AI on edge networks is the practice of running artificial intelligence applications at edge locations where computation and analysis can be done close to where data is actually generated. As a result, AI applications are able to produce data and insights faster to help users make more informed decisions.
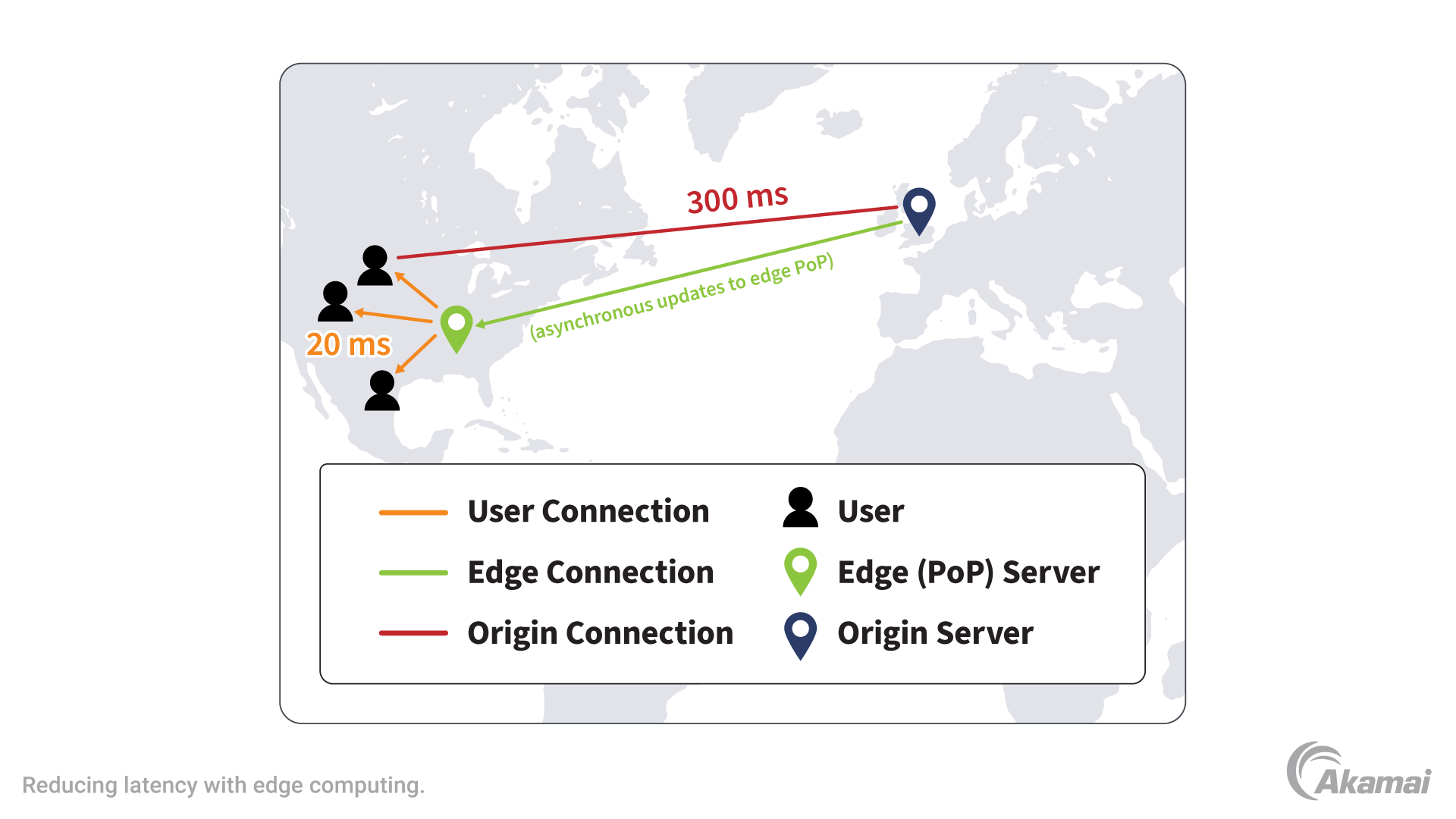
An edge network is a highly distributed computing paradigm where compute primitives are moved to the edge of the network, not in just the handful of typical regions — close to the users and devices that need them. As a result, edge networks can reduce latency, minimize bandwidth needs, reduce costs, improve security, and enhance user or customer experiences.
In an edge network, the resources that provide computer processing, storage, networking, security, and other functions no longer reside in the cloud or in central data centers. Instead, they are physically located at points of presence (PoPs) that are geographically nearer to the users and devices that produce, process, and consume data.
Why are edge networks needed?
Edge networks are a response to the massive growth of data that’s part of digital transformation. In modern computing environments, many applications and use cases are highly data intensive and latency sensitive. Services like streaming media, self-driving vehicles, healthcare devices that monitor patient vitals, smart cities solutions for directing traffic, and IoT devices that control industrial manufacturing processes all require a network that offers high performance, ultra-low latency, and the strongest security. Edge networks make this possible by moving computing functions away from centralized data centers and cloud environments, and allowing these processes to take place at the network’s edge, closer to where data is created and consumed.
