- Personally identifiable information (PII) is personal data that is unique to an individual. This may include Social Security numbers, email addresses, addresses, and telephone numbers.
- Protected health information (PHI) is the medical records of individuals.
- Sensitive customer data may include credit card numbers, financial transactions, usernames, and passwords.
- Confidential financial data includes financial reports, data concerning financial transactions, and information about bank account numbers.
- Intellectual property includes software, business plans, patents, and trade secrets.
- Account credentials include login information that enables attackers to take over accounts and access critical systems.
Data leak protection, or data loss protection (DLP), is the collection of cybersecurity practices and technologies used to keep sensitive data and valuable business information from being maliciously or inadvertently leaked, lost, corrupted, deleted, or stolen. Data leak protection is an essential part of security programs utilizing a Zero Trust framework. It protects organizations against malicious attacks and accidental leaks, and ensures compliance with data protection and privacy regulations.
Why is data leak protection important?
Whether it’s customer records, business plans, or financial documents, leaked data can have devastating consequences for an organization. In cyberattacks where data is leaked or exposed, organizations may incur substantial fines or legal action. Leaks can also result in significant losses — of revenue, customers, business deals, and reputation, since customers may not want to do business with a company that can’t adequately protect its data. Setbacks incurred from data breaches and leaks may also jeopardize business prospects and competitive opportunities.
Digital transformation makes the task of protecting data incredibly complex. IT networks are more distributed, the workforce is increasingly remote, and employees frequently use personal devices like laptops and mobile devices for business purposes. To complicate matters, regulatory frameworks like HIPAA and GDPR create complex requirements for restoring, protecting, and processing sensitive information. Additionally, despite a growing need for data leak protection, IT teams in every industry are experiencing a shortage of talent that often leaves organizations without adequate skills and protection.
In this environment, data security and data leak protection solutions play an invaluable role in automatically identifying potential leaks and blocking sensitive data from leaving the organization.
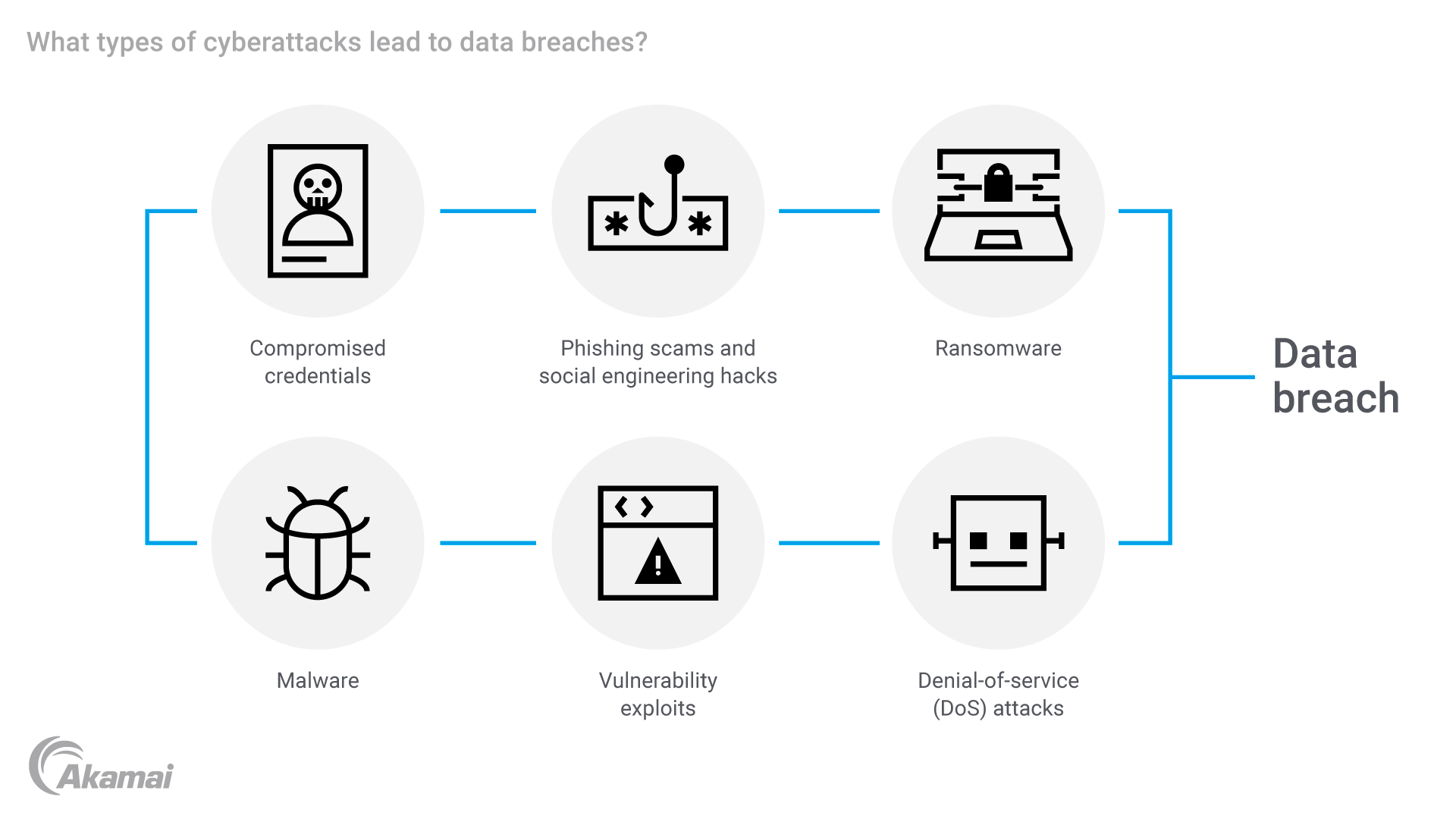
How do data leaks happen?
