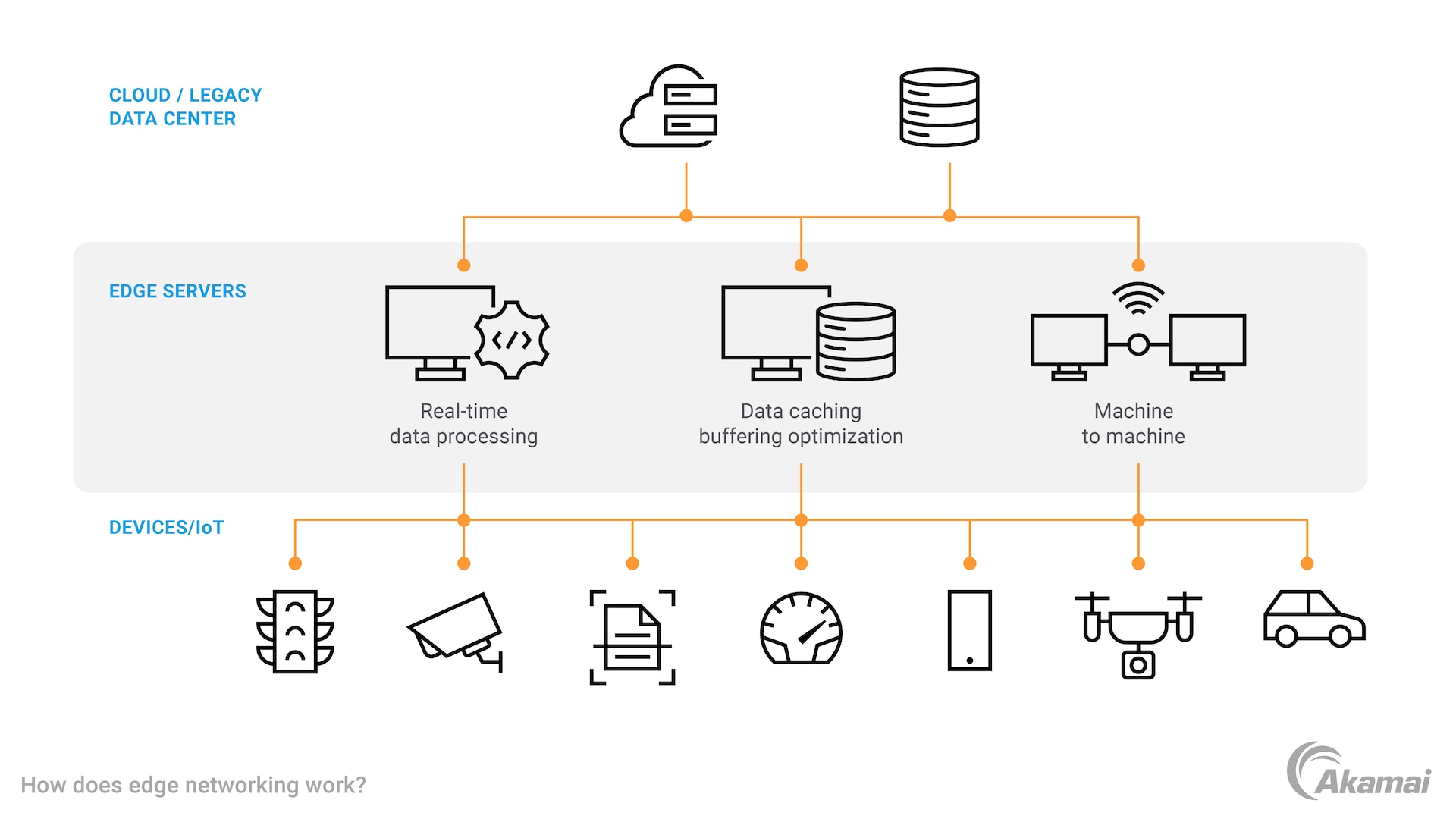 Fig. 1: How edge networking works; the differences among devices, edge servers, and data centers
Fig. 1: How edge networking works; the differences among devices, edge servers, and data centers
Of course, there are many security issues to be aware of when deploying an edge network. These include:
Data storage and protection. Data at the edge doesn’t have the same physical protection as centralized data. Data can be easily compromised when transferred to an edge resource or removed from physical storage — and backing up edge data with restricted local resources can be challenging.
Passwords and authentication. Passwords and authentication for edge devices are often compromised as cyberattackers use sophisticated methods to obtain user credentials.
Data sprawl. As new devices join an edge network, each one adds to the edge’s bandwidth. Once this bandwidth is depleted, security resources may start to malfunction, which can jeopardize your organization’s security.
How do Internet of Things (IoT) edge networks improve performance?
Connected Internet of Things (IoT) devices and software can serve as the bread and butter of your organization’s cloud-based edge network by performing distributed processing duties in place of a central server. For high-throughput network traffic, distributed IoT edge networks can process large volumes of data nearly instantaneously, improving internet-connected application performance to enhance the end-user experience.
Data processed by IoT edge networks can also be quickly transmitted from one IoT device to another, or from an IoT device back to a central server. This can improve overall processing speed in cases where one device’s data calculation process requires data from another device. Rather than halting the calculation process, the device can simply retrieve the relevant data that’s been processed by another IoT device via network transmission. This distributed processing approach resembles software’s use of multithreaded cores to perform multiple calculations at once (Figure 2).
