Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
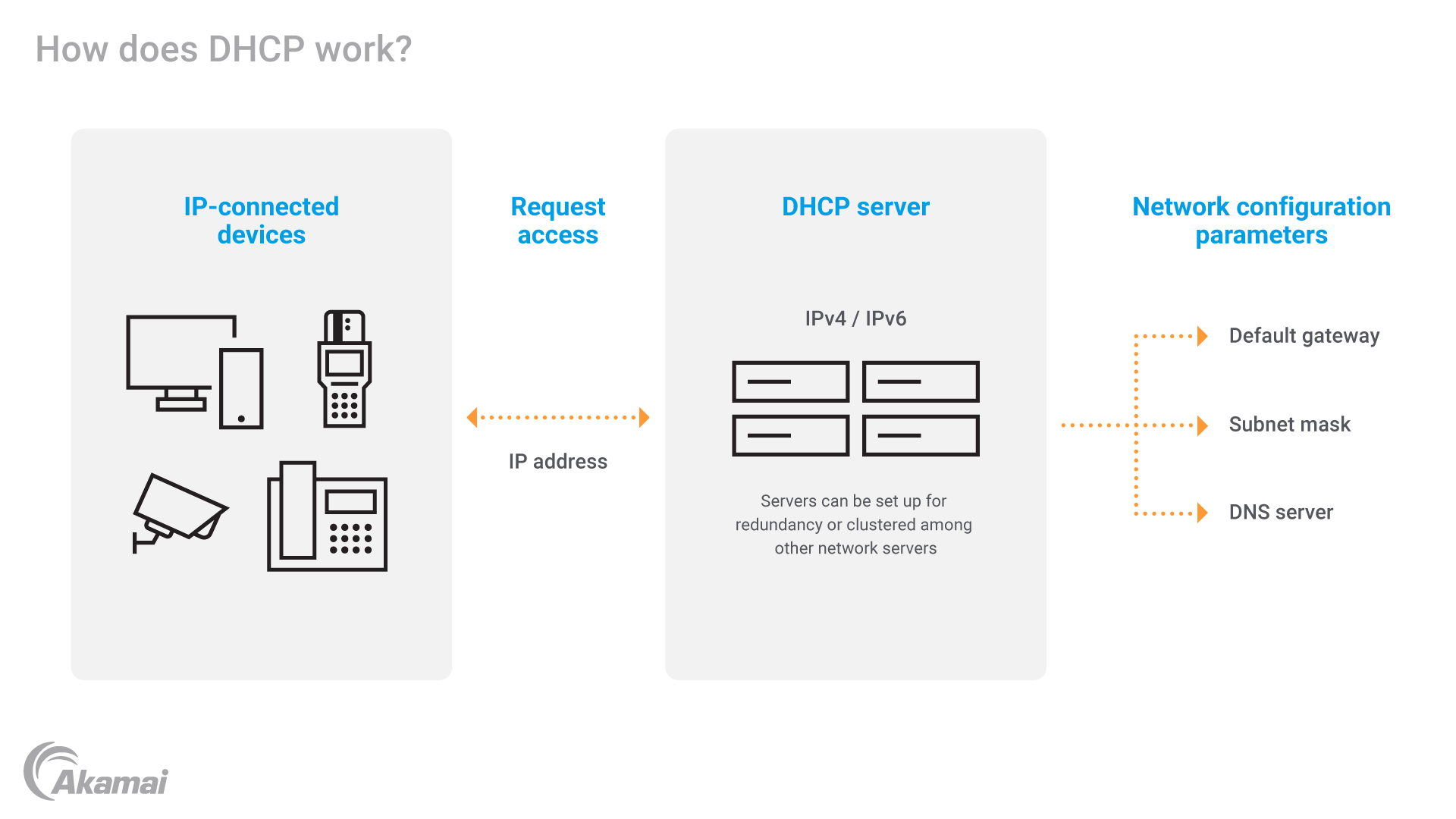
Dynamic Host Configuration Protocol (DHCP) is a system for assigning Internet Protocol (IP) addresses to each network device (known as a host) on an organization’s network. A host may be a desktop computer, a laptop, a tablet, a mobile device, a thin client, or other types of devices. Each host must have an IP address to communicate with other devices over the internet. The DHCP network protocol assigns addresses automatically, rather than requiring network administrators to make manual assignments. DHCP is also responsible for automatically assigning new IP addresses when devices move to new locations on the network. In addition to IP addresses, a DHCP service assigns configuration parameters like Domain Name System (DNS) addresses, subnet masks, and default gateways that are essential to network communications.
How does Dynamic Host Configuration Protocol work?
