A New Approach to Blocking Malicious JavaScript
A new approach to blocking malicious JavaScript
JavaScript is a text-based programming language used in web browsers on the client side and in web pages on the server side. Along with HTML and CSS, which offer structure and style to web pages, JavaScript provides interactive functions and features that make the end-user experience more dynamic, interactive, and engaging.
Malicious actors
Just like many other web technologies, JavaScript has long been used by malicious actors to execute attacks such as malware delivery, bitcoin-mining, phishing, and web skimming.
But now the attackers are using obfuscation techniques to hide the malicious JavaScript, which makes it harder to debug and, as a result, makes it much harder to detect. This is due to the fact that the obfuscated malicious code is not executed until it is on the client’s device, and by then it's too late — the damage is already done.
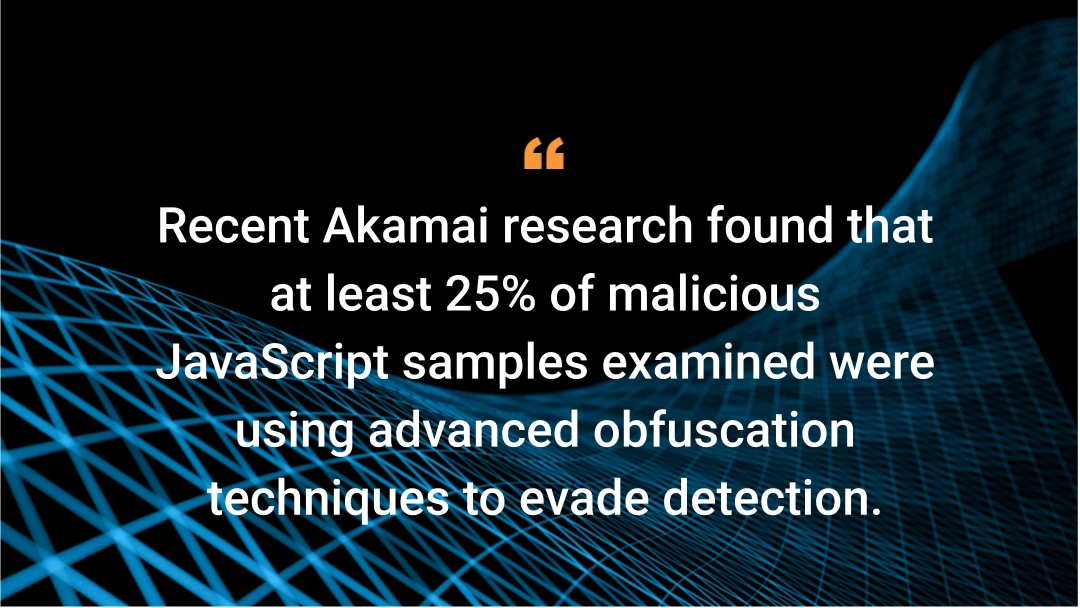
Recent Akamai research found that at least 25% of malicious JavaScript samples examined were using advanced obfuscation techniques to evade detection.
JavaScript obfuscation
The same research also highlighted that benign websites are also using JavaScript obfuscation techniques; according to Alexa.com, at least 0.5% of the 20,000 top-ranked websites contain embedded, obfuscated JavaScript code.
The usage of obfuscated code on those websites is not an indication of them being malicious, but is rather a technique to conceal the code functionality from others so it’s harder to understand.
However, this use of JavaScript obfuscation in both harmful and harmless web pages means that you can’t simply use the detection of obfuscation to classify content as malicious.
Advanced machine learning
During the research, Akamai security researchers used advanced machine learning techniques to examine more than 30,000 malicious and benign JavaScript samples. As a result, they saw that authors of the malicious JavaScript samples were frequently using software packers to compress and encrypt the code.
Profiling the behavior of those software packers has now resulted in the development of a new and unique detection engine for Akamai’s cloud secure web gateway, which can determine if JavaScript code is malicious or benign
Malicious JavaScript detection engine
The malicious JavaScript detection engine within Akamai Secure Internet Access Enterprise is designed to accurately categorize and block malicious JavaScript web pages in real time to increase protection against phishing, malware, and ransomware attacks that might evade other detection techniques.
In addition, the malicious JavaScript detection engine is also deployed offline where it is used to continuously classify JavaScript samples to identify new malicious web pages and create new detection fingerprints. Newly discovered malicious domains are then added automatically to Akamai’s real-time threat intelligence so all customers are protected right away.
Learn more
To find out more about Akamai’s cloud-based secure web gateway and to sign up for a free 60-day trial visit https://www.akamai.com/products/secure-internet-access-enterprise.