What are the elements of an edge network?
Edge networks involve a highly distributed collection of edge servers to decentralize computing and allow processing, storage, networking, and security to happen closer to the end users and devices that need these functions. Edge network infrastructure includes a variety of technologies.
- Specialized branch routers and network edge routers located at the boundary of networks use dynamic or static routing capabilities to move data between internal and external networks.
- Network switches connect devices within a computer network and allow devices to share resources without connecting to devices at the network’s core.
- A wide area network (WAN) connects local area networks (LANs), often through a software-defined WAN (SD-WAN) infrastructure.
- Firewalls inspect and manage data as it enters and exits the network, defending the edge network from a broad range of threats.
- Integrated access devices transform different types of data into a common format to simplify communications and improve the efficiency of transmission at the edge.
What are the benefits of an edge network?
By intelligently and efficiently routing traffic and workloads to nearby resources, edge networks provide a variety of operational benefits.
- Faster speed and reduced latency. By processing and serving data from edge locations, an edge network enables faster response times, speedier transactions, better experiences for users, and more reliable performance for real-time applications.
- Reduced bandwidth costs. By reducing the amount of data sent over the network to cloud servers, organizations can significantly minimize the cost of procuring bandwidth and storing large amounts of data.
- Enhanced security. Edge networks minimize the exposure of sensitive information by processing data closer to where it’s created and consumed, and limiting the transmission of personal data over the internet.
- Increased agility. With hundreds or thousands of edge servers, edge networks can optimize workloads by routing them to optimal locations, around bottlenecks or network connectivity issues, to improve performance, agility, and scalability.
- Improved data sovereignty. Moving data between devices and cloud servers located around the world creates issues with data sovereignty laws in various countries. By allowing data to be processed and stored close to where it’s consumed, organizations can more easily comply with regulations such as the European Union’s GDPR.
What are use cases for an edge network?
Common use cases for edge networks include:
- Healthcare. By processing the massive amounts of data collected from patients on edge servers, medical equipment like Internet of Things (IoT) devices and sensors can provide clinicians with real-time data and analytics that help save lives and improve healthcare outcomes.
- Transportation. Autonomous vehicles produce massive amounts of data that must be processed at the network’s edge in real time to guide vehicles safely and efficiently to their destination.
- Retail. Retail businesses rely on edge networks to manage and analyze large volumes of data from sales, inventory, supply chain tracking, and surveillance.
- Manufacturing. Industrial manufacturers use edge computing to power applications that rely on automation, machine learning, and real-time analytics that make production processes safer and more efficient.
What is an edge network vs. a CDN?
Most edge networks are designed to support real-time needs for ultra-fast data processing or to protect environments by delivering security functions at the edge. A CDN (content delivery network) is a type of edge network that’s designed primarily to cache content and serve it to users from nearby locations, providing higher performance and better user experiences. CDNs typically do not provide the kind of intense data processing functions that other edge networks offer.
What is edge network security?
Protecting an edge network requires multiple layers of security and comprehensive solutions that include:
- A Zero Trust framework. A Zero Trust approach to security requires all users, devices, and applications to be authenticated and validated on every request for access to resources, minimizing the potential for breaches and limiting the scope of any successful cyberattack.
- A web application firewall (WAF). Security teams can rely on a WAF in networking at the edge to protect against a wide range of cyberattacks, including distributed denial-of-service (DDoS) attacks, SQL injection, cross-site scripting, remote file inclusion, and cookie poisoning.
- Data encryption. Encrypting sensitive data processed and stored at the edge minimizes damage when data is inadvertently exposed or maliciously leaked.
- Intrusion detection. Intrusion prevention systems (IPS) and intrusion detection systems (IDS) monitor network traffic, analyze suspicious activity, and alert security teams to potential threats.
- Strong access control. Edge networks rely on superior access controls that strictly limit access to certain users and limit those users’ ability to access various IT assets. Access control solutions should operate with the principle of least privilege, permitting users access only to the resources they need to complete specific tasks at any given moment.
Frequently Asked Questions (FAQ)
Cloud computing relies on centralized virtualization to create a pool of resources, providing cloud services that can be accessed on demand. The servers that comprise cloud environments may reside anywhere in the world. Edge networks position physical servers at the edge of a network to provide processing and storage closer to users to reduce latency, improve security, and enhance performance.
A cloud edge network brings cloud computing resources to the network’s edge, combining the flexibility of on-demand access to virtualized resources with the proximity of edge computing.
Serverless frameworks are a computing paradigm that allow DevOps teams and organizations to build and run code in a development environment without needing to configure, maintain, or upgrade the servers that comprise the underlying infrastructure. Running serverless on edge networks reduces latency and improves the performance of serverless functions.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.