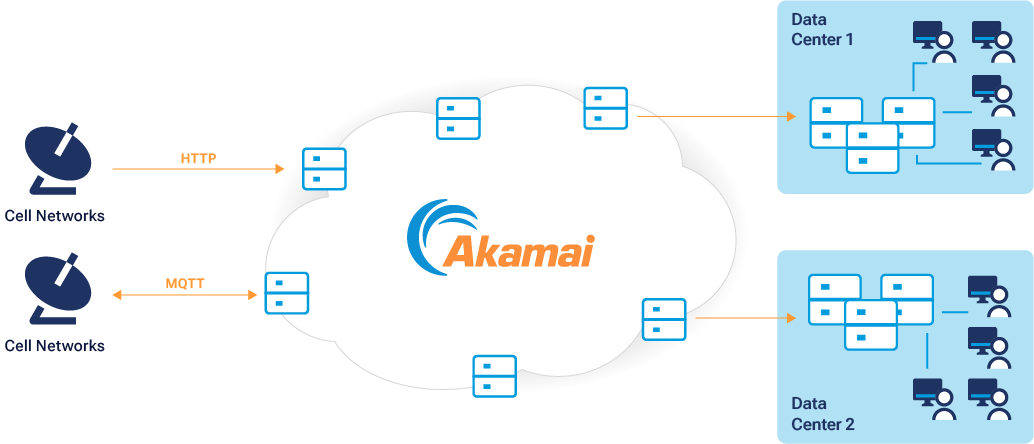 Fig. 2: MQTT, a real-time communication and data processing protocol
Fig. 2: MQTT, a real-time communication and data processing protocol
How do edge networks differ from edge computing?
While edge networks and edge computing both concern distributing resources across multiple locations and the physical location of the edge, they’re two distinct concepts.
In edge computing, computing and storage resources are positioned closer to end users through systems virtualization and cloud-based applications. This helps reduce latency for relevant services since physically closer data can transmit more quickly over shorter physical distances. Through edge computing, users benefit from low-latency services designed to connect them with the nearest edge.
Unlike edge networks, edge computing doesn’t distribute computing processes — rather, it creates more physical computing and storage resource locations in more parts of the world.
Together, edge networks and edge computing can significantly improve performance and benefit end users. Edge computing use cases enable an edge network of IoT-connected devices to perform high-speed data transmissions faster since resources are positioned closer to end users.
What makes up an edge network?
Edge networks are made up of various components that work together to enable faster, more efficient distributed computing use cases. An edge network includes:
Edge devices. These devices live at the network endpoint and interface between data centers and the world.
Edge routers. Located at a network boundary, edge routers transmit data from the internet to devices and enable connections between internal and external networks.
Wide-area networks (WANs). WANs consist of many networks, including local-area networks, that communicate with one another.
Switches. Sometimes called access nodes or service nodes, switches are located where networks meet and connect end user local area networks (LANs) to ISP networks. These can be routers, routing switches, integrated access devices, multiplexers, and metropolitan area network (MAN) or WAN devices.
Edge firewalls. Like normal firewalls, edge firewalls protect organizations’ networks, applications, servers, and content delivery networks (CDNs) from external cyberthreats. However, they exist far away from main servers and CDNs at the network edge, which makes them more capable of protecting main servers and edge devices.
Integrated access devices (IADs). IADs offer WAN and internet access by aggregating multiple information channels, including voice and data, and the utility of multiple networking devices — VoIP gateways, routers, and modems — across a single shared access link.
What is a secure access service edge (SASE)?
Secure access service edge (SASE) is a technology architecture offering combined network and security as a service capabilities, like WAN, as well as cloud-native security functions like secure web gateways, cloud-accessible security brokers, firewall as a service, and Zero Trust Network Access. These are delivered as cloud services by SASE vendors directly to connection sources rather than data centers.
SASEs offer organizations visibility into their overall network environment, from data centers to headquarters. They afford organizations:
Greater control over users, data, and applications
Improved monitoring, reporting, and diagnostics
Streamlined networking and security operations
What are the differences among network edges, cores, and perimeters?
The network edge — comprising edge devices, routers, WANs, switches, firewalls, and IADs — is just one high-level component of its overarching edge network.
Network cores comprise the network components — including WANs and LANs — located at or near the organization. They deliver processing-intensive services to network edge components that could not be efficiently executed at edge locations.
Network perimeters outline the physical boundaries between an organization’s private, locally managed network and the public internet.
Read on for more details on the differences between network edges, cores, and perimeters.
Network edges vs. network cores
Network edges — where edge devices connect to the internet — are located closer to end users and can perform content delivery back to users faster than the network core. However, the network core is still important because it can perform more intensive calculations and data processing tasks, then transmit that information back to the network edges where it can be served to end users.
Network edges vs. network perimeters
The network edge specifies where edge devices connect to the internet, bringing data computation and transmission closer to end users. Meanwhile, the network perimeter is a physical boundary that helps secure enterprise networks by separating an organization’s private network from public networks.
Whereas network edges comprise a firewall, router, or some other security-oriented WAN hardware, network perimeters — which include network routing, switching, security hardware, and security software — are designed to protect networks from malicious activity.
Sophisticated enterprise edge network services from Akamai
By partnering with an experienced edge network provider, enterprises and their users can improve speed and performance.
Akamai Connected Cloud is a state-of-the-art edge solution that offers edge applications, API acceleration, global traffic management, serverless cloud computing and optimization, and more to enrich your existing cloud infrastructure.
Find out more
Get in touch today to chat with one of our experts and learn more about how edge network technology from Akamai can benefit your users, workloads, and operations.


