Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Application programming interfaces (APIs) play a critical role in modern software development. By enabling diverse applications to communicate with each other, APIs allow data to flow freely between applications, web services, and interconnected systems. APIs accelerate software development and make applications more functional.
However, the explosive growth of APIs has also created an efficient and high-value attack vector for cybercriminals. Because APIs serve as the back end for many systems and services, they frequently transfer sensitive data. By adopting API security best practices, organizations can remediate vulnerabilities that attackers frequently exploit and protect APIs from security threats like unauthorized access and data breaches.
The importance of API security
Web applications have become an integral part of every aspect of business and daily life. Most web applications rely on APIs to communicate with other apps and systems. Consequently, APIs frequently expose application logic, resources, and sensitive data. When left unprotected, APIs provide attackers with an easy way to gain unauthorized access to IT networks and disrupt business, steal data, or launch other devastating cyberattacks. While application security has been a high priority for quite some time, API security has too often been an afterthought. Today, however, more organizations are realizing the importance of API security and adopting best practices to achieve it.
Threats to APIs
Cybercriminals use a wide range of techniques to gain unauthorized access to API endpoints and to expose or steal sensitive information. Common API risks and threats include:
- Injection attacks: Attackers can trick an API into executing unintended and dangerous actions by sending malicious code to an application’s server via an API request. SQL injection and command injection are common types of injection attacks. Injection attacks can result in data loss, data breaches, or the takeover of an entire system.
- Vulnerability exploits: Many APIs have vulnerabilities in their code that allows attackers to gain unauthorized access to the API or its corresponding application.
- Authentication issues: Weak authentication mechanisms enable attackers to gain unauthorized access to APIs and, in turn, to IT environments. When APIs don’t deploy proper authentication mechanisms, attackers can impersonate a legitimate user to view sensitive data or take unauthorized actions.
- Broken access controls: When an API authenticates a user’s identity but doesn’t properly check what level of access the user is permitted, users (or attackers posing as legitimate users) may be able to access data or actions that should not be available to them.
- Denial of service (DoS): DoS attacks use multiple, illegitimate API requests to cause a web server to slow down, break, or crash. When attackers use multiple APIs to issue an overwhelming number of requests, the threat becomes a distributed denial-of-service (DDoS) attack.
- Brute-force attacks: Attackers use APIs to break into an IT environment by exploiting weak passwords, automatically and repeatedly attempting to guess login credentials until they guess the right combination.
- API abuse: Attackers may misuse APIs for malicious purposes like sending spam or launching attacks from a source that appears to be reputable.
- Machine in the middle (MITM): By intercepting and manipulating API traffic between two parties, attackers can compromise communications, steal data, or inject malicious code.
- Cross-site scripting (XSS): These attacks inject malicious scripts into the code of a trusted website or application.
API security best practices
Organizations and security teams can follow these API security best practices to prevent APIs from being attacked or abused.
Secure development
- Design for security: Integrate API security standards and practices into every stage of the API development lifecycle. This enables organizations to find vulnerabilities before APIs enter production, reducing the risk of successful attacks.
- Test early and often: Starting in the early stages of development, incorporate automated security testing throughout the entire process, and run a wide range of tests simulating malicious traffic. Run API-focused security tests that run on demand or as part of a CI/CD pipeline.
- Validate and sanitize inputs: Implement strict input validation and sanitization to prevent injection attacks such as SQL injection and XSS. Ensure that all user inputs are checked for validity and sanitized before processing.
- Align API specs with governance: Inspect your API specifications against established governance policies and rules.
API discovery
- Build a comprehensive inventory: Locate and inventory all of your APIs regardless of configuration or type, with specialized capabilities for detecting difficult-to-find dormant, legacy, and zombie APIs. Identify forgotten, neglected, or otherwise unknown shadow domains.
Posture management
- Continuously assess API risk: Assess APIs and infrastructure for misconfigurations and vulnerabilities, evaluate your exposure to API attacks, and inspect contextual API data to find compliance gaps.
- Implement posture management capabilities:
This includes:- Automatically scanning infrastructure to uncover misconfigurations and hidden risks
- Creating custom workflows to notify key stakeholders of vulnerabilities
- Identifying which APIs and internal users are able to access sensitive data
- Assigning severity rankings to detected issues to prioritize remediation
Authentication and authorization
- Use strong authentication mechanisms: To ensure that user data is protected and only accessible to authorized individuals, security teams should integrate with authentication providers to implement robust user authentication methods such as multi-factor authentication, OAuth 2.0, API keys, JSON Web Tokens (JWT), and a Zero Trust approach to authenticating users, devices, and applications.
- Implement access control: Use role-based access control (RBAC) and least privilege principles to ensure that users have only the permissions they need.
Data security
- Encrypt data in transit: Use Transport Layer Security (TLS) to encrypt data transmitted between the client and server. This protects against MITM attacks and ensures data integrity.
- Encrypt sensitive data at rest: Protect sensitive information stored in databases or file systems using strong encryption algorithms.
Runtime protection
- Monitor API traffic: Continuously monitor API traffic to detect unusual patterns and potential security issues — this includes data tampering and leakage, policy violations, and suspicious behavior. Use logging to capture detailed information about API requests and responses.