When a device (also called a DHCP client) joins the network, it broadcasts a “DHCP discover” message to the subnet of the network, requesting an IP address along with other configuration information. When DHCP servers on the network receive the DHCP discover message, they respond with DHCP offers that may include an IP address selected from a pool of IP addresses, along with network parameters and DHCP information like DNS servers , subnet mask, default gateway, and duration of the IP address lease. While a DHCP client may receive multiple responses, it selects just one of the offered IP addresses and sends a return message confirming which offer it is accepting. The DHCP server acknowledges the acceptance with a message that contains the final, confirmed IP configuration details, which the client uses to configure its network interface. With DHCP, most clients are offered a lease for a specific period of time and can renew the lease by requesting an extension from the server. When a client is leaving a network, it sends a DHCP release message that lets the server know the IP address is now free and may be reallocated.
What are the components of the Dynamic Host Configuration Protocol?
DHCP server. DHCP servers automatically assign IP addresses from a pool of available addresses to devices that connect to a network. DHCP servers also provide additional network configuration parameters, including subnet masks, default gateways, and DNS servers.
DHCP client. Clients are devices that connect to a network and receive configuration information from a DHCP server. Clients may be computers, laptops, mobile devices, or any other device that needs a connection.
DHCP relay. DHCP relays enable communication between DHCP clients and servers.
IP address pool. These are the collections of IP addresses available to a DHCP server for allocation to devices.
Subnet. Subnets are smaller portions of an IP network, which are petitioned to simplify network management.
Lease. Leases are the amount of time that the IP address and configuration information received from a DHCP server is valid. When a lease expires, a device may request a renewal from the DHCP server.
DNS servers. DHCP servers can also provide DNS (Domain Name System) server information to DHCP clients, allowing them to resolve domain names for IP addresses.
Default gateway. A default gateway is where packets are directed when a destination is outside a local network.
What are the benefits of Dynamic Host Configuration Protocol?
The DHCP protocol enables organizations and network administrators to:
Streamline network management. DHCP reduces the burden on network administrators by efficiently and automatically handling IP address assignments. DHCP is especially effective for devices that must be updated frequently, such as mobile phones moving between different locations on a wireless network.
Optimize IP addresses. The ability to reuse IP addresses minimizes the total number of addresses required for a network.
Simplify change management. DHCP allows organizations to change IP address schemes from one range of addresses to another without disrupting end users.
Minimize mistakes. DHCP centralizes and automates the management of IP addresses, minimizing the chances of two devices receiving the same address or a device receiving an incorrect address.
What are threats to DHCP?
Dynamic Host Configuration Protocol is susceptible to several significant vulnerabilities.
Rogue DHCP servers. Rogue DHCP servers are unauthorized devices that offer malicious DHCP services to clients, including incorrect or conflicting IP addresses, subnet masks, gateways, or DNS servers. Rogue servers may result in denial of service , network disruption, or inaccurate routing, and they may be involved in machine-in-the-middle attacks.
Machine-in-the-middle attacks. DHCP servers may be susceptible to machine-in-the-middle attacks, where malicious actors intercept and relay messages between two parties.
DHCP starvation. A starvation attack sends a large number of DHCP requests with spoofed MAC addresses to exhaust the available IP address pool. The result is a denial of service, where legitimate network clients may not be able to obtain IP addresses or access the network.
Spoofing. In a DHCP spoofing attack, attackers intercept and modify DHCP messages to alter IP addresses, redirect network traffic, steal sensitive data, or conduct machine-in-the-middle attacks.
Relay attacks. DHCP relay agents are devices that forward DHCP messages between various network segments. In DHCP relay attacks, attackers may bypass security controls of a DHCP server by using a compromised DHCP relay agent to inject malicious DHCP messages or access restricted segments of the network.
Scripting vulnerabilities. DHCP operations can be automated and customized using scripts. When those scripts are not properly written or tested, they may contain errors or backdoors that can compromise the security of DHCP servers.
What are best practices for securing DHCP?
To increase network security, network administrators may adopt a multilayered approach when protecting Dynamic Host Configuration Protocol systems from threats.
Authentication and access control for DHCP servers and clients stops rogue DHCP servers and ensures that only authorized clients can receive IP addresses.
Firewalls can monitor and filter traffic, and secure the DHCP server from unauthorized access or attacks.
Logging enables administrators to monitor the performance of DHCP servers and identify suspicious behavior or anomalies.
Applying patches and updating servers can help prevent attacks that exploit vulnerabilities.
Data encryption mitigates data breaches and prevents eavesdropping.
DHCP snooping filters out rogue DHCP messages.
DNS firewalls block malicious domains or IP addresses.
FAQs
Assigning IP addresses is a critical step in enabling network devices to communicate using the standard Transmission Control Protocol/Internet Protocol (TCP/IP). DHCP makes the process easier and more efficient by automatically assigning IP addresses and reclaiming addresses from devices that have left the network. This reduces the burden on network administrators while improving accuracy of IP address assignments.
With dynamic DHCP, devices lease an IP address for a period of time rather than owning IP addresses permanently. Static IP assignments are permanent and are reserved for devices like web servers and switches.