Data leaks typically happen in one of three ways.
- Accidental data leaks. Many data leaks are inadvertent and unintended. Accidental leaks may be as simple as sending an email with confidential information to the wrong distribution list. Alternatively, inadvertent leaks may occur due to misconfiguration of security settings that result in data exposure or that leave the door wide open to hackers.
- Insider threats. Data may be leaked by current or former employees, contractors, or associates that have access to sensitive data within an organization. These malicious insiders may leak information for a variety of reasons, including personal gain, retribution, or the desire to take information with them as they leave for another job.
- Malicious attacks. Data exfiltration is the ultimate goal of many cyberattacks. Cybercriminals frequently steal and exfiltrate data after gaining unauthorized access to IT environments through malware, exploited vulnerabilities, phishing attacks, social engineering campaigns, or ransomware attacks.
What are forms of data leak protection?
- Email DLP solutions monitor email messages to identify sensitive information, block potential leaks, flag phishing scams, and alert security teams to other potential attacks.
- Network DLP technologies monitor incoming and outgoing traffic from every device connected to the network, blocking or alerting security teams to potential leaks and threats.
- Endpoint DLP security monitors for potential leaks on laptops, servers, and mobile phones, even when these devices are not connected to the network.
- Cloud DLP tracks data and IT assets being uploaded and downloaded from cloud storage and online repositories to monitor for potential leaks and misuse.
What are the elements of a data leak protection solution?
Data leak protection solutions are designed to protect several types of data.
- Data in motion may be tracked by filters installed at the network edge that monitor traffic and identify data leaving the organization that may violate security policies.
- Data on endpoints can be protected by technology that monitors information transferred between users and external parties, blocking attempts to share protected data in real time.
- Data at rest within storage solutions can be protected by access controls, encryption, and data retention policies.
- Data in use may be protected by systems that monitor and flag unauthorized user interactions.
Automated data classification is an essential feature of a data leak protection solution. DLP technology may use rules, metadata, and machine learning technology to analyze data and determine whether it requires special protection. DLP solutions typically also include security features like intrusion detection systems or intrusion prevention systems, and technology to authenticate users accessing or receiving data.
How does data leak protection work?
A data leak protection solution analyzes the content and context of data flowing in and out of an organization, including data sent via email and instant messages. Content analysis looks at the specific content of messages and network traffic, while context analysis looks at external factors such as the size and format of a message.
DLP tools use a variety of techniques to analyze content to ensure that it conforms with data leak protection policies. When data appears to violate DLP policy, the DLP solution may block the information from leaving the organization while alerting security teams. Most DLP solutions use a variety of techniques.
- Regular expression matching searches for specific types of information such as 16-digit credit card numbers, 9-digit Social Security numbers, and other types of data that fit a specific format.
- File checksum analysis helps to uncover whether data stored in databases is adequately protected.
- Structured data fingerprinting, also known as exact data matching, searches for exact matches from a live database or a database dump.
- Partial data matching searches for complete or partial matches of specific files, including multiple versions of forms that have been filled out by different users.
- Statistical analysis uses machine learning and statistical methods to trigger alerts for potential leaks of secure content.
- Lexicon matches analyze unstructured data using rules and dictionary terms to detect sensitive information.
- Categorization identifies sensitive data and compliance violations by analyzing the categories of data.
- Exact file matching matches file hashes to exact data fingerprints.
What are the benefits of data leak protection?
Organizations adopting DLP strategies and technologies can achieve significant benefits.
- Block potentially malicious activity. DLP software automatically scans traffic entering and leaving the network to identify and block potential leaks, data theft, and threats like ransomware.
- Ensure regulatory compliance. Regulatory frameworks like HIPAA, GDPR, PCI DSS, and other common standards have established clear compliance requirements for how data of customers and patients must be protected. DLP solutions help organizations ensure this data is effectively secured, helping to avoid fines, legal action, and loss of customer confidence.
- Improve visibility. By helping organizations to identify and track data at rest and in transit, DLP solutions provide better visibility of the types of data stored throughout the organization.
What are DLP best practices?
- Classify data. By classifying data based on risk of leaks and the impact to the organization, security teams can better prioritize DLP efforts and allocate limited resources for greatest impact.
- Inventory data. IT teams can’t protect data they don’t know about. Conducting a complete scan and inventory of data can help to identify all of the categories and types of data as well as specific data assets that must be protected.
- Deploy a centralized program. When multiple departments and units adopt their own solutions, data leak protection efforts may be inconsistent and ineffective due to gaps in security policies. A centralized DLP program enables a more cohesive approach to protecting sensitive information.
- Conduct security awareness training. Education can help employees understand the risks of data leaks, how they may contribute to them, and what they can do to help keep data secure.
Frequently Asked Questions (FAQ)
DLP may stand for data leak prevention, data leakage prevention, data leak protection, data loss prevention, or data loss protection.
Data leakage occurs when critical data within an organization is accidentally exposed to the public or transferred to an unintended, external recipient.
Akamai Security Solutions
Akamai protects your customer experience, workforce, systems, and data by helping to embed security into everything you create — anywhere you build it and everywhere you deliver it. Our platform’s visibility into global threats helps us adapt and evolve your security posture — to enable Zero Trust, stop ransomware, secure apps and APIs, or fight off DDoS attacks — giving you the confidence to continually innovate, expand, and transform what’s possible.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.