- Analyze logs for security incidents: Regularly review and analyze logs to identify security breaches, misconfigurations, and other security vulnerabilities.
- Use threat detection: Use signature-based threat detection and prevention as a baseline level of protection against known API attacks. Augment signature-based detection with AI and behavioral analytics to make API threat detection more scalable, accurate, business-relevant, and resilient against novel threats.
- Use automation to reduce risk: Integrate with existing workflows (ticketing, SIEM, etc.) to alert security/operations teams of potential API security incidents. Prevent attacks and misuse in real time with partial or fully automated remediation.
- Stay current: Stay informed about the latest threats and vulnerabilities. The Open Worldwide Application Security Project (OWASP) offers resources, security blogs, and industry news, along with an OWASP API Security Top 10 list that provides details about the primary threats to API security.
Security testing and compliance
- Conduct security testing: Perform regular security testing, including pen testing and vulnerability scanning, to identify and address security risks.
- Adhere to security standards: Follow security standards and guidelines such as those outlined in the OWASP API Security Top 10 list, to protect against common security threats and vulnerabilities.
Configuration management
- Secure API endpoints: Protect all API endpoints with appropriate security measures. Ensure that only authorized clients can access sensitive endpoints.
- Manage API lifecycle: Properly manage the lifecycle of APIs, including versioning, deprecation, and retirement, to maintain security and functionality.
Attack surface management
- Limit exposure: Limit the number of exposed API endpoints and functionalities to minimize the attack surface. Implement least privilege and ensure that only necessary services are accessible.
- Use secure headers: Implement security headers such as Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and X-Content-Type-Options to enhance security.
- Practice continuous discovery: Perform continuous discovery of APIs to ensure all APIs are adequately protected.
Auditing and updating
- Perform audits regularly: Schedule periodic audits by experienced penetration testers to identify vulnerabilities and weaknesses.
- Scan for vulnerabilities: Use automated scanning tools to uncover security issues.
Security incident handling
- Prepare for incident response: Have an incident response plan in place to address security breaches and other security incidents promptly. Ensure that your team is trained and ready to respond to potential attacks.
- Regularly update and patch systems: Keep your APIs and back-end systems updated with the latest security patches to protect against known vulnerabilities.
Security solution deployment
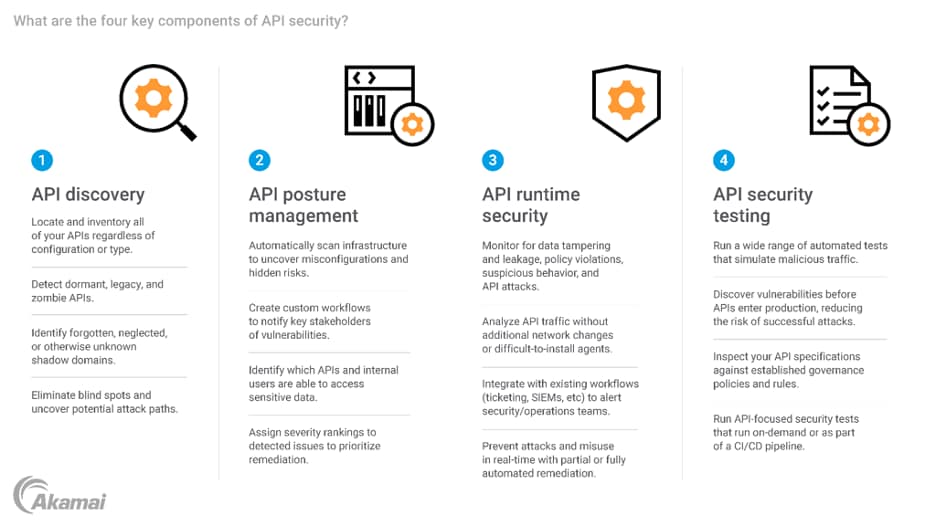
- API security solutions: A comprehensive API security solution protects APIs throughout their entire lifecycle, from development to production. A solution designed to secure against today’s API security threats can discover your APIs (including unmanaged APIs), understand their risk posture, analyze their behavior, and stop threats from lurking inside. API security solutions should provide four key capabilities:
- API discovery
- API posture management
- API runtime security
- API security testing
- Firewalls: Use web application firewalls (WAFs) to protect APIs from common threats and attacks.
- API management platforms: Tools like API gateways and management platforms help secure, manage, and monitor API traffic.
FAQs
An API, or application programming interface, is a set of rules or protocols that allow software applications to communicate with each other to share data, features, and functionality. APIs accelerate software development timelines by enabling developers to integrate services and functionality from other software rather than creating them from scratch.
REST (Representational State Transfer) and SOAP (Simple Object Access Protocol) are different types of API design. SOAP APIs are highly structured APIs — they use XML for messaging and are inherently more secure due to built-in standards like WS-Security. They often run over HTTPS and include support for various security standards like SSL/TLS. REST APIs are more flexible but somewhat less secure. REST APIs often use JSON for data interchange and rely on HTTP methods such as GET, POST, PUT, and DELETE. Security measures for REST APIs include TLS encryption, OAuth 2.0 for authentication, and API keys.